nmap
在线端口检测网站
扫描某一段地址里面是否开了80 端口
nmap -p 80,443 120.11.48.0/28
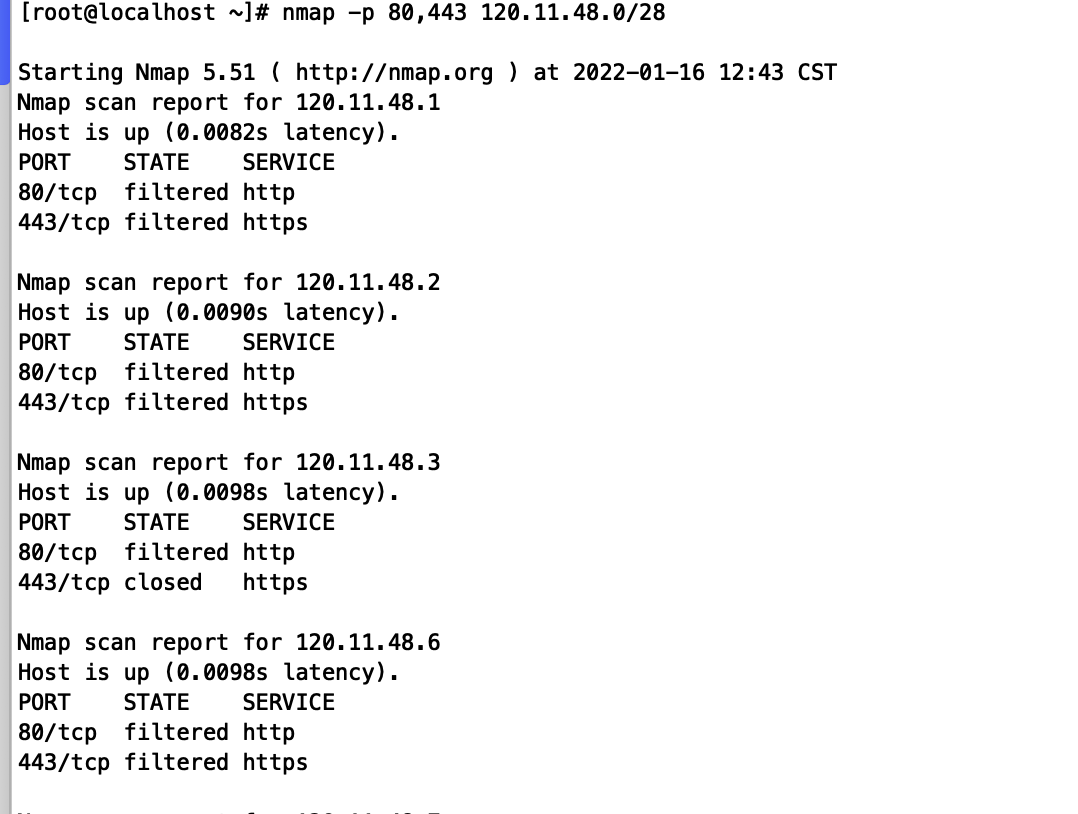
nmap -p 1000-1100 120.11.48.0/28
nmap -p- 3.5.6.7 #对所有端口进行探测
扫描某一个地址开了哪些端口
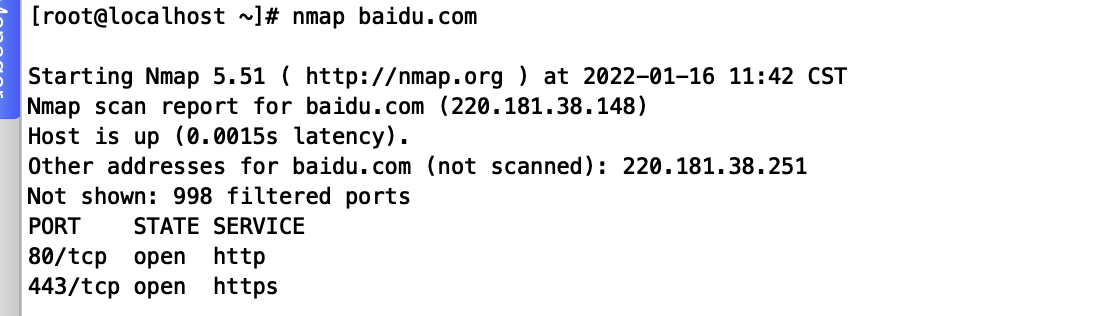
nmap baidu.com
指定dns服务器
nmap --dns-servers 114.114.114.114 baidu.com
指定协议进行探测
nmap -p -T:25 U:53 scanme.nmap.org
nmap -p smtp scanme.nmap.org
nmap -p s* scanme.nmap.org #扫描协议名称以s开头的所有协议
nmap -p [1-65535] scanme.nmap.org # 扫描注册在nmap中的端口
-Pn
对于已经知道存活或防火墙开启的机器,可以通过使用-Pn 来停止探测之前使用的ICMP请求,达到不解发防火墙的安全机制
nmap -Pn baidu.com
nmap -O $ip
端口状态

nmap -h
nmap 扫描技术
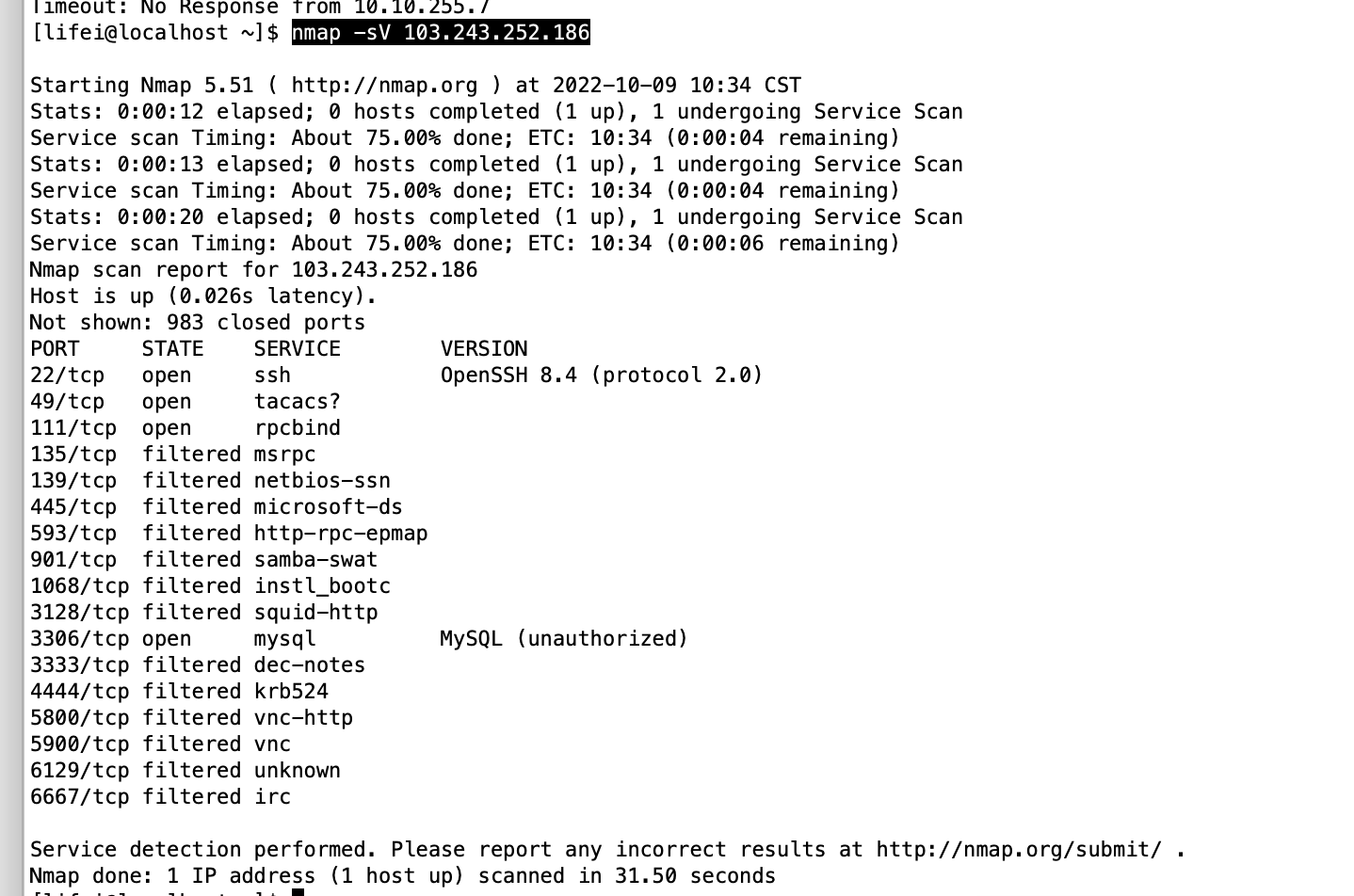
服务指纹

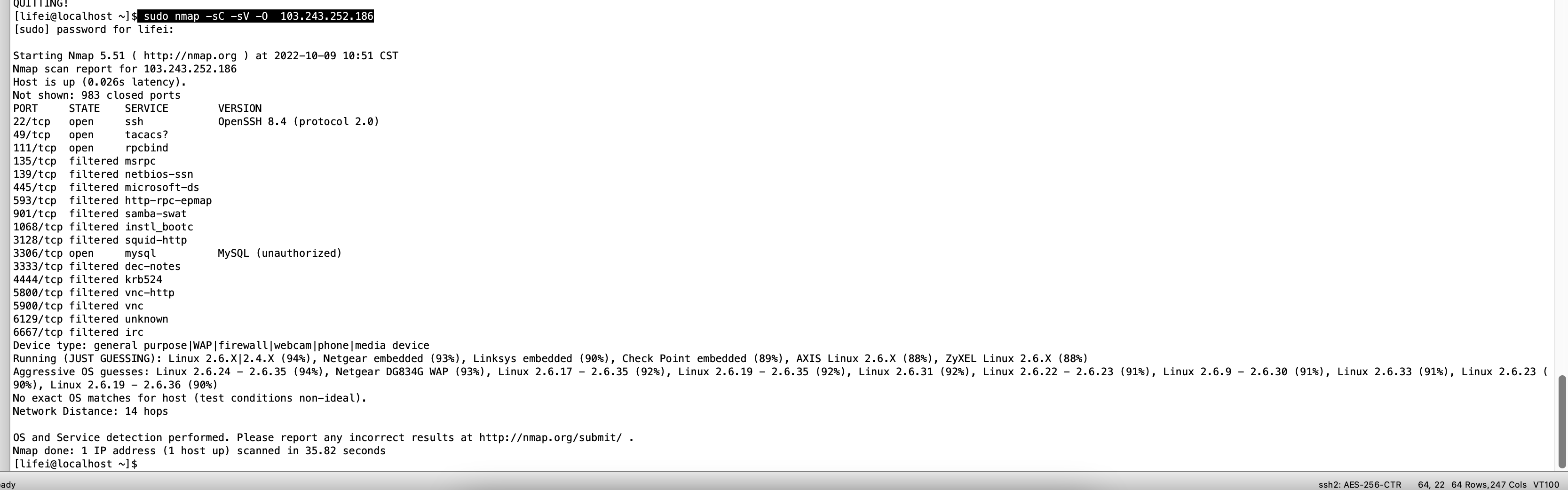
nmap -sV 103.243.252.186
侵略性探测
