Hw-09 Security and Cryptography
1. Entropy
-
Suppose a password is chosen as a concatenation of four lower-case dictionary words, where each word is selected uniformly at random from a dictionary of size 100,000. An example of such a password is
correcthorsebatterystaple. How many bits of entropy does this have?`log_2(100,000^4) ≈ 19` -
Consider an alternative scheme where a password is chosen as a sequence of 8 random alphanumeric characters (including both lower-case and upper-case letters). An example is
rg8Ql34g. How many bits of entropy does this have?
log_2(61^8) ≈ 47
- Which is the stronger password?
The entropy of the second is greater than the first, and entropy describe the strength of the password, so the second is more stronger.
-
Suppose an attacker can try guessing 10,000 passwords per second. On average, how long will it take to break each of the passwords?
1e16 seconds for the first and roughly 2e10 for the second.
2. Cryptographic hash functions
Download a Debian image from a mirror (e.g. from this Argentinean mirror). Cross-check the hash (e.g. using the sha256sum command) with the hash retrieved from the official Debian site (e.g. this file hosted at debian.org, if you’ve downloaded the linked file from the Argentinean mirror).
3. Symmetric cryptography
Encrypt a file with AES encryption, using OpenSSL: openssl aes-256-cbc -salt -in {input filename} -out {output filename}. Look at the contents using cat or hexdump. Decrypt it with openssl aes-256-cbc -d -in {input filename} -out {output filename} and confirm that the contents match the original using cmp.
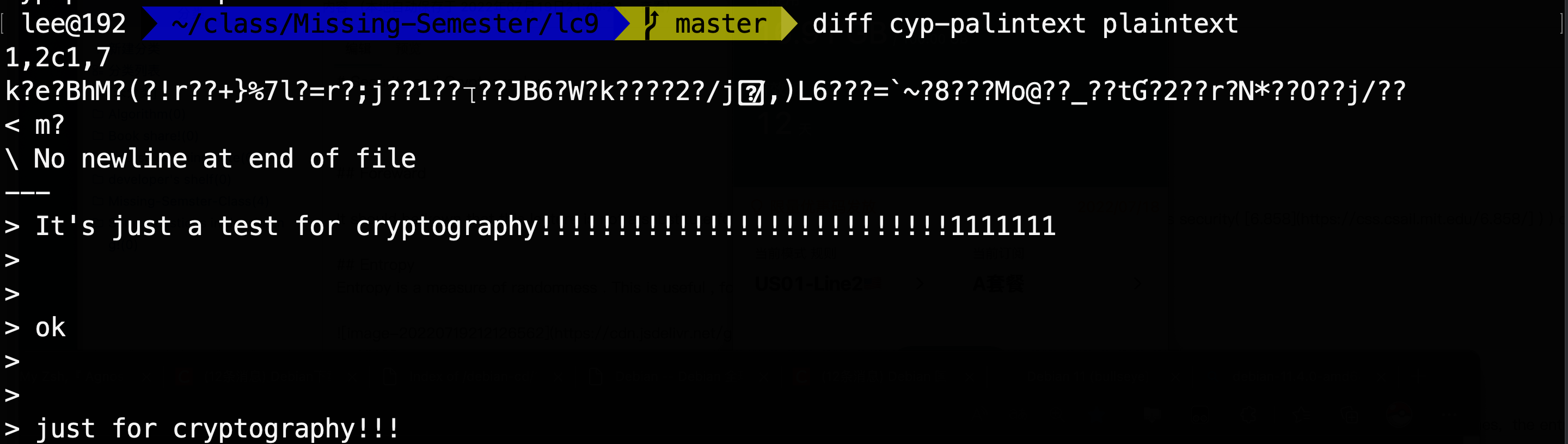

4. Asymmetric cryptography
-
Set up SSH keys on a computer you have access to (not Athena, because Kerberos interacts weirdly with SSH keys). Make sure your private key is encrypted with a passphrase, so it is protected at rest.
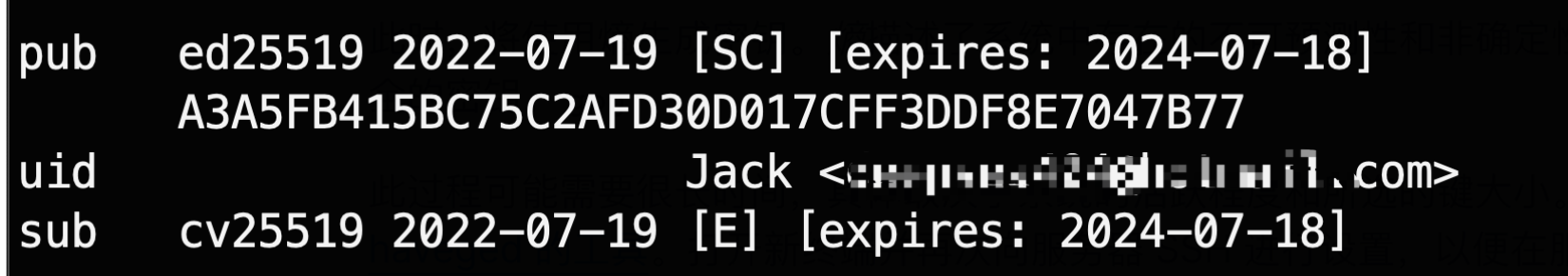
3. Send Anish an encrypted email (public key).
- Sign a Git commit with
git commit -Sor create a signed Git tag withgit tag -s. Verify the signature on the commit withgit show --show-signatureor on the tag withgit tag -v.


 浙公网安备 33010602011771号
浙公网安备 33010602011771号