Authorization Concept in SAP
Authorization Concept in SAP
Authorization Concept
The R/3 authorization concept allows you to protect transactions and programs from unauthorized use. R/3 does not allow a user to execute transactions or programs, unless he or she has explicitly defined authorizations for the activity.
To accomplish this, R/3 programs and transactions include authority checks, which ensure that users have the correct authorizations for an action.
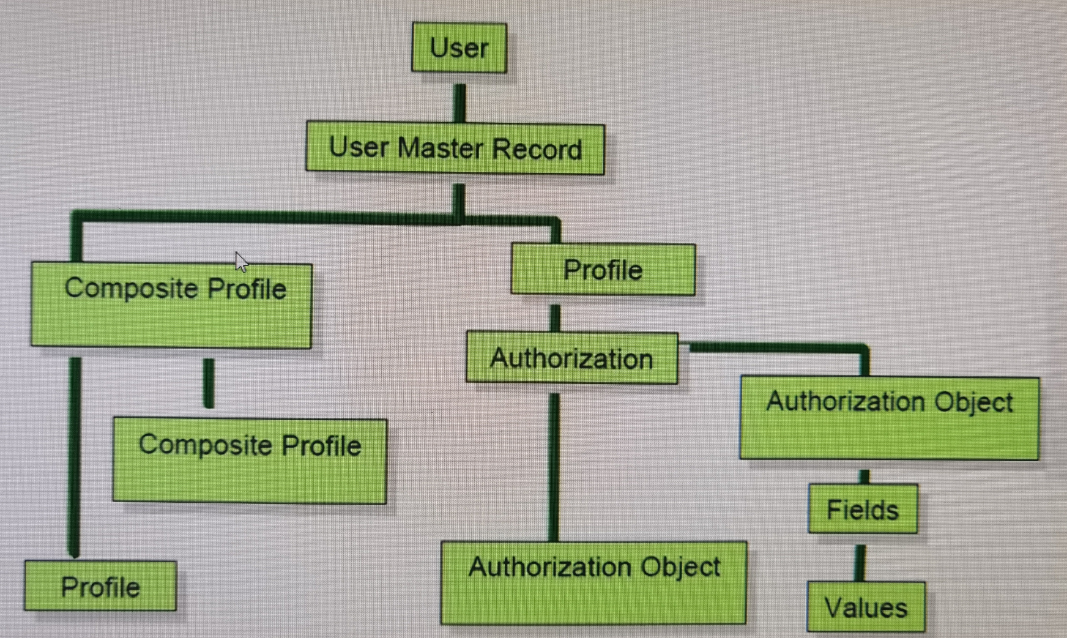
- An authorization object is a template for security that contains fields with blank values (an uncut key)
- Authorization Object may be reused for many transactions
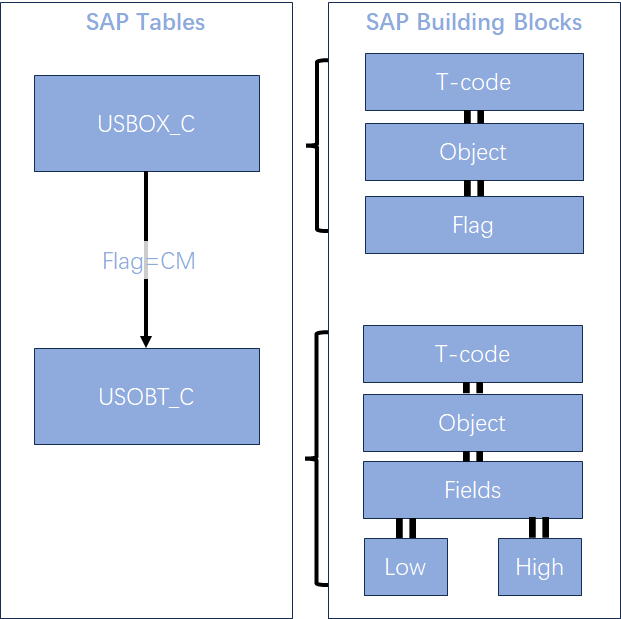
- Authorization Objects and Field Values are stored in two key SAP tables
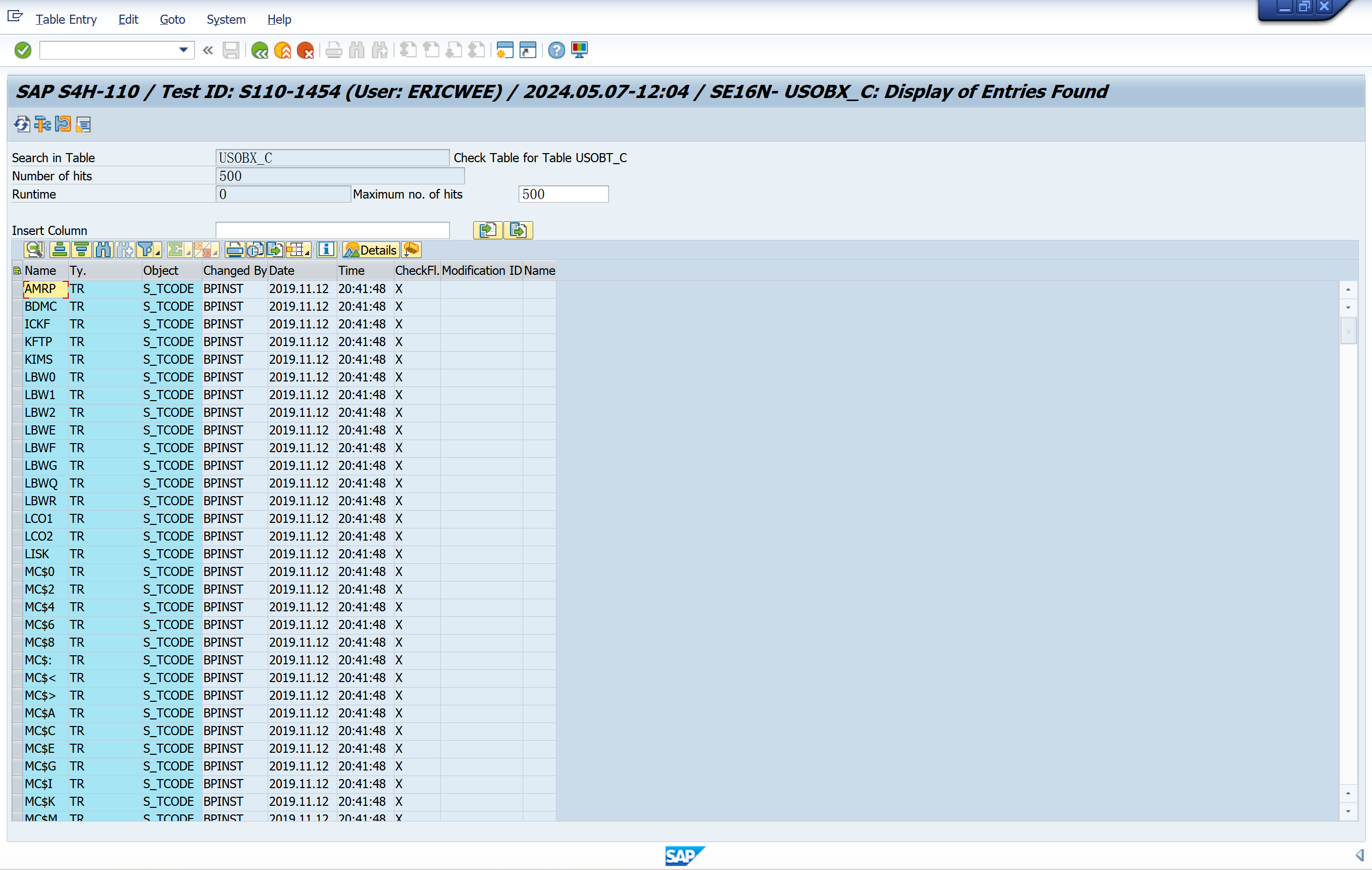
- USOBX_C: Transaction-to-object relationships
