BUUCTF Re部分wp(七)
突然产生了一种连载的感觉。。。
[网鼎杯 2020 青龙组]jocker
32exe,题目本身不难
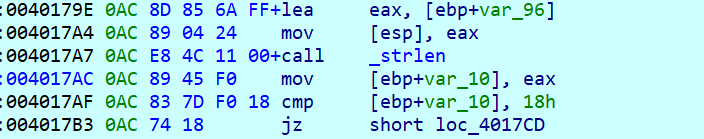
输入长18h,之后有一段smc,不管直接动调得到解密后的__Z7encryptPc
__Z7encryptPc的栈指针有点问题,需要稍微修改一下

逻辑简单,但是少五个值,找到__Z7finallyPc
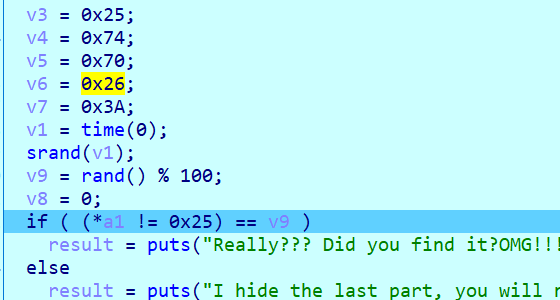
之后我也不知道为啥是与71异或,我的脑洞大概不太够,不过除去最后的”}“只有4位未知,爆破应该也可以
a="hahahaha_do_you_finGGGGG"
b="0e 0d 09 06 13 05 58 56 3e 06 0c 3c 1f 57 14 6b 57 59 0d 25 74 70 26 3a"
b=b.split()
for i in range(len(b)):
print(chr(ord(a[i])^eval("0x"+b[i])),end="")
[V&N2020 公开赛]h01k_re
32exe,这里有许多反调,nop掉
关键在于
跟进去可找到

这里是vm,opcode在

同时有两组长为16的特殊数据,
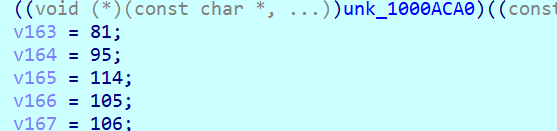

对这两处以及输入下断,可分析得到逻辑为输入异或0x33后加2再与v34异或,最后结果与v163比较
[MRCTF2020]EasyCpp
64elf,输入九个数字
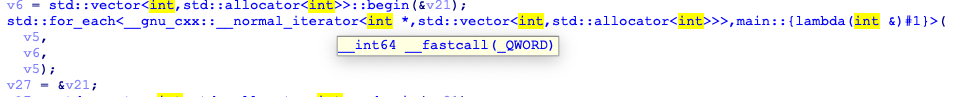
此处对输入的数字^1

