Semgrep体验
检查硬编码
规则
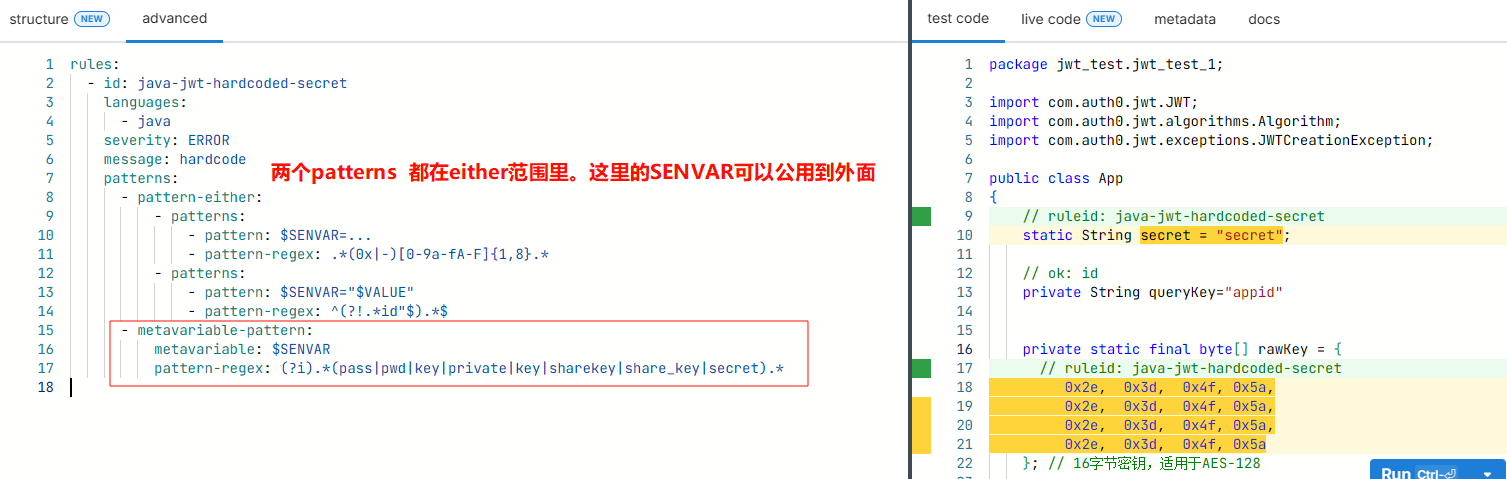
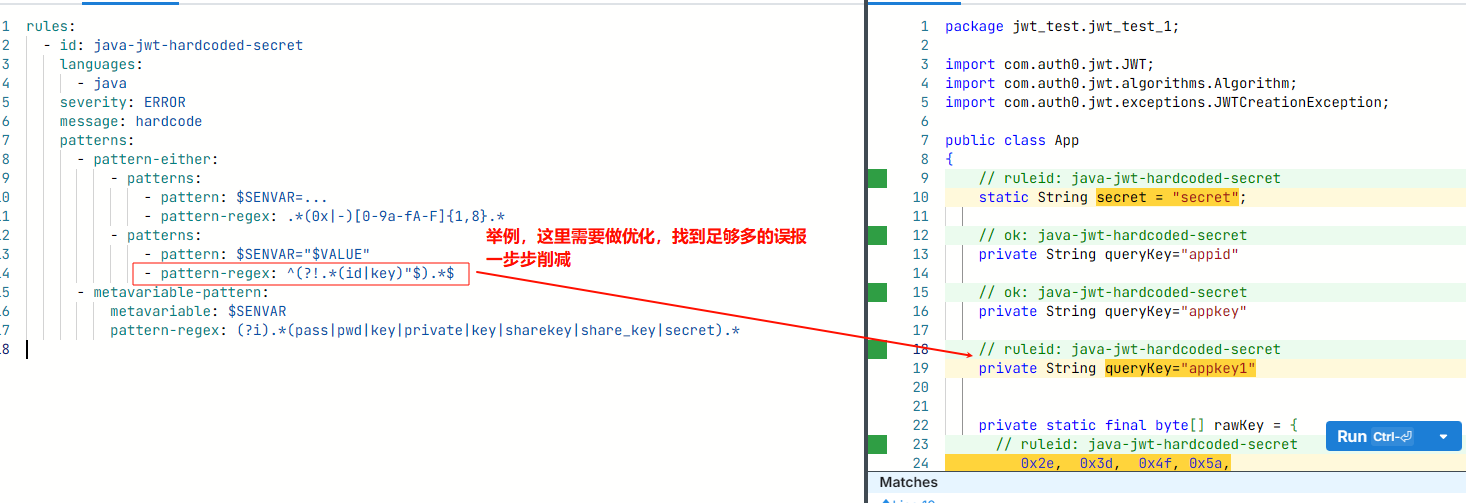
rules:
- id: java-jwt-hardcoded-secret
languages:
- java
severity: ERROR
message: hardcode
patterns:
- pattern-either:
- patterns:
- pattern: $SENVAR=...
