NGFW-IPSec的高可用性
一,主备链路备份
1.1拓扑图
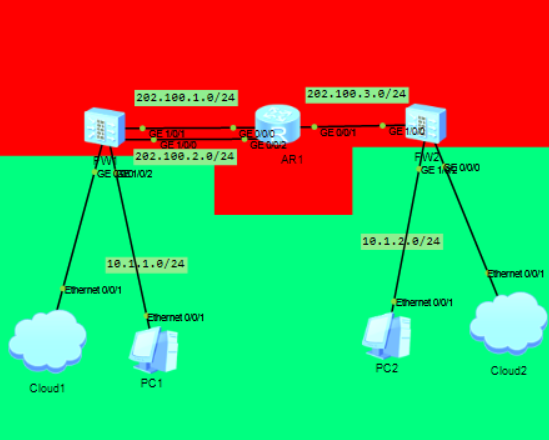
Cloud1和Cloud2桥接了物理机网卡,方便可以使用web图形化。
1.2需求说明
FW1双出口连接ISP,两条链路为主备。在FW2上配置tunnel口配置主备IPSec建立连接。
1.3配置
1.3.1基础配置
VLAN,IP地址,安全区域的配置省略
1.3.2 FW2配置Tunnel口
[FW2]interface Tunnel 1 //配置tunnel口 [FW2-Tunnel1]tunnel-protocol ipsec //指定tunnel口协议 [FW2-Tunnel1]ip address unnumbered interface GigabitEthernet 1/0/0 //像物理口借地址 [FW2-Tunnel1]interface Tunnel 2 [FW2-Tunnel2]tunnel-protocol ipsec [FW2-Tunnel2]ip address unnumbered interface GigabitEthernet 1/0/0
1.3.3静态路由联动IP-Link
FW1:浮动路由主备链路
[FW1]ip-link check enable [FW1]ip-link name link1 [FW1-iplink-link1]destination 202.100.1.254 interface GigabitEthernet 1/0/1 mode icmp next-hop 202.100.1.254 [FW1]ip route-static 0.0.0.0 0 202.100.1.254 track ip-link link1 [FW1]ip route-static 0.0.0.0 0 202.100.2.254 preference 70
FW2:感兴趣流指向tunnel口,两逻辑口为主备
[FW2]ip-link check enable [FW2]ip-link name link1 [FW2-iplink-link1]destination 202.100.1.254 interface GigabitEthernet 1/0/0 mode icmp next-hop 202.100.3.254 [FW2]ip route-static 0.0.0.0 0 202.100.3.254 [FW2]ip route-static 10.1.1.0 24 Tunnel 1 track ip-link link1 [FW2]ip route-static 10.1.1.0 24 Tunnel 2 preference 70
1.3.3IPSec
FW1:
[FW1]ike proposal 1 [FW1-ike-proposal-1]dis this 2022-10-15 03:30:11.870 # ike proposal 1 encryption-algorithm aes-256 dh group14 authentication-algorithm sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256 # return [FW1]ike peer ha [FW1-ike-peer-ha]remote-address 202.100.3.11 [FW1-ike-peer-ha]pre-shared-key Huawei@123 [FW1-ike-peer-ha]undo version 2 [FW1-ike-peer-ha]ike-proposal 1 [FW1-ike-peer-ha]ike peer ha2 [FW1-ike-peer-ha2]remote-address 202.100.3.11 [FW1-ike-peer-ha2]pre-shared-key Huawei@123 [FW1-ike-peer-ha2]undo version 2 [FW1-ike-peer-ha2]ike-proposal 1 [FW1-ike-peer-ha2]acl number 3000 [FW1-acl-adv-3000]rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255 [FW1-acl-adv-3000]acl number 3001 [FW1-acl-adv-3001]rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255 [FW1-acl-adv-3001]ipsec proposal 1 [FW1-ipsec-proposal-1]ipsec policy ipsec1 1 isakmp [FW1-ipsec-policy-isakmp-ipsec1-1]security acl 3000 [FW1-ipsec-policy-isakmp-ipsec1-1]proposal 1 [FW1-ipsec-policy-isakmp-ipsec1-1]ike-peer ha [FW1-ipsec-policy-isakmp-ipsec1-1]ipsec policy ipsec2 2 isakmp [FW1-ipsec-policy-isakmp-ipsec2-2]security acl 3001 [FW1-ipsec-policy-isakmp-ipsec2-2]proposal 1 [FW1-ipsec-policy-isakmp-ipsec2-2]ike-peer ha2
[FW1-GigabitEthernet1/0/1]ipsec policy ipsec1
[FW1-GigabitEthernet1/0/0]ipsec policy ipsec2
FW2:
[FW2]ike proposal 1 [FW2-ike-proposal-1]dis this 2022-10-15 03:37:01.290 # ike proposal 1 encryption-algorithm aes-256 dh group14 authentication-algorithm sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256 # return [FW2]ike peer ha [FW2-ike-peer-ha]remote-address 202.100.1.10 [FW2-ike-peer-ha]pre-shared-key Huawei@123 [FW2-ike-peer-ha]undo version 2 [FW2-ike-peer-ha]ike-proposal 1 [FW2-ike-peer-ha]ike peer ha2 [FW2-ike-peer-ha2]remote-address 202.100.2.10 [FW2-ike-peer-ha2]pre-shared-key Huawei@123 [FW2-ike-peer-ha2]undo version 2 [FW2-ike-peer-ha2]ike-proposal 1 [FW2-ike-peer-ha2]acl number 3000 [FW2-acl-adv-3000]rule permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255 [FW2-acl-adv-3000]acl number 3001 [FW2-acl-adv-3001]rule permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255 [FW2-acl-adv-3001]ipsec proposal 1 [FW2-ipsec-proposal-1]dis this 2022-10-15 03:40:27.440 # ipsec proposal 1 esp authentication-algorithm sha2-256 esp encryption-algorithm aes-256 # return [FW2-ipsec-proposal-1]ipsec policy ipsec1 1 isakmp [FW2-ipsec-policy-isakmp-ipsec1-1]proposal 1 [FW2-ipsec-policy-isakmp-ipsec1-1]security acl 3000 [FW2-ipsec-policy-isakmp-ipsec1-1]ike-peer ha [FW2-ipsec-policy-isakmp-ipsec1-1]ipsec policy ipsec2 2 isakmp [FW2-ipsec-policy-isakmp-ipsec2-2]proposal 1 [FW2-ipsec-policy-isakmp-ipsec2-2]security acl 3001 [FW2-ipsec-policy-isakmp-ipsec2-2]ike-peer ha2 [FW2-ipsec-policy-isakmp-ipsec2-2]interface Tunnel 1 [FW2-Tunnel1]ipsec policy ipsec1 [FW2-Tunnel1]interface Tunnel 2 [FW2-Tunnel2]ipsec policy ipsec2
1.3.4配置对象(地址集和服务)
FW1(FW2略):
[FW1]ip address-set ipsec type object [FW1-object-address-set-ipsec]address 202.100.1.10 mask 32 [FW1-object-address-set-ipsec]address 202.100.2.10 mask 32 [FW1-object-address-set-ipsec]address 202.100.3.11 mask 32 [FW1-object-address-set-ipsec]ip address-set vpn_pc type object [FW1-object-address-set-vpn_pc]address 10.1.1.0 mask 24 [FW1-object-address-set-vpn_pc]address 10.1.2.0 mask 24 [FW1-object-address-set-vpn_pc]ip service-set ISAKMP type objec [FW1-object-service-set-ISAKMP]service protocol udp source-port 500 destination-port 500
1.3.5安全策略
FW1(FW2略):
[FW1]security-policy [FW1-policy-security]rule name ipsec [FW1-policy-security-rule-ipsec]source-zone local untrust [FW1-policy-security-rule-ipsec]destination-zone local untrust [FW1-policy-security-rule-ipsec]source-address address-set ipsec [FW1-policy-security-rule-ipsec]destination-address address-set ipsec [FW1-policy-security-rule-ipsec]service ISAKMP esp [FW1-policy-security-rule-ipsec]action permit [FW1-policy-security-rule-ipsec]rule name vpn_pc [FW1-policy-security-rule-vpn_pc]source-zone trust untrust [FW1-policy-security-rule-vpn_pc]destination-zone trust untrust [FW1-policy-security-rule-vpn_pc]source-address address-set vpn_pc [FW1-policy-security-rule-vpn_pc]destination-address address-set vpn_pc [FW1-policy-security-rule-vpn_pc]action permit
1.4 测试现象
1.PC1发起访问,并抓包。(做的时候发现ping不通,因为忘记了将Tunnel口加安全区域)
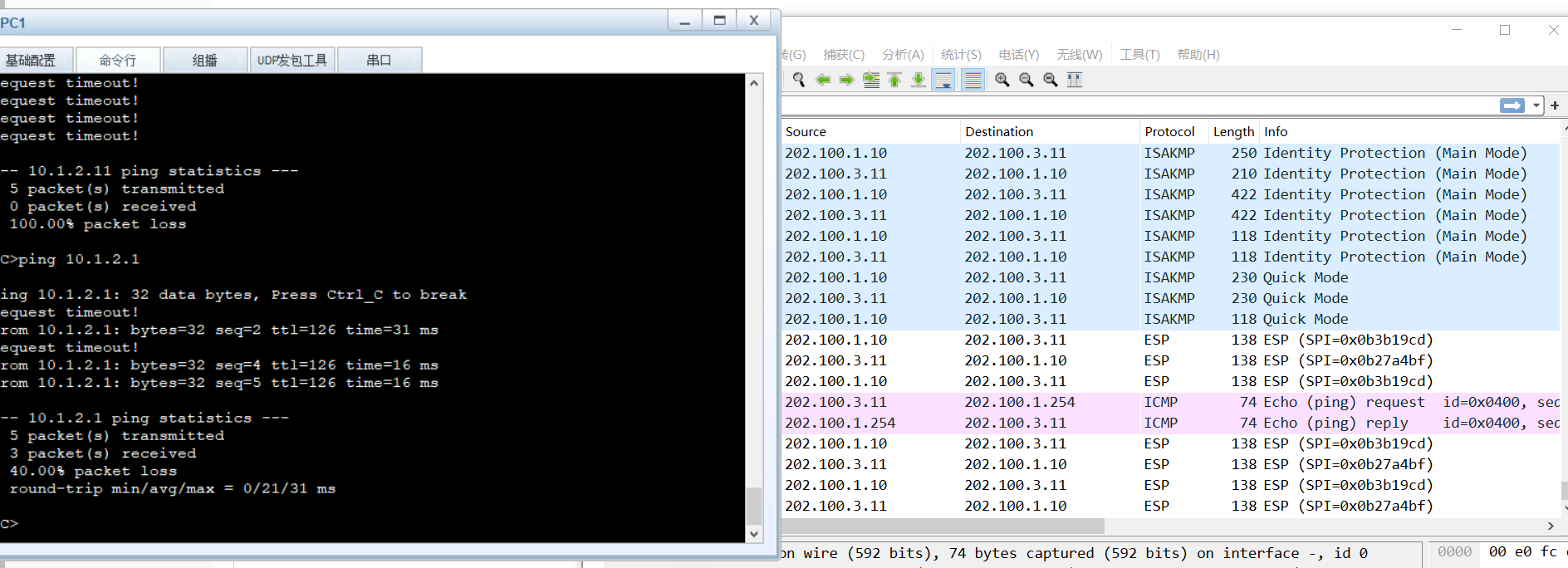
2.查看路由表(浮动路由)
[FW1]display ip routing-table protocol static 2022-10-15 04:15:54.350 Route Flags: R - relay, D - download to fib ------------------------------------------------------------------------------ Public routing table : Static Destinations : 1 Routes : 2 Configured Routes : 2 Static routing table status : <Active> Destinations : 1 Routes : 1 Destination/Mask Proto Pre Cost Flags NextHop Interface 0.0.0.0/0 Static 60 0 RD 202.100.1.254 GigabitEthernet1/0/1 Static routing table status : <Inactive> Destinations : 1 Routes : 1 Destination/Mask Proto Pre Cost Flags NextHop Interface 0.0.0.0/0 Static 70 0 R 202.100.2.254 GigabitEthernet1/0/0 [FW2]display ip routing-table protocol static 2022-10-15 04:16:26.640 Route Flags: R - relay, D - download to fib ------------------------------------------------------------------------------ Public routing table : Static Destinations : 2 Routes : 3 Configured Routes : 3 Static routing table status : <Active> Destinations : 2 Routes : 2 Destination/Mask Proto Pre Cost Flags NextHop Interface 0.0.0.0/0 Static 60 0 RD 202.100.3.254 GigabitEthernet1/0/0 10.1.1.0/24 Static 60 0 D 202.100.3.11 Tunnel1 Static routing table status : <Inactive> Destinations : 1 Routes : 1 Destination/Mask Proto Pre Cost Flags NextHop Interface 10.1.1.0/24 Static 70 0 202.100.3.11 Tunnel2
