二层防御(upx+简单逻辑)
题目:
int __fastcall main(int argc, const char **argv, const char **envp)
{
_main();
puts("Input :");
gets(str);
Check_Length();
Strlen();
sub122(x);
check();
return 0;
}
__int64 __fastcall sub122(int a1)
{
char v2; // [rsp+2Bh] [rbp-5h]
int i; // [rsp+2Ch] [rbp-4h]
for ( i = 1; a1 / 2 > i; ++i )
{
v2 = str[i];
str[i] = str[a1 - i - 1];
str[a1 - i - 1] = v2;
}
return sub133();
}
__int64 sub133(void)
{
__int64 result; // rax
int v1; // [rsp+Ch] [rbp-4h]
v1 = 1;
x1 = j;
while ( 1 )
{
result = (unsigned int)(x - 1);
if ( (_DWORD)result == v1 )
break;
str[v1] ^= x1;
--str[v1++];
}
return result;
}
__int64 check(void)
{
int i; // [rsp+2Ch] [rbp-4h]
for ( i = 0; i < x; ++i )
{
if ( flag1[i] != str[i] )
{
printf("Error!");
return 0i64;
}
}
printf(aRight);
return 1i64;
}
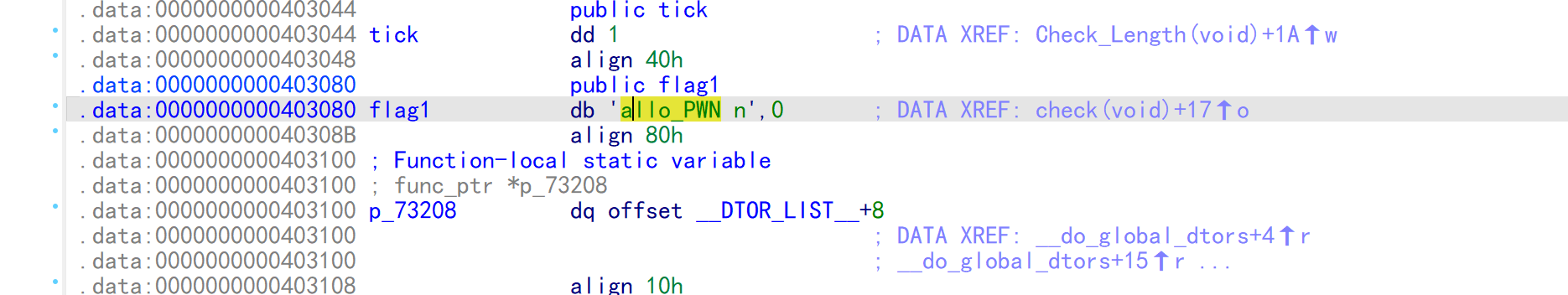
思路:
upx脱壳->flag1->逆向sub133->逆向sub122->运行测试
script:
s = "allo_PWN n"
flag = "a"
flagg = ""
for i in s[1:-1]:
# print(i)
flag += chr((ord(i) + 1) ^ 8)
flag += "n"
print(flag)
flagg = flag[0]
for i in range(len(flag) - 2, 0, -1):
flagg += flag[i]
print(flagg)
flagg += "n"
print(flagg)






 浙公网安备 33010602011771号
浙公网安备 33010602011771号