idapython 开发
调试方法
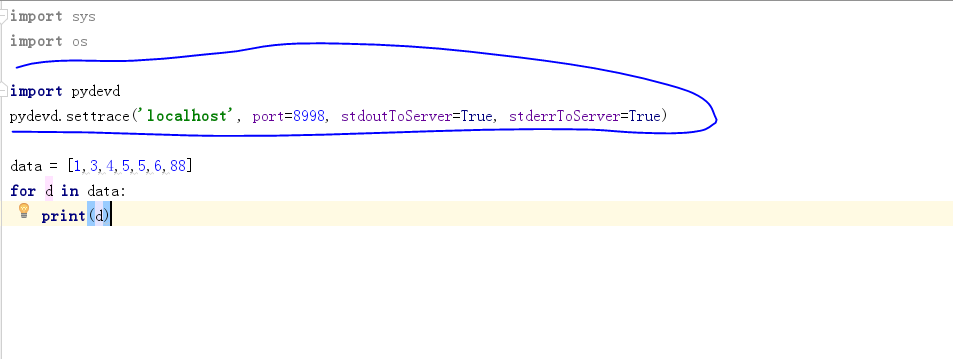
使用 pydevd
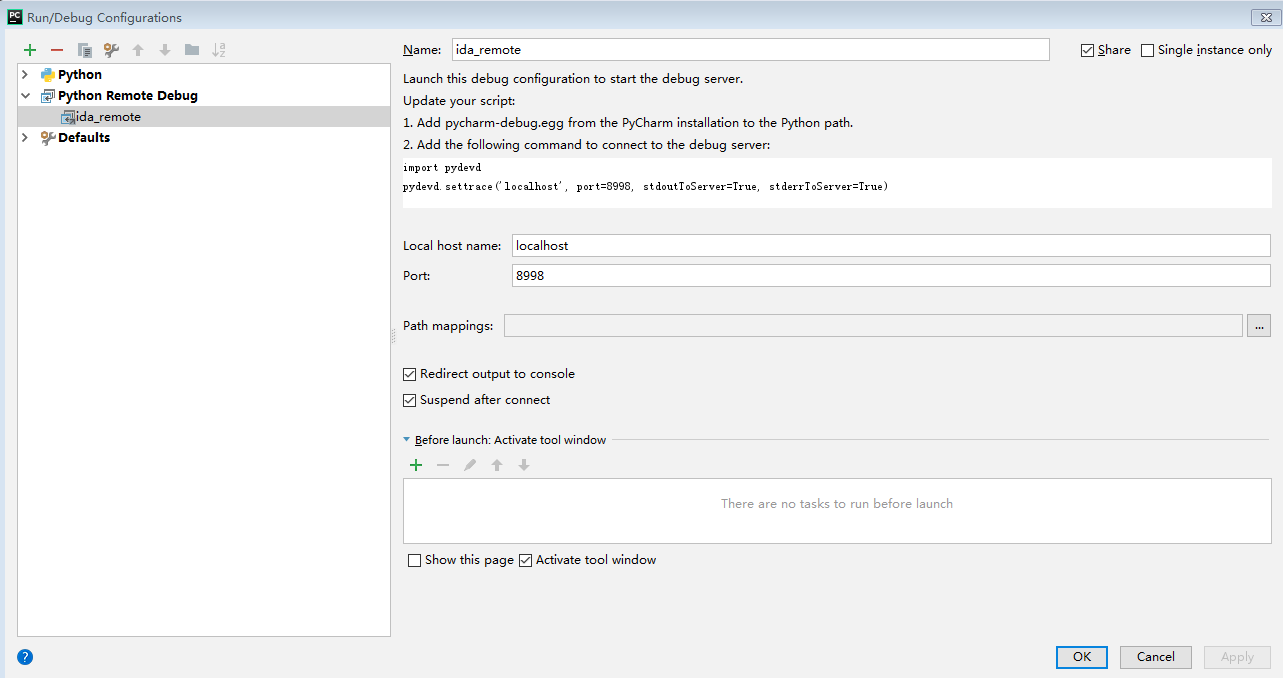
然后在需要调试处加入调试代码
GetOperandValue
作用
- 参数1: ea 虚拟地址
- 参数2: 操作数号
返回指令的操作数的被解析过的值
文档
def GetOperandValue(ea, n):
"""
Get number used in the operand
This function returns an immediate number used in the operand
@param ea: linear address of instruction
@param n: the operand number
@return: value
operand is an immediate value => immediate value
operand has a displacement => displacement
operand is a direct memory ref => memory address
operand is a register => register number
operand is a register phrase => phrase number
otherwise => -1
"""
实例
.text:080488C9 cmp eax, 1
.text:080488CC jz short loc_80488D8
.text:080488CE sub esp, 0Ch
其中 080488CC 处的指令的16进制表示为
74 0A
这一条指令有一个操作数,所以通过 GetOperandValue 可以获取获取通过 ida 解析的值。
Python>hex(GetOperandValue(0x080488CC,0))
0x80488d8L
GetMnem
作用
- 参数1: ea 虚拟地址
返回指令的操作码的助记符
文档
def GetMnem(ea):
"""
Get instruction mnemonics
@param ea: linear address of instruction
@return: "" - no instruction at the specified location
实例
.text:080488C9 cmp eax, 1
.text:080488CC jz short loc_80488D8
.text:080488CE sub esp, 0Ch
Python>GetMnem(0x80488CC)
jz
GetOpnd
作用
- 参数1: ea 虚拟地址
- 参数2: 操作数索引
返回指令的操作数
文档
def GetOpnd(ea, n):
"""
Get operand of an instruction
@param ea: linear address of instruction
@param n: number of operand:
0 - the first operand
1 - the second operand
@return: the current text representation of operand or ""
"""
实例
.text:080488C9 cmp eax, 1
.text:080488CC jz short loc_80488D8
.text:080488CE sub esp, 0Ch
Python>GetOpnd(0x80488CC,0)
loc_80488D8
GetDisasm
作用
- 参数1: ea 虚拟地址
得到指令的反汇编字符串
文档
def GetDisasm(ea):
"""
Get disassembly line
@param ea: linear address of instruction
@return: "" - could not decode instruction at the specified location
@note: this function may not return exactly the same mnemonics
as you see on the screen.
"""
实例
.text:080488C9 cmp eax, 1
.text:080488CC jz short loc_80488D8
.text:080488CE sub esp, 0Ch
Python>GetDisasm(0x80488CC)
jz short loc_80488D8
PrevHead 和 NextHead
作用
- 参数1: ea 虚拟地址
得到前一条或者后一条指令的地址
实例
.text:080488AF add esp, 10h
.text:080488B2 mov [ebp+fd], eax
.text:080488B5 sub esp, 4
Python>hex(PrevHead(0x080488B2))
0x80488afL
Python>hex(NextHead(0x080488B2))
0x80488b5L




 浙公网安备 33010602011771号
浙公网安备 33010602011771号