Penetration Test - Survey the Target(3)
Application and Open-Source Resources
DECOMPILATION
- Complier - translates source code into executable instructions
- Decompiler - attempts to convert executable instructions back into source code
- Output is generally awkward to read at best
- Sometimes target is not a direct executable(i.e. Jave)
DEBUGGING
-
Running an executable in a controlled manner
-
Debuggers make it easy to stop and examine memory at will
-
Can reveal a program's secrets and weaknesses
-
Tools - Windbg
OPEN SOURCE INTELLIGENCE GATHERING
- Open Source Intelligence Gathering(OSINT)
- Sources of research
- CERT(Computer Emergency Response Team) - https://us-cert.cisa.gov/
![image-20200802204901044]()
- NIST(National Institute of Standards and Technology) - https://csrc.nist.gov/
![image-20200802205230599]()
- JPCERT(Japan's CERT) - https://www.jpcert.or.jp/english/vh/project.html
![image-20200802205617992]()
- CAPEC(Common Attack Pattern Enumeration & Classification) - http://capec.mitre.org/
![image-20200802205947064]()
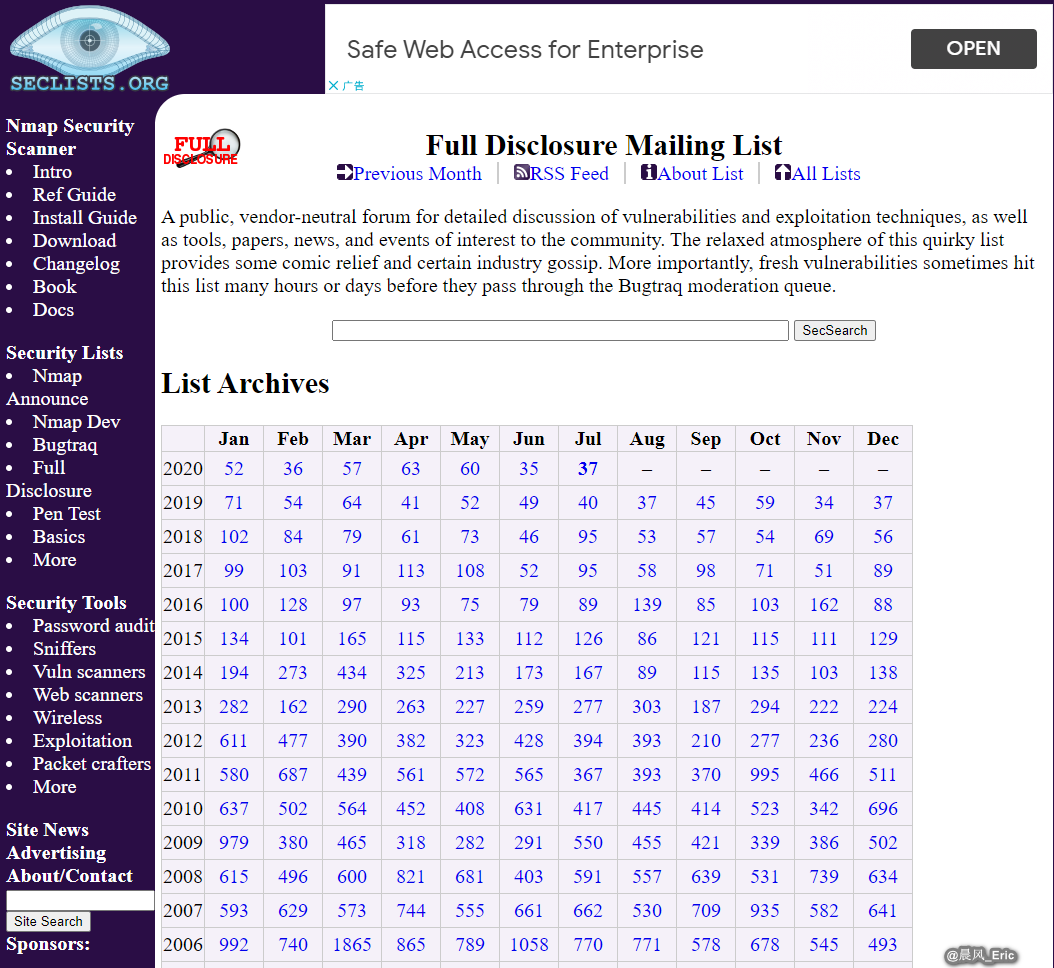
- Full disclosure - Popular mailing list from the folks who brought us nmap - https://seclists.org/fulldisclosure/
![image-20200802210245515]()
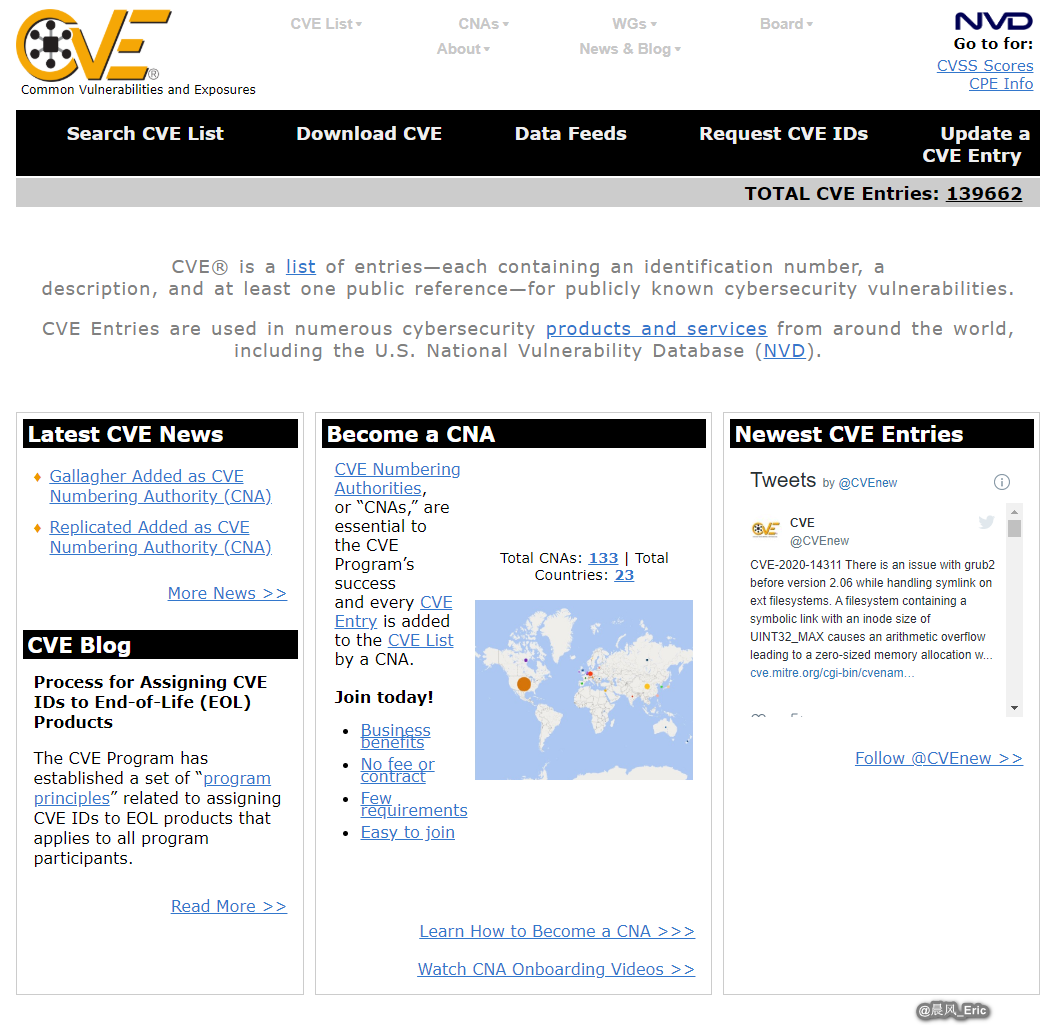
- CVE(Common Vulnerabilities and Exposures) - https://cve.mitre.org/
![image-20200802210521984]()