- pattern-regex: .*(0x|-)[0-9a-fA-F]{1,8}.*
- patterns:
- pattern: $SENVAR="$VALUE"
# 这里用正则去掉A="" 格式中的 以id"结尾的,比如queryKey="appid"有一些表示id或者一些xxxKey的
- pattern-regex: ^(?!.*id"$).*$
- metavariable-pattern:
metavariable: $SENVAR
pattern-regex: (?i).*(pass|pwd|key|private|key|sharekey|share_key|secret).*
实验代码
package jwt_test.jwt_test_1;
import com.auth0.jwt.JWT;
import com.auth0.jwt.algorithms.Algorithm;
import com.auth0.jwt.exceptions.JWTCreationException;
public class App
{
// ruleid: java-jwt-hardcoded-secret
static String secret = "secret";
// ok: id
private String queryKey="appid"
private static final byte[] rawKey = {
// ruleid: java-jwt-hardcoded-secret
0x2e, 0x3d, 0x4f, 0x5a,
0x2e, 0x3d, 0x4f, 0x5a,
0x2e, 0x3d, 0x4f, 0x5a,
0x2e, 0x3d, 0x4f, 0x5a
}; // 16字节密钥,适用于AES-128
private static void bad1() {
try {
// ruleid: java-jwt-hardcoded-secret
String password="Liu123456"
Algorithm algorithm = Algorithm.HMAC256("secret");
String token = JWT.create()
.withIssuer("auth0")
.sign(algorithm);
name="LYB"
} catch (JWTCreationException exception){
//Invalid Signing configuration / Couldn't convert Claims.
}
}
private static void ok1(String secretKey) {
try {
// ok: java-jwt-hardcoded-secret
Algorithm algorithm = Algorithm.HMAC256(secretKey);
String token = JWT.create()
.withIssuer("auth0")
.sign(algorithm);
} catch (JWTCreationException exception){
//Invalid Signing configuration / Couldn't convert Claims.
}
}
public static void main( String[] args )
{
bad1();
ok1(args[0]);
}
}
abstract class App2
{
// ruleid: java-jwt-hardcoded-secret
static String secret = "secret";
public void bad2() {
try {
Algorithm algorithm = Algorithm.HMAC256(secret);
String token = JWT.create()
.withIssuer("auth0")
.sign(algorithm);
} catch (JWTCreationException exception){
//Invalid Signing configuration / Couldn't convert Claims.
