deepin部署openldap服务
本文操作在deepin20.2.2发行版,最后更新时间2021-07-04
1. 背景概述
笔者在deepin上通过kvm创建了很多虚拟机(centos),为了使这些虚拟机能够实现全局认证,需要部署openldap服务。之前我是在centos里面部署openldap-server,这次直接在deepin上部署。
2. 服务端部署过程
第一步
在deepin上执行:sudo apt update && sudo apt install slapd ldap-utils
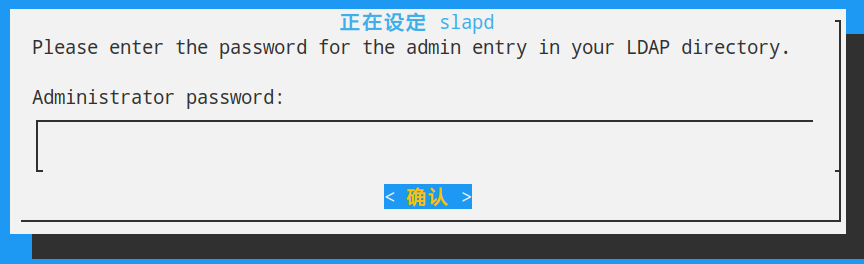
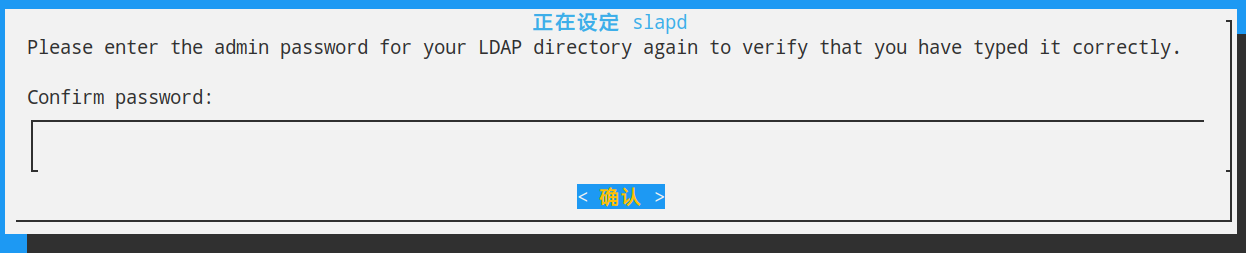
接下来按照如图操作,下面两个对话框,输入相同的密码。
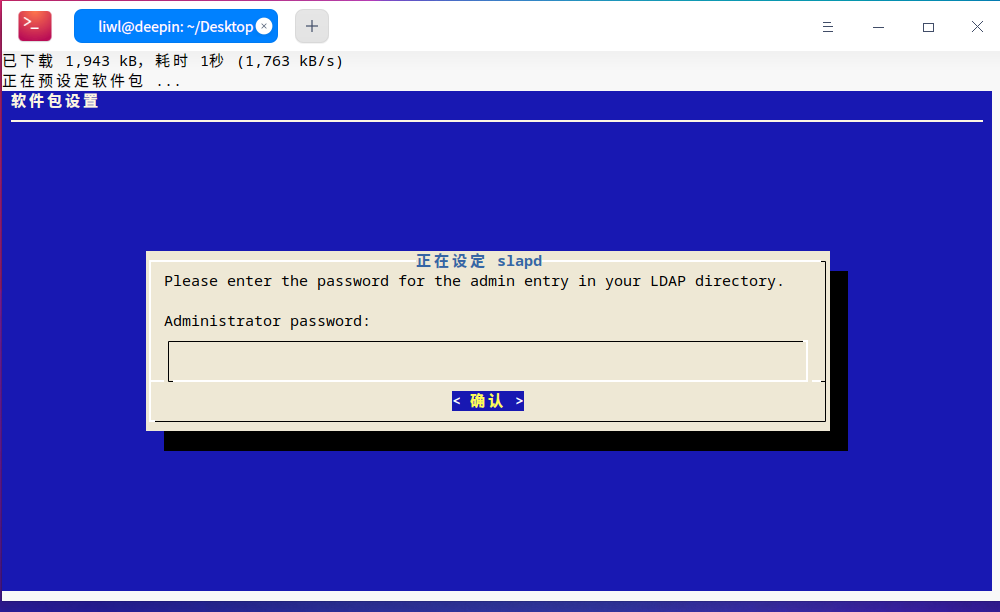
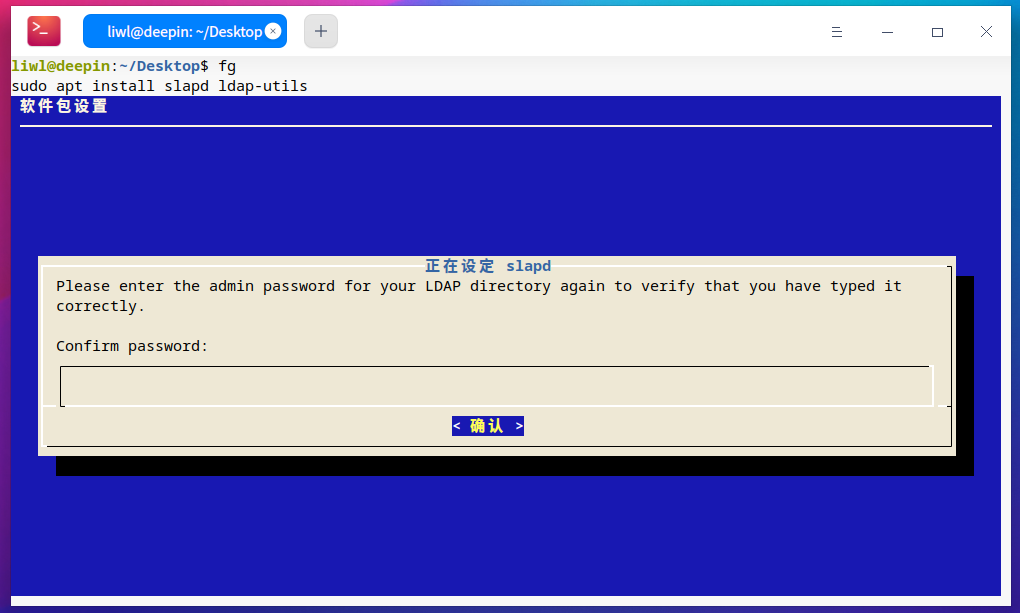
第二步
vim /etc/ldap/ldap.conf
#
# LDAP Defaults
#
# See ldap.conf(5) for details
# This file should be world readable but not world writable.
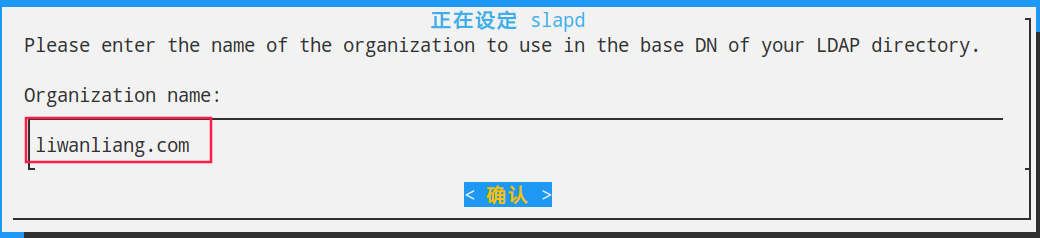
BASE dc=liwanliang,dc=com
URI ldap://192.168.80.99
#SIZELIMIT 12
#TIMELIMIT 15
#DEREF never
# TLS certificates (needed for GnuTLS)
TLS_CACERT /etc/ssl/certs/ca-certificates.crt
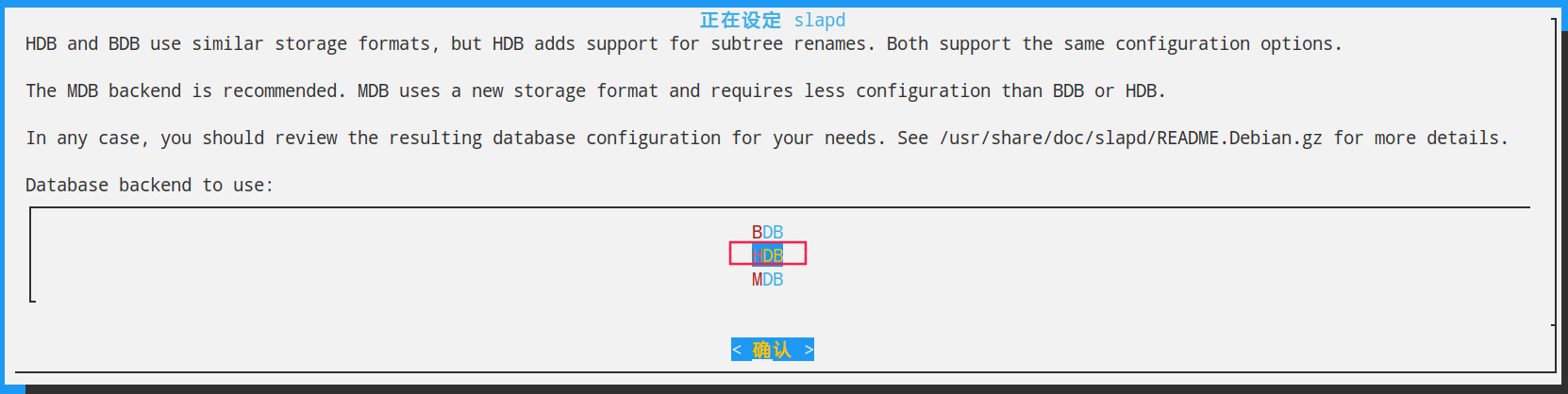
第三歩
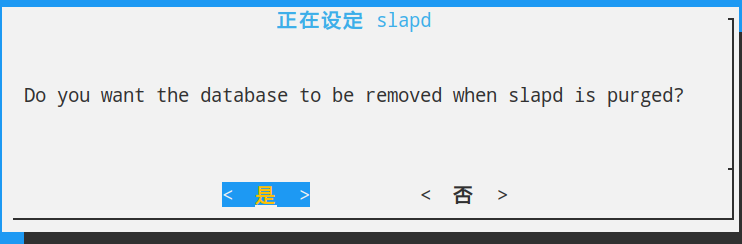
执行:dpkg-reconfigure slapd
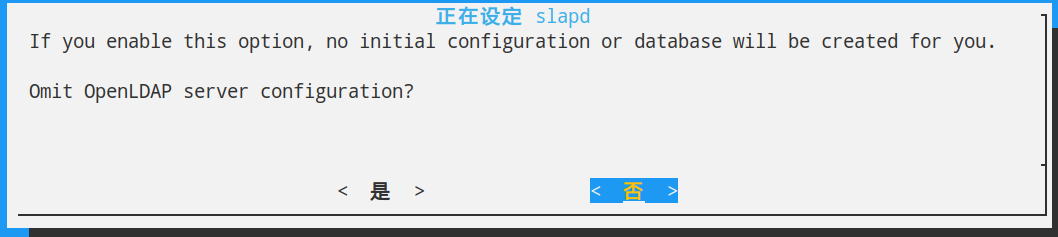
选择否

第四步
执行命令:ldapsearch -x
# extended LDIF
#
# LDAPv3
# base <dc=liwanliang,dc=com> (default) with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# liwanliang.com
dn: dc=liwanliang,dc=com