3,断开R1的G0/0/0,查看IP-link的变化和路由表的变化。这里IP-link检测到链路故障,优先级较高的路由失效,优先级较低的生效,重新协商了ipsec。
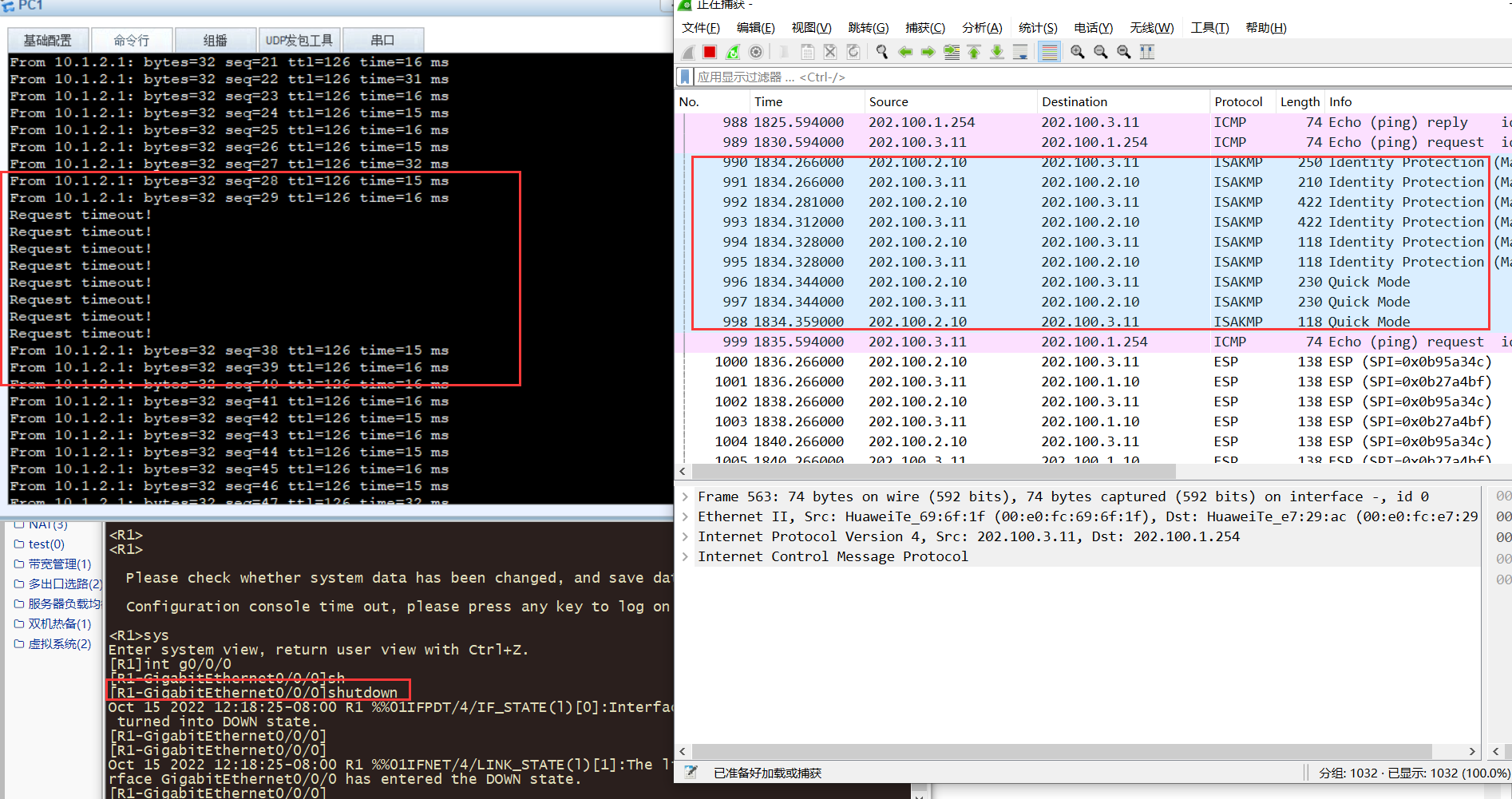
[FW1]display ip routing-table protocol static 2022-10-15 04:19:50.400 Route Flags: R - relay, D - download to fib ------------------------------------------------------------------------------ Public routing table : Static Destinations : 1 Routes : 2 Configured Routes : 2 Static routing table status : <Active> Destinations : 1 Routes : 1 Destination/Mask Proto Pre Cost Flags NextHop Interface 0.0.0.0/0 Static 70 0 RD 202.100.2.254 GigabitEthernet1/0/0 Static routing table status : <Inactive> Destinations : 1 Routes : 1 Destination/Mask Proto Pre Cost Flags NextHop Interface 0.0.0.0/0 Static 60 0 202.100.1.254 Unknown
[FW2]display ip routing-table protocol static 2022-10-15 04:19:54.240 Route Flags: R - relay, D - download to fib ------------------------------------------------------------------------------ Public routing table : Static Destinations : 2 Routes : 3 Configured Routes : 3 Static routing table status : <Active> Destinations : 2 Routes : 2 Destination/Mask Proto Pre Cost Flags NextHop Interface 0.0.0.0/0 Static 60 0 RD 202.100.3.254 GigabitEthernet1/0/0 10.1.1.0/24 Static 70 0 D 202.100.3.11 Tunnel2 Static routing table status : <Inactive> Destinations : 1 Routes : 1 Destination/Mask Proto Pre Cost Flags NextHop Interface 10.1.1.0/24 Static 60 0 202.100.3.11 Tunnel1
二,隧道化链路备份
2.1拓扑图
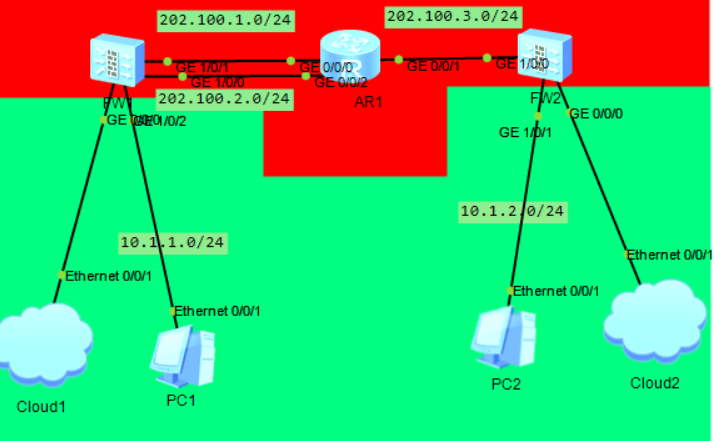
Cloud1和Cloud2桥接了物理机网卡,方便可以使用web图形化。
2.2需求说明
FW1双出口与ISP连接,两条链路负载均衡。联动IP-Link对链路监测。FW1与FW2建立IPSec,负载均衡链路其中一条故障也不会影响内网PC的通信。
2.3配置
IP地址,安全区域的配置省略。
2.3.1静态路由联动IP-Link
[FW1]ip-link check enable [FW1]ip-link name link1 [FW1-iplink-link1]destination 202.100.1.254 interface GigabitEthernet 1/0/1 mode icmp next-hop 202.100.1.254 [FW1-iplink-link1]ip-link name link2 [FW1-iplink-link2]destination 202.100.2.254 interface GigabitEthernet 1/0/0 mode icmp next-hop 202.100.2.254
[FW1]ip route-static 0.0.0.0 0 202.100.1.254 track ip-link link1 [FW1]ip route-static 0.0.0.0 0 202.100.2.254 track ip-link link2
[FW1]ip route-static 10.1.2.0 24 Tunnel 1
[FW2]ip route-static 0.0.0.0 0 202.100.3.254
2.3.2 FW1配置Tunnel口
[FW1]interface Tunnel 1 [FW1-Tunnel1]ip address 1.1.1.1 32 [FW1-Tunnel1]tunnel-protocol ipsec [FW1-Tunnel1]firewall zone untrust [FW1-zone-untrust]add interface Tunnel 1
AR1:
[AR1]ip route-static 1.1.1.1 32 202.100.1.10 [AR1]ip route-static 1.1.1.1 32 202.100.2.10
2.3.3配置IPSec
FW1:
[FW1]ike proposal 1 [FW1-ike-proposal-1]dis this 2022-10-15 05:53:00.240 # ike proposal 1 encryption-algorithm aes-256 dh group14 authentication-algorithm sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256 # return [FW1-ike-proposal-1]ike peer fw2 [FW1-ike-peer-fw2]undo version 2 [FW1-ike-peer-fw2]remote-address 202.100.3.11 [FW1-ike-peer-fw2]ike-proposal 1