depart里通过递归进行了某种操作使是输入分成了多个由空格分割的数字,经测试发现多个数相乘即为输入^1,之后在lambda里进行了替换
对比的值在
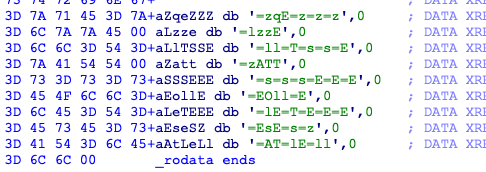
c=['zqE=z=z=z','lzzE','ll=T=s=s=E','zATT','s=s=s=E=E=E','EOll=E','lE=T=E=E=E','EsE=s=z','AT=lE=ll']
t="OlzEAsGTBq"
p=[]
flag=[]
for i in c:
temp=""
for j in i:
if j=="=":
temp+=" "
else :
temp+=str(t.index(j))
p.append(temp)
for i in p:
i=i.split()
f=1
for j in i:
f*=eval(j)
flag.append(f^1)
print(flag)
[WUSTCTF2020]funnyre
64位elf,找到main
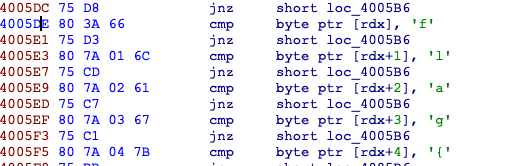
里面数据都很类似,有一些花,不太影响
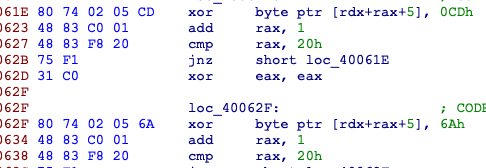
前半部分异或,后半部分加法,异或中间插了一条not和一条add,最后与unk_4025C0比较
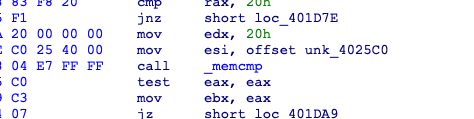
写个idapython
addr = 0x4005b0
b1=[]
b2=[]
c="D9 2C 27 D6 D8 2A DA 2D D7 2C DC E1 DB 2C D9 DD 27 2D 2A DC DB 2C E1 29 DA DA 2C DA 2A D9 29 2A"
c=c.split()
for i in range(len(c)):
c[i]=eval("0x"+c[i])
while(addr<0x401db3):
next_addr = NextHead(addr)
if "byte ptr [rdx+rax+5]" in GetDisasm(addr):
if "xor" in GetDisasm(addr):
b1.append(GetOpnd(addr,1))
if "add" in GetDisasm(addr):
b2.append(GetOpnd(addr,1))
addr = next_addr
else:
addr = next_addr
b1.reverse()
b2.reverse()
for i in range(len(c)):
for j in b2:
if "h" in j:
c[i]-=eval("0x"+j[:-1])
else:
c[i]-=eval(j)
c[i]+=0x80
for k in range(len(b1)):
if "h" in b1[k]:
c[i]^=eval("0x"+b1[k][:-1])
else:
c[i]^=eval(b1[k])
if b1[k]=="0C9h":
c[i]-=0x80
if b1[k]=="0F9h":
c[i]=~c[i]
c[i]=c[i]&0xfffor i in range(len(c)):
c[i]=chr(c[i])
print c
[MRCTF2020]VirtualTree
这题的源码给了,不详细说了
题目用了个二叉树,加密为以下两个函数

都比较简单,有几处简单的花也没什么影响 ,调着看就行
[UTCTF2020]png2
一张图片,开头告诉了高度和宽度,以raw打开修改高和宽,得到flag
[watevrCTF 2019]Timeout
64elf,拖进ida