objectClass: top
objectClass: dcObject
objectClass: organization
o: liwanliang.com
dc: liwanliang
# admin, liwanliang.com
dn: cn=admin,dc=liwanliang,dc=com
objectClass: simpleSecurityObject
objectClass: organizationalRole
cn: admin
description: LDAP administrator
# search result
search: 2
result: 0 Success
# numResponses: 3
# numEntries: 2
第五步
创建base.ldif
dn: ou=People,dc=liwanliang,dc=com
objectClass: organizationalUnit
ou: People
dn: ou=Group,dc=liwanliang,dc=com
objectClass: organizationalRole
cn: Group
添加base.ldif
root@deepin:~# ldapadd -x -D "cn=admin,dc=liwanliang,dc=com" -W -f base.ldif
Enter LDAP Password:
adding new entry "ou=People,dc=liwanliang,dc=com"
adding new entry "ou=Group,dc=liwanliang,dc=com"
root@deepin:~# cat base.ldif
第六步
创建用户与组:
dn: uid=liwl02,ou=People,dc=liwanliang,dc=com
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: shadowAccount
uid: liwl02
cn: liwl02
sn: liwl02
userPassword: {SSHA}Y9cnuD5NupEu8Bnf6VYMjVJuDfUsSnqt
uidNumber: 1102
gidNumber: 1102
loginShell: /bin/bash
homeDirectory: /home/liwl02
dn: cn=liwl02,ou=Group,dc=liwanliang,dc=com
objectClass: posixGroup
cn: liwl02