nmap -A -v -T4 103.243.252.186
[lifei@localhost ~]$ sudo nmap -A -v -T4 103.243.252.186
Starting Nmap 5.51 ( http://nmap.org ) at 2022-10-09 10:53 CST
NSE: Loaded 57 scripts for scanning.
Initiating Ping Scan at 10:53
Scanning 103.243.252.186 [4 ports]
Completed Ping Scan at 10:53, 0.05s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 10:53
Completed Parallel DNS resolution of 1 host. at 10:53, 0.03s elapsed
Initiating SYN Stealth Scan at 10:53
Scanning 103.243.252.186 [1000 ports]
Discovered open port 3306/tcp on 103.243.252.186
Discovered open port 111/tcp on 103.243.252.186
Discovered open port 22/tcp on 103.243.252.186
Discovered open port 49/tcp on 103.243.252.186
Completed SYN Stealth Scan at 10:53, 1.68s elapsed (1000 total ports)
Initiating Service scan at 10:53
Scanning 4 services on 103.243.252.186
Completed Service scan at 10:54, 29.57s elapsed (4 services on 1 host)
Initiating RPCGrind Scan against 103.243.252.186 at 10:54
Completed RPCGrind Scan against 103.243.252.186 at 10:54, 0.05s elapsed (1 port)
Initiating OS detection (try #1) against 103.243.252.186
Retrying OS detection (try #2) against 103.243.252.186
Initiating Traceroute at 10:54
Completed Traceroute at 10:54, 3.02s elapsed
Initiating Parallel DNS resolution of 13 hosts. at 10:54
Completed Parallel DNS resolution of 13 hosts. at 10:54, 0.51s elapsed
NSE: Script scanning 103.243.252.186.