[FW1-ike-peer-fw2]pre-shared-key Huawei@123 [FW1-ike-peer-fw2]acl number 3000 [FW1-acl-adv-3000]rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255 [FW1-acl-adv-3000]ipsec proposal 1 [FW1-ipsec-proposal-1]dis this 2022-10-15 05:55:35.670 # ipsec proposal 1 esp authentication-algorithm sha2-256 esp encryption-algorithm aes-256 # return [FW1-ipsec-proposal-1]ipsec policy ipsec1 1 isakmp [FW1-ipsec-policy-isakmp-ipsec1-1]security acl 3000 [FW1-ipsec-policy-isakmp-ipsec1-1]ike-peer fw2 [FW1-ipsec-policy-isakmp-ipsec1-1]proposal 1 [FW1-Tunnel1]ipsec policy ipsec1
FW2省略,对端地址指定1.1.1.1,其他配置镜像即可。
2.3.3 地址集和服务
[FW1]ip address-set ipsec type object [FW1-object-address-set-ipsec]address 202.100.3.11 mask 32 [FW1-object-address-set-ipsec]address 1.1.1.1 mask 32 [FW1-object-address-set-ipsec]ip address-set vpn_pc type object [FW1-object-address-set-vpn_pc]address 10.1.1.0 mask 24 [FW1-object-address-set-vpn_pc]address 10.1.2.0 mask 24
[FW1]ip service-set ISAKMP type object [FW1-object-service-set-ISAKMP]service protocol udp source-port 500 destination-port 500
2.3.4 安全策略
[FW1-policy-security-rule-icmp]rule name ipsec [FW1-policy-security-rule-ipsec]source-zone local untrust [FW1-policy-security-rule-ipsec]destination-zone local untrust [FW1-policy-security-rule-ipsec]source-address address-set ipsec [FW1-policy-security-rule-ipsec]destination-address address-set ipsec [FW1-policy-security-rule-ipsec]service ISAKMP esp [FW1-policy-security-rule-ipsec]action permit [FW1-policy-security-rule-ipsec]rule name vpn_pc [FW1-policy-security-rule-vpn_pc]source-zone trust untrust [FW1-policy-security-rule-vpn_pc]destination-zone trust untrust [FW1-policy-security-rule-vpn_pc]source-address address-set vpn_pc [FW1-policy-security-rule-vpn_pc]destination-address address-set vpn_pc [FW1-policy-security-rule-vpn_pc]action permit
2.4测试现象
1.查看路由表,双出口负载均衡
[FW1-policy-security]dis ip routing-table 2022-10-15 06:09:25.410 Route Flags: R - relay, D - download to fib ------------------------------------------------------------------------------ Routing Tables: Public Destinations : 10 Routes : 11 Destination/Mask Proto Pre Cost Flags NextHop Interface 0.0.0.0/0 Static 60 0 RD 202.100.1.254 GigabitEthernet1/0/1 Static 60 0 RD 202.100.2.254 GigabitEthernet1/0/0
2.PC1发起与PC2的通信
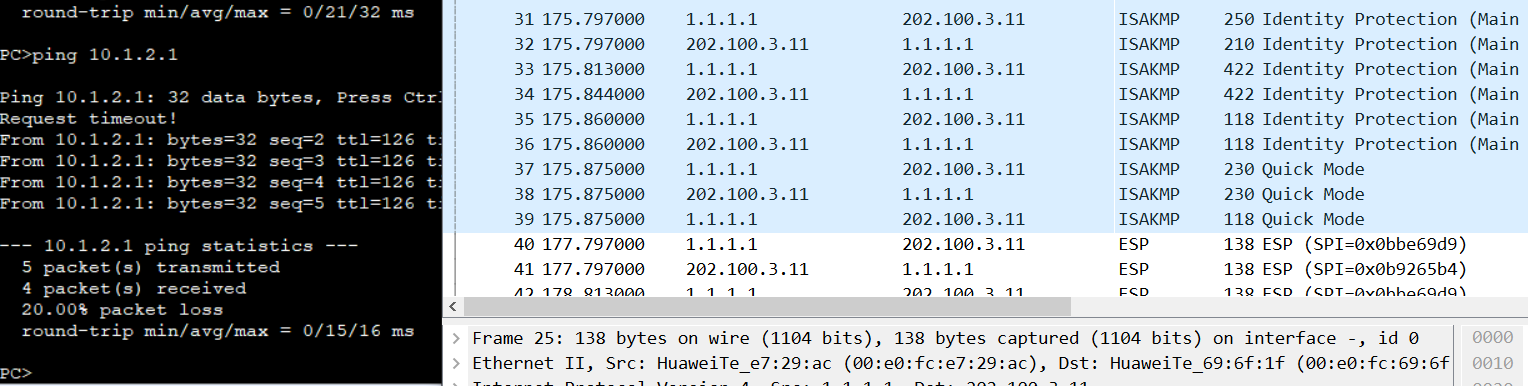
3.查看IKE SA,IPSEC SA
[FW1]dis ike sa 2022-10-15 06:15:39.190 IKE SA information : Conn-ID Peer VPN Flag(s) Phase RemoteType RemoteID ------------------------------------------------------------------------------------------------------------------------------------ 5 202.100.3.11:500 RD|ST|A v1:2 IP 202.100.3.11 4 202.100.3.11:500 RD|ST|A v1:1 IP 202.100.3.11 Number of IKE SA : 2
[FW1]dis ipsec sa 2022-10-15 06:15:56.530 ipsec sa information: =============================== Interface: Tunnel1 =============================== ----------------------------- IPSec policy name: "ipsec1" Sequence number : 1 Acl group : 3000 Acl rule : 5 Mode : ISAKMP ----------------------------- Connection ID : 5 Encapsulation mode: Tunnel Holding time : 0d 0h 1m 16s Tunnel local : 1.1.1.1:500 Tunnel remote : 202.100.3.11:500 Flow source : 10.1.1.0/255.255.255.0 0/0-65535 Flow destination : 10.1.2.0/255.255.255.0 0/0-65535 [Outbound ESP SAs] SPI: 197028313 (0xbbe69d9) Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128 SA remaining key duration (kilobytes/sec): 10485760/3524 Max sent sequence-number: 5 UDP encapsulation used for NAT traversal: N SA encrypted packets (number/bytes): 4/240 [Inbound ESP SAs] SPI: 194143668 (0xb9265b4) Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128 SA remaining key duration (kilobytes/sec): 10485760/3524 Max received sequence-number: 1 UDP encapsulation used for NAT traversal: N SA decrypted packets (number/bytes): 4/240 Anti-replay : Enable Anti-replay window size: 1024
