awk实现将lastb里超过失败登录次数上限的IP地址自动加入黑名单
日期:2024.11.6
起因:今天有人不断登录我主机,应该是拿我练习入侵。我也一直就有写个自动拉黑脚本的打算了,正好也用这个机会测试一下。
思路:用crontab创建计划任务每1小时用awk过滤lastb里显示的上个小时里失败登录的IP地址并做统计,超过设定的次数就自动加入firewalld的黑名单里并mail发邮件到我邮箱。
指令
[root@RHEL9 ~]# lastb | awk -v hourago="$(date --date='1 hour ago' '+%a %b %e %H:')" '$0~hourago{ip[$3]++}END{for (i in ip){if(ip[i]>11){system("firewall-cmd --add-source="i" --zone=block;firewall-cmd --runtime-to-permanent;echo \"$(hostname) ban "i" for connected "ip[i]" times in 1 hour\" >> /tmp/baninfo")}}}';[ -e /tmp/baninfo ] && cat /tmp/baninfo | mail -s "Ban Info" xxxxx@xx.com && rm -f /tmp/baninfo
crontab
[root@RHEL9 ~]# crontab -l
0 * * * * /usr/bin/lastb | /usr/bin/awk -v hourago="$(/usr/bin/date --date='1 hour ago' '+\%a \%b \%e \%H:')" '$0~hourago{ip[$3]++}END{for (i in ip){if(ip[i]>11){system("/usr/bin/firewall-cmd --add-source="i" --zone=block;/usr/bin/firewall-cmd --runtime-to-permanent;/usr/bin/echo \"$(/usr/bin/hostname) ban "i" for connected "ip[i]" times in 1 hour\" >> /tmp/baninfo")}}}';[ -e /tmp/baninfo ] && /usr/bin/cat /tmp/baninfo | /usr/bin/mail -s "Ban Info" xxxxx@xx.com && /usr/bin/rm -f /tmp/baninfo
shellscript自动写入crontab
[root@RHEL9 ~]# cat awkban.sh
#awkban.sh
#Date: 2024-11-12
#!/bin/bash
cat << EOF >> /var/spool/cron/root
0 * * * * /usr/bin/lastb | /usr/bin/awk -v hourago="\$(/usr/bin/date --date='1 hour ago' '+\%a \%b \%e \%H:')" '\$0~hourago{ip[\$3]++}END{for (i in ip){if(ip[i]>11){system("/usr/bin/firewall-cmd --add-source="i" --zone=block;/usr/bin/firewall-cmd --runtime-to-permanent;/usr/bin/echo \"\$(/usr/bin/hostname) ban "i" for connected "ip[i]" times in 1 hour\" >> /tmp/baninfo")}}}';[ -e /tmp/baninfo ] && /usr/bin/cat /tmp/baninfo | /usr/bin/mail -s "Ban Info" xxxxx@xx.com && /usr/bin/rm -f /tmp/baninfo
EOF
nftables版
[root@RHEL8 ~]# cat awknftban.sh
#awkban.sh
#Date: 2024-11-11
#!/bin/bash
#写入计划任务
#1.自动拉黑每小时登录失败超过指定次数的IP
rulefile='/etc/nftables/rhel8.nft'
cat << EOF >> /var/spool/cron/root
0 * * * * /usr/bin/lastb | /usr/bin/awk -v hourago="\$(/usr/bin/date --date='1 hour ago' '+\%a \%b \%e \%H:')" '\$0~hourago{ip[\$3]++}END{for (i in ip){if(ip[i]>11){system("/usr/sbin/nft insert rule inet NFT_FILTER NFC_INPUT handle 5 iifname enp1s0 ip saddr "i" reject;/usr/sbin/nft -a list ruleset >| ${rulefile};/usr/bin/echo \"\$(/usr/bin/hostname) ban "i" for connected "ip[i]" times in 1 hour\" >> /tmp/baninfo")}}}';[ -e /tmp/baninfo ] && /usr/bin/cat /tmp/baninfo | /usr/bin/mail -s "Ban Info" XXXXX@XX.com && /usr/bin/rm -f /tmp/baninfo
