∞
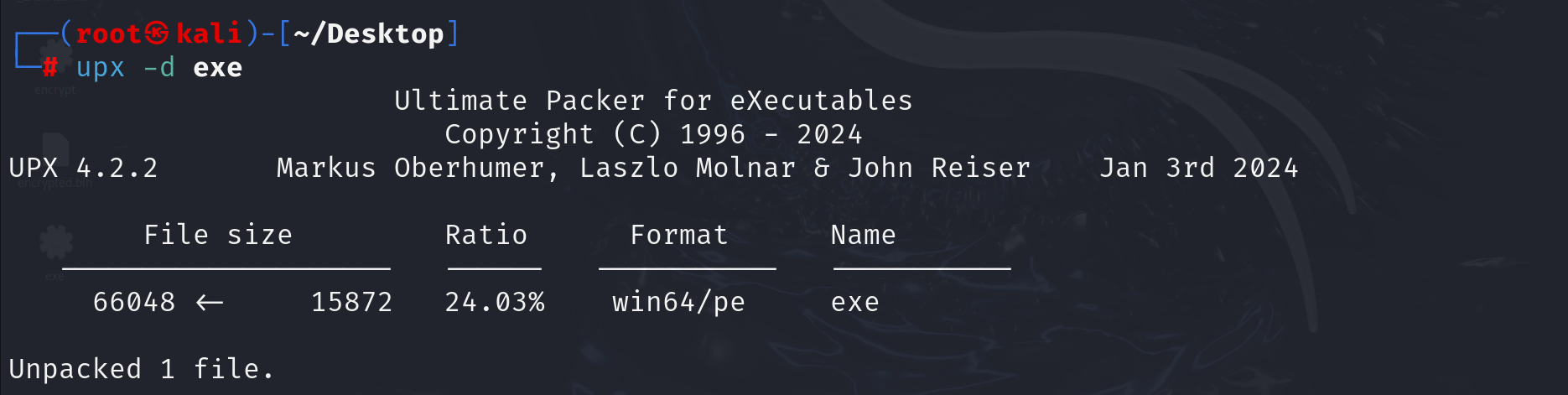
使用upx脱壳
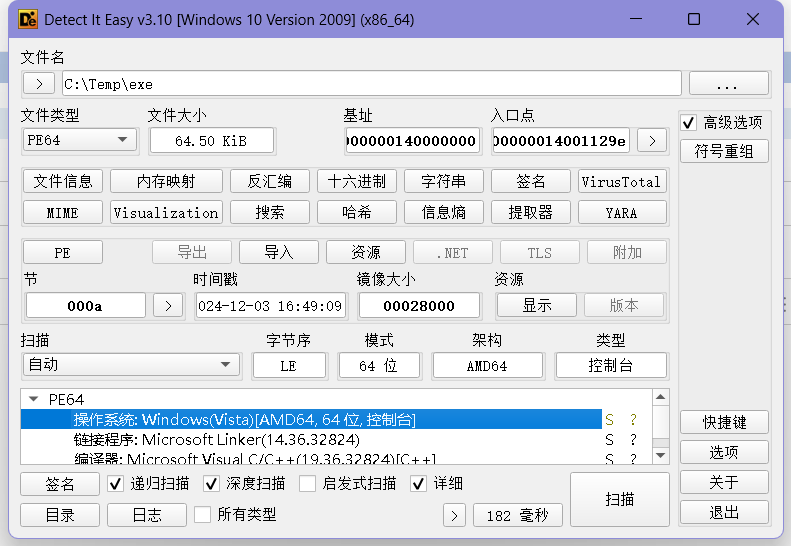
int __fastcall main_0(int argc, const char **argv, const char **envp)
{
char *v3; // rdi
__int64 i; // rcx
FILE *v5; // rax
char v7; // [rsp+20h] [rbp+0h] BYREF
char Buffer[144]; // [rsp+30h] [rbp+10h] BYREF
char Str1[132]; // [rsp+C0h] [rbp+A0h] BYREF
unsigned int v10[57]; // [rsp+144h] [rbp+124h] BYREF
size_t v11; // [rsp+228h] [rbp+208h]
v3 = &v7;
for ( i = 90i64; i; --i )
{
*(_DWORD *)v3 = -858993460;
v3 += 4;
}
j___CheckForDebuggerJustMyCode(&unk_140024014, argv, envp);
sub_1400111B3(&unk_14001ADD0);
v5 = _acrt_iob_func(0);
fgets(Buffer, 100, v5);
v11 = strcspn(Buffer, "\n");
if ( v11 >= 0x64 )
j___report_rangecheckfailure();
Buffer[v11] = 0;
sub_140011041(Buffer);
sub_1400111B3(&unk_14001ADF0);
sub_1400110A0(&unk_14001AE00, v10);
sub_140011217(Buffer, v10[0], Str1);
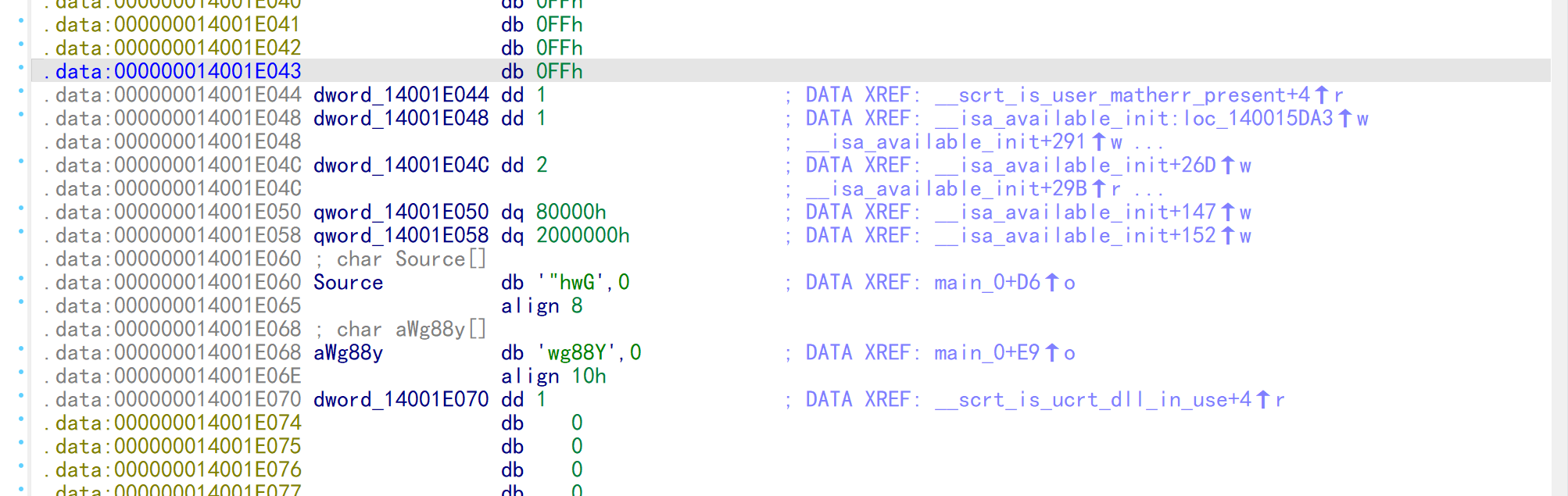
j_strcat(Str2, Source);
j_strcat(Str2, aWg88y);
if ( !j_strcmp(Str1, Str2) )
sub_1400111B3("flag!!!");
else
sub_1400111B3("nonono");
return 0;
}
__int64 __fastcall sub_140011B40(const char *a1, __int64 a2, __int64 a3)
{
