课程设计第四周进度
查找并研究SSL VPN协议标准


SSL_VPN子协议主要包括握手协议、密码规格变更协议、报警协议、网关到网关协议和记录层协议。
1. 握手协议(Handshake Protocol):
握手协议负责在通信双方建立安全通信通道之前进行握手。握手协议的主要任务包括:
- 协商加密算法和密钥材料。
- 互相验证身份,确保通信双方是合法的。
- 协商其他通信参数,如支持的协议版本等。
2. 密码规格变更协议(Change Cipher Spec Protocol):
变更密码规格协议用于通知对方,在握手完成后,后续的通信将使用新协商好的加密规范。它在握手协议结束后,通信的起始点明确告知对方即将使用新的密钥和加密规范进行通信。
3. 报警协议(Alert Protocol):
报警协议用于传递与连接状态相关的警告信息。这些信息可以包括握手失败、证书问题、连接关闭等。通过报警协议,通信双方能够及时了解到连接状态的问题,并采取适当的措施。
4. 网关到网关协议(Record Protocol):
记录协议是 TLS/SSL 协议的核心,负责将应用层的数据划分成适当的记录,并进行加密、认证和压缩。记录协议的主要任务包括:
- 加密和认证应用层数据,保障数据机密性和完整性。
- 维护记录边界,确保记录在传输过程中能够正确重组。
提供记录流的完整性检查,防止中间人攻击。
5. 网关到网关协议(Gateway-to-Gateway Protocol):
在 TLS/SSL 协议中,有一个称为 "网关到网关协议" 的标准协议。通常,网关指的是网络设备,而 TLS/SSL 主要用于端到端的加密和安全通信,涉及客户端和服务器。但SSL VPN 本身可能涉及到与 VPN 网关的通信,这通常是通过 TLS 握手协议和记录协议来实现的。
sslvpn的lua脚本代码如下
local function dissect_alert_protocol(tvb, pktinfo, root)
local alert_level = tvb(0, 1):uint()
local alert_description = tvb(1, 1):uint()
pktinfo.cols.protocol:set("SSL VPN - Alert Protocol")
-- Add specific logic for the Alert Protocol
if alert_level == 2 and alert_description == 2 then
pktinfo.cols.info:append(" - Custom Alert Logic: Detected Critical Alert!")
elseif alert_level == 1 and alert_description == 0 then
pktinfo.cols.info:append(" - Custom Alert Logic: Detected Warning Alert!")
else
pktinfo.cols.info:append(" - Custom Alert Logic: Other Alert Level/Description")
end
end
local function dissect_gateway_to_gateway_protocol(tvb, pktinfo, root)
local gateway_field = tvb(4, 2):uint()
pktinfo.cols.protocol:set("SSL VPN - Gateway-to-Gateway Protocol")
-- Add specific logic for the Gateway-to-Gateway Protocol
if gateway_field == 0x1234 then
pktinfo.cols.info:append(" - Custom Gateway Logic: Detected Gateway Field 0x1234!")
else
pktinfo.cols.info:append(" - Custom Gateway Logic: Other Gateway Field Value")
end
end
local function dissect_record_layer_protocol(tvb, pktinfo, root)
local record_type = tvb(0, 1):uint()
pktinfo.cols.protocol:set("SSL VPN - Record Layer Protocol")
-- Add specific logic for the Record Layer Protocol
if record_type == 0x14 then
pktinfo.cols.info:append(" - Custom Record Layer Logic: Detected Change Cipher Spec!")