EOF
[root@RHEL8 ~]# sh awknftban.sh
[root@RHEL8 ~]# crontab -l
0 * * * * /usr/bin/lastb | /usr/bin/awk -v hourago="$(/usr/bin/date --date='1 hour ago' '+\%a \%b \%e \%H:')" '$0~hourago{ip[$3]++}END{for (i in ip){if(ip[i]>11){system("/usr/sbin/nft insert rule inet NFT_FILTER NFC_INPUT handle 5 iifname enp1s0 ip saddr "i" reject;/usr/sbin/nft -a list ruleset >| /etc/nftables/rhel8.nft;/usr/bin/echo \"$(/usr/bin/hostname) ban "i" for connected "ip[i]" times in 1 hour\" >> /tmp/baninfo")}}}';[ -e /tmp/baninfo ] && /usr/bin/cat /tmp/baninfo | /usr/bin/mail -s "Ban Info" XXXXX@XX.com && /usr/bin/rm -f /tmp/baninfo
iptables
[root@ZH-ROUTER-rocky9 ~]# cat awkban.sh
#awkban.sh
#Date: 2025-01-04
#!/bin/bash
#写入计划任务
#1.自动拉黑每小时登录失败超过指定次数的IP
rulefile='/etc/sysconfig/iptables'
cat << EOF >> /var/spool/cron/root
0 * * * * /usr/bin/lastb | /usr/bin/awk -v hourago="\$(/usr/bin/date --date='1 hour ago' '+\%a \%b \%e \%H:')" '\$0~hourago{ip[\$3]++}END{for (i in ip){if(ip[i]>11){system("/usr/sbin/iptables -I INPUT 4 -s "i" -j REJECT;/usr/sbin/iptables-save >| ${rulefile};/usr/bin/echo \"\$(/usr/bin/hostname) ban "i" for connected "ip[i]" times in 1 hour\" >> /tmp/baninfo")}}}';[ -e /tmp/baninfo ] && /usr/bin/cat /tmp/baninfo | /usr/bin/mail -s "Ban Info" XXXXX@XX.com && /usr/bin/rm -f /tmp/baninfo
EOF
[root@ZH-ROUTER-rocky9 ~]# crontab -l
0 * * * * /usr/bin/lastb | /usr/bin/awk -v hourago="$(/usr/bin/date --date='1 hour ago' '+\%a \%b \%e \%H:')" '$0~hourago{ip[$3]++}END{for (i in ip){if(ip[i]>11){system("/usr/sbin/iptables -I INPUT 4 -s "i" -j REJECT;/usr/sbin/iptables-save >| /etc/sysconfig/iptables;/usr/bin/echo \"$(/usr/bin/hostname) ban "i" for connected "ip[i]" times in 1 hour\" >> /tmp/baninfo")}}}';[ -e /tmp/baninfo ] && /usr/bin/cat /tmp/baninfo | /usr/bin/mail -s "Ban Info" XXXXX@XX.com && /usr/bin/rm -f /tmp/baninfo
目前还一直在被登录
[root@RHEL9 ~]# lastb | head
sycdl ssh:notty 159.89.207.36 Wed Nov 6 23:53 - 23:53 (00:00)
ss97 ssh:notty 159.89.207.36 Wed Nov 6 23:53 - 23:53 (00:00)
smy ssh:notty 159.89.207.36 Wed Nov 6 23:53 - 23:53 (00:00)
smy ssh:notty 159.89.207.36 Wed Nov 6 23:53 - 23:53 (00:00)
shuminzh ssh:notty 159.89.207.36 Wed Nov 6 23:53 - 23:53 (00:00)
shuminzh ssh:notty 159.89.207.36 Wed Nov 6 23:53 - 23:53 (00:00)