__int64 result; // rax
unsigned int v4; // [rsp+24h] [rbp+4h]
int v5; // [rsp+44h] [rbp+24h]
int j; // [rsp+44h] [rbp+24h]
int i; // [rsp+64h] [rbp+44h]
char v8; // [rsp+84h] [rbp+64h]
j___CheckForDebuggerJustMyCode(&unk_140024014, a2, a3);
v4 = j_strlen(a1);
v5 = 0;
for ( i = v4 - 1; v5 < i; --i )
{
v8 = a1[v5];
a1[v5] = a1[i];
a1[i] = v8;
++v5;
}
for ( j = 0; ; ++j )
{
result = v4;
if ( j >= (int)v4 )
break;
a1[j] += j + 1;
}
return result;
}
void __fastcall sub_140011820(const char *a1, __int64 a2, __int64 a3)
{
int v3; // [rsp+24h] [rbp+4h]
_QWORD *Block; // [rsp+48h] [rbp+28h]
int i; // [rsp+64h] [rbp+44h]
int v6; // [rsp+84h] [rbp+64h]
int v7; // [rsp+A4h] [rbp+84h]
int j; // [rsp+C4h] [rbp+A4h]
int v9; // [rsp+E4h] [rbp+C4h]
int k; // [rsp+104h] [rbp+E4h]
int m; // [rsp+124h] [rbp+104h]
int n; // [rsp+144h] [rbp+124h]
int v14; // [rsp+248h] [rbp+228h]
v14 = a2;
j___CheckForDebuggerJustMyCode(&unk_140024014, a2, a3);
v3 = j_strlen(a1);
Block = malloc(saturated_mul(v14, 8ui64));
for ( i = 0; i < v14; ++i )
{
Block[i] = malloc(v3);
j_memset((void *)Block[i], 0, v3);
}
v6 = 0;
v7 = 1;
