ubuntu部署织梦记录二(添加https)
服务器情况:ubuntu + xampp (其实一开始不准备用xampp的,由于坑爹的php环境安装老是出问题,那个php-gd无法检测到,于是卸载了php,mysql,当时apache我保留下来了,只是将它停用,使用xampp自带的apache)
网站文件放/var/www 下 lampp目录在/opt/lampp下
第一步 当然是申请ssl证书,用的阿里云的免费版
先贴上官方apache的部署说明:
安装证书 文件说明: 1. 证书文件1533507204167.pem,包含两段内容,请不要删除任何一段内容。 2. 如果是证书系统创建的CSR,还包含:证书私钥文件1533507204167.key、证书公钥文件public.pem、证书链文件chain.pem。 ( 1 ) 在Apache的安装目录下创建cert目录,并且将下载的全部文件拷贝到cert目录中。如果申请证书时是自己创建的CSR文件,请将对应的私钥文件放到cert目录下并且命名为1533507204167.key; ( 2 ) 打开 apache 安装目录下 conf 目录中的 httpd.conf 文件,找到以下内容并去掉“#”: #LoadModule ssl_module modules/mod_ssl.so (如果找不到请确认是否编译过 openssl 插件) #Include conf/extra/httpd-ssl.conf ( 3 ) 打开 apache 安装目录下 conf/extra/httpd-ssl.conf 文件 (也可能是conf.d/ssl.conf,与操作系统及安装方式有关), 在配置文件中查找以下配置语句: # 添加 SSL 协议支持协议,去掉不安全的协议 SSLProtocol all -SSLv2 -SSLv3 # 修改加密套件如下 SSLCipherSuite HIGH:!RC4:!MD5:!aNULL:!eNULL:!NULL:!DH:!EDH:!EXP:+MEDIUM SSLHonorCipherOrder on # 证书公钥配置 SSLCertificateFile cert/public.pem # 证书私钥配置 SSLCertificateKeyFile cert/1533507204167.key # 证书链配置,如果该属性开头有 '#'字符,请删除掉 SSLCertificateChainFile cert/chain.pem ( 4 ) 重启 Apache。 ( 5 ) 通过 https 方式访问您的站点,测试站点证书的安装配置,如遇到证书不信任问题,请查看帮助视频。
官网讲的情况大致能过程清晰,具体部署还要参考下网上的做法。
第二步部署至服务器:
1、首先将证书解压后放到服务上指定目录,我放在/opt/lampp/share/openssl/certs/下
2、配置httpd.conf文件,通过sudo find / -name httpd.conf,发现有以下三个位置有httpd.conf,应该改的文件路径是/opt/lampp/etc/httpd.conf,
对下面两行去掉#注释,发现我上面默认的已经去掉注释了。。。
#LoadModule ssl_module modules/mod_ssl.so (如果找不到请确认是否编译过 openssl 插件)
#Include conf/extra/httpd-ssl.conf
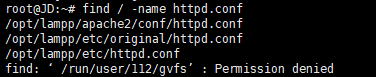
3、通过上面一步发现我的httpd-ssl.conf路径配的etc/extra/httpd-ssl.conf,但是服务器上找不到这个路径文件
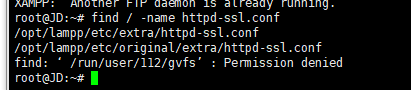
于是先对这个路径文件进行修改/opt/lampp/etc/extra
如果不行再计划如下:1、改httpd-ssl.conf路径配的etc/extra/httpd-ssl.conf
2、两个文件都改试试
结果直接OK了,不需要尝试了
对这个路径文件进行修改/opt/lampp/etc/extra内容如下:
搜索<VirtualHost _default_:443> ,
这个把下面的内容全部删除掉,包含搜索的这行,复制下面完整的配置,修改相关路径、域名证书文件等信息,
修改完重启apache服务。
看下完整的配置
DocumentRoot "/var/www/myweb" ServerName www.myweb.cn ServerAdmin myeamil@qq.com ErrorLog "/opt/lampp/logs/error_log" TransferLog "/opt/lampp/logs/access_log" SSLEngine on SSLProtocol all -SSLv2 -SSLv3 SSLCipherSuite HIGH:!RC4:!MD5:!aNULL:!eNULL:!NULL:!DH:!EDH:!EXP:+MEDIUM SSLHonorCipherOrder on SSLCertificateFile /opt/lampp/share/openssl/certs/public.pem SSLCertificateKeyFile /opt/lampp/share/openssl/certs/1533507204167.key SSLCertificateChainFile /opt/lampp/share/openssl/certs/chain.pem <Directory "/var/www/myweb"> Options FollowSymLinks AllowOverride All Require all granted </Directory>
在删除的时候我保留了原VirtualHost _default_:443> 中的以下内容放在新的VirtualHost _default_:443> 中
# SSL Engine Options: # Set various options for the SSL engine. # o FakeBasicAuth: # Translate the client X.509 into a Basic Authorisation. This means that # the standard Auth/DBMAuth methods can be used for access control. The # user name is the `one line' version of the client's X.509 certificate. # Note that no password is obtained from the user. Every entry in the user # file needs this password: `xxj31ZMTZzkVA'. # o ExportCertData: # This exports two additional environment