pyt ssh:notty 159.89.207.36 Wed Nov 6 23:52 - 23:52 (00:00)
pyt ssh:notty 159.89.207.36 Wed Nov 6 23:52 - 23:52 (00:00)
omnisky ssh:notty 159.89.207.36 Wed Nov 6 23:52 - 23:52 (00:00)
mrbai ssh:notty 159.89.207.36 Wed Nov 6 23:51 - 23:51 (00:00)
先用date指令调出1小时前的时间
[root@RHEL9 ~]# date
Wed Nov 6 11:59:43 PM CST 2024
[root@RHEL9 ~]# date --date='1 hour ago'
Wed Nov 6 11:00:32 PM CST 2024
lastb的时间日期格式为 缩写的星期名 缩写的月份名 空格填充的日期(个位日期前面没有0) 24小时的时间:分钟
%a locale's abbreviated weekday name (e.g., Sun)
%b locale's abbreviated month name (e.g., Jan)
%e day of month, space padded; same as %_d
%H hour (00..23)
%M minute (00..59)
按小时过滤,分钟这个参数用不上,但是测试的时候用的上。配置参数将date指令日期格式设置为与lastb相同
[root@RHEL9 ~]# lastb | head -1
lixiao ssh:notty 159.89.207.36 Thu Nov 7 00:33 - 00:33 (00:00)
[root@RHEL9 ~]# lastb | head -1 | sed -En 's/^.+\.[0-9]+ +(.+)$/\1/p'
Thu Nov 7 00:33 - 00:33 (00:00)
[root@RHEL9 ~]# date --date='1 hour ago' '+%a %b %e %H:%M'
Wed Nov 6 23:34
测试date指令在awk里赋值并调用
[root@RHEL9 ~]# echo | awk -v hourago="$(date --date='1 hour ago' '+%a %b %e %H:%M')" '{print hourago}'
Wed Nov 6 23:40
用 ~ 匹配,$0 ~ hourago ,检索 全文里 包含 hourago 变量里日期格式的行,按分钟显示出1小时前登录我主机的记录。
[root@RHEL9 ~]# lastb | awk -v hourago="$(date --date='1 hour ago' '+%a %b %e %H:%M')" '$0~hourago{print $0}'
fym ssh:notty 159.89.207.36 Wed Nov 6 23:49 - 23:49 (00:00)
csj20017 ssh:notty 159.89.207.36 Wed Nov 6 23:49 - 23:49 (00:00)
cjw ssh:notty 159.89.207.36 Wed Nov 6 23:49 - 23:49 (00:00)
[root@RHEL9 ~]# lastb | awk -v hourago="$(date --date='1 hour ago' '+%a %b %e %H:%M')" '$0~hourago{print $0}'
lj187153 ssh:notty 159.89.207.36 Wed Nov 6 23:50 - 23:50 (00:00)
lft ssh:notty 159.89.207.36 Wed Nov 6 23:50 - 23:50 (00:00)
hsy ssh:notty 159.89.207.36 Wed Nov 6 23:50 - 23:50 (00:00)
hsy ssh:notty 159.89.207.36 Wed Nov 6 23:50 - 23:50 (00:00)
hsy ssh:notty 159.89.207.36 Wed Nov 6 23:50 - 23:50 (00:00)
用for循环统计连接数,1小时前的当前分钟里登录了6次,上个小时里登录了300次
[root@RHEL9 ~]# lastb | awk -v hourago="$(date --date='1 hour ago' '+%a %b %e %H:%M')" '$0~hourago{ip[$3]++}END{for (i in ip) print i,ip[i]}'
159.89.207.36 6
[root@RHEL9 ~]# lastb | awk -v hourago="$(date --date='1 hour ago' '+%a %b %e %H:')" '$0~hourago{ip[$3]++}END{for (i in ip) print i,ip[i]}'
159.89.207.36 300
加入if语句进行条件判断,连接次数超过200打印出来
[root@RHEL9 ~]# lastb | awk -v hourago="$(date --date='1 hour ago' '+%a %b %e %H:')" '$0~hourago{ip[$3]++}END{for (i in ip){if(ip[i]>200)print i,ip[i]}}'