for ( j = 0; j < v3; ++j )
{
*(_BYTE *)(Block[v6] + j) = a1[j];
if ( v6 )
{
if ( v6 == v14 - 1 )
v7 = -1;
}
else
{
v7 = 1;
}
v6 += v7;
}
v9 = 0;
for ( k = 0; k < v14; ++k )
{
for ( m = 0; m < v3; ++m )
{
if ( *(_BYTE *)(Block[k] + m) )
*(_BYTE *)(a3 + v9++) = *(_BYTE *)(Block[k] + m);
}
}
*(_BYTE *)(a3 + v9) = 0;
for ( n = 0; n < v14; ++n )
free((void *)Block[n]);
free(Block);
}
script:
def dy1(x):
list = []
for j, char in enumerate(x):
offset = ord(char) - (j + 1)
offset = offset % 127
list.append(chr(offset))
decrypted_str = "".join(list)[::-1]
return decrypted_str
def dy2(x, a2):
v3 = len(x)
block = [["\0"] * v3 for _ in range(a2)]
v6 = 0
v7 = 1
for j in range(v3):
block[v6][j] = x[j]
if v6:
if v6 == a2 - 1:
v7 = -1
else:
v7 = 1
v6 += v7
flag = ""
for k in range(a2):
for m in range(v3):
if block[k][m] != "\0":
flag += block[k][m]
return flag
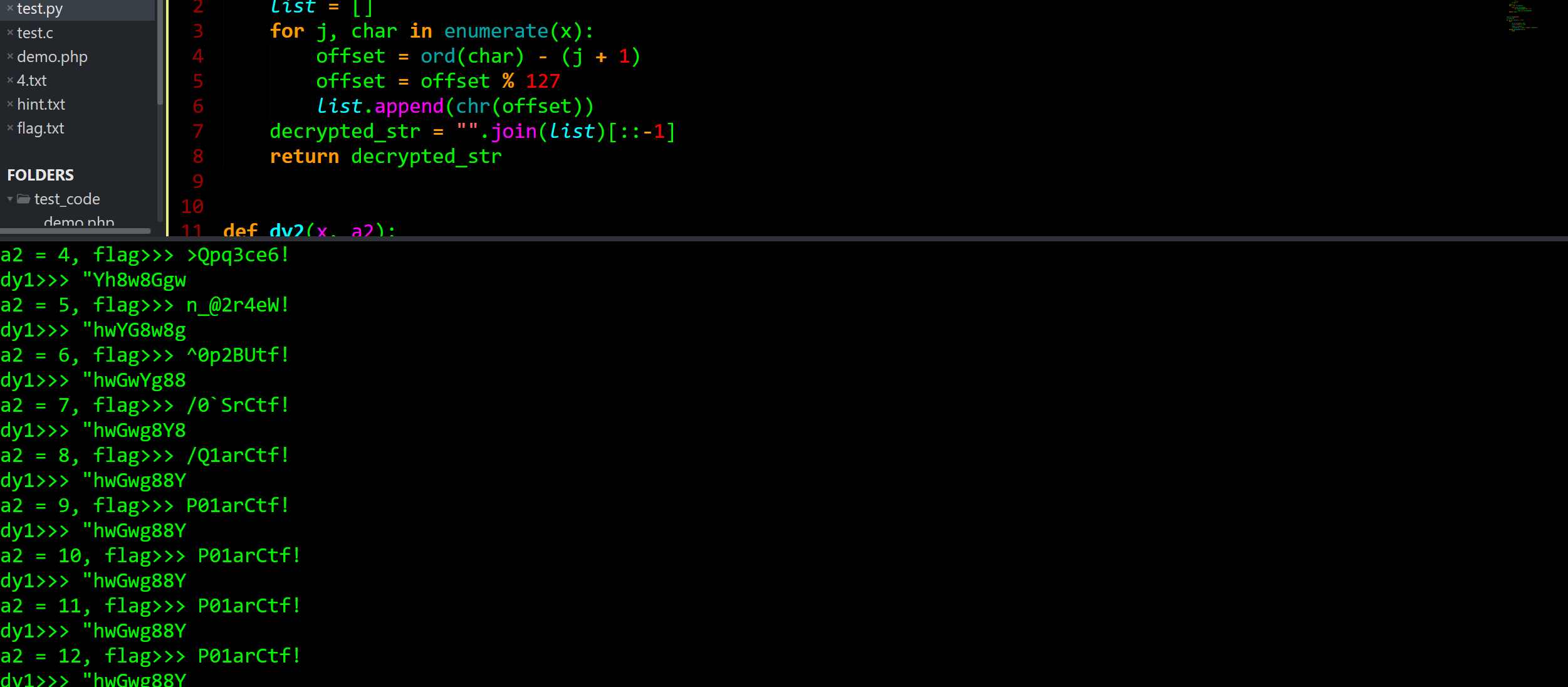
Str2 = '"hwGwg88Y'
print(Str2)
for a2 in range(1, 200):
try:
s1 = dy2(Str2, a2)
print("dy1>>>", s1)
flag = dy1(s1)
print(f"a2 = {a2}, flag>>> {flag}")
except Exception as e:
pass




 浙公网安备 33010602011771号
浙公网安备 33010602011771号