genearte为flag所在处,明文,打个补丁得到flag
[watevrCTF 2019]Repyc
python逆向,uncompyle6
佤 = 0
侰 = ~佤 * ~佤
俴 = 侰 + 侰
def 䯂(䵦):
굴 = 佤
굿 = 佤
괠 = [
佤] * 俴 ** (俴 * 俴)
궓 = [
佤] * 100
괣 = []
while 䵦[굴][佤] != '\xeb\x93\x83':
굸 = 䵦[굴][佤].lower()
亀 = 䵦[굴][侰:]
if 굸 == '\xeb\x89\x83':
괠[亀[佤]] = 괠[亀[侰]] + 괠[亀[俴]]
elif 굸 == '\xeb\xa0\x80':
괠[亀[佤]] = 괠[亀[侰]] ^ 괠[亀[俴]]
elif 굸 == '\xeb\xa0\xb3':
괠[亀[佤]] = 괠[亀[侰]] - 괠[亀[俴]]
elif 굸 == '\xeb\x83\x83':
괠[亀[佤]] = 괠[亀[侰]] * 괠[亀[俴]]
elif 굸 == '\xeb\xa2\xaf':
괠[亀[佤]] = 괠[亀[侰]] / 괠[亀[俴]]
elif 굸 == '\xeb\xa5\x87':
괠[亀[佤]] = 괠[亀[侰]] & 괠[亀[俴]]
elif 굸 == '\xeb\xa7\xb3':
괠[亀[佤]] = 괠[亀[侰]] | 괠[亀[俴]]
elif 굸 == '\xea\xb4\xa1':
괠[亀[佤]] = 괠[亀[佤]]
elif 굸 == '\xeb\xab\x87':
괠[亀[佤]] = 괠[亀[侰]]
elif 굸 == '\xea\xbc\x96':
괠[亀[佤]] = 亀[侰]
elif 굸 == '\xeb\xab\xbb':
궓[亀[佤]] = 괠[亀[侰]]
elif 굸 == '\xeb\x94\x93':
괠[亀[佤]] = 궓[亀[侰]]
elif 굸 == '\xeb\x8c\x92':
괠[亀[佤]] = 佤
elif 굸 == '\xeb\xac\x87':
궓[亀[佤]] = 佤
elif 굸 == '\xeb\xac\x9f':
괠[亀[佤]] = input(괠[亀[侰]])
elif 굸 == '\xea\xbd\xba':
궓[亀[佤]] = input(괠[亀[侰]])
elif 굸 == '\xeb\x8f\xaf':
print(괠[亀[佤]])
elif 굸 == '\xeb\xad\x97':
print(궓[亀[佤]])
elif 굸 == '\xeb\xad\xbf':
굴 = 괠[亀[佤]]
elif 굸 == '\xeb\xae\x93':
굴 = 궓[亀[佤]]
elif 굸 == '\xeb\xae\xb3':
굴 = 괣.pop()
elif 굸 == '\xeb\xaf\x83' or 괠[亀[侰]] > 괠[亀[俴]]:
굴 = 亀[佤]
괣.append(굴)
continue
elif 굸 == '\xea\xbd\xb2':
괠[7] = 佤
for i in range(len(괠[亀[佤]])):
if 괠[亀[佤]] != 괠[亀[侰]]:
괠[7] = 侰
굴 = 괠[亀[俴]]
괣.append(굴)
elif 굸 == '\xea\xbe\xae':
괢 = ''
for i in range(len(괠[亀[佤]])):
괢 += chr(ord(괠[亀[佤]][i]) ^ 괠[亀[侰]])
괠[亀[佤]] = 괢
elif 굸 == '\xea\xbf\x9a':
괢 = ''
for i in range(len(괠[亀[佤]])):
괢 += chr(ord(괠[亀[佤]][i]) - 괠[亀[侰]])
괠[亀[佤]] = 괢
elif 굸 == '\xeb\x96\x87' or 괠[亀[侰]] > 괠[亀[俴]]:
굴 = 괠[亀[佤]]
괣.append(굴)
continue
elif 굸 == '\xeb\x97\x8b' or 괠[亀[侰]] > 괠[亀[俴]]:
굴 = 궓[亀[佤]]
괣.append(굴)
continue
elif 굸 == '\xeb\x98\xb7' or 괠[亀[侰]] == 괠[亀[俴]]:
굴 = 亀[佤]
괣.append(굴)
continue
elif 굸 == '\xeb\x9a\xab' or 괠[亀[侰]] == 괠[亀[俴]]:
굴 = 괠[亀[佤]]
괣.append(굴)
continue
elif 굸 == '\xeb\x9d\x87' and 괠[亀[侰]] == 괠[亀[俴]]:
굴 = 궓[亀[佤]]
괣.append(굴)
continue
굴 += 侰
䯂([
[
'\xea\xbc\x96',
佤,
