Istio 是什么?
Istio是一个用于服务治理的开放平台
Istio是一个Service Mesh形态的用于服务治理的开放平台
Istio是一个与Kubernetes紧密结合的适用于云原生场景的Service Mesh形态的用于服务治理的开放平台
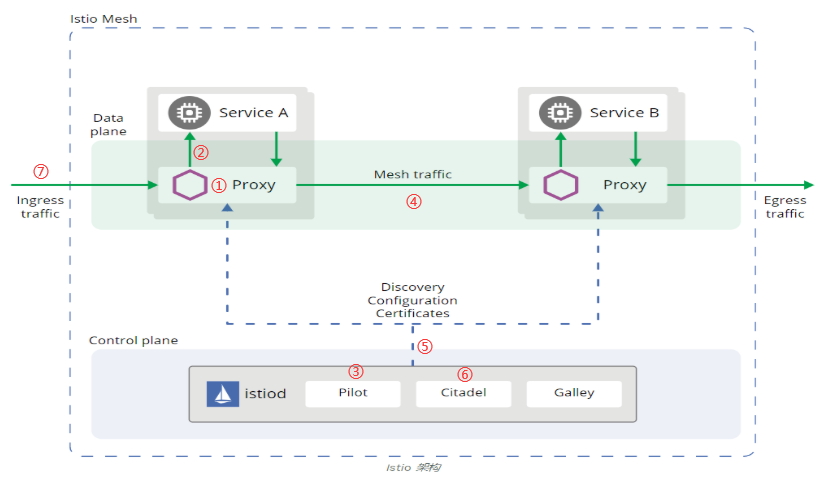
Istio核心组件:
- Proxy(Envoy):以 C++ 开发的高性能代理,用于调解服务网格中所有服务的所有入站和出站流量。
- Pilot:为 Envoy sidecar 提供服务发现功能,为智能路由(例如 A/B 测试、金丝雀部署等)和弹性(超时、重试、熔断器等)提供流量管理功能。
- Citadel:通过内置身份和凭证管理可以提供强大的服务间和最终用户身份验证。
- Galley:istio 负责配置管理的组件,验证配置信息的格式和内容的正确性,并将这些配置信息提供给控制面上向其他组件提供支持。
- Mixer:主要进行访问控制以及策略控制,同时也负责从 Envoy 中获取各项指标。
Istio基本功能:
① 自动注入:指在创建应用程序时自动注入Sidecar代理。
② 流量拦截:在Pod初始化时设置iptables规则,当有流量到来时,基于配置的iptables规则拦截业务容器的Inbound流量和Outbound流量到Sidecar上。
③ 服务发现:服务发起方的Envoy调用管理面组件Pilot的服务发现接口获取目标服务的实例列表。
④ 负载均衡:服务发起方的Envoy根据配置的负载均衡策略选择服务实例,并连接对应的实例地 址。
⑤ 流量治理:Envoy从Pilot中获取配置的流量规则,在拦截到Inbound流量和Outbound流量时执行治理逻辑。
⑥ 访问安全:在服务间访问时通过双方的Envoy进行双向认证和通道加密,并基于服务的身份进行授权管理。
⑦ 外部访问:在网格的入口处有一个Envoy扮演入口网关的角色。
Istio基本使用!