Initiating NSE at 10:54
Completed NSE at 10:54, 0.30s elapsed
Nmap scan report for 103.243.252.186
Host is up (0.026s latency).
Not shown: 983 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4 (protocol 2.0)
49/tcp open tacacs?
111/tcp open rpcbind
135/tcp filtered msrpc
139/tcp filtered netbios-ssn
445/tcp filtered microsoft-ds
593/tcp filtered http-rpc-epmap
901/tcp filtered samba-swat
1068/tcp filtered instl_bootc
3128/tcp filtered squid-http
3306/tcp open mysql MySQL (unauthorized)
3333/tcp filtered dec-notes
4444/tcp filtered krb524
5800/tcp filtered vnc-http
5900/tcp filtered vnc
6129/tcp filtered unknown
6667/tcp filtered irc
Device type: general purpose|WAP|firewall|webcam|phone|media device
Running (JUST GUESSING): Linux 2.6.X|2.4.X (94%), Netgear embedded (93%), Linksys embedded (90%), Check Point embedded (89%), AXIS Linux 2.6.X (88%), ZyXEL Linux 2.6.X (88%)
Aggressive OS guesses: Linux 2.6.24 - 2.6.35 (94%), Netgear DG834G WAP (93%), Linux 2.6.17 - 2.6.35 (92%), Linux 2.6.19 - 2.6.35 (92%), Linux 2.6.31 (92%), Linux 2.6.22 - 2.6.23 (91%), Linux 2.6.9 - 2.6.30 (91%), Linux 2.6.33 (91%), Linux 2.6.23 (90%), Linux 2.6.19 - 2.6.36 (90%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 10.280 days (since Thu Sep 29 04:11:25 2022)
Network Distance: 15 hops
TCP Sequence Prediction: Difficulty=255 (Good luck!)
IP ID Sequence Generation: All zeros
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 4.38 ms 103.227.80.129
2 0.67 ms 10.10.10.81
3 2.41 ms 61.48.49.118
4 2.60 ms 61.48.49.117
5 2.57 ms 61.148.146.21
6 3.60 ms 61.51.169.97
7 2.60 ms 125.33.186.249
8 ...
9 22.97 ms 139.226.231.102
10 23.21 ms 139.226.203.6
11 34.79 ms 112.65.207.34
12 27.20 ms 112.65.35.62
13 25.16 ms 101.227.182.255
14 ...
15 26.08 ms 103.243.252.186
Read data files from: /usr/share/nmap
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 39.49 seconds
Raw packets sent: 1081 (48.960KB) | Rcvd: 1215 (53.728KB)
sudo nmap -sC -sV -O 103.243.252.186
------------恢复内容开始------------
在线端口检测网站
udp 端口扫描
nmap -sU -p 123 118.194.165.0/24
扫描某一段地址里面是否开了80 端口
nmap -p 80,443 120.11.48.0/28

nmap -p 1000-1100 120.11.48.0/28
扫描某一个地址开了哪些端口
nmap baidu.com

指定dns服务器
nmap --dns-servers 114.114.114.114 baidu.com
-Pn
对于已经知道存活或防火墙开启的机器,可以通过使用-Pn 来停止探测之前使用的ICMP请求,达到不解发防火墙的安全机制
nmap -Pn baidu.com
nmap -O $ip
端口状态

nmap -h
nmap 扫描技术

服务指纹

nmap -sV 103.243.252.186

侵略性探测
nmap -A -v -T4 103.243.252.186
[lifei@localhost ~]$ sudo nmap -A -v -T4 103.243.252.186
Starting Nmap 5.51 ( http://nmap.org ) at 2022-10-09 10:53 CST
NSE: Loaded 57 scripts for scanning.