'Authentication token: '],
[
'\xea\xbd\xba',
佤,
佤],
[
'\xea\xbc\x96',
6, 'á×äÓâæíäàßåÉÛãåäÉÖÓÉäàÓÉÖÓåäÉÓÚÕæïèäßÙÚÉÛÓäàÙÔÉÓâæÉàÓÚÕÓÒÙæäàÉäàßåÉßåÉäàÓÉÚÓáÉ·Ôâ×ÚÕÓÔɳÚÕæïèäßÙÚÉÅä×ÚÔ×æÔÉ×Úïá×ïåÉßÉÔÙÚäÉæÓ×ÜÜïÉà×âÓÉ×ÉÑÙÙÔÉâßÔÉÖãäÉßÉæÓ×ÜÜïÉÓÚÞÙïÉäàßåÉåÙÚÑÉßÉàÙèÓÉïÙãÉáßÜÜÉÓÚÞÙïÉßäÉ×åáÓÜÜ\x97ÉïÙãäãÖÓ\x9aÕÙÛ\x99á×äÕà©â«³£ï²ÕÔÈ·±â¨ë'],
[
'\xea\xbc\x96',
俴,
俴 ** (3 * 俴 + 侰) - 俴 ** (俴 + 侰)],
[
'\xea\xbc\x96',
4,
15],
[
'\xea\xbc\x96',
3,
侰],
[
'\xeb\x83\x83',
俴,
俴,
3],
[
'\xeb\x89\x83',
俴,
俴,
4],
[
'\xea\xb4\xa1',
佤,
俴],
[
'\xeb\x8c\x92',
3],
[
'\xea\xbe\xae',
6,
3],
[
'\xea\xbc\x96',
佤,
'Thanks.'],
[
'\xea\xbc\x96',
侰,
'Authorizing access...'],
[
'\xeb\x8f\xaf',
佤],
[
'\xeb\x94\x93',
佤,
佤],
[
'\xea\xbe\xae',
佤,
俴],
[
'\xea\xbf\x9a',
佤,
4],
[
'\xea\xbc\x96',
5,
19],
[
'\xea\xbd\xb2',
佤,
6,
5],
[
'\xeb\x8f\xaf',
侰],
[
'\xeb\x93\x83'],
[
'\xea\xbc\x96',
侰,
'Access denied!'],
[
'\xeb\x8f\xaf',
侰],
[
'\xeb\x93\x83']])
vm题,经过分析可得到逻辑
L1[0] = 'Authentication token: '
L2[0] = input(L1[0])
L1[6]='á×äÓâæíäàßåÉÛãåäÉÖÓÉäàÓÉÖÓåäÉÓÚÕæïèäßÙÚÉÛÓäàÙÔÉÓâæÉàÓÚÕÓÒÙæäàÉäàßåÉßåÉäàÓÉÚÓáÉ·Ôâ×ÚÕÓÔɳÚÕæïèäßÙÚÉÅä×ÚÔ×æÔÉ×Úïá×ïåÉßÉÔÙÚäÉæÓ×ÜÜïÉà×âÓÉ×ÉÑÙÙÔÉâßÔÉÖãäÉßÉæÓ×ÜÜïÉÓÚÞÙïÉäàßåÉåÙÚÑÉßÉàÙèÓÉïÙãÉáßÜÜÉÓÚÞÙïÉßäÉ×åáÓÜÜ\x97ÉïÙãäãÖÓ\x9aÕÙÛ\x99á×äÕà©â«³£ï²ÕÔÈ·±â¨ë'
L1[2] = 120
L1[4] = 15
L1[3] = 1
L1[2] = L1[2] * L1[3]
L1[2] = L1[2] + L1[4]
L1[0] = L1[2]
L1[3] = 0
e = ''
for i in range(len(L1[6])):
e += chr(ord(L1[6][i]) ^ L1[3])
L1[6] = e
L1[0] = 'Thanks.'
L1[1] = 'Authorizing access...'
print(L1[0])
L1[0] = L2[0]
e = ''
for i in range(len(L1[0])):
e += chr(ord(L1[0][i]) ^ L1[2])#135
L1[0] = e
e = ''
for i in range(len(L1[0])):
e += chr(ord(L1[0][i]) - L1[4])#15
L1[0] = e
L1[5] = 19
L1[7] = 0
for i in range(len(L1[0])):
if L1[0] != L1[6]:
L1[7] = 1
a = L1[5]
L3.append(a)
print(L1[1])
其实这题有一点小问题,如果输入为空也会验证成功

[ACTF新生赛2020]fungame
感觉有点脑洞题
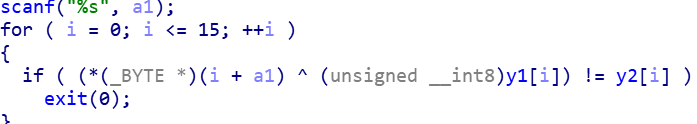
有个异或,但结果不是flag,在函数中随意翻翻,找到
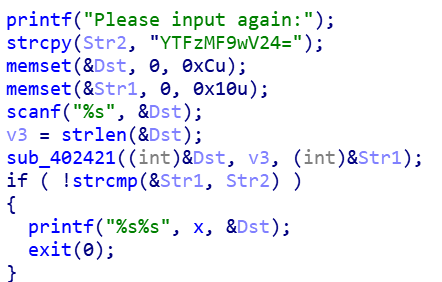
base64得到提示也是pwn
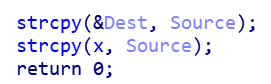
此处没控制长度,所以可以输入跳到到指定地址
所以flag为解异或的值+地址+解base64的值


 浙公网安备 33010602011771号
浙公网安备 33010602011771号