variables: SSL_CLIENT_CERT and # SSL_SERVER_CERT. These contain the PEM-encoded certificates of the # server (always existing) and the client (only existing when client # authentication is used). This can be used to import the certificates # into CGI scripts. # o StdEnvVars: # This exports the standard SSL/TLS related `SSL_*' environment variables. # Per default this exportation is switched off for performance reasons, # because the extraction step is an expensive operation and is usually # useless for serving static content. So one usually enables the # exportation for CGI and SSI requests only. # o StrictRequire: # This denies access when "SSLRequireSSL" or "SSLRequire" applied even # under a "Satisfy any" situation, i.e. when it applies access is denied # and no other module can change it. # o OptRenegotiate: # This enables optimized SSL connection renegotiation handling when SSL # directives are used in per-directory context. #SSLOptions +FakeBasicAuth +ExportCertData +StrictRequire <FilesMatch "\.(cgi|shtml|phtml|php)$"> SSLOptions +StdEnvVars </FilesMatch> <Directory "/opt/lampp/cgi-bin"> SSLOptions +StdEnvVars </Directory> # SSL Protocol Adjustments: # The safe and default but still SSL/TLS standard compliant shutdown # approach is that mod_ssl sends the close notify alert but doesn't wait for # the close notify alert from client. When you need a different shutdown # approach you can use one of the following variables: # o ssl-unclean-shutdown: # This forces an unclean shutdown when the connection is closed, i.e. no # SSL close notify alert is sent or allowed to be received. This violates # the SSL/TLS standard but is needed for some brain-dead browsers. Use # this when you receive I/O errors because of the standard approach where # mod_ssl sends the close notify alert. # o ssl-accurate-shutdown: # This forces an accurate shutdown when the connection is closed, i.e. a # SSL close notify alert is send and mod_ssl waits for the close notify # alert of the client. This is 100% SSL/TLS standard compliant, but in # practice often causes hanging connections with brain-dead browsers. Use # this only for browsers where you know that their SSL implementation # works correctly. # Notice: Most problems of broken clients are also related to the HTTP # keep-alive facility, so you usually additionally want to disable # keep-alive for those clients, too. Use variable "nokeepalive" for this. # Similarly, one has to force some clients to use HTTP/1.0 to workaround # their broken HTTP/1.1 implementation. Use variables "downgrade-1.0" and # "force-response-1.0" for this. BrowserMatch "MSIE [2-5]" \ nokeepalive ssl-unclean-shutdown \ downgrade-1.0 force-response-1.0 # Per-Server Logging: # The home of a custom SSL log file. Use this when you want a # compact non-error SSL logfile on a virtual host basis. CustomLog "/opt/lampp/logs/ssl_request_log" \ "%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b"
参考了
https://lirongyao.com/xampp-configure-ssl.html
外链挂两个



 浙公网安备 33010602011771号
浙公网安备 33010602011771号