手动申请免费泛域名证书
这里使用的是 certbot
环境
| 属性 | 值 |
|---|---|
| 系统 | Ubuntu |
| 版本 | 22.04.3 LTS |
| certbot版本 | 1.21.0 |
安装
sudo apt update
sudo apt install certbot
查看
$ certbot --version
certbot 1.21.0
使用
首次使用还会提示需要同意协议
同意协议
$ certbot certonly --manual --email xxx@xxxx.xxx --preferred-challenges dns -d *.xxx.xxx
Saving debug log to /var/log/letsencrypt/letsencrypt.log
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.3-September-21-2022.pdf. You must
agree in order to register with the ACME server. Do you agree?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o:
这里是提示您阅读 Let's Encrypt 的服务条款(Terms of Service),并要求您同意这些条款以便在 ACME 服务器上注册。
Let's Encrypt 是一个提供免费 SSL/TLS 证书的服务,你需要同意其服务条款才能使用其服务。
您可以通过访问提供的链接(https://letsencrypt.org/documents/LE-SA-v1.3-September-21-2022.pdf)阅读服务条款。
如果您同意这些条款,请在提示中输入 y 并按 Enter 键确认。如果您不同意这些条款,请输入 N 并按 Enter 键退出 Certbot。
是否接收邮件
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing, once your first certificate is successfully issued, to
share your email address with the Electronic Frontier Foundation, a founding
partner of the Let's Encrypt project and the non-profit organization that
develops Certbot? We'd like to send you email about our work encrypting the web,
EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o:
这里是在询问你是否愿意在成功颁发第一个证书后与电子前沿基金会(Electronic Frontier Foundation,简称 EFF)共享你的电子邮件地址。
电子前沿基金会是 Let's Encrypt 项目的创始合作伙伴之一,也是开发 Certbot 的非盈利组织。
他们希望与你联系,向你发送有关其在加密网络方面的工作、新闻、活动以及如何支持数字自由的信息。
如果你愿意接收这些电子邮件,请在提示中输入 Y 并按 Enter 键确认。
如果你不希望接收这些电子邮件,请输入 N 并按 Enter 键拒绝。
新建DNS记录
Account registered.
Requesting a certificate for *.xxx.xxx
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please deploy a DNS TXT record under the name:
_acme-challenge.xxx.xxx.
with the following value:
AOuRcwkvyyKOT_ZKQs8xrrEVGxs1AAOGMqwdvnj0ERs
Before continuing, verify the TXT record has been deployed. Depending on the DNS
provider, this may take some time, from a few seconds to multiple minutes. You can
check if it has finished deploying with aid of online tools, such as the Google
Admin Toolbox: https://toolbox.googleapps.com/apps/dig/#TXT/_acme-challenge.xxx.xxx.
Look for one or more bolded line(s) below the line ';ANSWER'. It should show the
value(s) you've just added.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Press Enter to Continue
这里是提示,需要在本域名的DNS权威服务器或者DNS 提供商中创建一个 TXT 记录
DNS提供商
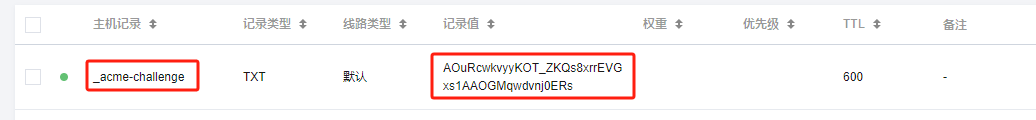
权威服务器类似
_acme-challenge TXT "AOuRcwkvyyKOT_ZKQs8xrrEVGxs1AAOGMqwdvnj0ERs"
公网校验
$ dig _acme-challenge.xxx.xxx txt
; <<>> DiG 9.18.12-0ubuntu0.22.04.3-Ubuntu <<>> _acme-challenge.xxx.xxx txt
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 2704
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 65494
;; QUESTION SECTION:
;_acme-challenge.xxx.xxx. IN TXT
;; ANSWER SECTION:
_acme-challenge.xxx.xxx. 600 IN TXT "AOuRcwkvyyKOT_ZKQs8xrrEVGxs1AAOGMqwdvnj0ERs"
;; Query time: 196 msec
;; SERVER: 127.0.0.53#53(127.0.0.53) (UDP)
;; WHEN: Sun Feb 18 11:15:57 CST 2024
;; MSG SIZE rcvd: 110
解析成功,回车 ,生成证书
生成证书
Successfully received certificate.