159.89.207.36 300
[root@RHEL9 ~]# lastb | awk -v hourago="$(date --date='1 hour ago' '+%a %b %e %H:')" '$0~hourago{ip[$3]++}END{for (i in ip){if(ip[i]>400)print i,ip[i]}}'
[root@RHEL9 ~]#
调用system{}语句块,在awk里执行bash指令并调用awk里的参数,用echo测试下
[root@RHEL9 ~]# lastb | awk -v hourago="$(date --date='1 hour ago' '+%a %b %e %H:')" '$0~hourago{ip[$3]++}END{for (i in ip){if(ip[i]>100){system("echo "i" "ip[i]"")}}}'
159.89.207.36 300
测试防火墙指令,后续还要测试crontab,拉进黑名单就没法测试了,先拉进白名单
[root@RHEL9 ~]# lastb | awk -v hourago="$(date --date='1 hour ago' '+%a %b %e %H:')" '$0~hourago{ip[$3]++}END{for (i in ip){if(ip[i]>100){system("firewall-cmd --permanent --add-source="i" --zone=trusted;firewall-cmd --reload")}}}'
success
success
[root@RHEL9 ~]# firewall-cmd --get-active-zones
libvirt
interfaces: virbr0
public
interfaces: LANbridge WANbridge enp4s0 DMZbridge
trusted
sources: 159.89.207.36
[root@RHEL9 ~]# firewall-cmd --permanent --remove-source=159.89.207.36 --zone=trusted;firewall-cmd --reload
success
success
编辑邮件内容测试
[root@RHEL9 ~]# lastb | awk -v hourago="$(date --date='1 hour ago' '+%a %b %e %H:')" '$0~hourago{ip[$3]++}END{for (i in ip){if(ip[i]>100){system("firewall-cmd --permanent --remove-source="i" --zone=trusted;firewall-cmd --reload;echo $(hostname) ban "i" for connected "ip[i]" times in 1 hour")}}}'
success
success
RHEL9 ban 159.89.207.36 for connected 300 times in 1 hour
通过mail发送,echo " 信件内容 "和 mail -s " 信件标题 " 需要用 转义+引号 " 引起来
[root@RHEL9 ~]# lastb | awk -v hourago="$(date --date='1 hour ago' '+%a %b %e %H:')" '$0~hourago{ip[$3]++}END{for (i in ip){if(ip[i]>100){system("firewall-cmd --permanent --remove-source="i" --zone=block;firewall-cmd --reload;echo \"$(hostname) ban "i" for connected "ip[i]" times in 1 hour\" | mail -s \"Ban Info\" XXXXX@XX.com")}}}'Warning: NOT_ENABLED: 159.89.207.36
success
success
s-nail: Warning: variable superseded or obsoleted: smtp
s-nail: Warning: variable superseded or obsoleted: smtp-auth-user
s-nail: Warning: variable superseded or obsoleted: smtp-auth-password
s-nail: Warning: variable superseded or obsoleted: ssl-verify
s-nail: Obsoletion warning: please do not use *smtp*, instead assign a smtp:// URL to *mta*!
s-nail: Obsoletion warning: Use of old-style credentials, which will vanish in v15!
s-nail: Please read the manual section "On URL syntax and credential lookup"
配置文件提示语法过时,好歹邮件是过去了
