随笔分类 - ret2libc3合集
摘要:# [HarekazeCTF2019]baby_rop2 64位的ret2libc3 ## 0x01  注意g
阅读全文
摘要:# ret2libc3 ctf-wiki ret2libc3 考点:栈溢出rop ### 0x01 file checksec —— 32-bit 开NX _2018_rop 经典ret2libc3 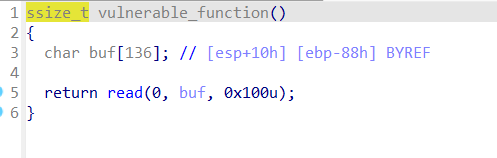 exp ```
阅读全文
摘要:# [OGeek2019]babyrop ## 0x01 64位程序,开启NX 没有system函数和/bin/sh字符串 ## 0x02 分析程序: main函数中,先读取一个随机数到fd,并作为参数传入sub_804871F函数,再将sub_804871F函数的返回值作为参数传入sub_8048
阅读全文
摘要:# ciscn_2019_c_1 ### 0x01 简单的ret2libc3 file checksec —— 64-bit 开NX ### 0x02 运行一下看看 


 浙公网安备 33010602011771号
浙公网安备 33010602011771号