Istio路由规则配置:VirtualService
1 路由规则定义
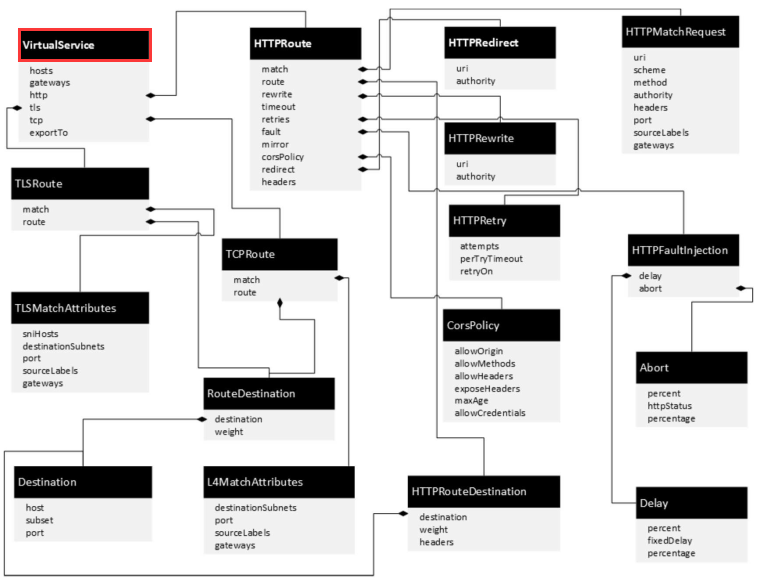
2 HTTP路由(HTTPRoute)
apiVersion: networking.istio.io/v1alpha3 kind: VirtualService metadata: name: frontend-route spec: hosts: - "*" gateways: - istio-system/weather-gateway http: - match: - port: 80 route: - destination: host: frontend port: number: 3000 subset: v1
3 TLS路由(TLSRoute)
apiVersion: networking.istio.io/v1alpha3 kind: VirtualService metadata: name: frontend-route spec: gateways: - istio-system/weather-gateway hosts: - www.weather.com http: - route: - destination: host: frontend subset: v1
4 TCP路由(TCPRoute)
apiVersion: networking.istio.io/v1alpha3 kind: VirtualService metadata: name: tcp-echo spec: hosts: - "*" gateways: - tcp-echo-gateway tcp: - route: - destination: host: tcp-echo port: number: 9000 subset: v1
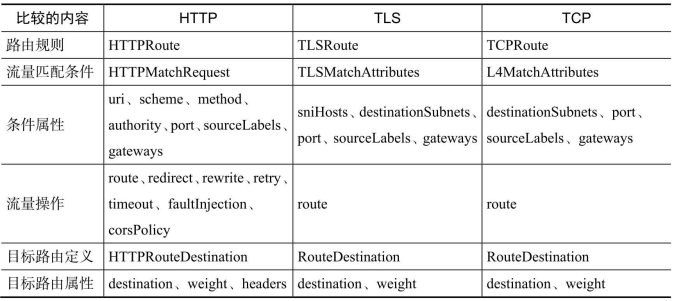
5 三种协议路由规则的对比
Istio目标规则配置:DestinationRule
1 DestinationRule配置示例
apiVersion: networking.istio.io/v1alpha3 kind: DestinationRule metadata: name: frontend-dr namespace: weather spec: host: frontend subsets: - name: v1 labels: version: v1
2 DestinationRule规则定义 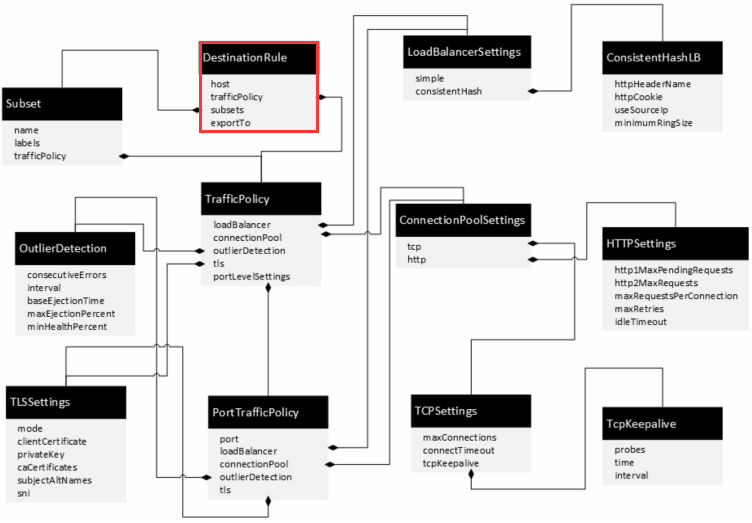
Istio服务网关配置:Gateway
1 Gateway配置示例
apiVersion: networking.istio.io/v1alpha3 kind: Gateway metadata: name: weather-gateway namespace: istio-system spec: selector: istio: ingressgateway # use istio default controller servers: - port: number: 80 name: http protocol: HTTP hosts: - "*"
2 Gateway规则定义 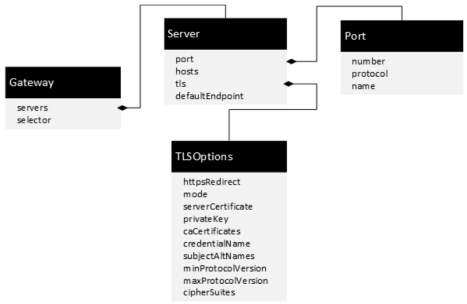
Istio外部服务配置:ServiceEntry
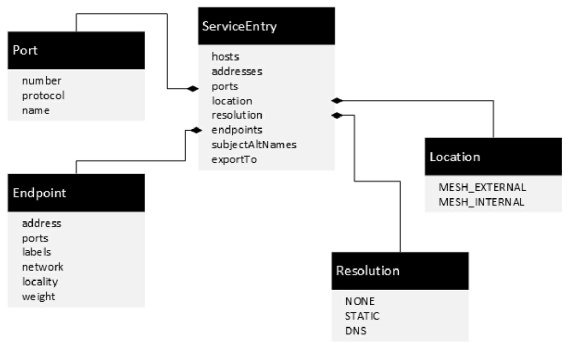
1 ServiceEntry配置示例
apiVersion: networking.istio.io/v1alpha3 kind: ServiceEntry metadata: name: weather-external spec: hosts: - www.wearherdb.com ports: - number: 80 name: http protocol: HTTP location: MESH_EXTERNAL resolution: DNS
2 ServiceEntry规则的定义和用法
Istio代理规则配置:Sidecar
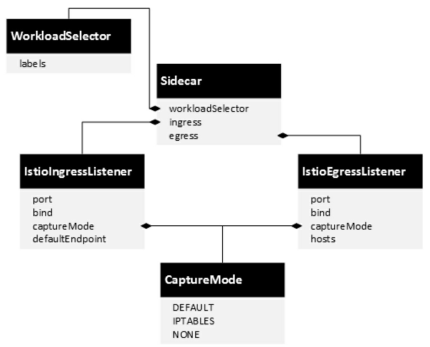
1 Sidecar配置示例
apiVersion: networking.istio.io/v1alpha3 kind: Sidecar metadata: name: default namespace: weather spec: egress: - hosts: - "news/*" - "istio-system/*"
2 Sidecar规则定义
Istio部署记录!