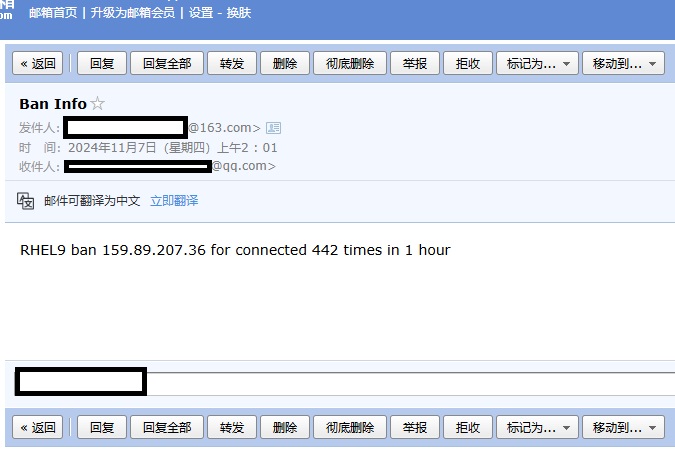
最后查一遍语句写入crontab
lastb | awk -v hourago="$(date --date='1 hour ago' '+%a %b %e %H:')" '$0~hourago{ip[$3]++}END{for (i in ip){if(ip[i]>11){system("firewall-cmd --permanent --add-source="i" --zone=block;firewall-cmd --reload;echo \"$(hostname) ban "i" for connected "ip[i]" times in 1 hour\" | mail -s \"Ban Info\" xxxx@xx.com")}}}'
上面写法执行会报错,只执行到 + 就停了,需要将日期时间格式里的 % 转义
之前在centos7上测试时的报错提示
Message 3:
From root@centos7.localdomain Thu Nov 7 00:05:01 2024
Return-Path: <root@centos7.localdomain>
X-Original-To: root
Delivered-To: root@centos7.localdomain
From: "(Cron Daemon)" <root@centos7.localdomain>
To: root@centos7.localdomain
Subject: Cron <root@centos7> lastb | awk -v hourago="$(date --date='1 hour ago' '+
Content-Type: text/plain; charset=UTF-8
Auto-Submitted: auto-generated
Precedence: bulk
修改后的crontab语句
[root@RHEL9 ~]# crontab -l
30 * * * * lastb | awk -v hourago="$(date --date='1 hour ago' '+\%a \%b \%e \%H:')" '$0~hourago{ip[$3]++}END{for (i in ip){if(ip[i]>11){system("firewall-cmd --permanent --add-source="i" --zone=block;firewall-cmd --reload;echo \"$(hostname) ban "i" for connected "ip[i]" times in 1 hour\" | mail -s \"Ban Info\" XXXXX@XX.com")}}}'
防火墙规则,已经进黑名单了
[root@RHEL9 ~]# firewall-cmd --get-active-zones
block
sources: 159.89.207.36
libvirt
interfaces: virbr0
public
interfaces: LANbridge WANbridge enp4s0 DMZbridge
理所当然停止登录了
[root@RHEL9 ~]# date;lastb | head
Thu Nov 7 02:34:50 AM CST 2024
gaoyuan ssh:notty 159.89.207.36 Thu Nov 7 02:29 - 02:29 (00:00)
gaoyuan ssh:notty 159.89.207.36 Thu Nov 7 02:29 - 02:29 (00:00)
gaojialu ssh:notty 159.89.207.36 Thu Nov 7 02:29 - 02:29 (00:00)
gaojialu ssh:notty 159.89.207.36 Thu Nov 7 02:29 - 02:29 (00:00)
fuyanjie ssh:notty 159.89.207.36 Thu Nov 7 02:29 - 02:29 (00:00)
fuyanjie ssh:notty 159.89.207.36 Thu Nov 7 02:29 - 02:29 (00:00)
fuyahui ssh:notty 159.89.207.36 Thu Nov 7 02:28 - 02:28 (00:00)
cuilingh ssh:notty 159.89.207.36 Thu Nov 7 02:28 - 02:28 (00:00)
cuilingh ssh:notty 159.89.207.36 Thu Nov 7 02:28 - 02:28 (00:00)
cuilingh ssh:notty 159.89.207.36 Thu Nov 7 02:28 - 02:28 (00:00)
邮件
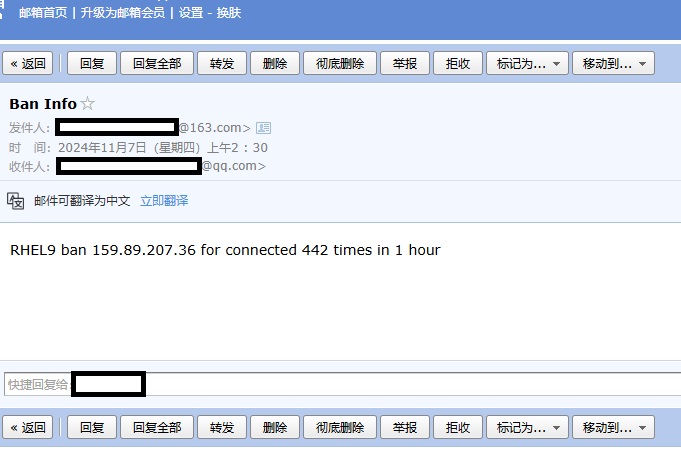
- 优化为多IP版:
目前的测试环境是每小时仅检测出1条IP超出连接次数并拉黑,如果有多条IP满足拉黑条件,每拉黑1个IP,就要reload1次,然后发1次邮件。例如awk检索到3条满足条件的IP,在很短时间内就要reload防火墙3次并连续发3封邮件,简单粗暴不够优雅但是也凑合用。考虑上述原因又做了两点优化。
- 修改firewall语句
原先为--permanent写入配置文件保存再--reload读取并生效