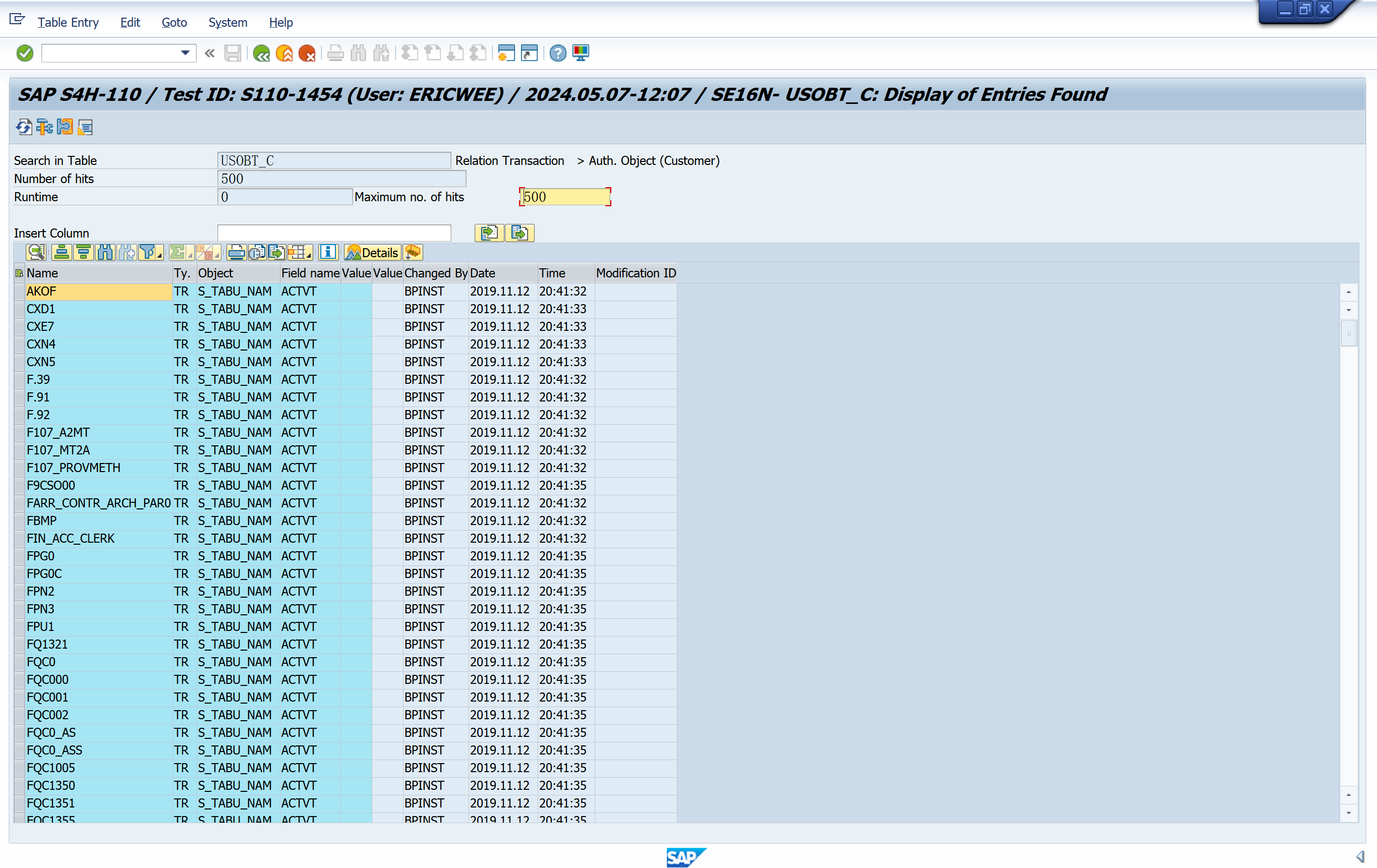
- USOBT_C: Transaction-to-object field value relationships
- Both tables are maintained via transaction code SU24 and used by PFCG (Profile Generator)
- An authorization is an authorization object with completed fields (a cut key)
- It takes one or more "keys" to open the doors to access a particular risk, or transaction, within SAP
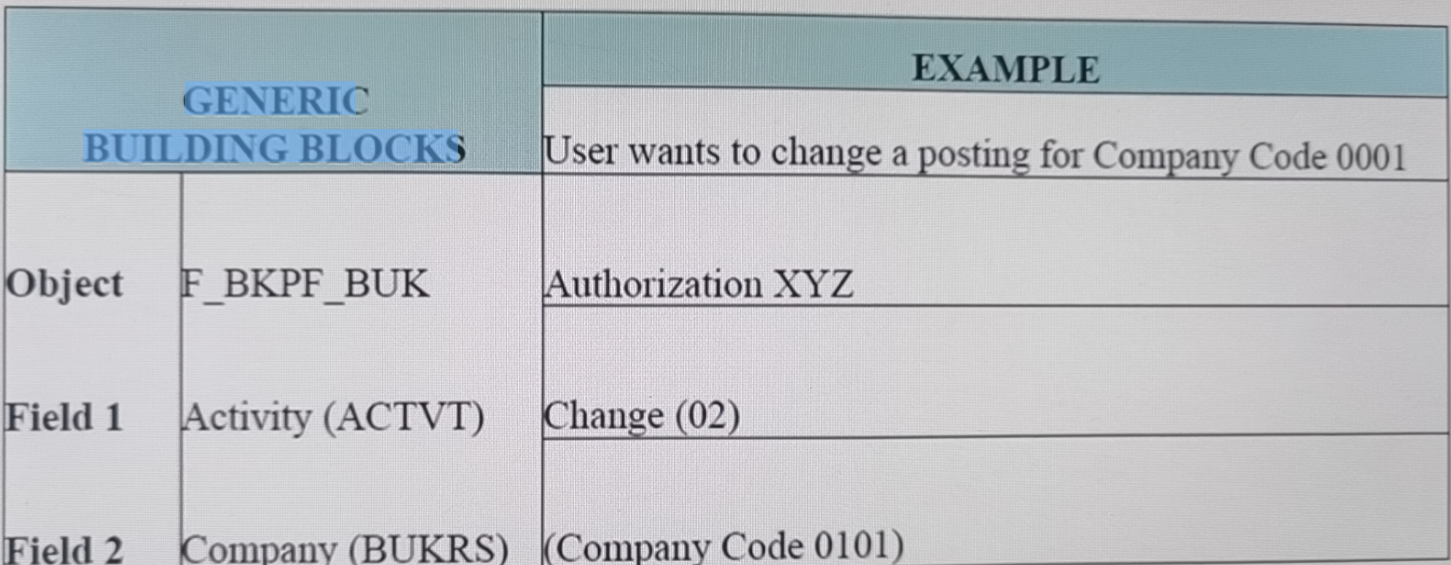
Field and Activity Auth Field is the least granular object that we can restrict.
Authorizations Provide Authorizations based on authorization Objects assigned in that authorization Profile
Authorization Object Grouping of Authorization field
Auth. Object Class Grouping of Authorization objects
Profile Provide authorization based on provided authorization objects and authorizations.
Role Collection of menu's, auth profiles and personalizations.