else
pktinfo.cols.info:append(" - Custom Record Layer Logic: Other Record Type")
end
end
local function dissect_client_hello(tvb, pktinfo, root)
-- Extract TLS version information
local tls_version = tvb(1, 2):uint()
pktinfo.cols.info:set("TLS Version: " .. tostring(tls_version))
-- Extract Cipher Suites information
local cipher_suites_offset = 43
local cipher_suites_length = tvb(cipher_suites_offset, 2):uint()
local cipher_suites = tvb(cipher_suites_offset + 2, cipher_suites_length)
pktinfo.cols.info:append("Cipher Suites: " .. tostring(cipher_suites))
-- Other information extraction and settings can be done here
print("Debug: ClientHello dissected successfully!") -- Add debug information
end
local function dissect_ssl_handshake(tvb, pktinfo, root)
local handshake_type = tvb(0, 1):uint()
if handshake_type == 0x01 then
local tls_version = tvb(1, 2):uint()
pktinfo.cols.protocol:set("SSL VPN - ClientHello")
-- Call the function to parse ClientHello
dissect_client_hello(tvb, pktinfo, root)
elseif handshake_type == 0x02 then
pktinfo.cols.protocol:set("SSL VPN - ServerHello")
else
pktinfo.cols.protocol:set("SSL VPN - Other Handshake")
end
end
local function dissect_cipher_spec_change(tvb, pktinfo, root)
local record_type = tvb(0, 1):uint()
if record_type == 0x14 then -- SSL/TLS Record Layer: Change Cipher Spec
pktinfo.cols.protocol:set("SSL VPN - Cipher Spec Change")
else
pktinfo.cols.protocol:set("SSL VPN - Other Cipher Spec")
end
end
local function dissect_tcp_three_way_handshake(tvb, pktinfo, root)
local tcp_flags_offset = 47 -- TCP Flags offset
local tcp_flags = tvb(tcp_flags_offset, 1):uint()
-- Add debug information to ensure correct TCP Flags are obtained
io.write("Debug: TCP Flags - " .. string.format("%02X", tcp_flags) .. "\n")
local syn_flag = bit32.band(tcp_flags, 0x02) ~= 0
local ack_flag = bit32.band(tcp_flags, 0x10) ~= 0
if syn_flag and not ack_flag then
pktinfo.cols.protocol:set("SSL VPN - TCP SYN")
elseif syn_flag and ack_flag then
pktinfo.cols.protocol:set("SSL VPN - TCP SYN-ACK")
elseif not syn_flag and ack_flag then