firewall-cmd --permanent --add-source="i" --zone=block;firewall-cmd --reload;
改为先修改规则直接生效然后--runtime-to-permanent再写入配置文件保存,避免了短时间反复读取配置文件
firewall-cmd --add-source="i" --zone=block;firewall-cmd --runtime-to-permanent;
- 将{system}语句块里的echo指令显示的信息写入文件/tmp/baninfo 将mail指令移出{system}语句块
[root@RHEL9 ~]# lastb | awk -v hourago="$(date --date='22 hour ago' '+%a %b %e %H:')" '$0~hourago{ip[$3]++}END{for (i in ip){if(ip[i]>11){system("firewall-cmd --add-source="i" --zone=block;firewall-cmd --runtime-to-permanent;echo \"$(hostname) ban "i" for connected "ip[i]" times in 1 hour\" >> /tmp/baninfo")}}}';
Warning: ZONE_ALREADY_SET: '159.89.207.36' already bound to 'block'
success
success
[root@RHEL9 ~]# cat /tmp/baninfo
RHEL9 ban 159.89.207.36 for connected 300 times in 1 hour
判断如果 /tmp/baninfo 存在,发送邮件,成功后删除/tmp/baninfo
[ -e /tmp/baninfo ] && cat /tmp/baninfo | mail -s "Ban Info" XXXXX@XX.com && rm -f /tmp/baninfo
- 完整指令
[root@RHEL9 ~]# lastb | awk -v hourago="$(date --date='1 hour ago' '+%a %b %e %H:')" '$0~hourago{ip[$3]++}END{for (i in ip){if(ip[i]>11){system("firewall-cmd --add-source="i" --zone=block;firewall-cmd --runtime-to-permanent;echo \"$(hostname) ban "i" for connected "ip[i]" times in 1 hour\" >> /tmp/baninfo")}}}';[ -e /tmp/baninfo ] && cat /tmp/baninfo | mail -s "Ban Info" xxxxx@xx.com && rm -f /tmp/baninfo
- crontab里的指令
[root@RHEL9 ~]# crontab -l
0 * * * * /usr/bin/lastb | /usr/bin/awk -v hourago="$(/usr/bin/date --date='1 hour ago' '+\%a \%b \%e \%H:')" '$0~hourago{ip[$3]++}END{for (i in ip){if(ip[i]>11){system("/usr/bin/firewall-cmd --add-source="i" --zone=block;/usr/bin/firewall-cmd --runtime-to-permanent;/usr/bin/echo \"$(/usr/bin/hostname) ban "i" for connected "ip[i]" times in 1 hour\" >> /tmp/baninfo")}}}';[ -e /tmp/baninfo ] && /usr/bin/cat /tmp/baninfo | /usr/bin/mail -s "Ban Info" xxxxx@xx.com && /usr/bin/rm -f /tmp/baninfo
- 实现脚本化自动写入crontab
[root@RHEL9 ~]# cat awkban.sh
#awkban.sh
#Date: 2024-11-12
#!/bin/bash
cat << EOF >> /var/spool/cron/root
0 * * * * /usr/bin/lastb | /usr/bin/awk -v hourago="\$(/usr/bin/date --date='1 hour ago' '+\%a \%b \%e \%H:')" '\$0~hourago{ip[\$3]++}END{for (i in ip){if(ip[i]>11){system("/usr/bin/firewall-cmd --add-source="i" --zone=block;/usr/bin/firewall-cmd --runtime-to-permanent;/usr/bin/echo \"\$(/usr/bin/hostname) ban "i" for connected "ip[i]" times in 1 hour\" >> /tmp/baninfo")}}}';[ -e /tmp/baninfo ] && /usr/bin/cat /tmp/baninfo | /usr/bin/mail -s "Ban Info" xxxxx@xx.com && /usr/bin/rm -f /tmp/baninfo
