Security and Cryptography
Foreward
It should be kown that this lecture is not a substitute for a more rigorous and complete course one computer systems security( 6.858 ) or crptography (6.857and 6.875), but it give us general understanding of the programs and protocols we already use.
Hash functions
sha1(bytes)->160bits
lee@LAPTOP-6VVDNARH:~$ printf 'hello' | sha1sum
aaf4c61ddcc5e8a2dabede0f3b482cd9aea9434d -
lee@LAPTOP-6VVDNARH:~$ printf 'Hello' | sha1sum
f7ff9e8b7bb2e09b70935a5d785e0cc5d9d0abf0 -
-
Deterministic
-
non-invertible
-
collision resistant
That is hard to find two different inputs that produce the same output
You need to know that SHA-1 is no longer considered a strong cryptographic hash function.
Look the table of lifetimes of cryptographic hash functions.
Key derivation functions (KDFs)
PBKDF2()
- Slow (in order to slow down offline brute-force attacks)
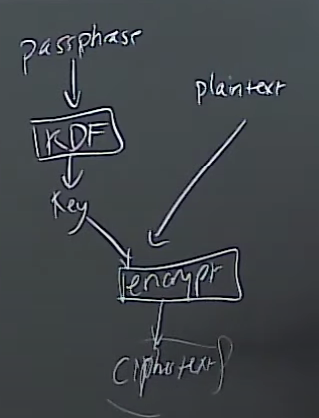
salt, hash(password + salt)
salt is a randomized value
Symmetric key cryptography
-
Keygen() -> key (this fuction is randomized)
-
encrypt(plain text, key) ->cipher text
-
decrypt(cipher text, key)->plain text
given cipher text can't figure out plain text (without the key)
decrypt(encrypt(m, key), key) = m
An example of a symmetric cryptosystem in wide use today is AES.
Encrypting files for storage in an untrusted cloud service. This can be combined with KDFs, so you can encrypt a file with a passphrase. Gnerate key = KDF(passphrase), and then store encrypt(file, key).
Asymmetric key cryptography
- keygen() ->(public key, private key)
- encrypt(p, public key)->C
- decrypt(c, private key)->P
Encrypt something with the public key, and decrypt the ciphertext with the private key, but public key is available to show in the internet or other scenarios.
-
sign(message, private key) ->signature
-
verify(message, public key)->ok?
decrypt(encrypt(m, public key), private key) = m
Feature
- hard to forge (without the key)
- correct
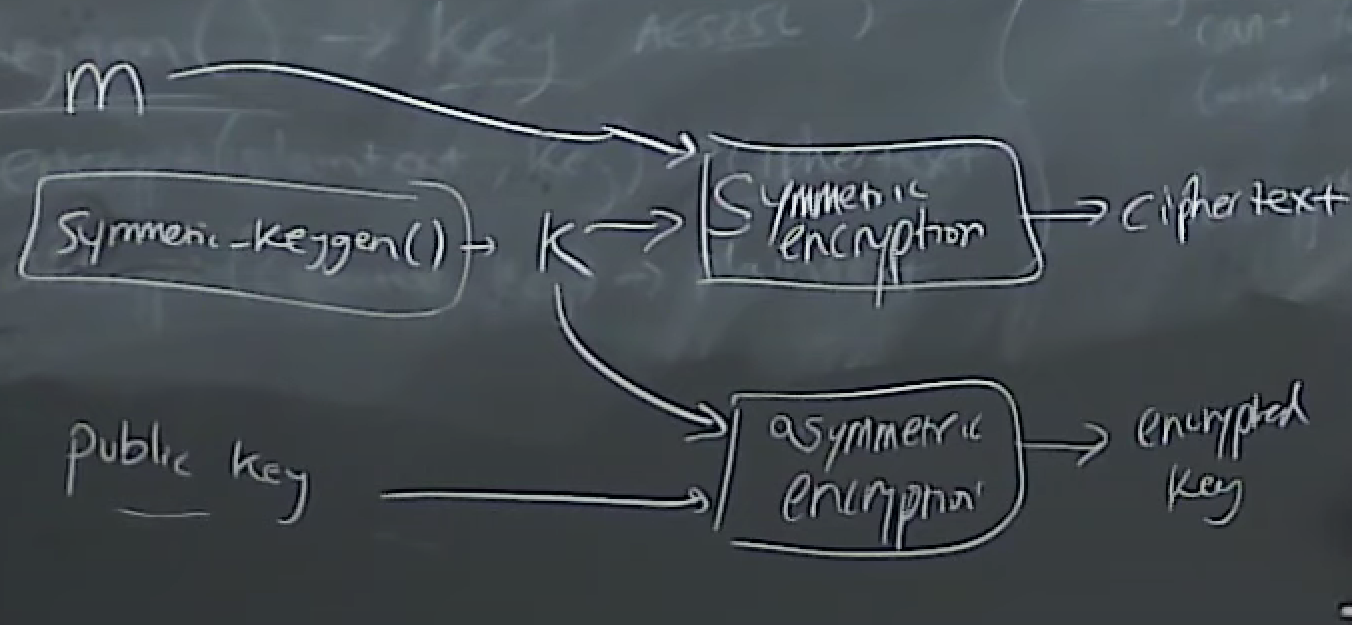
appliction:
-
PGP email encryption. People can have their public keys posted online (e.g. in a PGP keyserver, or on Keybase). Anyone can send them encrypted email.
-
Private messaging. Apps like Signal and Keybase use asymmetric keys to establish private communication channels.
-
Signing software. Git can have GPG-signed commits and tags. With a posted public key, any one can verify the authenticity of downloaded software.
Key distribution
Asymmetric-key cryptography is wonderful, but it has a big challenge of distributing public keys / mapping public keys to real-world identities.
Signal has one simple solution: trust on first use, and support out-of-band public key exchange (you verify your friends’ “safety numbers” in person). PGP has a different solution, which is web of trust. Keybase has yet another solution of social proof (along with other neat ideas). Each model has its merits; we (the instructors) like Keybase’s model.
Case studies
Password managers
A essential tools that everyone should try to use(e.g. . KeePassXC, pass, and 1Password).
encrypted with a symmetric cipher with a key produced from a passphrase using a KDF.
Using a password manager lets you avoid password reuse(so you are less impacted when websites get compromised), use high-entropy passwords(so you are less likely to get compromised), and only need to remeber a single high-entropy password.
Two-factor authentication
Tow-factor-autentication (2FA) requires you to use a passphrase (“something you know”) along with a 2FA authenticator(like a YubiKey, “something you have”) in order to protect against stolen passwords and phishing attacks.
Full disk encryption
Protect your laptop in the case that your laptop is stolen.
cryptsetup + LUKS on linux.
BitLocker on windows.
FileVault on macOS.
This encrypt the entire disk with a symmetric cipher, with a key protected by a passphrase.
Private messaging
Use Signal or Keybase. asymmetric key pair.
SSH
ssh-keygen, it generates an asymmetric keypair(pub_key and pri_key)randomly.
Resources
- Last year’s notes: from when this lecture was more focused on security and privacy as a computer user
- Cryptographic Right Answers: answers “what crypto should I use for X?” for many common X.


 浙公网安备 33010602011771号
浙公网安备 33010602011771号