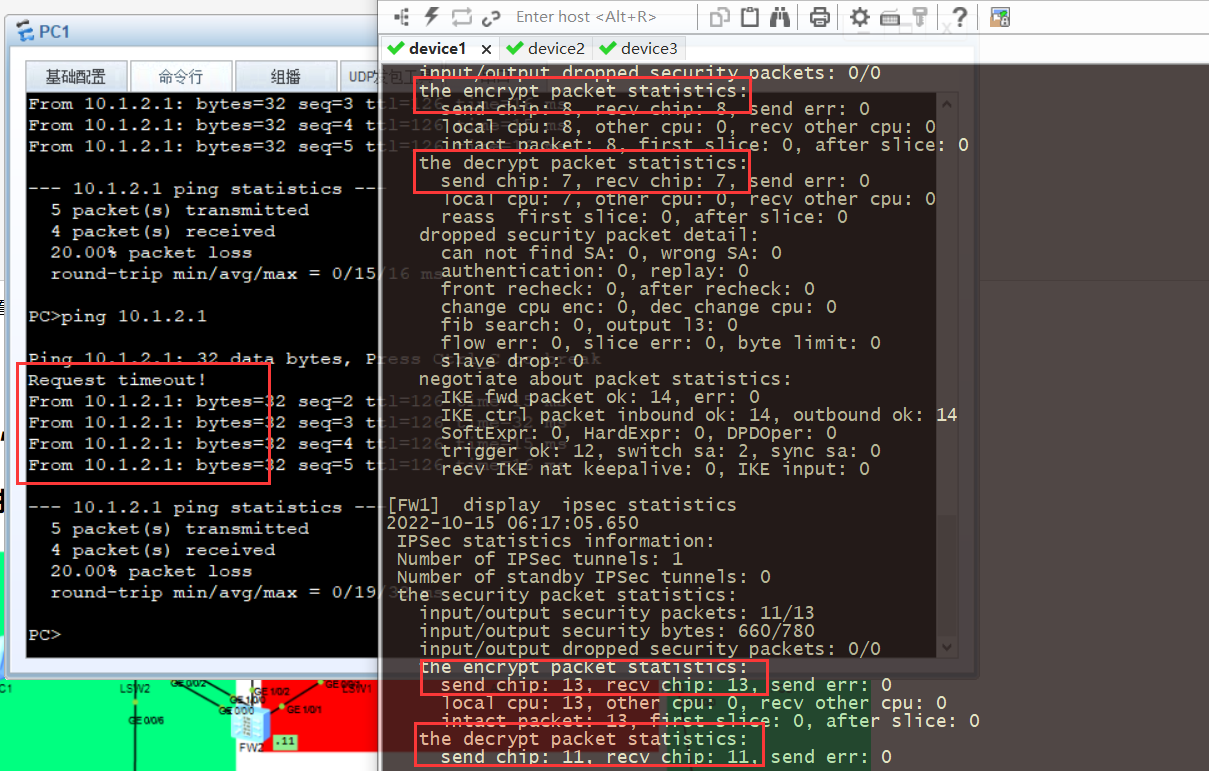
4.查看加密统计,ping5次丢包一次,查看表对比ping之前的结果,加密增加5个,解密增加4个,正确的。
5.制造链路故障查看现象,断开AR1的G0/0/0口
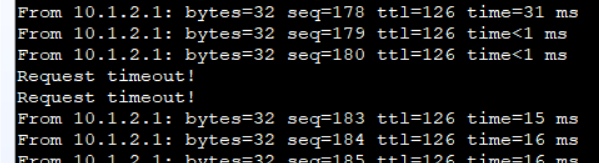
6.IP-Link生效,故障链路的静态路由变为失效。
[FW1]display ip routing-table 2022-10-15 06:22:55.410 Route Flags: R - relay, D - download to fib ------------------------------------------------------------------------------ Routing Tables: Public Destinations : 9 Routes : 9 Destination/Mask Proto Pre Cost Flags NextHop Interface 0.0.0.0/0 Static 60 0 RD 202.100.2.254 GigabitEthernet1/0/0 1.1.1.1/32 Direct 0 0 D 127.0.0.1 Tunnel1
三,主备网关备份
3.1拓扑图
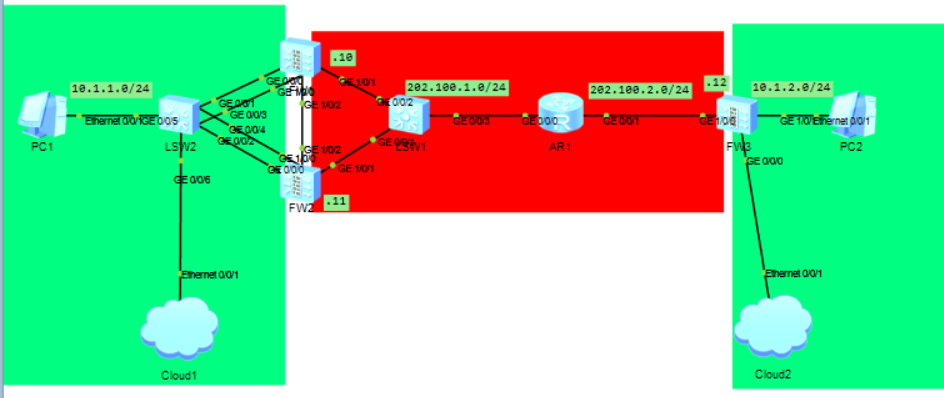
Cloud1和Cloud2桥接了物理机网卡,方便可以使用web图形化。
3.2需求说明
FW1和FW2做三层上下行连接交换机的主备备份,虚拟IP的主机位均是100。建立双机热备后使用虚拟IP与FW3建立IPSec VPN,使得trust区域的PC可以通过VPN互通。
3.3配置
3.3.1基础配置
VLAN,IP地址,安全区域的配置省略。因为双机热备不会备份路由,配置静态路由指向AR1如下。
[FW1]ip route-static 0.0.0.0 0 202.100.1.254 [FW2]ip route-static 0.0.0.0 0 202.100.1.254 [FW3]ip route-static 0.0.0.0 0 202.100.2.254
3.3.2双机热备
FW1:
[FW1]interface GigabitEthernet 1/0/1 [FW1-GigabitEthernet1/0/1]vrrp vrid 1 virtual-ip 202.100.1.100 active //指定为主设备 [FW1-GigabitEthernet1/0/1]interface GigabitEthernet 1/0/0 [FW1-GigabitEthernet1/0/0]vrrp vrid 2 virtual-ip 10.1.1.100 active [FW1-GigabitEthernet1/0/0]quit [FW1]hrp interface GigabitEthernet 1/0/2 remote 172.16.1.11 //指定心跳线接口和对端地址 [FW1]hrp enable
FW2:
[FW2]interface GigabitEthernet 1/0/1 [FW2-GigabitEthernet1/0/1]vrrp vrid 1 virtual-ip 202.100.1.100 standby //指定为备设备 [FW2-GigabitEthernet1/0/1]interface GigabitEthernet 1/0/0 [FW2-GigabitEthernet1/0/0]vrrp vrid 2 virtual-ip 10.1.1.100 standby [FW2-GigabitEthernet1/0/0]quit [FW2]hrp interface GigabitEthernet 1/0/2 remote 172.16.1.10 //指定心跳线接口和对端地址 [FW2]hrp enable
3.3.3对象的配置(地址集,服务)
HRP_M[FW1]ip address-set ipsec type object (+B) //地址集,方便安全策略使用 HRP_M[FW1-object-address-set-ipsec]address 202.100.1.100 mask 32 (+B) HRP_M[FW1-object-address-set-ipsec]address 202.100.2.12 mask 32 (+B) HRP_M[FW1]ip address-set vpn_pc type object (+B) HRP_M[FW1-object-address-set-vpn_pc]address 10.1.1.0 mask 24 (+B) HRP_M[FW1-object-address-set-vpn_pc]address 10.1.2.0 mask 24 (+B) HRP_M[FW1]ip service-set ISAKMP type object (+B) //加密流量的端口方便安全策略使用 HRP_M[FW1-object-service-set-ISAKMP]service protocol udp source-port 500 destination-port 500 (+B)
[FW3]ip address-set ipsec type object [FW3-object-address-set-ipsec]address 202.100.1.100 mask 32 [FW3-object-address-set-ipsec]address 202.100.2.12 mask 32 [FW3-object-address-set-ipsec]ip address-set vpn_pc type object [FW3-object-address-set-vpn_pc]address 10.1.1.0 mask 24 [FW3-object-address-set-vpn_pc]address 10.1.2.0 mask 24 [FW3-object-address-set-vpn_pc]ip service-set ISAKMP type objec [FW3-object-service-set-ISAKMP]service protocol udp source-port 500 destination-port 500
3.3.4 IPSec配置
FW1:
HRP_M[FW1]ike proposal 1 (+B) //ike提议使用默认 HRP_M[FW1-ike-proposal-1]dis this 2022-10-15 01:24:38.090 # ike proposal 1 encryption-algorithm aes-256 dh group14 authentication-algorithm sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256 # return HRP_M[FW1-ike-proposal-1]ike peer fw2 (+B) //配置ike对等体 HRP_M[FW1-ike-peer-fw2]ike-proposal 1 (+B) //调用ike提议 HRP_M[FW1-ike-peer-fw2]undo version 2 (+B) //使用version1,默认v1,v2都开启,发起时使用v2 HRP_M[FW1-ike-peer-fw2]pre-shared-key Huawei@123 (+B) //预定义密钥 HRP_M[FW1-ike-peer-fw2]remote-address 202.100.2.12 (+B) //指定对端地址 HRP_M[FW1]ipsec proposal 1 (+B) //ipsec提议使用默认 HRP_M[FW1-ipsec-proposal-1]dis this 2022-10-15 01:31:23.110 # ipsec proposal 1 esp authentication-algorithm sha2-256 esp encryption-algorithm aes-256 # return HRP_M[FW1-ipsec-proposal-1]acl number 3000 (+B) //配置感兴趣流,及加密的流量是谁 HRP_M[FW1-acl-adv-3000]rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255 (+B) HRP_M[FW1-acl-adv-3000]ipsec policy ipsec1 1 isakmp (+B) //配置ipsec策略 HRP_M[FW1-ipsec-policy-isakmp-ipsec1-1]proposal 1 (+B) //调用ipsec提议 HRP_M[FW1-ipsec-policy-isakmp-ipsec1-1]security acl 3000 (+B) //调用感兴趣流 HRP_M[FW1-ipsec-policy-isakmp-ipsec1-1]ike-peer fw2 (+B) //调用对等体
HRP_M[FW1-ipsec-policy-isakmp-ipsec1-1]tunnel local 202.100.1.100 //指定本段地址为vrrp的虚拟地址 HRP_M[FW1-ipsec-policy-isakmp-ipsec1-1]interface GigabitEthernet1/0/1 (+B) //在接口下调用IPsec策略 HRP_M[FW1-GigabitEthernet1/0/1]ipsec policy ipsec1 (+B)
FW3:
[FW3]ike proposal 1 //ike提议与对端保持一致 [FW3-ike-proposal-1]dis this 2022-10-15 01:44:18.470 # ike proposal 1 encryption-algorithm aes-256 dh group14 authentication-algorithm sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256 # return [FW3-ike-proposal-1]ike peer HQ //ike对等体使用version1 [FW3-ike-peer-HQ]ike-proposal 1 [FW3-ike-peer-HQ]undo version 2 [FW3-ike-peer-HQ]pre-shared-key Huawei@123 [FW3-ike-peer-HQ]remote-address 202.100.1.100 [FW3-ike-peer-HQ]acl number 3000 //感兴趣流 [FW3-acl-adv-3000]rule permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255 [FW3-acl-adv-3000]ipsec proposal 1 //ipsec提议保持一致 [FW3-ipsec-proposal-1]dis this 2022-10-15 01:47:29.350 # ipsec proposal 1 esp authentication-algorithm sha2-256 esp encryption-algorithm aes-256 # return [FW3-ipsec-proposal-1]ipsec policy ipsec1 1 isakmp //ipsec策略 [FW3-ipsec-policy-isakmp-ipsec1-1]security acl 3000 [FW3-ipsec-policy-isakmp-ipsec1-1]ike-peer HQ [FW3-ipsec-policy-isakmp-ipsec1-1]proposal 1 [FW3-ipsec-policy-isakmp-ipsec1-1]interface GigabitEthernet1/0/0 //接口下调用ipsec策略 [FW3-GigabitEthernet1/0/0]ipsec policy ipsec1
3.3.5 安全配置
HRP_M[FW1]security-policy (+B) HRP_M[FW1-policy-security]rule name ipsec (+B) HRP_M[FW1-policy-security-rule-ipsec]source-zone local untrust (+B) HRP_M[FW1-policy-security-rule-ipsec]destination-zone local untrust (+B) HRP_M[FW1-policy-security-rule-ipsec]source-address address-set ipsec (+B) HRP_M[FW1-policy-security-rule-ipsec]destination-address address-set ipsec (+B) HRP_M[FW1-policy-security-rule-ipsec]service ISAKMP esp (+B) HRP_M[FW1-policy-security-rule-ipsec]action permit (+B) HRP_M[FW1-policy-security-rule-ipsec]rule name vpn_pc (+B) HRP_M[FW1-policy-security-rule-vpn_pc]source-zone trust untrust (+B) HRP_M[FW1-policy-security-rule-vpn_pc]destination-zone trust untrust (+B) HRP_M[FW1-policy-security-rule-vpn_pc]source-address address-set vpn_pc (+B) HRP_M[FW1-policy-security-rule-vpn_pc]destination-address address-set vpn_pc (+B) HRP_M[FW1-policy-security-rule-vpn_pc]action permit (+B)