Initiating Ping Scan at 10:53
Scanning 103.243.252.186 [4 ports]
Completed Ping Scan at 10:53, 0.05s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 10:53
Completed Parallel DNS resolution of 1 host. at 10:53, 0.03s elapsed
Initiating SYN Stealth Scan at 10:53
Scanning 103.243.252.186 [1000 ports]
Discovered open port 3306/tcp on 103.243.252.186
Discovered open port 111/tcp on 103.243.252.186
Discovered open port 22/tcp on 103.243.252.186
Discovered open port 49/tcp on 103.243.252.186
Completed SYN Stealth Scan at 10:53, 1.68s elapsed (1000 total ports)
Initiating Service scan at 10:53
Scanning 4 services on 103.243.252.186
Completed Service scan at 10:54, 29.57s elapsed (4 services on 1 host)
Initiating RPCGrind Scan against 103.243.252.186 at 10:54
Completed RPCGrind Scan against 103.243.252.186 at 10:54, 0.05s elapsed (1 port)
Initiating OS detection (try #1) against 103.243.252.186
Retrying OS detection (try #2) against 103.243.252.186
Initiating Traceroute at 10:54
Completed Traceroute at 10:54, 3.02s elapsed
Initiating Parallel DNS resolution of 13 hosts. at 10:54
Completed Parallel DNS resolution of 13 hosts. at 10:54, 0.51s elapsed
NSE: Script scanning 103.243.252.186.
Initiating NSE at 10:54
Completed NSE at 10:54, 0.30s elapsed
Nmap scan report for 103.243.252.186
Host is up (0.026s latency).
Not shown: 983 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4 (protocol 2.0)
49/tcp open tacacs?
111/tcp open rpcbind
135/tcp filtered msrpc
139/tcp filtered netbios-ssn
445/tcp filtered microsoft-ds
593/tcp filtered http-rpc-epmap
901/tcp filtered samba-swat
1068/tcp filtered instl_bootc
3128/tcp filtered squid-http
3306/tcp open mysql MySQL (unauthorized)
3333/tcp filtered dec-notes
4444/tcp filtered krb524
5800/tcp filtered vnc-http
5900/tcp filtered vnc
6129/tcp filtered unknown
6667/tcp filtered irc
Device type: general purpose|WAP|firewall|webcam|phone|media device
Running (JUST GUESSING): Linux 2.6.X|2.4.X (94%), Netgear embedded (93%), Linksys embedded (90%), Check Point embedded (89%), AXIS Linux 2.6.X (88%), ZyXEL Linux 2.6.X (88%)
Aggressive OS guesses: Linux 2.6.24 - 2.6.35 (94%), Netgear DG834G WAP (93%), Linux 2.6.17 - 2.6.35 (92%), Linux 2.6.19 - 2.6.35 (92%), Linux 2.6.31 (92%), Linux 2.6.22 - 2.6.23 (91%), Linux 2.6.9 - 2.6.30 (91%), Linux 2.6.33 (91%), Linux 2.6.23 (90%), Linux 2.6.19 - 2.6.36 (90%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 10.280 days (since Thu Sep 29 04:11:25 2022)
Network Distance: 15 hops
TCP Sequence Prediction: Difficulty=255 (Good luck!)
IP ID Sequence Generation: All zeros
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 4.38 ms 103.227.80.129
2 0.67 ms 10.10.10.81
3 2.41 ms 61.48.49.118
4 2.60 ms 61.48.49.117
5 2.57 ms 61.148.146.21
6 3.60 ms 61.51.169.97
7 2.60 ms 125.33.186.249
8 ...
9 22.97 ms 139.226.231.102
10 23.21 ms 139.226.203.6
11 34.79 ms 112.65.207.34
12 27.20 ms 112.65.35.62
13 25.16 ms 101.227.182.255
14 ...
