目录
1. 安装ansible:
sudo apt install ansible -y
2. 安装ansible的cisco和juniper模块
Ansible 模块大全
ansible-galaxy collection install cisco.ios
ansible-galaxy collection install junipernetworks.junos
ansible-galaxy collection install cisco.asa
3. 创建ansible inventory
可以在hosts中创建,也可以自行写一个inventory文件,vars是switch的一些变量
[cisco_switch]
switch1 ansible_host=192.168.1.1
[cisco_switch:vars]
ansible_connection=ansible.netcommon.network_cli
ansible_network_os=cisco.ios.ios
ansible_user=backupuser # ssh的用户名
ansible_become=true
ansible_become_method=enable # 开启enable
ansible_network_cli_ssh_type=libssh
[cisco_asa]
ASA ansible_host=192.168.1.2
[cisco_asa:vars]
ansible_connection=ansible.netcommon.network_cli
ansible_network_os=cisco.asa.asa
ansible_user=backupuser # ssh的用户名
ansible_network_cli_ssh_type=libssh
[juniper_firewalls]
juniper ansible_host=192.168.1.3
[china_juniper_firewalls:vars]
ansible_connection=ansible.netcommon.netconf
ansible_network_os=junipernetworks.junos.junos
ansible_user=backupuser # ssh的用户名
4. 创建密码加密
由于在playbook中直接将ssh的登录名及密码以明文的方式写在里面,非常不安全,可以使用ansible-vault对这些密码进行加密,而后将加密后的密码写在一个pass.yml文件中,我们只需要保存好用于解密pass.yml文件的密码即可,安全性大大提高
- 加密ssh密码:
ansible-vault encrypt_string 'test1234' --name 'cisco_pass'

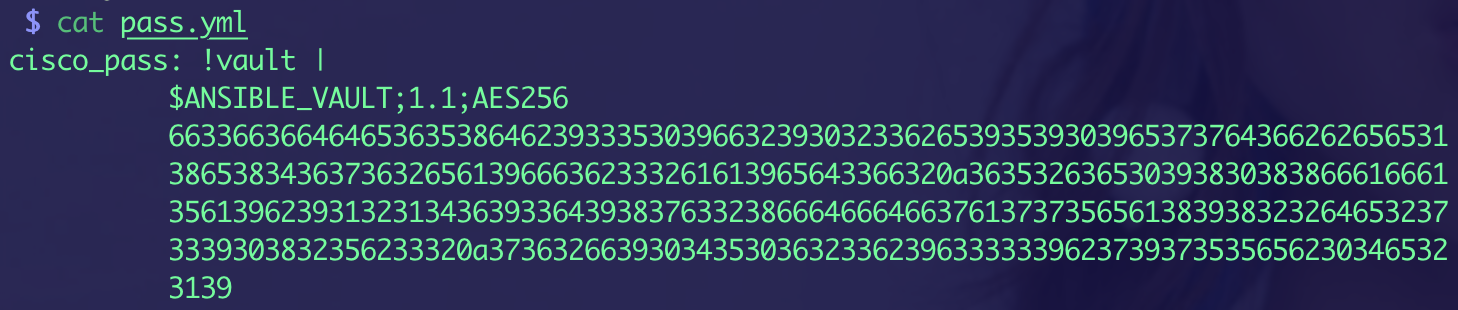
- 将加密后的秘文写入pass.yml文件中
`cat pass.yml`
- 依次加密cisco的enable密码及juniper密码,写入pass.yml中

5. 创建备份playbook
backup.yml:
---
- name: Backup cisco switches
hosts: cisco_switches
gather_facts: false
vars_files:
- pass.yml
vars:
ansible_password: '{{cisco_pass}}'
ansible_become_password: '{{cisco_enable_pass}}'
tasks:
- name: Get timestamp
ansible.builtin.command: date +%Y%m%d-%H-%M-%S
run_once: true
register: timestamp
- name: Backup ios config
cisco.ios.ios_config:
backup: true
backup_options:
filename: "running-config-{{ timestamp.stdout }}"
dir_path: "/backup/{{ inventory_hostname }}"
- name: Backup cisco asa
hosts: cisco_asa
gather_facts: false
vars_files:
- pass.yml
vars:
ansible_password: '{{_asa_pass}}'
ansible_become_password: '{{asa_enable_pass}}'
tasks:
- name: Get timestamp
ansible.builtin.command: date +%Y%m%d-%H-%M-%S
run_once: true
register: timestamp
- name: Backup asa config
cisco.asa.asa_config:
backup: true
backup_options:
filename: "running-config-{{ timestamp.stdout }}"
dir_path: "/backup/{{ inventory_hostname }}"
- name: Backup juniper firewalls
hosts: juniper_firewalls
gather_facts: false
vars_files:
- pass.yml
vars:
ansible_password: '{{juniper_pass}}'
tasks:
- name: Get timestamp
ansible.builtin.command: date +%Y%m%d-%H-%M-%S
run_once: true
register: timestamp
- name: Backup junos config
junipernetworks.junos.junos_config:
backup: true
backup_options:
filename: "running-config-{{ timestamp.stdout }}"
dir_path: "/backup/{{ inventory_hostname }}"
6. 运行playbook
ansible-playbook -i inventory backup.yml --ask-vault-pass




 浙公网安备 33010602011771号
浙公网安备 33010602011771号