gidNumber: 1102
memberUid: liwl02
添加
root@deepin:~# ldapadd -H ldap://192.168.80.99 -x -D cn=admin,dc=liwanliang,dc=com -W -f user_group.ldif
Enter LDAP Password:
adding new entry "uid=liwl02,ou=People,dc=liwanliang,dc=com"
adding new entry "cn=liwl02,ou=Group,dc=liwanliang,dc=com"
3. 客户端
客户端是centos操作系统,首先安装:yum -y install sssd
然后创建/etc/sssd/sssd.conf配置文件,内容如下,注意文件权限修改为600,属主为root
[root@node14 ~]# cat /etc/sssd/sssd.conf
[sssd]
config_file_version = 2
services = nss, pam, autofs
domains = default
[nss]
filter_users = root,ldap
[pam]
[domain/default]
auth_provider = ldap
id_provider = ldap
chpass_provider = ldap
ldap_uri = ldap://192.168.80.99/
ldap_search_base = dc=liwanliang,dc=com
ldap_tls_reqcert = never
ldap_id_use_start_tls = False
ldap_tls_cacertdir = /etc/openldap/cacerts
cache_credentials = False
entry_cache_timeout = 60
ldap_network_timeout = 3
autofs_provider = ldap
[autofs]
最后启动sssd服务,service sssd start
执行验证:
[root@node14 ~]# id liwl01
uid=1101(liwl01) gid=1101(liwl01) 组=1101(liwl01)
[root@node14 ~]# id liwl02
uid=1102(liwl02) gid=1102(liwl02) 组=1102(liwl02)
[root@node14 ~]#


 浙公网安备 33010602011771号
浙公网安备 33010602011771号