第四篇:华为防火墙USG5500-企业双ISP出口
需求:
(1)技术部IP地址自动获取,网段为192.168.10.0/24,该部门访问Internet的报文正常情况下流入链路ISP1。
总经办IP地址自动获取,网段为192.168.20.0/24,该部门访问Internet的报文正常情况下流入链路ISP2。
(2)技术部和总经办所在链路互为备份,当某部门的链路(以下称主链路)出现故障时,流量切换到另一部门所在的链路(以下称备链路)上。
(3)开SYN Flood、UDP Flood和ICMP Flood攻击防范功能.。
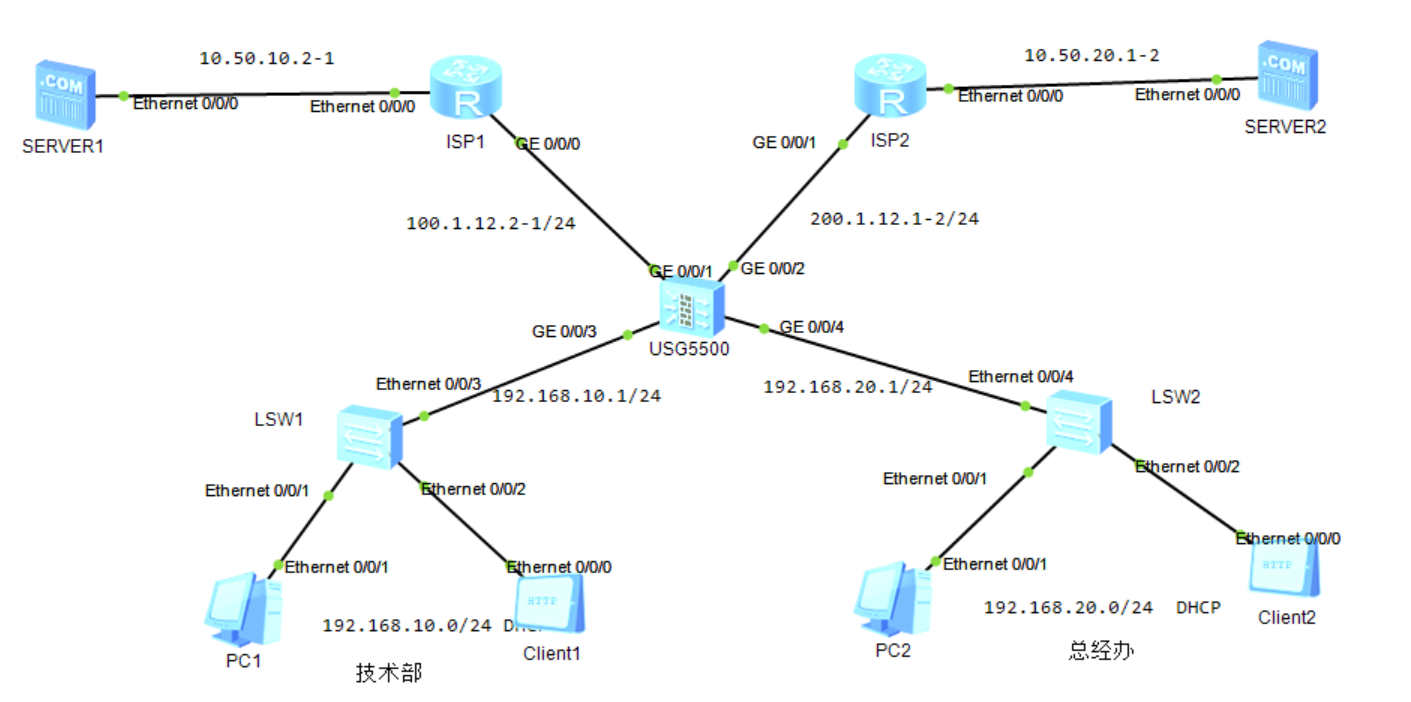
一、ISP1配置:
#
interface Ethernet0/0/0
ip address 10.50.10.1 255.255.255.0
#
interface GigabitEthernet0/0/0
ip address 100.1.12.2 255.255.255.0
二、ISP2配置:
interface Ethernet0/0/0
ip address 10.50.20.1 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 200.1.12.2 255.255.255.0
三、USG5500配置:
#
acl number 2001
rule 5 permit source 192.168.10.0 0.0.0.255
rule 100 deny
#
acl number 2002
rule 5 permit source 192.168.20.0 0.0.0.255
rule 100 deny
#
interface GigabitEthernet0/0/1
ip address 100.1.12.1 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 200.1.12.1 255.255.255.0
#
interface GigabitEthernet0/0/3
ip address 192.168.10.1 255.255.255.0
ip policy-based-route 10
dhcp select interface
dhcp server gateway-list 192.168.10.1
dhcp server dns-list 114.114.114.114 10.50.10.10
dhcp server domain-name huawei.com
#
interface GigabitEthernet0/0/4
ip address 192.168.20.1 255.255.255.0
ip policy-based-route 20
dhcp select interface
dhcp server gateway-list 192.168.20.1
dhcp server dns-list 114.114.114.114 10.50.20.20
dhcp server domain-name huawei.com
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/3
add interface GigabitEthernet0/0/4
#
#
firewall zone name isp1
set priority 15
add interface GigabitEthernet0/0/1
#
firewall zone name isp2
set priority 20
add interface GigabitEthernet0/0/2
#
#
ip route-static 0.0.0.0 0.0.0.0 100.1.12.2 track ip-link 2
ip route-static 0.0.0.0 0.0.0.0 200.1.12.2 track ip-link 1
#
#
policy-based-route 10 permit node 5
if-match acl 2001
apply ip-address next-hop 100.1.12.2
policy-based-route 20 permit node 5
if-match acl 2002
apply ip-address next-hop 200.1.12.2
#
firewall packet-filter default permit interzone trust isp1 direction outbound
firewall packet-filter default permit interzone trust isp2 direction outbound
#nat-policy interzone trust isp1 outbound
policy 1
action source-nat
easy-ip GigabitEthernet0/0/1
#
nat-policy interzone trust isp2 outbound
policy 1
action source-nat
easy-ip GigabitEthernet0/0/2
#
firewall defend syn-flood enable
firewall defend udp-flood enable
firewall defend icmp-flood enable
firewall defend icmp-flood base-session max-rate 5
return




 浙公网安备 33010602011771号
浙公网安备 33010602011771号