OSCP Learning Notes - Post Exploitation(3)
Post-Exploit Password Attacks
1. Crack using the tool - john (Too slow in real world)
Locate the rockyou file.

john --wordlist=/usr/share/wordlists/rockyou.txt windows
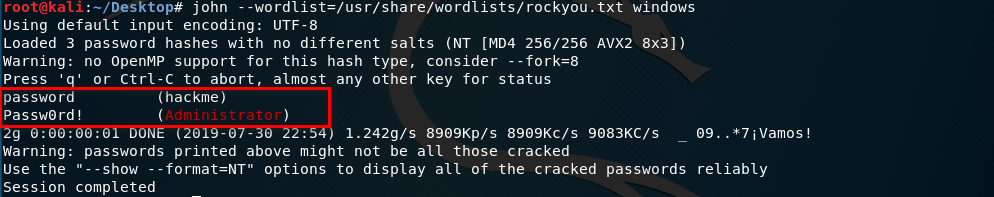
john --show windows

Conbine the files and save as unshadow.
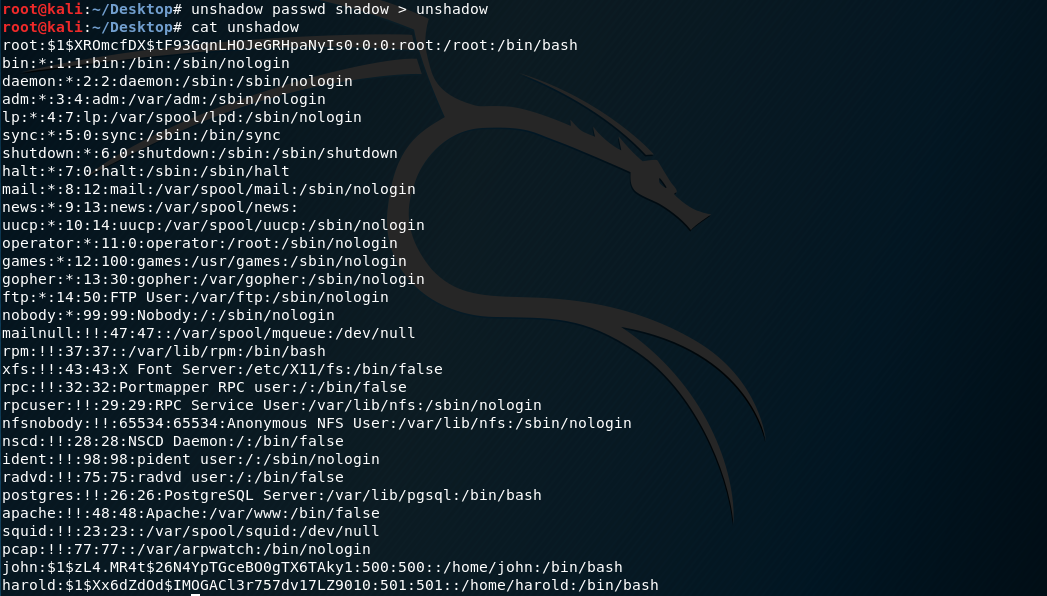
john --rules --wordlist=/usr/share/wordlists/rockyou.txt unshadow

2.Using Hash craker on the Internet. (Suggested)
8846F7EAEE8FB117AD06BDD830B7586C