[root@k8s-32 istio-1.6.0]# istioctl manifest apply --set profile=demo Detected that your cluster does not support third party JWT authentication. Falling back to less secure first party JWT. See https://istio.io/docs/ops/best-practices/security/#configure-third-party-service-account-tokens for details. ✔ Istio core installed ✔ Istiod installed ✔ Ingress gateways installed ✔ Egress gateways installed ✔ Addons installed ✔ Installation complete [root@k8s-32 istio-1.6.0]# [root@k8s-32 istio-1.6.0]# kubectl -n istio-system get pod NAME READY STATUS RESTARTS AGE grafana-74dc798895-r9w4k 1/1 Running 0 3m24s istio-egressgateway-69bf865cf8-dqmbm 1/1 Running 0 3m25s istio-ingressgateway-569d44555d-7r6qf 1/1 Running 0 3m25s istio-tracing-8584b4d7f9-zmcrs 1/1 Running 0 3m24s istiod-84cc4dfcd8-cr9vs 1/1 Running 0 3m50s kiali-6f457f5964-7b6h4 1/1 Running 0 3m24s prometheus-79878ff5fd-ktlpf 2/2 Running 0 3m24s
[root@k8s-32 istio-1.6.0]# kubectl -n istio-system get svc NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE grafana ClusterIP 10.96.184.105 <none> 3000/TCP 23m istio-egressgateway ClusterIP 10.103.86.9 <none> 80/TCP,443/TCP,15443/TCP 23m istio-ingressgateway LoadBalancer 10.104.28.37 <pending> 15020:32340/TCP,80:32254/TCP,443:32115/TCP,31400:32616/TCP,15443:32470/TCP 23m istiod ClusterIP 10.105.190.0 <none> 15010/TCP,15012/TCP,443/TCP,15014/TCP,53/UDP,853/TCP 24m jaeger-agent ClusterIP None <none> 5775/UDP,6831/UDP,6832/UDP 23m jaeger-collector ClusterIP 10.108.128.31 <none> 14267/TCP,14268/TCP,14250/TCP 23m jaeger-collector-headless ClusterIP None <none> 14250/TCP 23m jaeger-query ClusterIP 10.104.174.30 <none> 16686/TCP 23m kiali ClusterIP 10.101.20.142 <none> 20001/TCP 23m prometheus ClusterIP 10.99.39.72 <none> 9090/TCP 23m tracing ClusterIP 10.99.205.57 <none> 80/TCP 23m zipkin ClusterIP 10.106.72.65 <none> 9411/TCP 23m
[root@k8s-32 istio-1.6.0]# kubectl -n istio-system edit svc istio-ingressgateway service/istio-ingressgateway edited
[root@k8s-32 istio-1.6.0]# kubectl -n istio-system get svc NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE grafana ClusterIP 10.96.184.105 <none> 3000/TCP 25m istio-egressgateway ClusterIP 10.103.86.9 <none> 80/TCP,443/TCP,15443/TCP 25m istio-ingressgateway NodePort 10.104.28.37 <none> 15020:32340/TCP,80:32254/TCP,443:32115/TCP,31400:32616/TCP,15443:32470/TCP 25m istiod ClusterIP 10.105.190.0 <none> 15010/TCP,15012/TCP,443/TCP,15014/TCP,53/UDP,853/TCP 25m jaeger-agent ClusterIP None <none> 5775/UDP,6831/UDP,6832/UDP 25m jaeger-collector ClusterIP 10.108.128.31 <none> 14267/TCP,14268/TCP,14250/TCP 25m jaeger-collector-headless ClusterIP None <none> 14250/TCP 25m jaeger-query ClusterIP 10.104.174.30 <none> 16686/TCP 24m kiali ClusterIP 10.101.20.142 <none> 20001/TCP 24m prometheus ClusterIP 10.99.39.72 <none> 9090/TCP 24m tracing ClusterIP 10.99.205.57 <none> 80/TCP 24m zipkin ClusterIP 10.106.72.65 <none> 9411/TCP 24m