}
}
}
优化:
日志打印
规则
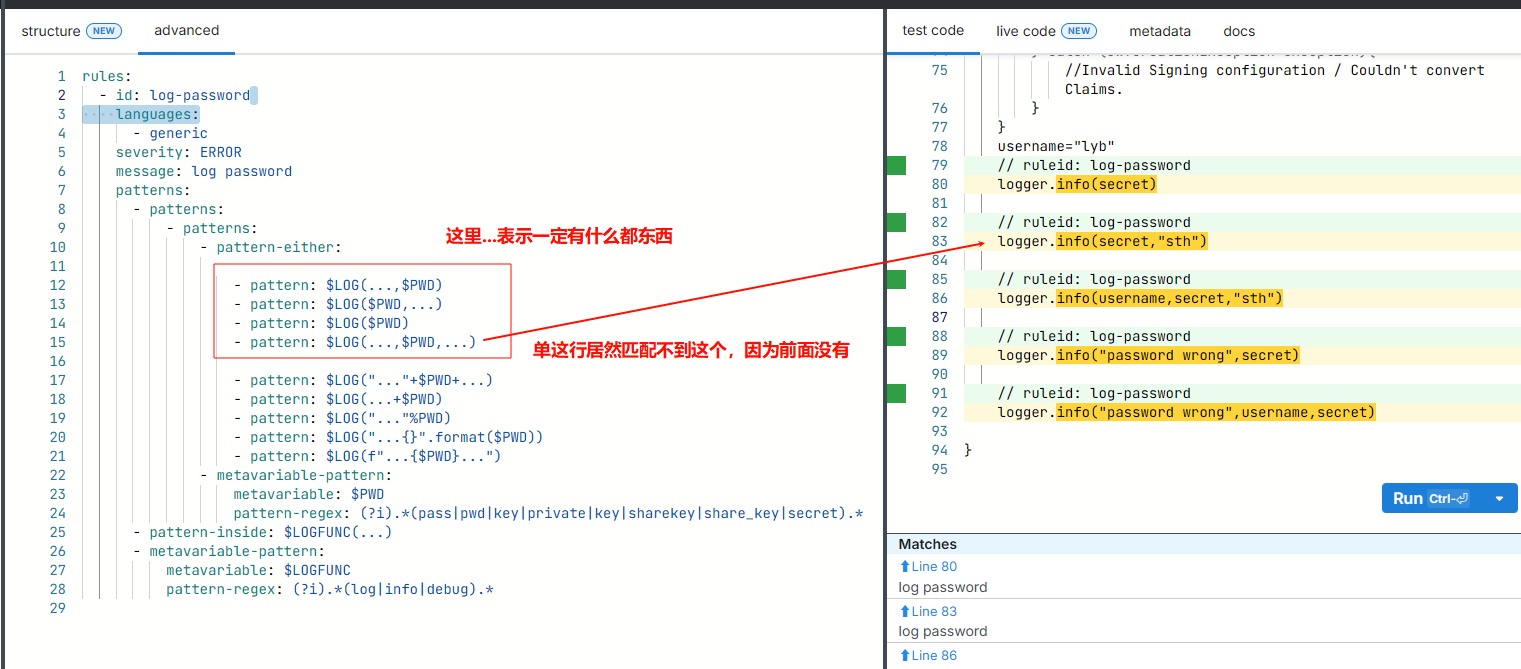
rules:
- id: log-password
languages:
- generic
severity: ERROR
message: log password
patterns:
- patterns:
- patterns:
- pattern-either:
- pattern: $LOG(...,$PWD)
- pattern: $LOG($PWD,...)
- pattern: $LOG($PWD)
- pattern: $LOG(...,$PWD,...)
- pattern: $LOG("..."+$PWD+...)
- pattern: $LOG(...+$PWD)
- pattern: $LOG("..."%PWD)
- pattern: $LOG("...{}".format($PWD))
- pattern: $LOG(f"...{$PWD}...")
- metavariable-pattern:
metavariable: $PWD
pattern-regex: (?i).*(pass|pwd|key|private|key|sharekey|share_key|secret).*
- pattern-inside: $LOGFUNC(...)
- metavariable-pattern:
metavariable: $LOGFUNC
pattern-regex: (?i).*(log|info|debug).*
测试代码
abstract class App2
{
// ruleid: java-jwt-hardcoded-secret
static String secret = "secret";
public void bad2() {
try {
Algorithm algorithm = Algorithm.HMAC256(secret);
String token = JWT.create()
.withIssuer("auth0")
.sign(algorithm);
} catch (JWTCreationException exception){
//Invalid Signing configuration / Couldn't convert Claims.