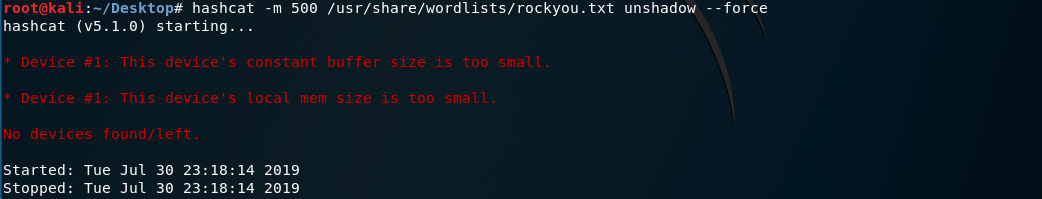
3. Use the tool hashcat
On Kali Linux.(Too slow locally)
hashcat -m 500 /usr/share/wordlists/rockyou.txt unshadow --force
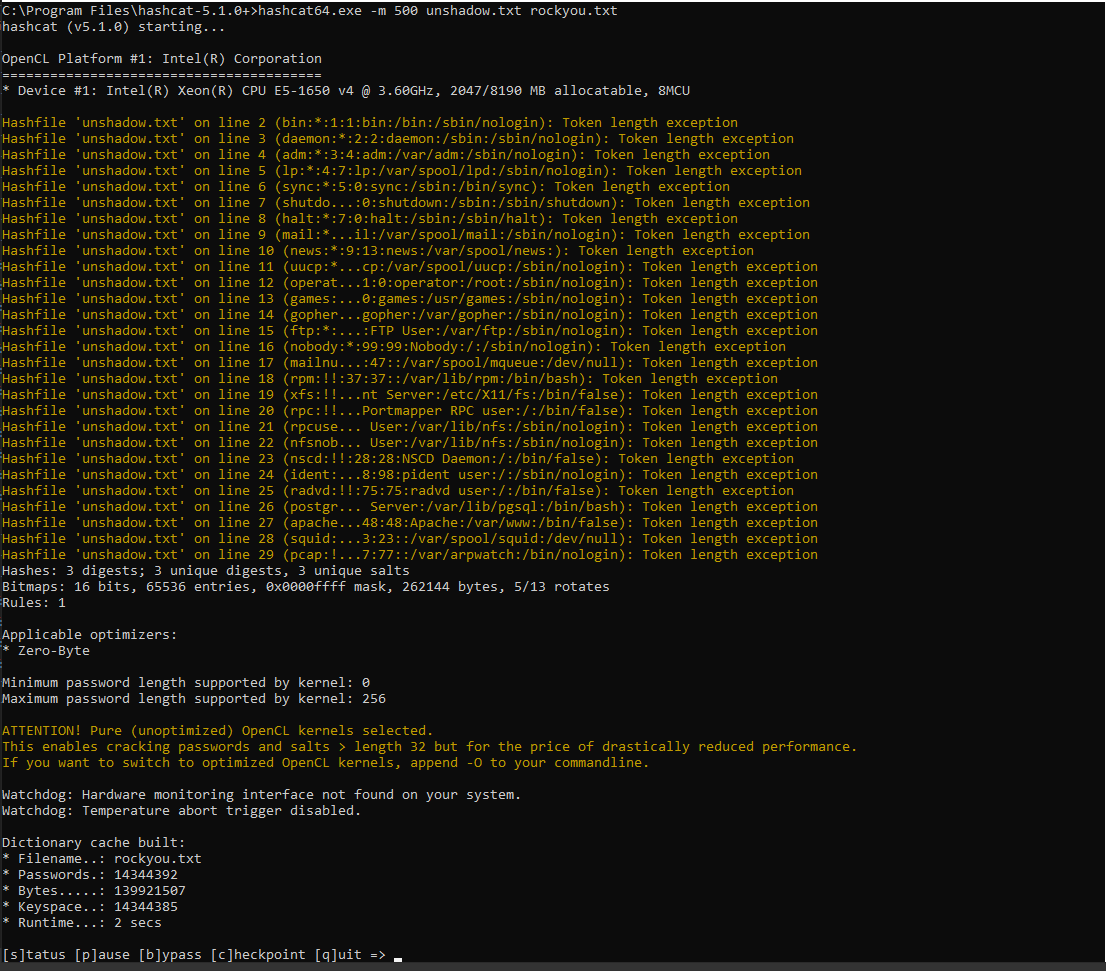
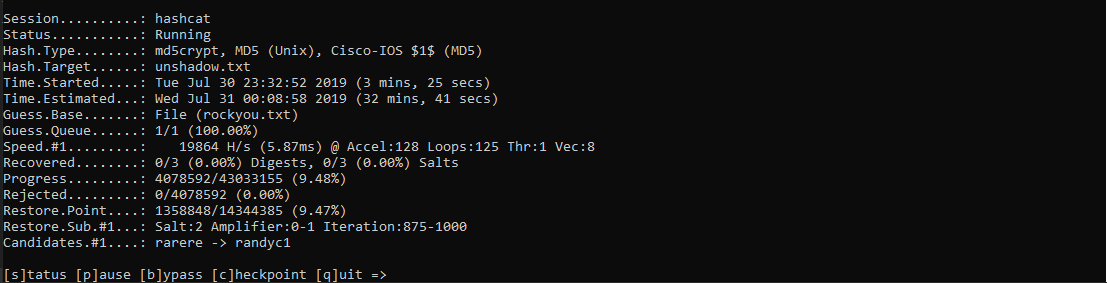
On Windows
hashcat64.exe -m 500 unshadow.txt rockyou.txt
Hash Craker Websites:
Tips: If it is hard to crack the password, do not waste time on it. Just skip it and find another way.
相信未来 - 该面对的绝不逃避,该执著的永不怨悔,该舍弃的不再留念,该珍惜的好好把握。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号