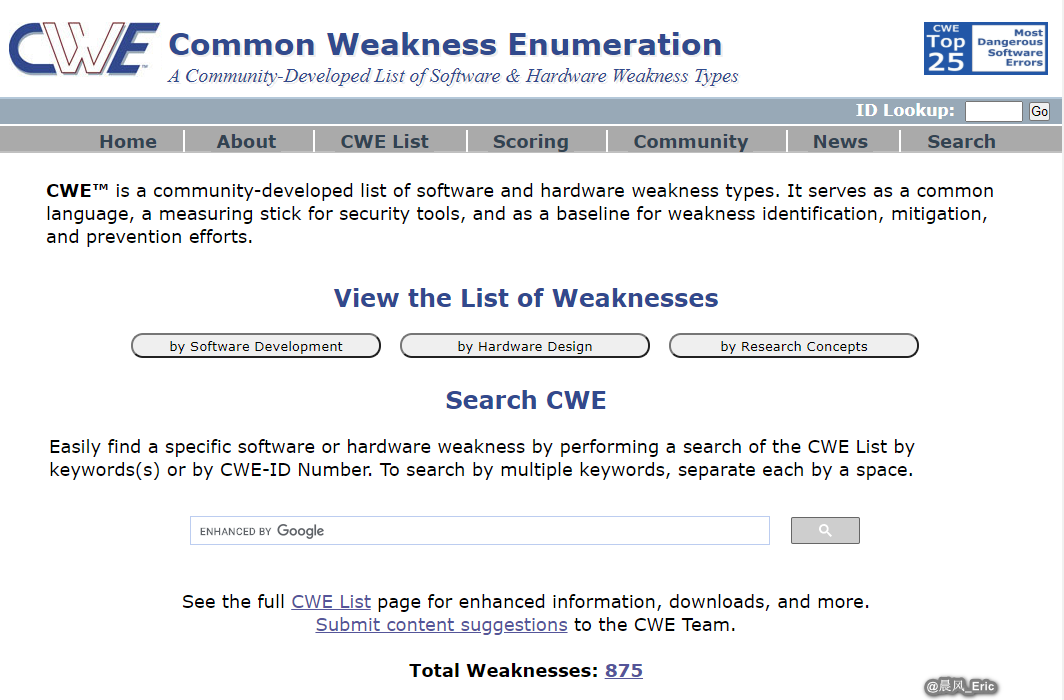
- CWE(Common Weakness Enumeration) - https://cwe.mitre.org/
![image-20200802210847557]()
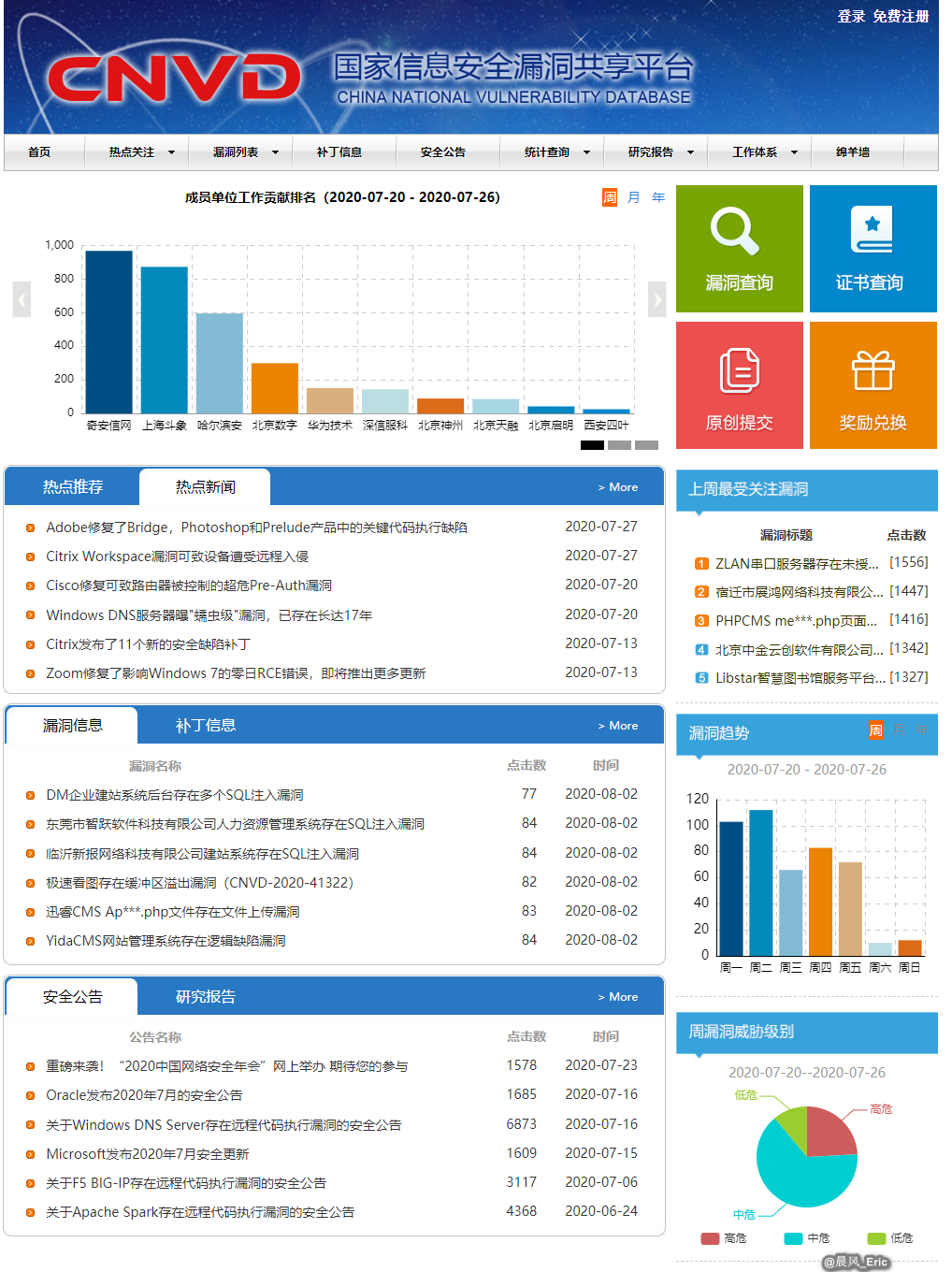
- CNVD(China National Vulnerability Database) - https://www.cnvd.org.cn/
![image-20200802211304812]()
- CERT(Computer Emergency Response Team) - https://us-cert.cisa.gov/
QUICK REVIEW
- Decompilers and debuggers can help to see what a program is doing.
- Lots of useful attack information is available online
- Use scan output to determine target vulnerabilities
- Efficient penetration testing depends on correlated information
相信未来 - 该面对的绝不逃避,该执著的永不怨悔,该舍弃的不再留念,该珍惜的好好把握。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号