[root@k8s-32 istio-1.6.0]# kubectl label namespace default istio-injection=enabled error: 'istio-injection' already has a value (enabled), and --overwrite is false
[root@k8s-32 istio-1.6.0]# kubectl apply -f samples/bookinfo/platform/kube/bookinfo.yaml service/details created serviceaccount/bookinfo-details created deployment.apps/details-v1 created service/ratings created serviceaccount/bookinfo-ratings created deployment.apps/ratings-v1 created service/reviews created serviceaccount/bookinfo-reviews created deployment.apps/reviews-v1 created deployment.apps/reviews-v2 created deployment.apps/reviews-v3 created service/productpage created serviceaccount/bookinfo-productpage created deployment.apps/productpage-v1 created
[root@k8s-32 istio-1.6.0]# kubectl apply -f samples/bookinfo/networking/bookinfo-gateway.yaml gateway.networking.istio.io/bookinfo-gateway created virtualservice.networking.istio.io/bookinfo created
[root@k8s-32 istio-1.6.0]# kubectl apply -f samples/bookinfo/networking/destination-rule-all.yaml destinationrule.networking.istio.io/productpage created destinationrule.networking.istio.io/reviews created destinationrule.networking.istio.io/ratings created destinationrule.networking.istio.io/details created
[root@k8s-32 istio-1.6.0]# kubectl get pod NAME READY STATUS RESTARTS AGE details-v1-78d78fbddf-jxx2h 0/2 Init:0/1 0 9s productpage-v1-85b9bf9cd7-kh5wg 0/2 Init:0/1 0 7s ratings-v1-6c9dbf6b45-ccdcg 0/2 Init:0/1 0 8s reviews-v1-564b97f875-5j5x5 0/2 Init:0/1 0 8s reviews-v2-568c7c9d8f-vg52z 0/2 Init:0/1 0 8s reviews-v3-67b4988599-fsjnb 0/2 Init:0/1 0 8s
[root@k8s-32 istio-1.6.0]# kubectl get pod NAME READY STATUS RESTARTS AGE details-v1-78d78fbddf-jxx2h 2/2 Running 0 2m53s productpage-v1-85b9bf9cd7-kh5wg 2/2 Running 0 2m51s ratings-v1-6c9dbf6b45-ccdcg 2/2 Running 0 2m52s reviews-v1-564b97f875-5j5x5 2/2 Running 0 2m52s reviews-v2-568c7c9d8f-vg52z 2/2 Running 0 2m52s reviews-v3-67b4988599-fsjnb 2/2 Running 0 2m52s
其他信息
微服务、容器、Kubernetes、Istio四者关系:
Istio与Kubernetes架构的关系:
Istio+Kubernetes的方案与SDK开发的微服务+Kubernetes的方案比较:
Gateway上的服务发布方式比较
![]()
作者:Leozhanggg
出处: https://www.cnblogs.com/leozhanggg/p/12936327.html
本文版权归作者和博客园共有,欢迎转载,但未经作者同意必须保留此段声明,且在文章页面明显位置给出原文连接,否则保留追究法律责任的权利。




 浙公网安备 33010602011771号
浙公网安备 33010602011771号