15 26.08 ms 103.243.252.186
Read data files from: /usr/share/nmap
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 39.49 seconds
Raw packets sent: 1081 (48.960KB) | Rcvd: 1215 (53.728KB)
sudo nmap -sC -sV -O 103.243.252.186


nmap 主机发现
sudo nmap -sP 103.243.252.184/30
sudo nmap -sn 103.243.252.184/30
导入到xml 格式文件
sudo nmap -sn 103.243.252.128/25 -oX aa.xml
NSE脚本
介绍
NSE(NMAP Script Engine) Nmap脚本引擎,内置很多可以用来扫描的、针对特定任务的脚本。通过NSE不断扩展NMAP的扫描策略,加强Nmap的功能
Nmap 中使用--script 来指定调用的脚本,并且存储在nmap安装路径下的script文件夹下,对于kali linux存储在/usr/share/nmap/script 文件夹下
使用
- 使用nmap 探测web服务的标题,-nmap-script 脚本名称,目标
nmap --script http-title www.baidu.com
nmap 分类的使用
对于目标使用多个分类脚本进行探测,可以更快地找到目标的信息及弱点 ,使用的命令如下
nmap -sV --script vuln 目标
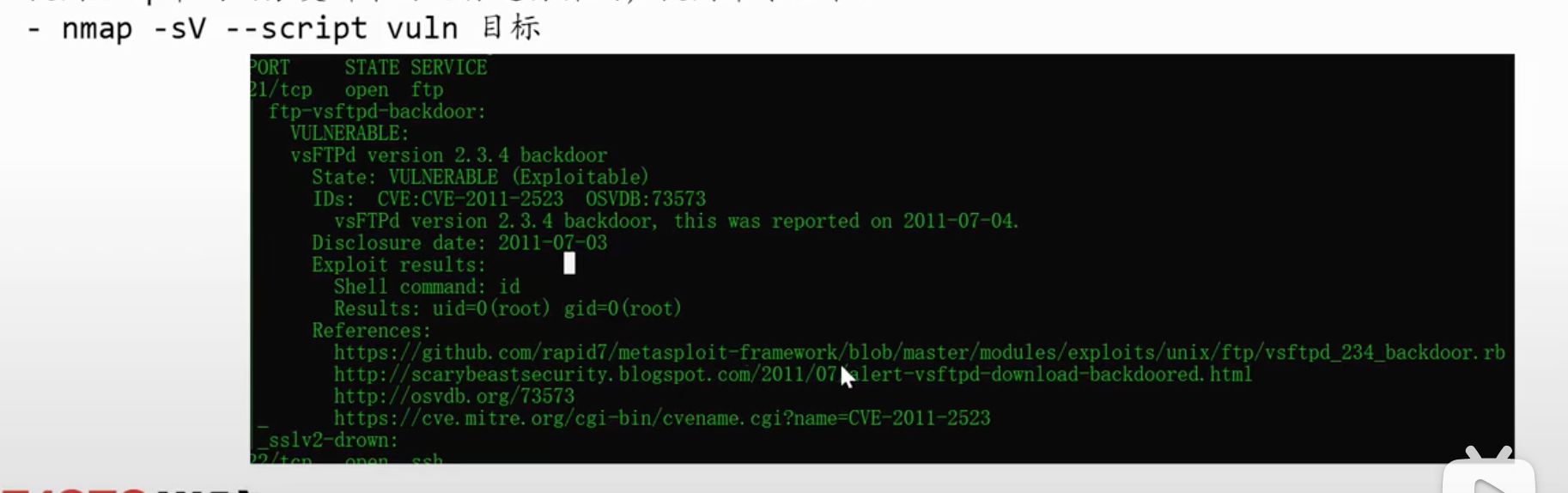
使用nmap中发现和版本信息分类进行探测,使用命令如下
nmap -sV --script="version,discovery" 目标
nmap -sV --script="not exploit" 目标
NES分类使用
使用NMAP中http脚本,但是除了(http-broute 和http-slowlors)的命令如下
nmap -sV --script="(http) and not (http-broute and http-broute)" 目标
NES 调试功能的使用
使用NMAP中的expoit,但是在使用的同时开启调试模式。使用命令如下
nmap -sV --script exploit -d 3 --script-trace 目标
注意 -d (debug 范围0-9)
NES 参数的使用
使用nmap的http-title 脚本,并且指定使用对应的User-Agent.命令如下
nmap -sV --script http-title --script-args http.user-agent="Mozilla 999"
NES更新
nmap --script-updatedb
NSE参考链接
nmap指定特定网卡进行探测
nmap提供了切换使用特定网卡进行探测的参数-e
nmap -e eth0 192.168.1.0/24



 浙公网安备 33010602011771号
浙公网安备 33010602011771号