Example of Authorizations
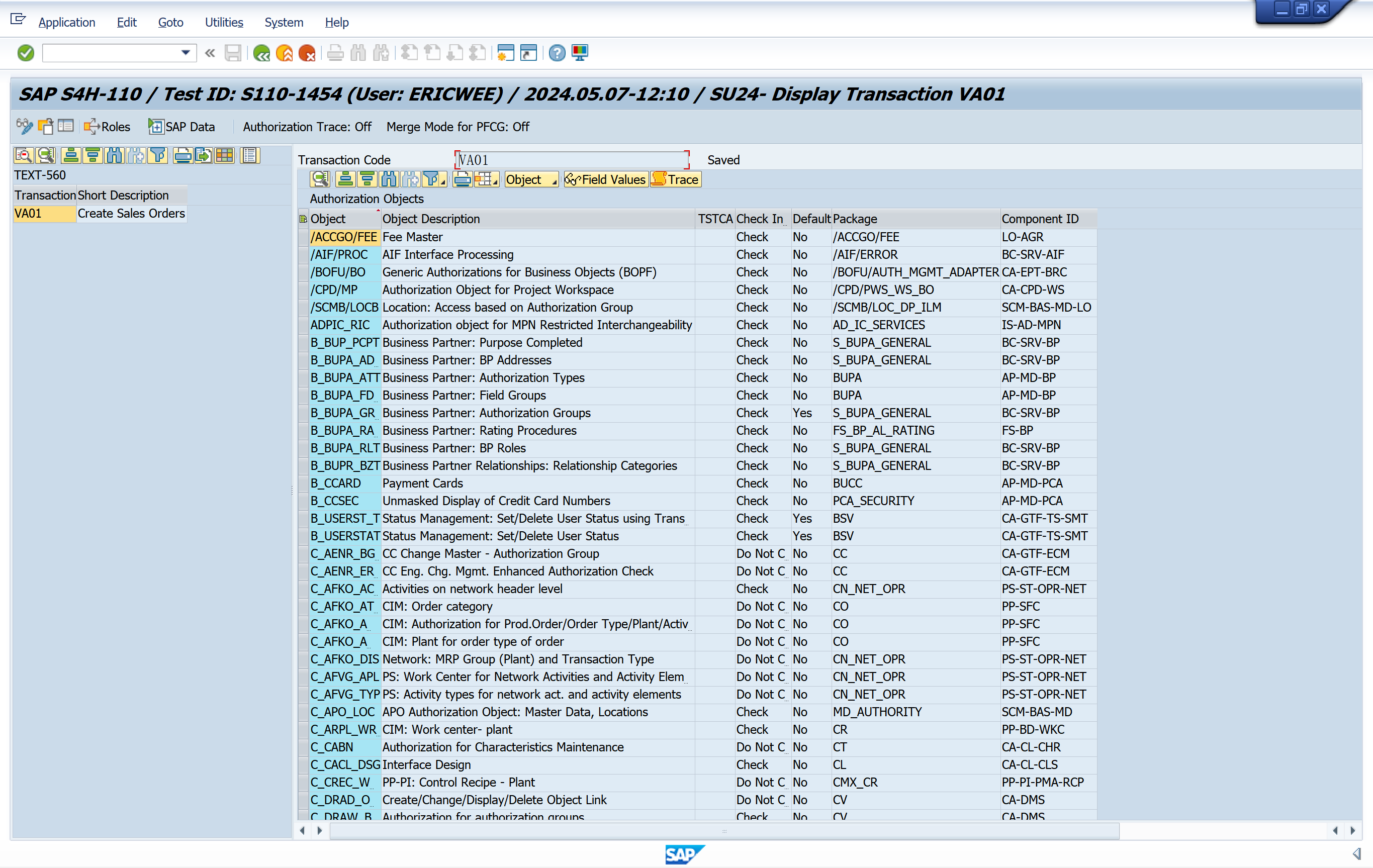
Relationship of Authorizations to T-Codes
Maintains the USOBX_C table
-
T-code to object relationship and special handling flag
![image-20240507120646662]()
Maintains the USBOT_C table
-
T-code to object to default field value relationship
![image-20240507120753862]()
These tables are client independent. Modifications via transaction code SU24 modifications will affect all clients in an SAP system.




 浙公网安备 33010602011771号
浙公网安备 33010602011771号