EOF
- 修改指令为绝对路径,新增 nftables 指令 2024.11.12
firewall-cmd 和 nft 两个指令不在一个目录下
[root@RHEL9 ~]# which firewall-cmd
/usr/bin/firewall-cmd
[root@RHEL8 ~]# which nft
/usr/sbin/nft
其余指令也都在/usr/bin目录下
[root@RHEL8 ~]# which lastb awk date echo hostname cat mail rm
alias rm='rm -i'
/usr/bin/rm
/usr/bin/lastb
/usr/bin/awk
/usr/bin/date
/usr/bin/echo
/usr/bin/hostname
/usr/bin/cat
/usr/bin/mail
crontab的配置文件显示/usr/bin/和/usr/sbin/两个路径都包括,但是实际测试中nft不加绝对路径在crontab里无法运行,个人认为很有可能是lastb后面的管道或者awk里的语句块的问题,还是不能图省事,老老实实都加上绝对路径,程序容错率高
[root@RHEL8 ~]# cat /etc/crontab
SHELL=/bin/bash
PATH=/sbin:/bin:/usr/sbin:/usr/bin
MAILTO=root
# For details see man 4 crontabs
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
[root@RHEL8 ~]# cat awknftban.sh
#awkban.sh
#Date: 2024-11-11
#!/bin/bash
#写入计划任务
#1.自动拉黑每小时登录失败超过指定次数的IP
rulefile='/etc/nftables/rhel8.nft'
cat << EOF >> /var/spool/cron/root
0 * * * * /usr/bin/lastb | /usr/bin/awk -v hourago="\$(/usr/bin/date --date='1 hour ago' '+\%a \%b \%e \%H:')" '\$0~hourago{ip[\$3]++}END{for (i in ip){if(ip[i]>11){system("/usr/sbin/nft insert rule inet NFT_FILTER NFC_INPUT handle 5 iifname enp1s0 ip saddr "i" reject;/usr/sbin/nft -a list ruleset >| ${rulefile};/usr/bin/echo \"\$(/usr/bin/hostname) ban "i" for connected "ip[i]" times in 1 hour\" >> /tmp/baninfo")}}}';[ -e /tmp/baninfo ] && /usr/bin/cat /tmp/baninfo | /usr/bin/mail -s "Ban Info" XXXXX@XX.com && /usr/bin/rm -f /tmp/baninfo
EOF
[root@RHEL8 ~]# sh awknftban.sh
[root@RHEL8 ~]# crontab -l
0 * * * * /usr/bin/lastb | /usr/bin/awk -v hourago="$(/usr/bin/date --date='1 hour ago' '+\%a \%b \%e \%H:')" '$0~hourago{ip[$3]++}END{for (i in ip){if(ip[i]>11){system("/usr/sbin/nft insert rule inet NFT_FILTER NFC_INPUT handle 5 iifname enp1s0 ip saddr "i" reject;/usr/sbin/nft -a list ruleset >| /etc/nftables/rhel8.nft;/usr/bin/echo \"$(/usr/bin/hostname) ban "i" for connected "ip[i]" times in 1 hour\" >> /tmp/baninfo")}}}';[ -e /tmp/baninfo ] && /usr/bin/cat /tmp/baninfo | /usr/bin/mail -s "Ban Info" XXXXX@XX.com && /usr/bin/rm -f /tmp/baninfo
- 注意事项
RHEL9最小化安装没有mail指令,发件前请确认主机安装mail - 不足之处
通过mail发送需要设置.mailrc文件,QQ邮箱需要加密我没设置好,163邮箱不需加密目前我在用,但是认证码半年到期就要换一次。我用的.mailrc配置文件在CentOS7上正常,在RHEL9上提示快过时了,需要用新的语法,设置.mailrc的方法暂时不写了,有时间再好好研究。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号