Certificate is saved at: /etc/letsencrypt/live/xxx.xxx/fullchain.pem
Key is saved at: /etc/letsencrypt/live/xxx.xxx/privkey.pem
This certificate expires on 2024-05-18.
These files will be updated when the certificate renews.
NEXT STEPS:
- This certificate will not be renewed automatically. Autorenewal of --manual certificates requires the use of an authentication hook script (--manual-auth-hook) but one was not provided. To renew this certificate, repeat this same certbot command before the certificate's expiry date.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
If you like Certbot, please consider supporting our work by:
* Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
* Donating to EFF: https://eff.org/donate-le
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
会提示成功,并显示到期时间,并给出证书位置
证书的有效期只有90天,到期了需要手动再申请
查看证书
上面也是给出了证书的目录
Successfully received certificate.
Certificate is saved at: /etc/letsencrypt/live/xxx.xxx/fullchain.pem
Key is saved at: /etc/letsencrypt/live/xxx.xxx/privkey.pem
查看证书目录
$ ll /etc/letsencrypt/live/xxx.xxx/
总计 12
drwxr-xr-x 2 root root 4096 Feb 18 11:16 ./
drwx------ 3 root root 4096 Feb 18 11:16 ../
-rw-r--r-- 1 root root 692 Feb 18 11:16 README
lrwxrwxrwx 1 root root 33 Feb 18 11:16 cert.pem -> ../../archive/xxx.xxx/cert1.pem
lrwxrwxrwx 1 root root 34 Feb 18 11:16 chain.pem -> ../../archive/xxx.xxx/chain1.pem
lrwxrwxrwx 1 root root 38 Feb 18 11:16 fullchain.pem -> ../../archive/xxx.xxx/fullchain1.pem
lrwxrwxrwx 1 root root 36 Feb 18 11:16 privkey.pem -> ../../archive/xxx.xxx/privkey1.pem
可以看到,其实就是从archive目录下生成的软连接
$ ll /etc/letsencrypt/archive/xxx.xxx/
总计 24
drwxr-xr-x 2 root root 4096 Feb 18 11:16 ./
drwx------ 3 root root 4096 Feb 18 11:16 ../
-rw-r--r-- 1 root root 1757 Feb 18 11:16 cert1.pem
-rw-r--r-- 1 root root 1826 Feb 18 11:16 chain1.pem
-rw-r--r-- 1 root root 3583 Feb 18 11:16 fullchain1.pem
-rw------- 1 root root 1704 Feb 18 11:16 privkey1.pem
使用
在nginx中,只需要将 fullchain1.pem 和 privkey1.pem 安装到对应的位置,并开启https就可以了
选项
命令
certbot certonly --manual --email xxx@xxxx.xxx --preferred-challenges dns -d *.xxx.xxx
certonly:此选项告诉 Certbot 仅获取证书,而不安装它。这对于在手动配置 Web 服务器以使用证书时非常有用。manual:此选项告诉 Certbot 使用手动验证方法。在这种情况下,您需要手动完成验证过程,例如创建 DNS 记录或配置 Web 服务器。--email xxx@xxxx.xxx:此选项告诉 Certbot 在验证过程中使用 xxx@xxxx.xxx 作为您的电子邮件地址。这对于接收有关证书过期和其他相关通知非常有用。--preferred-challenges dns:此选项告诉 Certbot 优先使用 DNS 验证方法。在这种情况下,您需要在您的 DNS 提供商中创建一个 TXT 记录,以便验证您对域名的所有权。-d *.xxx.xxx:此选项告诉 Certbot 为通配符域名 *.xxx.xxx 获取证书。这意味着证书将适用于所有子域名,如果还想适用于根域名xxx.xxx,那还需要在上面的命令后面再加-d xxx.xxx。
总结
以上方法只是一个简单轻量的申请免费证书的方法,当然,还有许多其他更好的方法,大家也可以在评论区分享自己使用其他比较方便的方法,互相学习。
以上大家使用的时候,只需要将邮箱换成自己的邮箱,域名换成自己的域名就可以了
本文来自博客园,作者:厚礼蝎,转载请注明原文链接:https://www.cnblogs.com/guangdelw/p/18019050


 浙公网安备 33010602011771号
浙公网安备 33010602011771号