[FW3]security-policy [FW3-policy-security]rule name ipsec [FW3-policy-security-rule-ipsec]source-zone local untrust [FW3-policy-security-rule-ipsec]destination-zone local untrust [FW3-policy-security-rule-ipsec]source-address address-set ipsec [FW3-policy-security-rule-ipsec]destination-address address-set ipsec [FW3-policy-security-rule-ipsec]service ISAKMP esp [FW3-policy-security-rule-ipsec]action permit [FW3-policy-security-rule-ipsec]rule name vpn_pc [FW3-policy-security-rule-vpn_pc]source-zone trust untrust [FW3-policy-security-rule-vpn_pc]destination-zone trust untrust [FW3-policy-security-rule-vpn_pc]source-address address-set vpn_pc [FW3-policy-security-rule-vpn_pc]destination-address address-set vpn_pc [FW3-policy-security-rule-vpn_pc]action permit
3.4现象测试
3.4.1双机热备
1.查看vrrp组状态
HRP_M[FW1]display vrrp brief 2022-10-15 01:52:33.360 Total:2 Master:2 Backup:0 Non-active:0 VRID State Interface Type Virtual IP ---------------------------------------------------------------- 1 Master GE1/0/1 Vgmp 202.100.1.100 2 Master GE1/0/0 Vgmp 10.1.1.100 HRP_S[FW2]display vrrp brief 2022-10-15 01:52:41.780 Total:2 Master:0 Backup:2 Non-active:0 VRID State Interface Type Virtual IP ---------------------------------------------------------------- 1 Backup GE1/0/1 Vgmp 202.100.1.100 2 Backup GE1/0/0 Vgmp 10.1.1.100
2.查看HRP状态
HRP_S[FW2]display hrp state verbose 2022-10-15 01:53:25.930 Role: standby, peer: active Running priority: 45000, peer: 45000 Backup channel usage: 0.00% Stable time: 0 days, 0 hours, 34 minutes Last state change information: 2022-10-15 1:19:14 HRP link changes to up. Configuration: hello interval: 1000ms preempt: 60s mirror configuration: off mirror session: off track trunk member: on auto-sync configuration: on auto-sync connection-status: on adjust ospf-cost: on adjust ospfv3-cost: on adjust bgp-cost: on nat resource: off Detail information: GigabitEthernet1/0/1 vrrp vrid 1: standby GigabitEthernet1/0/0 vrrp vrid 2: standby ospf-cost: +65500 ospfv3-cost: +65500 bgp-cost: +100
3.4.2 IPSec建立
1.使用PC1 主动向 PC2发起通信
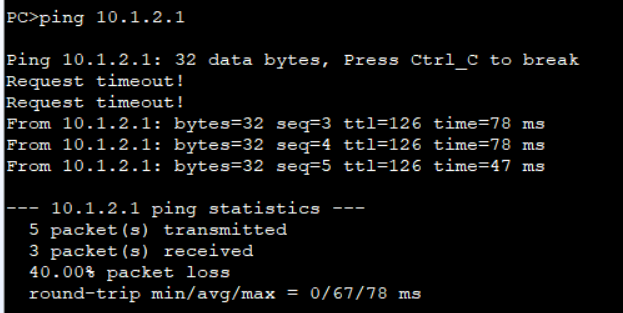
2.IPSec协商成功
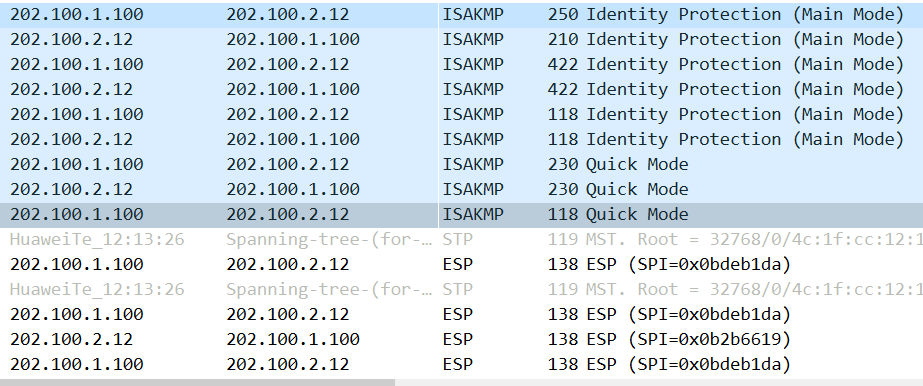
HRP_M[FW1]dis ike sa 2022-10-15 02:08:45.450 IKE SA information : Conn-ID Peer VPN Flag(s) Phase RemoteType RemoteID ------------------------------------------------------------------------------------------------------------------------------------ 7 202.100.2.12:500 RD|ST|M v1:2 IP 202.100.2.12 6 202.100.2.12:500 RD|ST|M v1:1 IP 202.100.2.12 Number of IKE SA : 2 ------------------------------------------------------------------------------------------------------------------------------------ Flag Description: RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO--TIMEOUT HRT--HEARTBEAT LKG--LAST KNOWN GOOD SEQ NO. BCK--BACKED UP M--ACTIVE S--STANDBY A--ALONE NEG--NEGOTIATING
HRP_M[FW1]dis ipsec sa 2022-10-15 02:09:02.220 ipsec sa information: =============================== Interface: GigabitEthernet1/0/1 =============================== ----------------------------- IPSec policy name: "ipsec1" Sequence number : 1 Acl group : 3000 Acl rule : 5 Mode : ISAKMP ----------------------------- Connection ID : 7 Encapsulation mode: Tunnel Holding time : 0d 0h 3m 7s Tunnel local : 202.100.1.100:500 Tunnel remote : 202.100.2.12:500 Flow source : 10.1.1.0/255.255.255.0 0/0-65535 Flow destination : 10.1.2.0/255.255.255.0 0/0-65535 [Outbound ESP SAs] SPI: 199143898 (0xbdeb1da) Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128 SA remaining key duration (kilobytes/sec): 10485760/3412 Max sent sequence-number: 5 UDP encapsulation used for NAT traversal: N SA encrypted packets (number/bytes): 4/240 [Inbound ESP SAs] SPI: 187393561 (0xb2b6619) Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128 SA remaining key duration (kilobytes/sec): 10485760/3412 Max received sequence-number: 1 UDP encapsulation used for NAT traversal: N SA decrypted packets (number/bytes): 3/180 Anti-replay : Enable Anti-replay window size: 1024