}
}
username="lyb"
// ruleid: log-password
logger.info(secret)
// ruleid: log-password
logger.info(secret,"sth")
// ruleid: log-password
logger.info(username,secret,"sth")
// ruleid: log-password
logger.info("password wrong",secret)
// ruleid: log-password
logger.info("password wrong",username,secret)
}
PBKDF2
规则
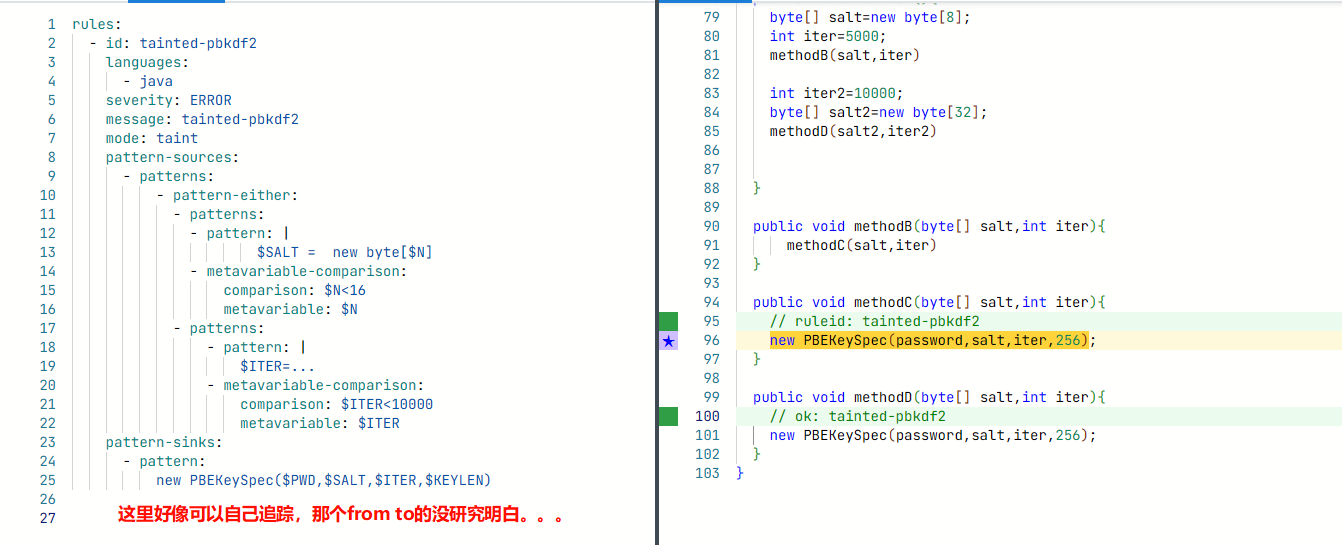
rules:
- id: tainted-pbkdf2
languages:
- java
severity: ERROR
message: tainted-pbkdf2
mode: taint
pattern-sources:
- patterns:
- pattern-either:
- patterns:
- pattern: |
$SALT = new byte[$N]
- metavariable-comparison:
comparison: $N<16
metavariable: $N
- patterns:
- pattern: |
$ITER=...
- metavariable-comparison:
comparison: $ITER<10000
metavariable: $ITER
pattern-sinks:
- pattern:
new PBEKeySpec($PWD,$SALT,$ITER,$KEYLEN)
测试代码
public void methodA(){
byte[] salt=new byte[8];
int iter=5000;
methodB(salt,iter)
int iter2=10000;
byte[] salt2=new byte[32];
methodD(salt2,iter2)
}
public void methodB(byte[] salt,int iter){
methodC(salt,iter)
}
public void methodC(byte[] salt,int iter){
// ruleid: tainted-pbkdf2
new PBEKeySpec(password,salt,iter,256);
}
public void methodD(byte[] salt,int iter){
// ok: tainted-pbkdf2
new PBEKeySpec(password,salt,iter,256);
}
实际可能更复杂一些,而且不同代码类型也不一样。。。
走自己的路


 浙公网安备 33010602011771号
浙公网安备 33010602011771号