pktinfo.cols.protocol:set("SSL VPN - TCP ACK")
else
pktinfo.cols.protocol:set("SSL VPN - Other TCP")
end
end
local function dissect_ssl_vpn(tvb, pktinfo, root)
local src_port = pktinfo.src_port
local dst_port = pktinfo.dst_port
-- Check port numbers to determine SSL VPN traffic
if src_port == 443 or dst_port == 443 then
-- Call TCP three-way handshake analysis function
dissect_tcp_three_way_handshake(tvb, pktinfo, root)
-- Check if TCP three-way handshake has been successfully dissected
local protocol_str = tostring(pktinfo.cols.protocol)
if protocol_str and string.find(protocol_str, "TCP SYN") then
return
end
-- Call SSL handshake protocol analysis function
dissect_ssl_handshake(tvb, pktinfo, root)
-- Check if SSL handshake has been successfully dissected
protocol_str = tostring(pktinfo.cols.protocol)
if protocol_str and string.find(protocol_str, "ClientHello") then
return
end
-- Call Cipher Spec Change protocol analysis function
dissect_cipher_spec_change(tvb, pktinfo, root)
-- Check if Cipher Spec Change has been successfully dissected
protocol_str = tostring(pktinfo.cols.protocol)
if protocol_str and string.find(protocol_str, "Cipher Spec Change") then
return
end
-- Call Alert Protocol analysis function
dissect_alert_protocol(tvb, pktinfo, root)
-- Call Gateway-to-Gateway Protocol analysis function
dissect_gateway_to_gateway_protocol(tvb, pktinfo, root)
-- Call Record Layer Protocol analysis function
dissect_record_layer_protocol(tvb, pktinfo, root)
end
end
local function ssl_vpn_protocol_init()
local ssl_vpn_proto = Proto("ssl_vpn", "SSL VPN Protocol")
function ssl_vpn_proto.dissector(tvb, pktinfo, root)
dissect_ssl_vpn(tvb, pktinfo, root)
end
-- Associate the dissector with the default SSL VPN port (443)
local tcp_table = DissectorTable.get("tcp.port")
tcp_table:add(443, ssl_vpn_proto)
end
-- Call the function to start SSL VPN protocol analysis
ssl_vpn_protocol_init()
查看wireshark插件是否正常import
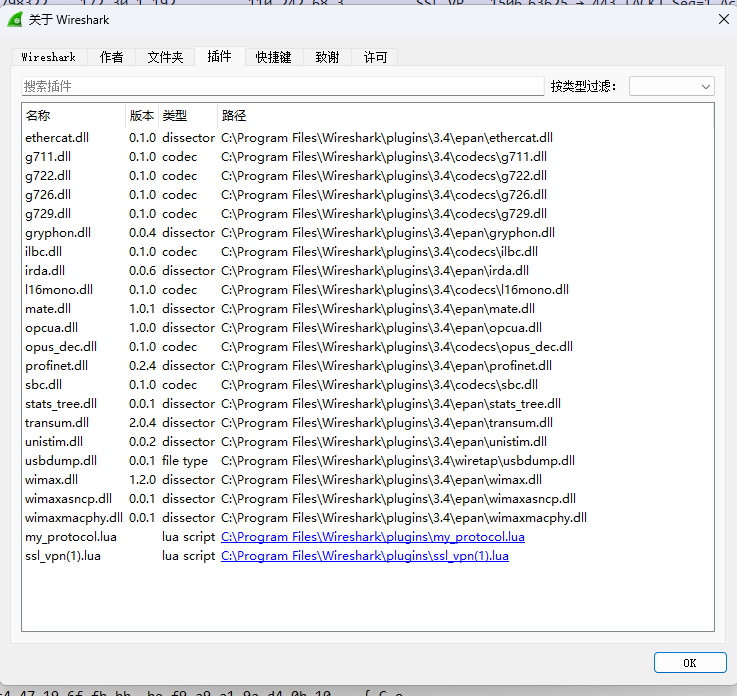
运行结果分析
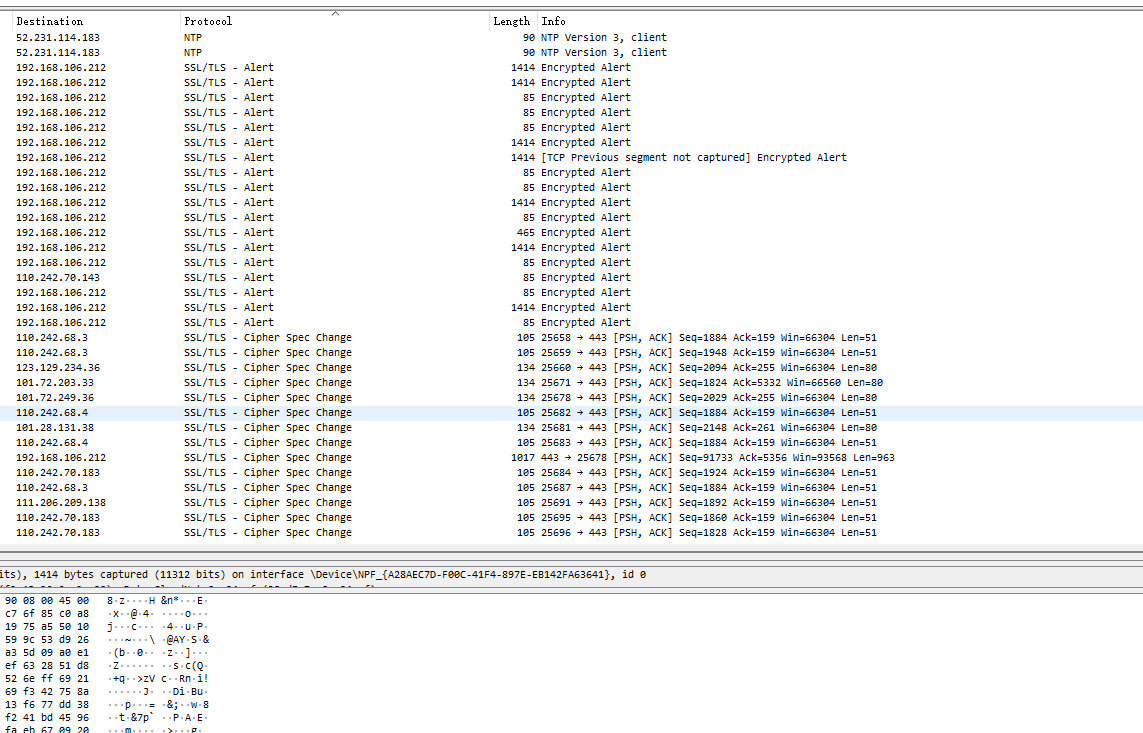
可以在Wirshark中抓获数据包中成功捕捉并显示相关报警协议、密码规格变更协议等



 浙公网安备 33010602011771号
浙公网安备 33010602011771号