3.当前流量从主设备出
HRP_M[FW1]display firewall session table verbose protocol icmp 2022-10-15 02:10:07.040 Current Total Sessions : 1 icmp VPN: public --> public ID: c487f5699e0571038ee634a167e Zone: trust --> untrust TTL: 00:00:20 Left: 00:00:19 Recv Interface: GigabitEthernet1/0/0 Interface: GigabitEthernet1/0/1 NextHop: 202.100.1.254 MAC: 0000-0000-0000 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 10.1.1.1:29462 --> 10.1.2.1:2048 PolicyName: vpn_pc
4.断开SW2的G0/0/2,使得双机热备主备切换。观察现象,PC1的通信短暂的终端后恢复。
5.双机热备主备切换
HRP_S[FW2] Oct 15 2022 02:13:12 FW2 HRPI/1/CORE_STATE:1.3.6.1.4.1.2011.6.122.51.2.2.1 The HRP core state changed due to "Unknown". (old_state=normal,new_state=abnormal(active), local_priority=45000, peer_priority=44998) Oct 15 2022 02:13:12 FW2 %%01HRPI/4/CORE_STATE(l)[20]:The HRP core state changed due to "Unknown". (old_state=normal, new_state=abnormal(active), local_priority=45000, peer_priority=44998)
Oct 15 2022 02:13:11 FW1 HRPI/1/CORE_STATE:1.3.6.1.4.1.2011.6.122.51.2.2.1 The HRP core state changed due to "VRRP change to Down". (old_state=normal,new_state=abnormal(standby), local_priority=44998, peer_priority=45000) Oct 15 2022 02:13:11 FW1 %%01PHY/4/STATUSDOWN(l)[11]:GigabitEthernet1/0/1 changed status to down. Oct 15 2022 02:13:11 FW1 %%01IFNET/4/LINK_STATE(l)[12]:The line protocol IP on the interface GigabitEthernet1/0/1 has entered the DOWN state. Oct 15 2022 02:13:11 FW1 %%01HRPI/4/PRIORITY_CHANGE(l)[13]:The priority of the local VGMP group changed. (change_reason="VRRP change to down.", local_old_priority=45000, local_new_priority=44998) Oct 15 2022 02:13:11 FW1 %%01RM/4/IPV4_DEFT_RT_CHG(l)[14]:IPV4 default Route is changed. (ChangeType=Delete, InstanceId=0, Protocol=Static, ExitIf=Unknown, Nexthop=202.100.1.254, Neighbour=0.0.0.0, Preference=60, Label=NULL, Metric=0) Oct 15 2022 02:13:11 FW1 %%01HRPI/4/CORE_STATE(l)[15]:The HRP core state changed due to "VRRP change to Down". (old_state=normal, new_state=abnormal(standby), local_priority=44998, peer_priority=45000)
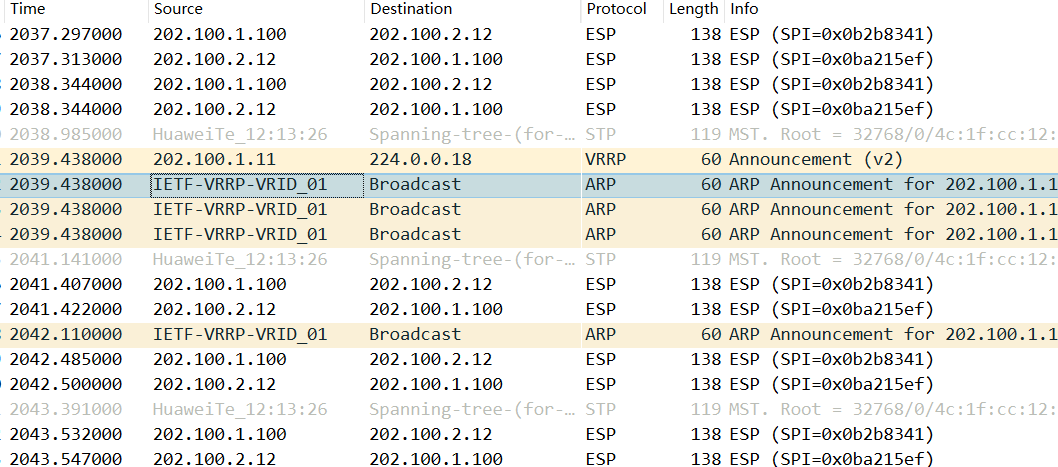
6.并且通过抓包发现过程中并没有重新建立IPSec
HRP_S[FW1]display ike sa 2022-10-15 02:16:47.890 IKE SA information : Conn-ID Peer VPN Flag(s) Phase RemoteType RemoteID ------------------------------------------------------------------------------------------------------------------------------------ 7 202.100.2.12:500 RD|ST|S v1:2 IP 202.100.2.12 6 202.100.2.12:500 RD|ST|S v1:1 IP 202.100.2.12 Number of IKE SA : 2 ------------------------------------------------------------------------------------------------------------------------------------ Flag Description: RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO--TIMEOUT HRT--HEARTBEAT LKG--LAST KNOWN GOOD SEQ NO. BCK--BACKED UP M--ACTIVE S--STANDBY A--ALONE NEG--NEGOTIATING



 浙公网安备 33010602011771号
浙公网安备 33010602011771号