前期准备
配置yum
CENTOS vsftpd
rm -rf /etc/yum.repos.d/*
vi /etc/yum.repos.d/1.repo
[1]
name=1
baseurl=http://172.17.15.200/Centos1511
gpgcheck=0
enabled=1
nmtui
ip a
useradd hxl17
passwd hxl17
yum install vsftpd
systemctl start vsftpd
DROP 命令
sudo iptables -A OUTPUT -p tcp --tcp-flags RST RST -d 192.168.17.129 --dport 21 -j DROP
OR
sudo iptables -A OUTPUT -p tcp --tcp-flags RST RST -j DROP
DeepSeek版本输出
from scapy.all import *
import time
import random
target = "192.168.17.129"
dport = 21
sport = random.randint(1024,65535)
# 1. 建立 TCP 三次握手
syn = IP(dst=target)/TCP(sport=sport, dport=dport, flags='S', seq=1000)
syn_ack = sr1(syn, timeout=5)
if not syn_ack:
print("SYN-ACK 未收到,连接失败")
exit()
ack = IP(dst=target)/TCP(sport=sport, dport=dport, flags='A', seq=syn_ack.ack, ack=syn_ack.seq + 1)
send(ack)
print("TCP 连接建立成功")
# 2. 接收服务器的欢迎消息
time.sleep(1) # 等待服务器发送欢迎消息
res = sniff(filter=f"tcp and host {target} and port {dport}", count=1, timeout=5)
if not res:
print("未收到服务器欢迎消息")
exit()
res = res[0]
print(f"收到服务器消息: {res.summary()}")
# 3. 处理欢迎消息,安全地获取数据长度
server_seq = res[TCP].seq
server_ack = res[TCP].ack
# 安全地检查是否有 Raw 层数据
if Raw in res:
data_len = len(res[Raw].load)
welcome_msg = res[Raw].load.decode('utf-8', errors='ignore')
print(f"欢迎消息: {welcome_msg}")
else:
data_len = 0 # 如果没有数据,长度为0
print("服务器响应中没有数据负载")
user_seq = server_ack
user_ack = server_seq + data_len
# 4. 发送 USER 命令
user_pkt = IP(dst=target)/TCP(sport=sport, dport=dport, flags='PA', seq=user_seq, ack=user_ack)/"USER anonymous\r\n"
print("发送 USER 命令...")
user_res = sr1(user_pkt, timeout=5)
if not user_res:
print("USER 命令无响应")
exit()
print(f"USER 响应: {user_res.summary()}")
# 5. 安全处理 USER 响应
if Raw in user_res:
user_data_len = len(user_res[Raw].load)
user_msg = user_res[Raw].load.decode('utf-8', errors='ignore')
print(f"USER 响应消息: {user_msg}")
else:
user_data_len = 0
pass_seq = user_res.ack
pass_ack = user_res.seq + user_data_len
# 6. 发送 PASS 命令
pass_pkt = IP(dst=target)/TCP(sport=sport, dport=dport, flags='PA', seq=pass_seq, ack=pass_ack)/"PASS anonymous\r\n"
print("发送 PASS 命令...")
pass_res = sr1(pass_pkt, timeout=5)
if not pass_res:
print("PASS 命令无响应")
exit()
# 7. 显示登录结果
if Raw in pass_res:
result_msg = pass_res[Raw].load.decode('utf-8', errors='ignore')
print(f"登录结果: {result_msg}")
else:
print("登录响应中没有数据")
# 8. 发送 RST 包关闭连接
rst_seq = pass_seq + len("PASS anonymous\r\n")
rst = IP(dst=target)/TCP(sport=sport, dport=dport, flags='R', seq=rst_seq, ack=pass_ack)
send(rst)
print("连接已关闭")
效果图
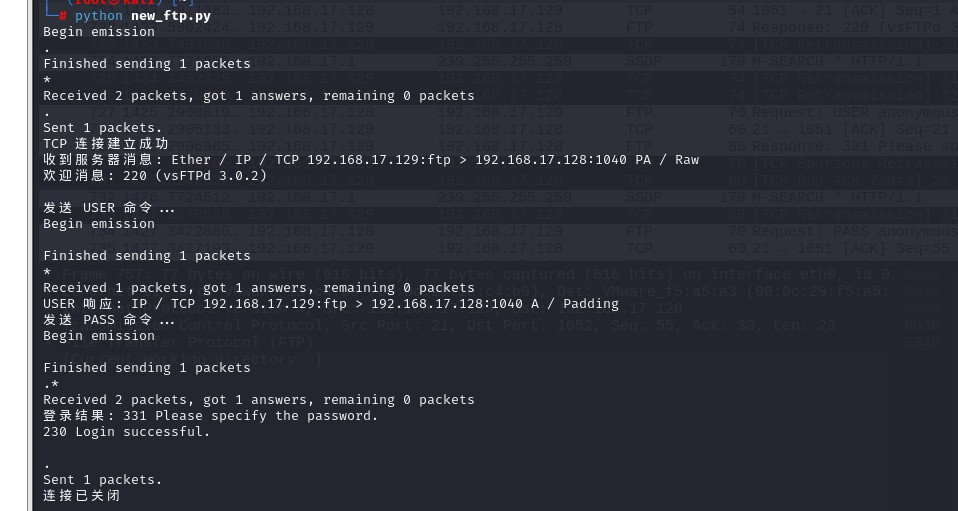
老师加上修改
from scapy.all import *
import time
import random
target = "192.168.17.129"
dport = 21
sport = random.randint(1024,65535)
syn = IP(dst=target)/TCP(sport=sport, dport=dport, flags='S', seq=1000)
syn_ack = sr1(syn,timeout=5)
ack = IP(dst=target)/TCP(sport=sport, dport=dport, flags='A',seq=syn_ack.ack, ack=syn_ack.seq + 1)
send(ack)
time.sleep(1)
res = sniff(filter=f"tcp and host {target} and port {dport}", count=1,timeout=5)
print(res)
res = res[0]
server_seq = res[TCP].seq # 服务器的序列号
server_ack = res[TCP].ack # 服务器的确认号(=1001)
data_len = len(res[Raw].load) # 220 消息长度
user_seq = server_ack # 我们的 seq = 服务器上次 ack
user_ack = server_seq + data_len # 我们的 ack = 服务器 seq + 数据长度
user_pkt = IP(dst=target)/TCP(sport=sport, dport=dport,flags='PA',seq=user_seq,ack=user_ack)/"USER anonymous\r\n"
user_res = sr1(user_pkt,timeout=5)
user_res = sr1(user_pkt,timeout=5)
pass_seq = user_res.ack
user_data_len = len(user_res[Raw].load)
pass_ack = user_res.seq + user_data_len
pass_pkt = IP(dst=target)/TCP(sport=sport, dport=dport,flags='PA',seq=pass_seq,ack=pass_ack)/"PASS anonymous\r\n"
pass_res = sr1(pass_pkt,timeout=5)
pass_res = sr1(pass_pkt,timeout=5)
print(pass_res[Raw].load.decode())
rst = IP(dst=target)/TCP(sport=sport, dport=dport, flags='R', seq=pass_seq + len("PASS anonymous\r\n"), ack=pass_ack)
send(rst)



 浙公网安备 33010602011771号
浙公网安备 33010602011771号