NGFW-虚拟系统互访NAT
一,拓扑
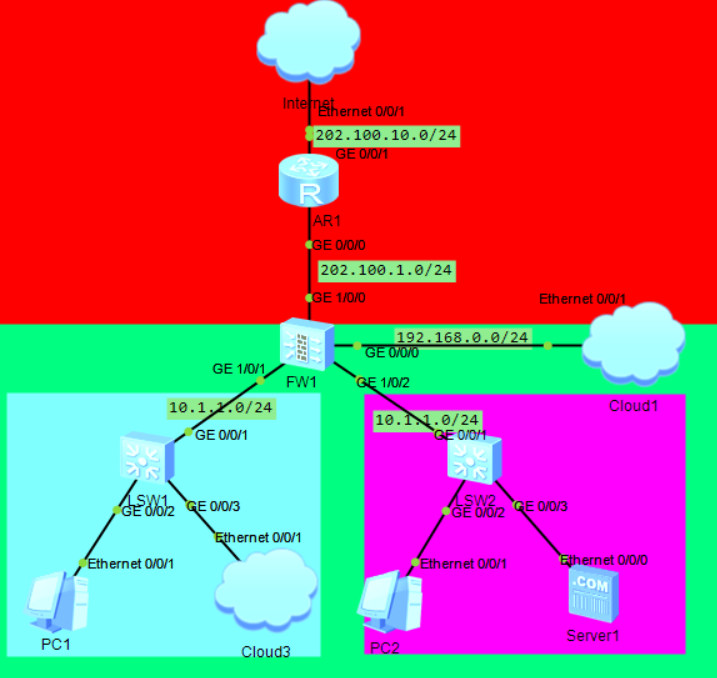
二,实验需求
①配置Cloud3做NAPT,配置Server1为NAT-Server,使Cloud3可以通过2.2.2.2访问Server1。
②配置PC1,PC2做源目双向NAT。
三,NAPT与NAT Server互访
3.1配置
1.根墙分配地址
[FW1]vsys name VSYSA [FW1-vsys-VSYSA]assign global-ip 1.1.1.1 1.1.1.2 free [FW1-vsys-VSYSA]vsys name VSYSB [FW1-vsys-VSYSB]assign global-ip 2.2.2.1 2.2.2.2 free
2.虚拟系统VSYSA配置Cloud3做NAPT
[FW1-VSYSA]nat address-group Cloud3_NAPT [FW1-VSYSA-vsys-address-group-Cloud3_NAPT]section 1.1.1.1 1.1.1.1 [FW1-VSYSA-policy-nat]rule name Cloud3_NAPT [FW1-VSYSA-policy-nat-rule-Cloud3_NAPT]source-zone trust [FW1-VSYSA-policy-nat-rule-Cloud3_NAPT]destination-zone untrust [FW1-VSYSA-policy-nat-rule-Cloud3_NAPT]source-address 10.1.1.2 32 [FW1-VSYSA-policy-nat-rule-Cloud3_NAPT]action source-nat address-group Cloud3_NAPT
3.虚拟系统VSYSA的安全策略
# rule name Cloud3 source-zone trust destination-zone untrust source-address 10.1.1.2 mask 255.255.255.255 action permit #
3.虚拟系统VSYSB配置Server1做NAT-Server
[FW1-VSYSB]nat server Server1 zone untrust protocol tcp global 2.2.2.1 2000 inside 10.1.1.2 80 unr-route
4.虚拟系统VSYSB配置安全策略
# security-policy rule name Server1 source-zone untrust destination-zone trust destination-address 10.1.1.2 mask 255.255.255.255 action permit #
5.根墙配置路由
[FW1]ip route-static vpn-instance VSYSA 2.2.2.1 32 vpn-instance VSYSB [FW1]ip route-static 1.1.1.1 32 vpn-instance VSYSA
3.2测试现象
1.Cloud3通过http://2.2.2.1:2000 访问Server1
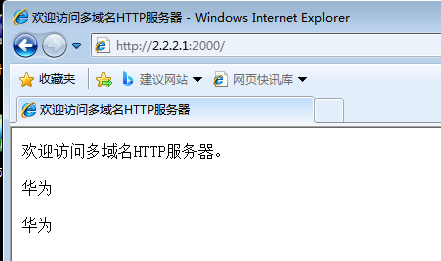
2.查看会话表
VSYSA:
[FW1-VSYSA]display firewall session table verbose 2022-10-07 03:22:40.340 Current Total Sessions : 2 sccp VPN: VSYSA --> VSYSB ID: c287f903ee459602c633f9b69 Zone: trust --> untrust TTL: 00:20:00 Left: 00:19:51 Recv Interface: GigabitEthernet1/0/1 Interface: Virtual-if1 NextHop: 0.0.0.0 MAC: 0000-0000-0000 <--packets: 4 bytes: 778 --> packets: 6 bytes: 858 10.1.1.2:49167[1.1.1.1:2053] --> 2.2.2.1:2000 PolicyName: Cloud3 TCP State: established
VSYSB:
[FW1-VSYSB]display firewall session table verbose 2022-10-07 03:23:23.870 Current Total Sessions : 2 http VPN: VSYSB --> VSYSB ID: c387f903ee45a489d4633f9b69 Zone: untrust --> trust TTL: 00:20:00 Left: 00:19:08 Recv Interface: Virtual-if2 Interface: GigabitEthernet1/0/2 NextHop: 10.1.1.2 MAC: 5489-9826-5813 <--packets: 4 bytes: 778 --> packets: 6 bytes: 858 1.1.1.1:2053 --> 2.2.2.1:2000[10.1.1.2:80] PolicyName: Server1 TCP State: established
四,配置双向NAT互访
4.1配置
1.上面分配的地址池资源不够用,分配10.1.1.3地址给VSYSA和VSYSB
[FW1]vsys name VSYSA [FW1-vsys-VSYSA]assign global 10.1.1.3 10.1.1.3 free [FW1]vsys name VSYSB [FW1-vsys-VSYSB]assign global 10.1.1.3 10.1.1.3 free
2.配置地址池
VSYSA:
[FW1-VSYSA]nat address-group SNAT1 [FW1-VSYSA-vsys-address-group-SNAT1]section 10.1.1.3 10.1.1.3 [FW1-VSYSA-vsys-address-group-SNAT1]mode no-pat local [FW1-VSYSA]nat address-group SNAT2 [FW1-VSYSA-vsys-address-group-SNAT2]mode no-pat local [FW1-VSYSA-vsys-address-group-SNAT2]section 1.1.1.2 1.1.1.2
[FW1-VSYSA]destination-nat address-group DNA1 [FW1-VSYSA-vsys-dnat-address-group-DNA1]section 2.2.2.2 2.2.2.2 [FW1-VSYSA]destination-nat address-group DNAT2 [FW1-VSYSA-vsys-dnat-address-group-DNAT2]section 10.1.1.1 10.1.1.1
VSYSB:
[FW1-VSYSB]NAT address-group SNAT1 [FW1-VSYSB-vsys-address-group-SNAT1]section 10.1.1.3 10.1.1.3 [FW1-VSYSB-vsys-address-group-SNAT1]mode no-pat local [FW1-VSYSB]nat address-group SNAT2 [FW1-VSYSB-vsys-address-group-SNAT2]mode no-pat local [FW1-VSYSB-vsys-address-group-SNAT2]section 2.2.2.2 2.2.2.2 [FW1-VSYSB]destination-nat address-group DNAT1 [FW1-VSYSB-vsys-dnat-address-group-DNAT1]section 1.1.1.2 1.1.1.2 [FW1-VSYSB]destination-nat address-group DNAT2 [FW1-VSYSB-vsys-dnat-address-group-DNAT2]section 10.1.1.1 10.1.1.1
3.配置双向NAT策略
VSYSA:
nat-policy rule name NAT01 source-zone trust source-address 10.1.1.1 mask 255.255.255.255 destination-address 10.1.1.3 mask 255.255.255.255 action source-nat address-group SNAT2 action destination-nat static address-to-address address-group DNA1 rule name NAT02 source-zone untrust source-address 2.2.2.2 mask 255.255.255.255 destination-address 1.1.1.2 mask 255.255.255.255 action source-nat address-group SNAT1 action destination-nat static address-to-address address-group DNAT2 #
VSYSB:
# nat-policy rule name NAT01 source-zone trust source-address 10.1.1.1 mask 255.255.255.255 destination-address 10.1.1.3 mask 255.255.255.255 action source-nat address-group SNAT2 action destination-nat static address-to-address address-group DNAT1 rule name NAT02 source-zone untrust source-address 1.1.1.2 mask 255.255.255.255 destination-address 2.2.2.2 mask 255.255.255.255 action source-nat address-group SNAT1 action destination-nat static address-to-address address-group DNAT2 # return
4.2测试现象
1.可以使用10.1.1.3与对端虚拟系统的PC通信。
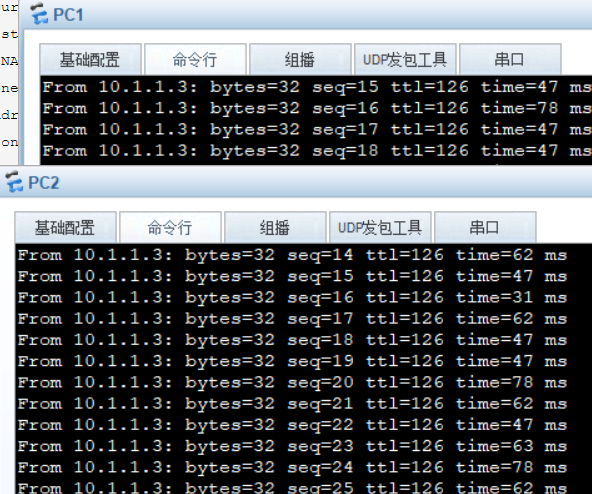
2.查看会话表
[FW1-VSYSB]display firewall session table verbose protocol icmp 2022-10-07 09:47:24.910 Current Total Sessions : 37 icmp VPN: VSYSB --> VSYSB ID: c387fc22e7fbaf8264633ff5a7 Zone: untrust --> trust TTL: 00:00:20 Left: 00:00:15 Recv Interface: Virtual-if2 Interface: GigabitEthernet1/0/2 NextHop: 10.1.1.1 MAC: 5489-9883-2a75 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 1.1.1.2:41461[10.1.1.3:41461] --> 2.2.2.2:2048[10.1.1.1:2048] PolicyName: default icmp VPN: VSYSB --> VSYSA ID: c387fc22e7fd0505a5633ff5a4 Zone: trust --> untrust TTL: 00:00:20 Left: 00:00:12 Recv Interface: GigabitEthernet1/0/2 Interface: Virtual-if2 NextHop: 0.0.0.0 MAC: 0000-0000-0000 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 10.1.1.1:40693[2.2.2.2:40693] --> 10.1.1.3:2048[1.1.1.2:2048] PolicyName: default
[FW1-VSYSA]display firewall session table verbose protocol icmp 2022-10-07 09:48:11.000 Current Total Sessions : 37 icmp VPN: VSYSA --> VSYSB ID: c187fc22e7bcde0e633ff5d7 Zone: trust --> untrust TTL: 00:00:20 Left: 00:00:17 Recv Interface: GigabitEthernet1/0/1 Interface: Virtual-if1 NextHop: 0.0.0.0 MAC: 0000-0000-0000 <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 10.1.1.1:53749[1.1.1.2:53749] --> 10.1.1.3:2048[2.2.2.2:2048] PolicyName: default icmp VPN: VSYSA --> VSYSA ID: c387fc22e7c1908168633ff5d1 Zone: untrust --> trust TTL: 00:00:20 Left: 00:00:11 Recv Interface: Virtual-if1 Interface: GigabitEthernet1/0/1 NextHop: 10.1.1.1 MAC: 5489-9866-3bdb <--packets: 1 bytes: 60 --> packets: 1 bytes: 60 2.2.2.2:52213[10.1.1.3:52213] --> 1.1.1.2:2048[10.1.1.1:2048] PolicyName: default



 浙公网安备 33010602011771号
浙公网安备 33010602011771号